Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
The world of cybercrime has its own cast of characters, each with a unique script. Some are patient spies, like state-sponsored groups that move silently within a network for months to gather intelligence. Others are loud and aggressive, like ransomware gangs that operate like ruthless businesses, demanding payment to restore critical operations. Knowing the difference is crucial. Recognizing an attacker’s signature tactics—from the phishing lures they use to the malware they deploy—is the first step toward building a defense that can withstand their specific playbook. Below, we will profile the top 10 threat actors, giving you a detailed “who’s who” of your most dangerous adversaries.
Understanding the threat landscape means knowing the players. Attacks aren’t random; they’re orchestrated by specific groups with distinct motivations, tools, and targets. Getting familiar with these threat actors helps you move from a generic defense posture to a focused, intelligence-driven strategy. When you know who might be knocking on your door and what they’re looking for, you can build stronger walls and smarter alarms.
These groups range from state-sponsored espionage units conducting covert operations to financially motivated cybercriminals running ransomware like a business. Each has a unique signature, from the phishing lures they craft to the malware they deploy. For example, a state-sponsored group like APT29 might spend months inside your network moving silently, while a ransomware group like LockBit will announce its presence loudly and demand payment quickly. Recognizing these different operational styles is key to effective incident response. Keeping an eye on their evolving tactics is essential for anticipating their next move and ensuring your security controls are prepared for real-world attack methods. Below, we’ll cover some of the most prominent groups, from nation-state actors to RaaS syndicates, to give you a clearer picture of who you’re up against.
Attributed to Russia’s Foreign Intelligence Service (SVR), APT29, or Cozy Bear, is a master of stealthy, long-term espionage campaigns. Their primary goal is intelligence gathering, not disruption. They often initiate attacks with highly targeted phishing emails to gain initial access. Once inside a network, they move patiently, using tools like AdFind to map Active Directory and identify high-value targets. Their operations are notoriously difficult to detect, as seen in the sophisticated SolarWinds supply chain attack. A 2023 analysis of their breach of Microsoft email accounts revealed their use of password spraying to blend in with normal network traffic.
Also linked to Russian intelligence, but this time the GRU military agency, APT28 (Fancy Bear) is known for more aggressive and disruptive operations. While also focused on espionage, their tactics are often louder and designed to support Russia’s geopolitical interests. This group was famously implicated in the interference of the 2016 U.S. presidential election. APT28 typically relies on spear-phishing campaigns armed with malware and exploits to infiltrate government, military, and media organizations. Their willingness to cause chaos makes them a persistent and high-impact threat.
The Lazarus Group is a prolific state-sponsored actor operating on behalf of North Korea. This group is a hybrid threat, conducting operations for both espionage and financial gain to fund the regime. Their activities are incredibly diverse, ranging from attacks on cryptocurrency exchanges to deploying destructive malware. Lazarus was behind the infamous Sony Pictures hack and the global WannaCry ransomware outbreak, demonstrating their capability and willingness to execute both targeted and indiscriminate attacks. The U.S. government has issued numerous advisories on their activities, highlighting their continued threat to the financial and critical infrastructure sectors.
RansomHub has emerged as a significant player in the ransomware-as-a-service (RaaS) landscape, attracting affiliates from other now-defunct groups. They operate a double-extortion model, where they not only encrypt a victim’s data but also exfiltrate it, threatening to publish the sensitive information on their data leak site if the ransom isn’t paid. The group targets a wide variety of industries, demonstrating a purely financial motivation. Their platform allows less-skilled attackers to launch sophisticated attacks, making them a widespread and unpredictable threat.
The Qilin ransomware group is another RaaS operation that has gained notoriety for targeting critical infrastructure, including healthcare and education organizations, where downtime is especially damaging. Their ransomware is written in the Go programming language, which allows their malware to be easily adapted to target different operating systems, including Windows and Linux. This cross-platform capability, combined with their focus on high-pressure targets, makes Qilin a formidable adversary for organizations that rely on a mix of technology environments.
FIN7 is a sophisticated and persistent financially motivated group that has been active for nearly a decade. They are known for their carefully crafted social engineering campaigns, often targeting employees in the retail, restaurant, and hospitality sectors to gain access to point-of-sale (POS) systems. Their primary objective is to steal payment card data and other financial information. Over the years, FIN7 has evolved its tactics, using a variety of custom malware and even creating fake security companies to recruit unwitting IT specialists to help with their operations.
Often associated with FIN7, the Carbanak group specializes in large-scale heists targeting banks and financial institutions. Unlike many cybercriminal groups, Carbanak operates with the patience and precision of a state-sponsored actor. They infiltrate a bank’s network and spend months conducting reconnaissance, studying internal procedures, and identifying critical systems. Once they have a deep understanding of the environment, they execute their attack, using their access to make fraudulent wire transfers or even command ATMs to dispense cash at specific times for collection.
