Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
Security teams are often buried under a mountain of vulnerability alerts. The daily reality is a constant scramble to patch the most critical issues, leaving a massive backlog of lower-priority—but still dangerous—exposures. This reactive cycle is exhausting and unsustainable. It’s like trying to empty the ocean with a bucket. What if you could move from constantly putting out fires to systematically preventing them? This is where building an effective exposure remediation automation process changes the game. It’s about creating a system that intelligently finds, prioritizes, and fixes vulnerabilities for you, allowing your team to finally get ahead of threats and focus on strategic defense.
Exposure remediation automation is about using technology to automatically find and fix security vulnerabilities across your digital environment. Think of it as a shift from a manual, often overwhelming, security checklist to a proactive system that handles threats for you. Instead of your team spending hours patching individual systems or correcting misconfigurations, an automated process can execute these fixes consistently and at machine speed. This approach allows your security operations to move from a reactive stance—putting out fires—to a proactive one where you systematically reduce your attack surface before attackers can exploit it. The goal is to make your security responses faster, more accurate, and scalable, freeing up your team for more complex challenges.
At its heart, exposure remediation automation involves a few key elements working together. It starts with a system that can continuously monitor your entire environment, from cloud infrastructure to on-premise servers, to find exposures. Once a vulnerability is detected, the system uses predefined rules and workflows to apply a fix automatically. This could be anything from applying a software patch to reconfiguring a firewall rule or revoking exposed credentials. The final piece is alerting and reporting, which notifies your team that a fix has been deployed and documents the action for compliance and review. It’s about creating a closed-loop system that constantly watches your total attack surface, identifies problems, and resolves them without manual intervention.
A common misconception is that automation aims to replace security experts. In reality, it’s designed to empower them. The most effective strategies blend automated actions with human oversight. Automation is perfect for handling high-volume, low-complexity tasks that consume a significant amount of your team’s time. This frees up your analysts to focus on what they do best: investigating complex threats, hunting for novel attack patterns, and making strategic decisions. Human experts are still essential for setting the rules, handling exceptions, and reviewing situations that require nuanced judgment. This partnership allows security teams to respond to threats much faster while ensuring that critical decisions still have a human touchpoint, especially when it comes to vulnerability and threat prioritization.
Implementing automated remediation isn’t just a technical upgrade; it’s a strategic business decision. The most significant benefit is the dramatic reduction in response time. Automation minimizes the critical window between when a vulnerability is discovered and when it’s fixed, giving attackers less time to act. This directly improves your overall security posture. Furthermore, automation ensures that fixes are applied consistently across your entire organization, which helps eliminate human error and maintain compliance standards. By handling repetitive tasks, it also allows you to reallocate your security team’s time and resources to more strategic initiatives. A platform that provides a unified view of cyber risks can make this process even more efficient, saving time and strengthening your defenses.
Putting automated remediation into practice isn’t about flipping a single switch. It’s a structured, cyclical process that ensures you’re acting on the right information at the right time. Thinking about it in five distinct stages helps break down the complexity and build a reliable system that moves from discovery to validation without missing a beat. This framework isn’t a linear checklist you complete once; it’s a continuous loop that gets smarter and more efficient over time. Each stage feeds into the next, creating a robust workflow that strengthens your security posture with every cycle. By following these steps, you can transform your remediation efforts from a reactive scramble into a proactive, well-oiled machine.
