Comprehensive Threat Exposure Management Platform
For a detailed threat digest, download the PDF file here
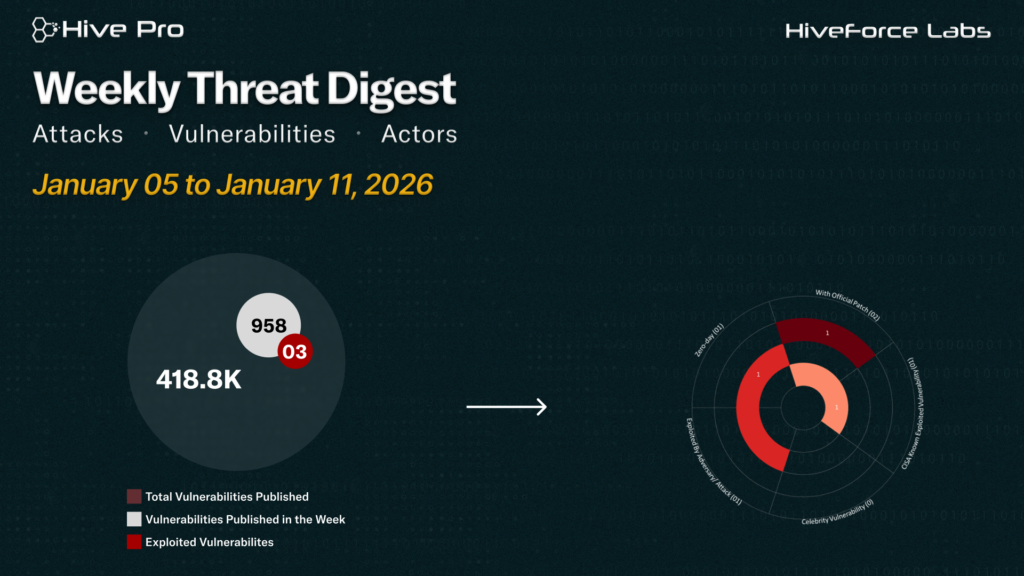
HiveForce Labs has reported a sharp rise in cybersecurity threats, highlighting the increasing complexity and frequency of global cyber incidents. Over the past week, six major attacks were detected, three critical vulnerabilities were publicly disclosed, and one active threat actor group was monitored, signaling a concerning escalation in malicious activity.
CVE-2026-0625 is a critical, actively exploited vulnerability in multiple legacy D-Link DSL routers. Exploitation was confirmed in late 2025 and mirrors techniques used in historical DNSChanger campaigns. All affected models reached end-of-life over six years ago and will not be patched, leaving any remaining deployments permanently exposed. Device replacement is the only viable risk elimination measure.
CVE-2025-37164 is a critical unauthenticated remote code execution flaw in HPE OneView that allows complete compromise of the infrastructure management platform over the network. Recent APT36 operations demonstrate how minimal user interaction can facilitate persistent, stealthy espionage. The campaign reflects APT36’s shift toward more resilient and security-aware intrusion frameworks. These underscore the need for disciplined security updates and sustained monitoring in response to rapidly evolving attack methodologies.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.