BlackCat, also known as ALPHV, is a highly sophisticated ransomware group known for its technical innovation and aggressive tactics. They were one of the first major ransomware families written in the Rust programming language, which offers improved performance and makes the malware more difficult for security researchers to reverse-engineer. BlackCat is infamous for its triple-extortion tactics: on top of encrypting and threatening to leak data, they often launch DDoS attacks against the victim’s public-facing websites to increase pressure to pay the ransom.
Although the Conti ransomware brand officially disbanded in 2022, its legacy and influence persist. At its height, Conti was one of the most ruthless RaaS operations, responsible for hundreds of attacks on critical infrastructure, including hospitals and emergency services. The group operated like a legitimate tech company with a clear hierarchy. After internal chats and their attack playbooks were leaked, the world got an unprecedented look into the inner workings of a top-tier ransomware syndicate. Many of its former members have since funneled into other ransomware groups, bringing their skills and experience with them.
LockBit is currently one of the most prolific and active RaaS operations in the world, having claimed thousands of victims across nearly every industry. The group is known for its fast and efficient encryption malware and its professional, business-like approach to extortion. LockBit operates a robust affiliate program, providing its partners with the tools and infrastructure needed to launch attacks. Their constant innovation and aggressive recruitment have allowed them to maintain a dominant position in the cybercrime ecosystem, making them a top threat for organizations globally.
Understanding what drives a threat actor is key to anticipating their moves and building a stronger defense. While the specific goals can vary, most motivations fall into a few core categories, from financial enrichment to political maneuvering. Knowing the “why” behind an attack helps you better prepare for the “how.”
For a huge number of threat actors, it all comes down to money. Cybercrime is a booming industry, and these groups operate like businesses, complete with their own R&D and customer support. Their goal is to maximize profit with minimal risk. They achieve this through tactics like ransomware, where they encrypt your data and demand a hefty payment for its release. Other common methods include phishing scams to steal credentials, selling stolen data on the dark web, and Business Email Compromise (BEC) to trick employees into wiring funds. It’s a mistake to think only large enterprises are in their crosshairs; smaller businesses are often targeted because they’re seen as easier prey with fewer security resources.
When a nation-state is backing a threat actor, the motives shift from profit to power. These groups, often called Advanced Persistent Threats (APTs), carry out missions on behalf of their governments. Their objectives can include stealing state secrets, gathering intelligence on foreign policy, pilfering valuable intellectual property to gain a competitive edge, or disrupting the critical infrastructure of rival nations. Groups linked to countries like Russia, China, and Iran are known for their sophisticated, long-term campaigns. They have significant resources and time, allowing them to execute highly targeted and stealthy attacks that can go undetected for months or even years. You can track the activities of these groups through our ongoing threat advisories.
Not every attack is about money or national secrets. Hacktivists are driven by ideology. These individuals or groups use their technical skills to support a political or social cause, aiming to spread a message, protest actions, or expose what they see as wrongdoing. Their tactics often include defacing websites with political messages, leaking sensitive documents to embarrass an organization, or launching Distributed Denial-of-Service (DDoS) attacks to take a target offline. While they might not be trying to steal your money, the reputational damage and operational disruption caused by a hacktivist campaign can be just as costly for a business.
Threat actor motivations are not always black and white. Some of the most complex groups operate in a gray area, blending different objectives. For instance, a group might engage in state-sponsored espionage while running a side hustle in cybercrime to fund their operations or for personal enrichment. A prime example is APT41, which is known for both spying on behalf of the Chinese government and deploying ransomware for financial gain. This blending of motives makes them highly unpredictable. Understanding these complex behaviors is a core focus of security research teams like HiveForce Labs, as it helps predict their next moves and protect potential targets.
Threat actors rely on a proven playbook of tactics to breach defenses and achieve their goals. While their specific tools may change, the underlying strategies often remain the same. Understanding these common methods is the first step in building a more resilient security posture. From exploiting human psychology to leveraging sophisticated software flaws, these are the core techniques you’re most likely to encounter.
This is more than just a generic spam email. Spear phishing is a highly targeted attack where threat actors use personalized information to trick specific individuals or groups. Groups like APT29 (Cozy Bear) are masters of this, crafting convincing emails that lure victims into revealing login details or downloading custom malware. These attacks succeed by exploiting human trust and urgency. By researching their targets on social media and corporate websites, attackers create a believable pretext that bypasses suspicion. This makes strong employee security training a critical layer of defense against these socially engineered threats.