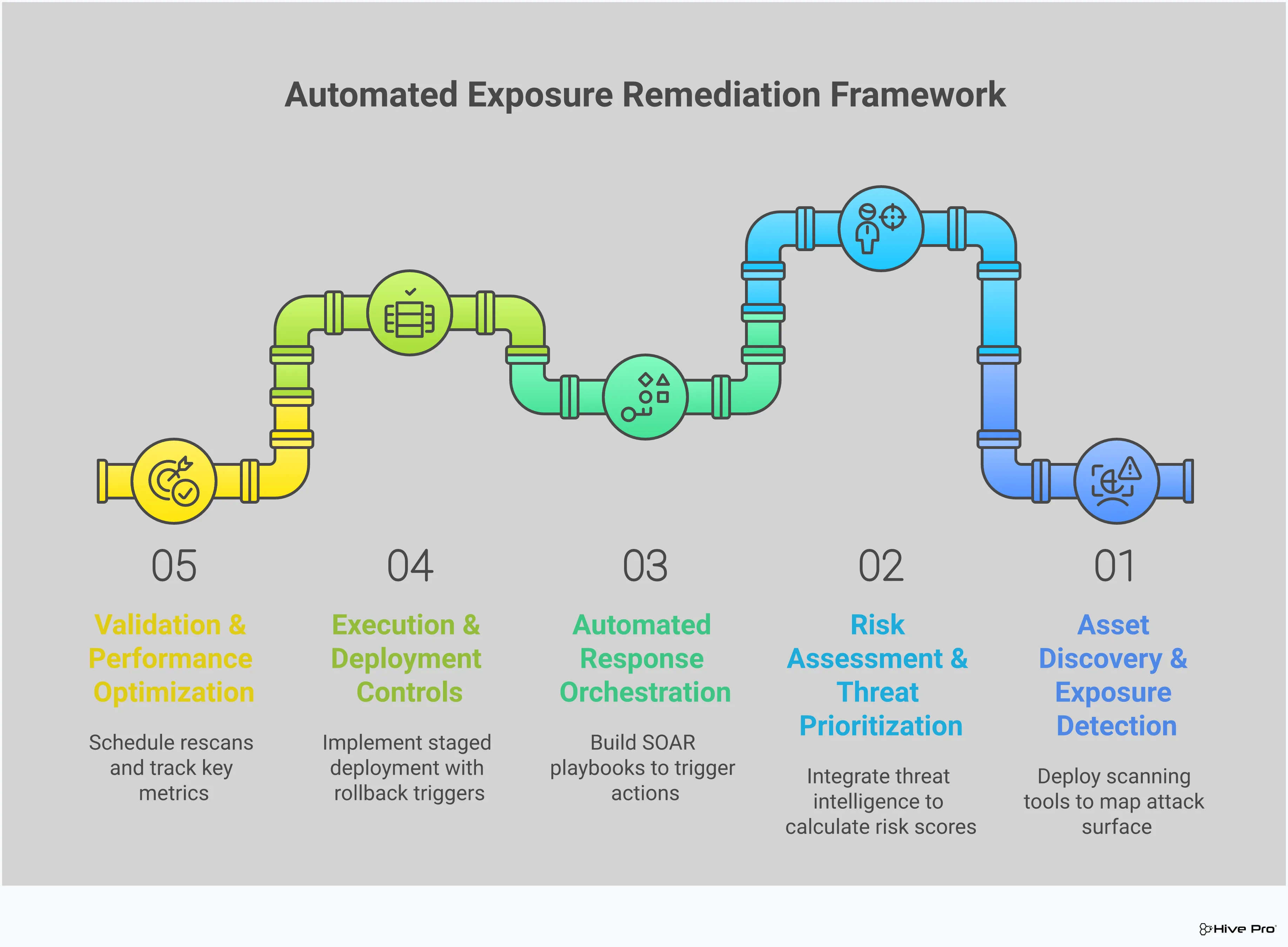
You can’t protect what you don’t know you have. That’s why the first stage is all about getting a complete and current picture of your environment. This means continuously discovering and mapping every asset across your total attack surface—from on-premise servers and employee laptops to cloud workloads and IoT devices. The goal is to create a comprehensive inventory that serves as your single source of truth. As Hive Pro’s platform shows, the key is to “continuously reveal your full attack surface, prioritize exposure based on real-world threats, and provide insights into potential vulnerabilities.” This isn’t a one-time scan; it’s an ongoing process that gives you the foundational visibility needed for any effective security program.
With full visibility, you can now figure out what actually matters. Not all vulnerabilities are created equal, and your team can’t fix everything at once. This stage is about cutting through the noise to focus on the exposures that pose a genuine threat to your business. By enriching vulnerability data with threat intelligence and business context, you can perform a more accurate vulnerability and threat prioritization. As experts at Brinqa point out, tracking key performance indicators (KPIs) and key risk indicators (KRIs) helps “assess program effectiveness, guide prioritization, and demonstrate remediation progress to stakeholders.” This data-driven approach ensures your automation efforts are aimed at the most critical issues first.
