Hive Pro for SecOps
Full Asset Visibility & Proactive Threat Prevention
Gain total asset visibility, integrate threat intelligence, validate defenses, prioritize critical risks, and automate remediation to strengthen security and optimize response efforts effectively.
How Hive Pro Supercharges SecOps
The impact on your team’s performance and security posture.
Threat Detection
Exposure Points
Streamlined Remediation
how it helps
Streamline Security, Accelerate Innovation
Uni5 Xposure integrates seamlessly into your workflow, empowering your team to deliver on secure assets and resiliency against threats with speed and with greater confidence.
How It Works
Automating Security throughout the SecOps Pipeline
Uni5 Xposure seamlessly integrates with your SecOps processes, enhancing threat detection, incident response, and continuous monitoring to ensure robust and efficient security operations.
Automated and Manual External Attack Surface Scans
Automated and Manual Out-of-the-box Security Scans: Code, Container, Cloud, Web, Network, Mobile
See our integrations here.
Surface control gaps, weak points and misconfigurations
- Asset Criticality and Risk Appetite
- Vulnerability Intelligence (+Wormable)
- Threat Intelligence
- Compensatory Controls
- All Exploits (+Zero Days)
- Vertical & Geographical Location
- All and Active Threat Actors
- Recent Attacks & TTPs

You must know how well your controls are working to know where remediation matters most.
- Simulate Real-World Attacks:
3700+ Attack Scenarios and Countless Playbooks at Your Fingertips
- Surface Control Weaknesses & Gaps:
Surface and Dive into Faulty Controls and Where Attackers Find an In.
- Remediate Misconfigurations & Escalate Fixes:
Leverage a Large Patch Database and Multi-Path Remediation Recommendations

Uni5 Xposure provides intelligence you can leverage to fortify assets and improve controls.
- Largest Patch Intelligence Database:
50,000+ Patch Database to Streamline Patches
- IoC Intelligence for Reactive Response Improvement:
Where patches are unavailable, leverage IoC intelligence to improve detection and response signatures.
- Multiple Remediation Options Where Available:
Remediate according to your risk appetite, and track all decisions
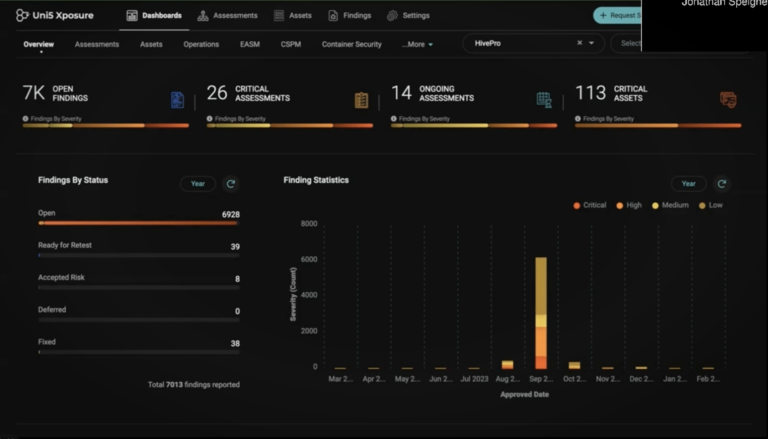
External Attack Surface Scans
Automated and Manual External Attack Surface Scans
Security Scans
Automated and Manual Out-of-the-box Security Scans: Code, Container, Cloud, Web, Network, Mobile
Integration Friendly Scanning
See our integrations here.
Breach & Attack Simulation Test
Surface control gaps, weak points and misconfigurations

Parameters For Exposure Prioritization
- Asset Criticality and Risk Appetite
- Vulnerability Intelligence (+Wormable)
- Threat Intelligence
- Compensatory Controls
- All Exploits (+Zero Days)
- Vertical & Geographical Location
- All and Active Threat Actors
- Recent Attacks & TTPs

Transparent Risks With Cyber Validation
You must know how well your controls are working to know where remediation matters most.
Simulate Real-World Attacks:
3700+ Attack Scenarios and Countless Playbooks at Your Fingertips
Surface Control Weaknesses & Gaps:
Surface and Dive into Faulty Controls and Where Attackers Find an In.
Remediate Misconfigurations & Escalate Fixes:
Leverage a Large Patch Database and Multi-Path Remediation Recommendations

Proactive and Reactive Remediation Options
Uni5 Xposure provides intelligence you can leverage to fortify assets and improve controls.
Largest Patch Intelligence Database:
50,000+ Patch Database to Streamline Patches
IoC Intelligence for Reactive Response Improvement:
Where patches are unavailable, leverage IoC intelligence to improve detection and response signatures.
Multiple Remediation Options Where Available:
Remediate according to your risk appetite, and track all decisions
Automated tools integrations
Leverage the power of integrated platforms. Uni5 Xposure works seamlessly with various vulnerability scanners, patch management tools, ITSM platforms, EDR, and more.
View AllExplore how we’ve help other companies
faq
Quick answers to questions you may have
Discover everything about Hive Pro features, benefits, and more.