The rise of Ransomware-as-a-Service (RaaS) has democratized cybercrime, allowing less-skilled actors to launch devastating attacks. Groups like RansomHub, one of the most active operations, function like a dark-web SaaS company. They provide the ransomware tools, payment portals, and support to affiliates in exchange for a cut of the profits. This business model is incredibly efficient, enabling widespread campaigns without requiring deep technical expertise from every attacker. The RaaS model significantly increases the volume of ransomware threats, making it essential for organizations to have robust backup and incident response plans in place to minimize damage and downtime.
The most sophisticated threat actors don’t wait for vulnerabilities to be publicly disclosed. Groups like APT28 (Fancy Bear) are known for their ability to discover and weaponize zero-day exploits—flaws in software that are unknown to the vendor. By attacking these unpatched vulnerabilities, they can bypass traditional signature-based security controls. This tactic is often combined with custom malware and aggressive phishing campaigns to ensure success. Defending against zero-days requires a shift from reactive patching to proactive exposure management. You need to prioritize vulnerabilities based on threat intelligence and potential impact, focusing on what attackers are actively exploiting in the wild.
Why break down the front door when you can find an unlocked window? That’s the logic behind supply chain attacks. Instead of targeting a well-defended organization directly, attackers compromise a less secure third-party vendor, partner, or software supplier. By hiding malicious code in software updates or exploiting trusted connections, they gain backdoor access to their ultimate target. These attacks are particularly dangerous because they exploit the inherent trust between business partners. A single compromised supplier can lead to the breach of dozens or even hundreds of their clients, making third-party risk management a non-negotiable part of any modern security strategy.
In the past, ransomware attacks were about one thing: encrypting your data and demanding a ransom to get it back. Today, things are more complicated. Threat actors like Dark Angels now practice “double extortion.” First, they steal sensitive data before encrypting the network. Then, they threaten to leak the stolen information publicly if the ransom isn’t paid. This puts immense pressure on victims, as they now face not only operational disruption but also regulatory fines, reputational damage, and customer lawsuits. This tactic ensures attackers have leverage even if the victim has reliable backups, making data exfiltration a primary concern in any ransomware incident.
Gaining initial access is just the first step. The real goal for many attackers is to move freely within the network to find and exfiltrate high-value data. To do this, they need valid credentials. Groups like APT41 (Winnti Group) are adept at stealing login details through phishing, malware, or exploiting software flaws. Once they have a foothold, they use these credentials for lateral movement, escalating their privileges and mapping out the network architecture. This allows them to blend in with normal traffic, making them difficult to detect. Protecting credentials with multi-factor authentication and monitoring for unusual account activity are essential for stopping attackers before they can reach their objective.
It might seem like cyberattacks are random, but threat actors are often quite strategic in how they select their victims. Their targeting methods range from highly specific, intelligence-driven campaigns to broad, opportunistic attacks that prey on the unprepared. Understanding these motivations helps you see your organization through an attacker’s eyes and anticipate where you might be most vulnerable. It’s less about who you are and more about what you have, what you do, and what weaknesses you expose.
Some of the most dangerous threat groups go after the biggest targets: critical infrastructure and high-value assets. Think energy grids, healthcare systems, financial institutions, and government agencies. An attack on these sectors causes significant real-world disruption and public panic, which gives attackers immense leverage. These organizations are often seen as “must-pay” targets for ransomware because downtime isn’t just an inconvenience—it can be a matter of public safety. As a result, groups that target critical infrastructure know they have a high chance of a successful, and lucrative, attack.
Just as you specialize in your field, many threat actors specialize in theirs. Groups like Qilin Ransomware are known for developing deep expertise in specific industries, such as healthcare or manufacturing. By focusing on one sector, they learn the common technologies, software, operational pressures, and compliance requirements unique to those businesses. This specialized knowledge allows them to craft more effective attack methods, from tailored phishing emails to exploiting industry-specific software vulnerabilities. They know exactly where the crown jewels are and how to pressure organizations into paying a ransom quickly to restore operations.
Not every attack is about money. For state-sponsored groups and hacktivists, target selection is often driven by political agendas and geographical boundaries. Groups like the Cyber Army of Russia Reborn launch attacks to advance a nation’s interests, disrupt foreign adversaries, or spread propaganda. Their targets are chosen based on their connection to an opposing government or political ideology. These geopolitically motivated cyberattacks can include espionage to steal state secrets, disruptive attacks on infrastructure, or misinformation campaigns designed to influence public opinion, making them a powerful tool in modern international conflicts.
While some attackers have specific targets in mind, many are simply opportunistic. They continuously scan the internet for low-hanging fruit: organizations with unpatched software, exposed databases, or weak credentials. For these actors, the target isn’t a specific company but a specific weakness. They use automated tools to find exploitable entry points and launch widespread campaigns, knowing that it’s a numbers game. This is why even small businesses can become victims. Attackers aren’t necessarily looking for you; they’re looking for the vulnerabilities you haven’t fixed yet, making proactive exposure management a critical line of defense.