Now that your priorities are clear, it’s time to build your playbook. This stage is where you define the rules of engagement for your automation. Based on the risk level, asset criticality, and threat context, you can create specific “if-then” workflows. For example, if a high-severity vulnerability is found on a public-facing server, the workflow might automatically create a patch ticket and notify the asset owner. The idea is to have an active response system that can “automatically remediate exposures for you,” as noted by Palo Alto Networks. This planning phase is crucial for building trust in the system and ensuring automation acts as a precise tool aligned with your operational needs.
This is where the plan springs into action. When a predefined trigger is met, the automation engine executes the remediation task, whether that’s applying a patch, updating a firewall rule, or changing a system configuration. The biggest advantage here is speed. Automation closes the gap between detection and resolution, shrinking the window of opportunity for attackers. As ConnectSecure highlights, “Automation’s real-time reaction minimizes the time needed to deal with security issues.” Instead of waiting days or weeks for manual intervention, you can resolve exposures in minutes, which fundamentally improves your security posture and frees up your team to focus on more strategic initiatives.
The job isn’t done until you’ve confirmed the fix worked. This final stage closes the loop by validating that the vulnerability has been successfully remediated and that the fix didn’t introduce any new problems. This typically involves rescanning the asset and documenting the outcome. Tracking metrics like Mean Time to Remediate (MTTR) is critical here, as it offers “insights into the effectiveness of the remediation process.” This validation step not only neutralizes the immediate threat but also generates valuable data. You can use these insights to refine your automation playbooks, report progress to leadership, and continuously improve the efficiency of your entire exposure management program.
Your tech stack is the engine that powers your entire automation strategy. Having the right tools isn’t just about buying the latest software; it’s about creating a cohesive ecosystem where different systems can communicate and act in concert. A well-chosen set of technologies will help you detect threats faster, automate responses accurately, and give your team the visibility it needs to make smart decisions. Without a solid foundation of the right platforms and solutions, even the best-laid automation plans can fall flat.
The key is to find tools that not only solve an immediate problem but also integrate smoothly with your existing infrastructure. Think of it as building a team—each player needs to have a specific skill set, but they also need to be able to work together seamlessly to win the game. From orchestrating complex workflows to securing your cloud assets, each piece of technology plays a vital role in building a robust and effective automated remediation process.
Security Orchestration, Automation, and Response (SOAR) and Endpoint Detection and Response (EDR) platforms are foundational for automating your remediation workflows. SOAR platforms act as the central nervous system, connecting your various security tools—like firewalls, SIEMs, and threat intelligence feeds—into a single, coordinated system. They allow you to build automated playbooks that execute a series of actions when a specific type of threat is detected.
When you’re evaluating these tools, focus on a few key areas. First, how well do they connect with your other systems? Strong integration capabilities are non-negotiable. You also want flexibility in how you can set up your response plans, as a one-size-fits-all approach rarely works in security. Finally, consider if the platform can grow with your organization. Your needs will change, and your SOAR platform should be able to scale with you.
As more infrastructure moves to the cloud, your automation strategy needs to follow. Cloud environments are dynamic and complex, making manual security checks nearly impossible to keep up with. This is where cloud-native security solutions and configuration management tools come in. They can automatically enforce security policies and remediate issues without human intervention.
For example, you can build an automated system in AWS to find S3 storage buckets that aren’t encrypted and then fix them on the spot. This kind of automation helps you maintain data security and follow compliance rules without requiring your team to perform constant manual audits. By automating these routine but critical tasks, you free up your security professionals to focus on more complex threats.
For your automation efforts to be truly effective, your tools need to talk to each other. Seamless integration is the glue that holds your entire remediation process together. This means looking for platforms with robust APIs and the ability to provide a unified view of your security posture. When your systems are siloed, you create blind spots and slow down your response times.
By adopting a platform approach, you can finally start measuring what matters: prevention over reaction and outcomes over activity. Instead of tracking how many alerts your team closed, you can measure how many potential breaches were automatically prevented. A platform like Hive Pro’s Uni5 Xposure brings all your exposure data into one place, making it easier to see the full picture and build intelligent, cross-functional automation workflows.
Artificial intelligence and machine learning are transforming exposure remediation from a reactive task to a proactive strategy. These technologies can analyze massive amounts of data to identify patterns, prioritize threats with incredible accuracy, and even predict where the next attack might come from. This allows you to move beyond simple, rule-based automation and create a more intelligent and adaptive defense.
