Comprehensive Exposure Assessment & Adversarial Exposure Validation
From one platform: Get 360° asset exposure visibility, then assess, prioritize, validate, and remediate the security issues that matter most.
Issues In Managing Threat Exposure
The vulnerability noise, escalating cyber threats, and resource constraints are overwhelming. You're not alone.
Limited and incompatible scanning tools create blind spots in vulnerability management, complicating risk assessment and mitigation. Fragmented security findings hinder comprehensive exposure management and impede practitioners’ ability to achieve full protection.
Hidden cyber threats, exacerbated by scanners and other tools lacking threat prediction capabilities, obscure critical vulnerabilities and security findings, impeding proactive risk mitigation efforts and leaving systems vulnerable to exploitation.

Generic risk prioritization efforts baselined on global frameworks lacking subjectivity fail to consider the effects of patchable and non-patchable exposures, leaving systems vulnerable to overlooked threats and potential exploitation.
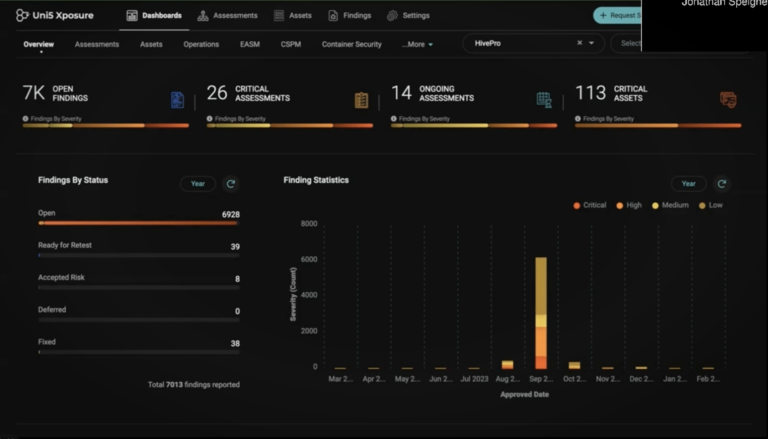

Inadequate and business risk-lacking intelligence on remediation guidance undermines and impedes comprehensive exposure mitigation efforts. Resource-constrained security teams struggle to manage threat exposure effectively, needing automated solutions for contextual analysis without inducing analysis paralysis.

Limited and incompatible scanning tools create blind spots in vulnerability management, complicating risk assessment and mitigation. Fragmented security findings hinder comprehensive exposure management and impede practitioners’ ability to achieve full protection.

Hidden cyber threats, exacerbated by scanners and other tools lacking threat prediction capabilities, obscure critical vulnerabilities and security findings, impeding proactive risk mitigation efforts and leaving systems vulnerable to exploitation.

Generic risk prioritization efforts baselined on global frameworks lacking subjectivity fail to consider the effects of patchable and non-patchable exposures, leaving systems vulnerable to overlooked threats and potential exploitation.


Inadequate and business risk-lacking intelligence on remediation guidance undermines and impedes comprehensive exposure mitigation efforts. Resource-constrained security teams struggle to manage threat exposure effectively, needing automated solutions for contextual analysis without inducing analysis paralysis.
One platform – absolute ease
Uni5 Xposure Eliminates These Issue For Good
Uni5 Xposure sees through the noise, combats threat exposure, and empowers you to remediate what matters most.
Uni5 Xposure enhances asset visibility, eliminating blind spots caused by limited and incompatible scanning tools, for comprehensive exposure management and risk mitigation. See your enterprise from the attacker’s perspective.
Code-Infrastructure-Cloud ScanningUni5 Xposure’s integration-friendly platform combines 6 native Code-Infra-Cloud Scanners with EASM to resolve siloed security findings for comprehensive exposure assessment and risk mitigation.
Security Assessment, Scan & Test ManagementUni5 Xposure’s integration and management of vulnerability assessments, security scans, security assessment and penetration tests builds for optimal visibility, streamlines remediation, and fortifies security defenses.
In-Depth Security IntelligenceUni5 Xposure enables you to stay ahead of threats with rich threat intelligence, revealing critical vulnerabilities, zero days, and beyond, fueling proactive risk mitigation efforts and fortifying system resilience. The platform is also robust with attack, threat actor, and patch intelligence. Visit the HiveForce Labs page to learn more.
Vulnerability & Threat PrioritizationUni5 Xposure’s engine prioritizes all exposure points, not just vulnerabilities, combatting threats effectively based on what is visible to threat actors.
Breach & Attack Simulation and Control ValidationBy simulating threat actor motives, actions, PoCs, exploitable vulnerabilities and more, Uni5 Xposure assesses your compensatory controls’ adequacy and effectiveness.
Patch & IoC IntelligenceIntegrating patch and IoC intelligence into Uni5 Xposure ensures timely exposure remediation, proactive threat detection, streamlined operations, improved efficiency, enhanced collaboration, and fortified security resilience.
Remediation OrchestrationUni5 Xposure boosts security-IT teamwork within SLA constraints, integrating smoothly for efficient remediation, ensuring effective risk management guided by threat insights.
benefits
Streamlining processes to minimize intricacies

No blind spots in vulnerability detection, reduced likelihood of costly breaches and minimized potential financial losses.
Proactive threat, actor and vulnerability intelligence and simulation capabilities to detect and mitigate cyber risks before they happen.

Uni5 Xposure automates critical finding importance, threat tracking, remediation, and collaboration, saving time and resource energy.
Uni5 Xposure’s intelligence facilitates efficient issue resolution, comprehensive risk management, compliance adherence, and organizational resilience across security, IT, and business teams.
Automated tools integrations
Leverage the power of integrated platforms. Uni5 Xposure works seamlessly with various vulnerability scanners, patch management tools, and ITSM platforms and more.
View AllFAQ
Quick answers to questions you may have
Discover everything about Hive Pro features, benefits, and more.