It’s not just one single quality that makes a threat actor dangerous. It’s the combination of their skills, resources, and persistence that creates such a significant challenge for security teams. These groups operate like well-oiled machines, blending technical prowess with strategic patience to bypass defenses and achieve their objectives. Understanding what gives them an edge is the first step in building a more resilient security posture. They don’t just find holes in your defense; they actively work to create them, stay hidden, and adapt faster than most organizations can patch.
Top-tier threat actors, particularly state-sponsored groups, operate with the kind of funding and support that rivals legitimate tech companies. They aren’t lone hackers in a basement; they are organized teams of skilled developers, intelligence analysts, and operators. This backing allows them to purchase or develop zero-day exploits, create custom malware that evades standard detection, and sustain long-term campaigns that can last for months or even years. With significant resources at their disposal, they can conduct extensive reconnaissance and launch multi-faceted attacks designed to achieve specific strategic goals, whether it’s stealing intellectual property or disrupting critical infrastructure. The intelligence gathered by research teams like HiveForce Labs is crucial for tracking these advanced capabilities.
One of the biggest challenges in cybersecurity is that you can’t fight what you can’t see. The most dangerous threat actors are masters of stealth, using sophisticated techniques to blend in with normal network traffic and avoid detection. They often use “living-off-the-land” tactics, where they hijack legitimate system tools like PowerShell to carry out their attacks, leaving a minimal footprint. This makes it incredibly difficult for traditional security solutions to distinguish malicious activity from routine administrative tasks. By constantly refining their methods to get around security tools, these groups can remain hidden inside a network for long periods, quietly escalating privileges and exfiltrating data before anyone even knows they’re there.
Threat actors leverage the borderless nature of the internet to their advantage. Many operate from jurisdictions that are unwilling to cooperate with international law enforcement, creating safe havens where they can act with near impunity. This makes attribution and prosecution incredibly difficult, if not impossible. Groups like the Cyber Army of Russia Reborn can launch politically motivated attacks from one country while targeting another, knowing the geopolitical landscape protects them. They use anonymizing tools and complex infrastructure to obscure their origins, making it a real challenge for security teams to figure out who is attacking them and why. This operational freedom allows them to be bold and persistent in their campaigns.
The threat landscape is anything but static, and the best threat actors are incredibly agile. As soon as the security community develops a new defense or patches a vulnerability, these groups are already working on a workaround. They are persistent and adaptable, quickly changing their tactics, techniques, and procedures (TTPs) to overcome new obstacles. This constant evolution is fueled by a thriving underground economy where exploits and tools are shared and sold, accelerating innovation. For defenders, this means a reactive security strategy is doomed to fail. You need a platform that provides continuous threat exposure management to keep pace with attackers who never stop looking for the next open door.
Knowing which threat actors are out there is one thing; using that knowledge to build a stronger defense is another. Threat intelligence is the critical link that turns information into action. It provides the context you need to understand not just what your vulnerabilities are, but why they matter in the real world. Without it, you’re looking at a massive list of potential problems with no clear starting point. With it, you can see which vulnerabilities are being actively targeted, which threat actors are using them, and what their goals are.
This is how you move from a reactive cycle of patching and praying to a proactive strategy. Instead of trying to fix everything, you focus on fixing what matters most right now. A strong threat intelligence program helps you anticipate an attacker’s next move, allocate your resources where they’ll have the most impact, and make security decisions based on data, not guesswork. It’s about understanding the battlefield so you can build defenses that are tailored to the actual threats you face, not just the ones that exist in theory. This approach is the foundation of a modern threat exposure management program.
To defend against modern threats, you need to know how they operate today. Attack methods are constantly evolving. For example, the rise of Ransomware-as-a-Service (RaaS) has dramatically lowered the barrier to entry for cybercriminals. This trend allows less-skilled attackers to launch sophisticated campaigns, which means the volume and variety of threats are increasing.
Threat intelligence gives you a real-time view of these trends. It helps you understand which attack vectors are most popular and which industries are being targeted. By analyzing current attack patterns, you can adjust your defensive posture to counter the most prevalent threats. Instead of guessing where an attack might come from, you can use intelligence from sources like threat advisories to see what’s happening on the front lines and prepare your defenses accordingly.
Your security team can’t fix every single vulnerability. There are simply too many, and not all of them pose a genuine risk to your organization. The key is to focus on the ones that attackers are actually using. Attackers are getting better at hiding their actions and bypassing security tools, making it crucial to prioritize vulnerabilities that are currently being exploited in the wild.