The Uni5 Xposure platform is designed for this dynamic reality, providing a constant feedback loop that helps you stay ahead of attackers. It enables total asset exposure visibility by combining the strength of the HivePro Uni5 platform with actionable recommendations for remediation. This approach not only streamlines your security operations but also enhances cross-functional collaboration by providing a unified platform for real-time data sharing and streamlined threat exposure management.
Jumping into automation without a plan is like setting sail without a map. You might make some progress, but you’re unlikely to reach your destination efficiently. A solid strategy ensures your automated remediation efforts are targeted, effective, and aligned with your organization’s security goals. It transforms automation from a simple tool into a core component of your security posture. This means thinking through your objectives, defining your processes, and preparing your team for a new way of working. A well-crafted strategy provides the framework you need to move from a reactive state of vulnerability management to a proactive model of exposure reduction, giving your team the confidence to act decisively.
Before you automate a single task, you need to define what success looks like. What are you trying to achieve? Your objectives should be specific and measurable. Are you aiming to reduce the Mean Time to Remediate (MTTR) for critical vulnerabilities by 50%? Do you want to free up your security analysts to focus on complex threat hunting instead of routine patching? Automated remediation uses technology to quickly find and fix cybersecurity problems, moving away from manual security work to achieve faster and more accurate responses. Clearly defined goals will guide your implementation, help you choose the right tools, and make it easier to demonstrate the value of your automation program to leadership.
With your objectives in place, it’s time to map out the “how.” Your workflows are the step-by-step processes that your automation will follow. This involves defining the triggers, actions, and conditions for every automated task. For example, a workflow might be triggered when a new asset is discovered on your network or when a vulnerability with a high-risk score is detected. The subsequent actions could include creating a ticket in your IT service management system, applying a virtual patch, or isolating the affected device. A critical part of this process is determining the right level of human oversight. Your workflows should clearly outline when an action requires manual approval versus when it can be fully automated, ensuring you maintain control while gaining efficiency.
Implementing automated remediation doesn’t happen overnight—it requires a thoughtful allocation of time, budget, and personnel. You need a realistic roadmap that accounts for the initial setup, configuration, and ongoing maintenance of your automation platform. Adopting a “crawl, walk, run” approach is a great way to manage this process. Start with low-risk, high-impact automations, like patching non-critical systems or generating reports. As your team gains confidence and you refine your workflows, you can gradually move on to more complex and critical tasks. This incremental approach helps you secure early wins, demonstrate value quickly, and build momentum for your program without overwhelming your team or your budget.
Technology is only as effective as the people who use it. Automation will change your team’s day-to-day responsibilities, shifting their focus from manual tasks to more strategic oversight and exception handling. Proper training is essential to ensure a smooth transition and successful adoption. Your team needs to understand not just how to operate the new tools but also the logic behind the automated workflows. This builds trust in the system and empowers them to manage it effectively. Platforms like HivePro’s Uni5 Xposure often include comprehensive training programs to get your team up to speed, ensuring they have the skills and confidence to make the most of your automation strategy.
Once you have a strategy, the real work of implementation begins. How you roll out your automation is just as important as the tools you choose. A rushed or poorly planned implementation can create more problems than it solves, leading to system disruptions, team frustration, and a lack of trust in the new process. The goal is to integrate automation smoothly into your existing security operations, not to overhaul everything overnight. A thoughtful approach builds a foundation for a program that can scale effectively and earn the trust of both your technical teams and business leadership.
By following a few key best practices, you can ensure a successful transition that minimizes risk and maximizes results. This means starting with a manageable scope, defining exactly how your automation should behave, and building in checks and balances to verify every action. A thoughtful approach also involves considering your compliance obligations and ensuring every automated step is documented and auditable. This careful planning helps build a resilient and effective automated remediation program that your team can rely on, transforming your threat exposure management from a reactive chore into a proactive strength.
Jumping into full-scale automation across your entire environment is a recipe for disaster. Instead, adopt an incremental “crawl, walk, run” approach. Begin with a pilot program focused on a low-risk, high-impact area. For example, you could start by automating the patching of vulnerabilities on a set of non-critical internal servers. This allows your team to learn the system, refine workflows, and troubleshoot any issues in a controlled setting. A phased rollout helps you demonstrate early wins, building confidence and securing buy-in from stakeholders before you expand the program to more critical assets and complex remediation tasks.