Threat intelligence cuts through the noise by flagging vulnerabilities that have been weaponized by threat actors. It tells you which CVEs are part of an active exploit chain and which are being used by groups like LockBit or FIN7. This allows you to direct your remediation efforts to the critical few weaknesses that represent the most immediate danger, ensuring your team’s time and resources are spent on what truly matters.
Threat intelligence isn’t just about tracking known vulnerabilities; it’s about understanding the adversary’s playbook. Threat actors follow specific patterns, using a combination of tactics, techniques, and procedures (TTPs) to achieve their goals. By studying these behaviors, you can learn to recognize the signs of an attack even when the specific tools or malware strains are new.
Think of it as a field guide to your adversaries. High-quality intelligence from research teams like HiveForce Labs helps you understand the TTPs of various threat actors, from initial access methods to data exfiltration techniques. This knowledge allows you to build more resilient defenses that are designed to detect and disrupt the entire attack chain, not just a single indicator of compromise. It prepares you for what attackers will do tomorrow, not just what they did yesterday.
Ultimately, threat intelligence empowers you to make smarter, more effective security decisions. It replaces assumptions with evidence, allowing you to build a security strategy that is directly aligned with the current threat landscape. When you can show that a specific vulnerability is being actively exploited by a threat actor known to target your industry, it becomes much easier to justify the resources needed for remediation.
Utilizing threat intelligence allows for informed decision-making in your security strategy. It helps you answer critical questions: Which security controls do we need to strengthen? Where should we focus our monitoring efforts? How can we best train our employees to spot emerging threats? By grounding your security program in real-world data, you can build a more efficient, effective, and defensible posture against top-tier threats.
Knowing about the top threat actors is one thing, but knowing if your defenses can actually stop them is another. This is where you move from theory to practice. Instead of just hoping your security controls work, you can actively test them with Breach and Attack Simulation (BAS). Think of it as a continuous, automated sparring partner for your security team. BAS platforms safely run simulated attacks that mimic the real-world tactics, techniques, and procedures (TTPs) used by groups like Lazarus Group or FIN7.
This isn’t about pointing fingers or running a one-time penetration test that’s outdated the moment the report is printed. It’s about creating a constant feedback loop. By running these simulations, you get a clear, evidence-based picture of how your security stack performs against specific threats. You can see exactly where an attack path succeeds and where it fails, allowing you to make targeted improvements. This proactive approach is a cornerstone of modern adversarial exposure validation, helping you shift from a reactive posture to one that’s always prepared for the next threat.
Threat actors are creatures of habit. They often reuse attack methods that have proven successful. BAS allows you to leverage this predictability to your advantage. You can run simulations based on the well-documented TTPs found in frameworks like MITRE ATT&CK to validate that your security controls—from your firewall to your EDR—are configured correctly and behave as expected. It answers critical questions like, “Can we actually detect and block the specific PowerShell command used in a recent Conti ransomware attack?” This process ensures your defenses are effective against the common, everyday threats you’re most likely to face, turning intelligence into tangible proof of your security posture.
An incident response (IR) plan that only exists in a document is just a theory. The middle of a real crisis is the worst possible time to discover that your communication channels are unclear or your team doesn’t know how to access a critical tool. BAS provides a safe environment to conduct realistic fire drills. By simulating a breach, you can trigger your IR process and let your team practice their roles. This helps you identify gaps in your playbook, refine workflows, and build the muscle memory needed to respond swiftly and effectively when a real attack occurs. It’s about ensuring your people and processes are just as ready as your technology.
Vulnerability scanners are great at finding individual weaknesses, but they don’t always show you the full picture. A single low-risk vulnerability might seem insignificant on its own, but what if an attacker can chain it with a misconfiguration to gain full network access? BAS helps you connect these dots. It reveals the complex attack paths that adversaries could exploit by moving laterally across your environment. By simulating these multi-stage attacks, you can uncover critical security gaps that traditional scanning might miss, giving you a true understanding of your total attack surface and where your most significant risks lie.
You can’t improve what you don’t measure. BAS provides the hard data you need to track your security performance over time and make informed decisions. The results of each simulation offer concrete metrics on detection, prevention, and response times. This data helps you demonstrate the value of your security investments and prioritize future efforts. For example, if simulations consistently bypass a specific control, you know exactly where to focus your resources. This continuous cycle of testing, measuring, and hardening your defenses is what builds a truly resilient security program, one that adapts and grows stronger against evolving threats.
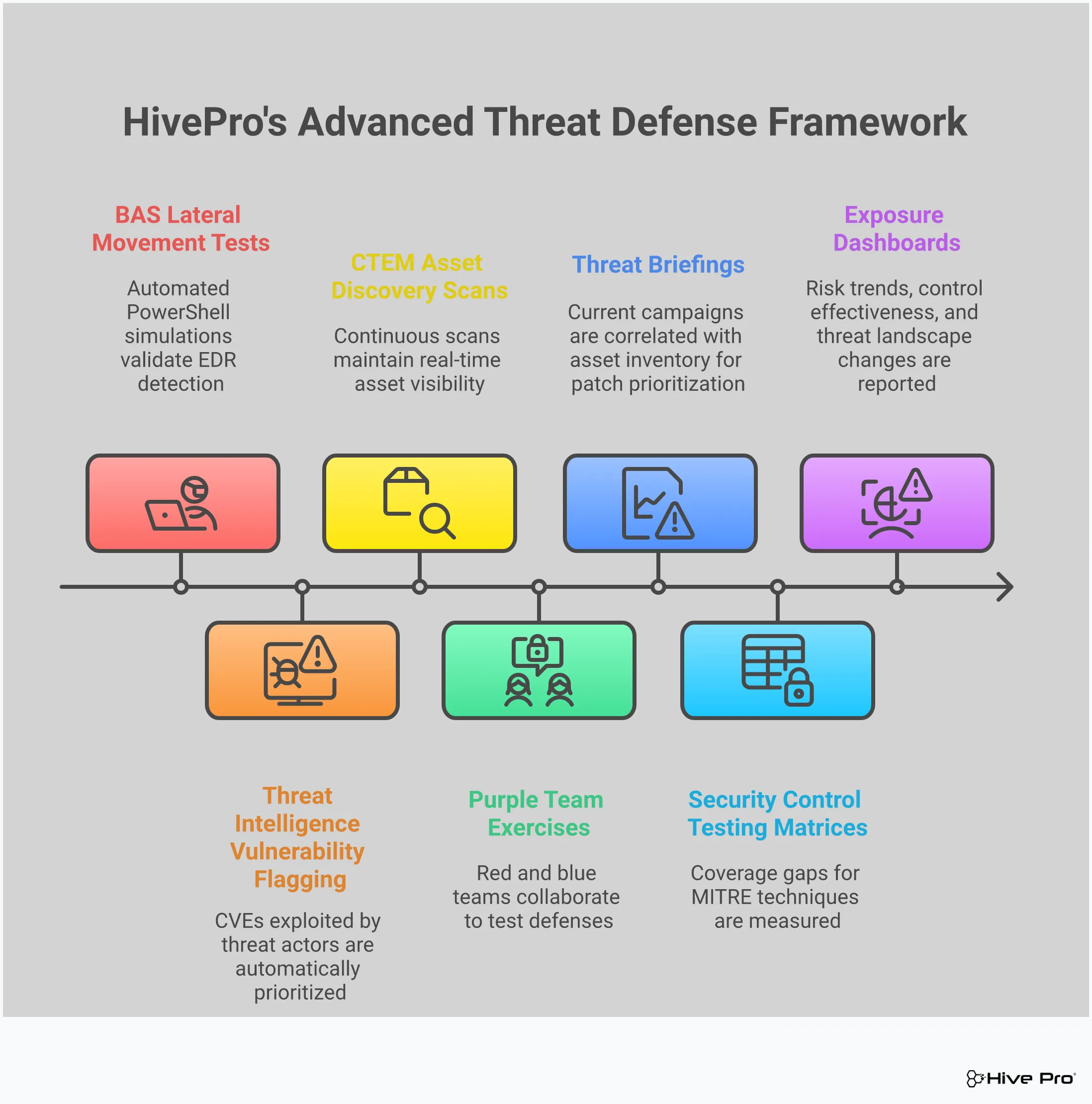
Knowing who the top threat actors are and how they operate is the first step. The next is building a security program that can stand up to their attacks. A modern defense isn’t a single product you set and forget; it’s a dynamic strategy that combines technology, proactive processes, and well-trained people. To effectively counter sophisticated groups like APT29 and Lazarus Group, you need to move beyond a reactive stance and build a resilient, multi-faceted defense.
A comprehensive approach means you’re not just waiting for alarms to go off. You’re actively hunting for weaknesses, validating your controls, and ensuring every part of your organization is prepared. This involves layering your technical defenses, continuously managing your threat exposure, deploying smart detection tools, and empowering your employees to be a line of defense, not a liability. By integrating these elements, you can create a security posture that is prepared for today’s threats and adaptable enough for tomorrow’s. The goal is to make your organization a much harder, and less attractive, target for even the most persistent adversaries.
Think of your security like a medieval castle. You wouldn’t rely on just a single wall to protect the crown jewels. You’d have a moat, a drawbridge, high walls, and guards at every gate. This is the principle behind a multi-layered security architecture, often called “defense-in-depth.” The idea is that if one security control fails, another is in place to stop or slow down an attack. A strong defense needs many layers, including protecting devices, controlling access, and having a solid incident response plan. This approach ensures that a single vulnerability doesn’t lead to a full-blown breach. A complete view of your Total Attack Surface Management is the foundation for building these effective layers.
A multi-layered defense is only effective if you know where your weaknesses are. That’s where Continuous Threat Exposure Management (CTEM) comes in. Instead of running a vulnerability scan once a quarter and getting a list of thousands of issues, CTEM is an ongoing cycle. It helps you continuously discover your assets, prioritize vulnerabilities based on real-world threats, and validate that your security controls are working. To fight advanced threats, organizations need a strong and ongoing security plan. By adopting a CTEM program with a platform like Uni5 Xposure, you shift from a reactive game of whack-a-mole to a proactive strategy focused on reducing your most critical exposures before they can be exploited.
While prevention is key, you must also assume that a determined attacker might eventually get through a layer of your defense. That’s why you need tools that can detect and respond to suspicious activity in real time. Technologies like Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) act as your digital security guards, constantly monitoring for signs of a compromise. But how do you know if they’re configured correctly and will actually work during an attack? That’s where Adversarial Exposure Validation comes in. By safely simulating real attacker techniques, you can test your detection and response capabilities, find gaps, and ensure your tools are ready for a real incident.
Your technology and processes can be perfect, but your security is only as strong as its weakest link—which is often a person. Threat actors are experts at social engineering and phishing because they know it works. That’s why you must continuously educate staff on how to spot and avoid phishing emails, suspicious links, and other common attack methods. This isn’t a one-time event but an ongoing cultural commitment. Regular, engaging security awareness training and phishing simulations can turn your employees from potential targets into a vigilant human firewall. When your team knows what to look for, they become a critical part of your multi-layered defense strategy.
Knowing who the top threat actors are and how they operate is one thing; stopping them is another. Building a resilient defense means implementing security controls that directly counter their most common tactics. While no single tool is a silver bullet, a layered approach that combines several key controls can significantly reduce your attack surface and make it much harder for adversaries to succeed. These controls are foundational for any modern security program and are particularly effective against the sophisticated groups we’ve discussed.
The goal is to create friction for attackers at every step of their operation. From the initial entry point to their attempts to move laterally and exfiltrate data, the right controls can detect, delay, and ultimately defeat an attack. This isn’t about building an impenetrable fortress—an impossible goal. Instead, it’s about creating a security architecture with enough depth and visibility to spot malicious activity early and respond effectively. The following controls represent critical layers in that architecture, each addressing a different facet of a modern cyberattack and working together to protect your organization. By implementing them thoughtfully, you shift from a reactive posture to a proactive one, making your environment a much less attractive target.
The old model of trusting everything inside the network perimeter is long gone. Adopting a “Zero Trust” approach is now standard practice, and it starts with the assumption that no user or device can be trusted by default. This framework requires strict verification for anyone trying to access resources, regardless of their location. A critical component of this is Multi-Factor Authentication (MFA), which requires users to provide multiple forms of identification. By enforcing MFA, you can shut down an attacker’s primary path to entry: stolen credentials. This simple step is one of the most powerful ways to protect against unauthorized access and lateral movement.
If an attacker does manage to breach your perimeter, your next goal is to contain them. Network segmentation is a powerful way to do this. By dividing your network into smaller, isolated zones, you can limit an intruder’s ability to move around and access sensitive data. Think of it like closing bulkhead doors on a ship to contain a leak. This strategy ensures that a compromise in one area doesn’t lead to a full-blown disaster. Pairing segmentation with continuous monitoring of network activity helps you spot unusual behavior quickly, allowing your team to investigate and respond before significant damage is done.
Your endpoints—laptops, servers, and mobile devices—are often the primary targets for malware and ransomware. Endpoint Detection and Response (EDR) tools act as a security detail for these devices. They go beyond traditional antivirus by continuously monitoring for suspicious activity and providing the visibility needed to investigate and neutralize threats in real time. When an EDR solution detects a potential attack, like a fileless malware execution or an unusual process, it can automatically isolate the affected endpoint to prevent the threat from spreading. This capability is essential for catching the advanced, evasive techniques used by groups like FIN7 and Lazarus Group.
Threat actors are experts at finding and exploiting unpatched vulnerabilities in software and systems. A reactive approach to patching simply isn’t fast enough to keep up. Instead, you need a proactive strategy that focuses on the vulnerabilities most likely to be exploited. This is where a risk-based vulnerability management program comes in. By combining vulnerability scan data with real-time threat intelligence, you can prioritize patching the flaws that pose an immediate danger to your organization. This allows you to focus your resources where they matter most, closing critical security gaps before attackers can find them.
Staying ahead of sophisticated threat actors isn’t about having a crystal ball; it’s about building a security strategy that’s as dynamic and adaptive as they are. The old approach of reactively patching vulnerabilities as they appear is no longer enough. To truly defend your organization, you need to shift to a proactive stance that anticipates attacker moves and continuously validates your defenses. This means focusing your efforts where they’ll have the most impact. By combining risk-based prioritization with continuous testing and up-to-the-minute intelligence, you can build a resilient security posture. Let’s walk through four key strategies that will help you move from a reactive cycle of firefighting to a proactive state of control over your threat exposure.
Your team is likely facing a mountain of vulnerabilities, and trying to patch everything at once is a recipe for burnout. The reality is, not every vulnerability carries the same weight. A risk-based approach helps you cut through the noise by focusing on the threats that matter most to your business. Instead of relying solely on CVSS scores, this strategy incorporates real-world threat intelligence, asset criticality, and exploitability. This allows you to prioritize vulnerabilities that are actively being targeted by threat actors and pose a genuine risk to your critical systems. It’s about working smarter, not harder, to reduce your exposure to the most imminent threats first.
How do you know if your security controls actually work against the tactics used by groups like Lazarus Group or FIN7? You have to test them. Regular security assessments are like a sparring session for your defenses—they help you find the weak spots before a real opponent does. This goes beyond annual penetration tests. By using tools for adversarial exposure validation, like Breach and Attack Simulation (BAS), you can continuously test your security posture against the latest attack techniques. These simulations show you exactly where your defenses hold up and where they fail, providing clear, actionable insights to strengthen your security before you face a real attack.
To defend against an enemy, you have to understand them. Maintaining a stream of up-to-date threat intelligence is crucial for understanding the latest hacker methodologies and emerging threats. This isn’t just about subscribing to a generic feed; it’s about getting contextualized information that tells you which threat actors are targeting your industry, what vulnerabilities they’re exploiting, and the specific tactics they’re using. High-quality threat advisories can transform your security strategy, helping you anticipate attacker moves, fine-tune your detection rules, and make informed decisions about where to focus your defensive resources. It’s the difference between guessing what might happen and knowing what to prepare for.
An incident response (IR) plan gathering dust on a shelf is useless. The best plans are living documents that are tested, refined, and adapted over time. Your IR plan should be a clear playbook that your team can execute under pressure, outlining roles, communication channels, and containment procedures. Regularly run tabletop exercises and simulations based on current threat intelligence to ensure your team knows exactly what to do when an attack happens. A well-rehearsed and adaptive incident response plan is vital for minimizing damage, restoring operations quickly, and learning from every incident to make your defenses even stronger for the next time.
What’s the real difference between a state-sponsored group like APT29 and a ransomware group like LockBit? Think of it in terms of their ultimate goal. A state-sponsored group like APT29 is playing a long game of espionage. Their mission is to gather intelligence, so they prioritize stealth and persistence, often remaining hidden in a network for months or years. A ransomware group like LockBit, on the other hand, is a business focused on quick profit. They want to get in, cause maximum disruption by encrypting files, and get paid as fast as possible, making their presence known very loudly.
My company isn’t in a critical sector. Do I still need to worry about these major threat actors? Yes, absolutely. While some groups do specialize in certain industries, many others are opportunistic. They use automated scanners to search for common weaknesses across the internet, and they don’t care if the vulnerable system belongs to a hospital or a small marketing agency. Furthermore, the rise of Ransomware-as-a-Service means that even less-skilled criminals can use sophisticated tools developed by top-tier groups, which dramatically increases the volume of threats for everyone.
Isn’t keeping my software patched the best way to defend against these groups? Patching is essential, but it’s not a complete strategy on its own. Security teams are overwhelmed with thousands of vulnerabilities, and it’s impossible to fix them all immediately. The key is to focus on what attackers are actually exploiting in the wild. A risk-based approach uses threat intelligence to identify the handful of vulnerabilities that pose a clear and present danger, allowing you to prioritize your efforts. It’s about fixing the most critical issues first, not just the ones with the highest CVSS score.
How can I use information about these threat actors to actually make my security program better? This information is the foundation for a proactive defense. Instead of just building generic walls, you can tailor your security controls to counter the specific tactics used by groups that might target you. You can use Breach and Attack Simulation to run controlled tests that mimic their methods, giving you real proof of whether your defenses can stop them. This turns abstract threat data into a practical, evidence-based plan for improvement.
Threat actors are always changing their tactics. How can my team possibly keep up? You’re right, it can feel like an impossible race. The key is to stop chasing individual threats and instead build an adaptive security program. This involves establishing a continuous cycle of discovering your attack surface, prioritizing your most critical exposures, and validating your defenses against real-world attack methods. By focusing on a resilient process rather than reacting to every new alert, you build a security posture that is prepared for both today’s threats and whatever comes next.