Automation isn’t magic—it’s logic. It only works as well as the instructions you provide. To make it effective, you need to establish a clear framework. This starts with defining the rules, which are the specific conditions that trigger an automated action. For instance, a rule might be to initiate remediation for any vulnerability with a CVSS score above 9.0 discovered on an external-facing web server. Next, you need documented procedures, which are the precise, step-by-step actions the system takes in response. This ensures every action is predictable, consistent, and aligned with your security policies, leaving no room for ambiguity.
Deploying a fix doesn’t mean the job is done. You have to confirm that the remediation was successful and didn’t introduce any new issues. Your implementation plan must include robust testing and validation protocols. After an automated fix is applied, the system should automatically trigger a re-scan of the asset to verify the exposure is no longer present. This closed-loop process provides concrete proof that your automation is working. It’s also critical to have a documented rollback plan. If a patch or configuration change causes an unexpected problem, you need an automated or manual procedure to revert it quickly, ensuring business continuity.
Automation can be a huge asset for compliance, but only if it’s implemented correctly. Every automated action must be logged to create a clear, unchangeable audit trail. This is non-negotiable for meeting regulatory requirements like PCI DSS, HIPAA, or GDPR. Your system should record what remediation was performed, why it was triggered, when it happened, and whether it was successful. This documentation is essential for demonstrating due diligence to auditors. Furthermore, ensure your team understands how these new automated processes align with your organization’s compliance framework and how their roles may shift toward overseeing and verifying these systems.
Implementing an automated remediation process isn’t a “set it and forget it” task. To get the most out of your efforts, you need to continuously monitor performance, measure your results, and refine your approach. This is how you demonstrate the value of your program, justify your resource allocation, and stay ahead of threats. By tracking the right metrics, you can turn raw data into a clear story of progress and identify exactly where you can make your process even more efficient and effective.
A strong measurement framework helps you answer critical questions: Are we fixing vulnerabilities faster? Are we reducing our overall risk? Is the automation working as intended without causing disruptions? Answering these questions with hard data is key to building confidence in your strategy and gaining buy-in from leadership. It transforms your remediation program from a cost center into a strategic asset that actively protects the business. This ongoing optimization ensures your automated defenses remain sharp and aligned with your security goals, proving their worth every step of the way.
Your first step is to decide what success looks like and how you’ll measure it. Key Performance Indicators (KPIs) are the specific, quantifiable metrics you’ll use to gauge the effectiveness of your automation. These aren’t just numbers for a dashboard; they are vital for guiding your vulnerability and threat prioritization and demonstrating progress to stakeholders.
Start by selecting a handful of KPIs that align with your program’s goals. You might track the percentage of critical vulnerabilities remediated within a specific timeframe, the reduction in your overall attack surface over time, or the number of assets covered by your automated workflows. These metrics provide a clear, data-backed view of your program’s health and its impact on your organization’s security posture.
Speed is everything in cybersecurity. The longer an exposure exists, the larger the window of opportunity for an attacker. That’s why tracking response times, particularly Mean Time to Remediate (MTTR), is so important. MTTR measures the average time it takes your team to fix a vulnerability from the moment it’s discovered. A consistently decreasing MTTR is one of the strongest indicators that your automation strategy is working.
Effective vulnerability management metrics translate raw scan data into actionable insights about your team’s efficiency. Beyond MTTR, consider tracking Mean Time to Detect (MTTD) to see how quickly you’re identifying new threats. Using a unified platform helps you monitor these timelines closely, spot bottlenecks, and fine-tune your automated responses to act even faster.
Automation is meant to make your life easier, not create new problems. That’s why quality control is essential. You need to ensure that your automated fixes are being deployed correctly and aren’t causing unintended operational disruptions. This involves tracking metrics like the success rate of automated patches, the number of rollbacks required, and any system performance issues reported after a deployment.
By aggregating these KPIs, you can track the maturity of your remediation activities and pinpoint gaps in your processes or controls. For example, a high rollback rate might indicate that your pre-deployment testing needs to be more thorough. These quality checks ensure your automation is not only fast but also reliable and safe, maintaining system stability while improving security.
The data you collect from your KPIs, response times, and quality control checks shouldn’t just sit in a report. It should fuel a cycle of continuous improvement. Regularly review your metrics to understand what’s working well and where there are opportunities to refine your workflows, rules, and playbooks. This iterative process is what turns a good automation program into a great one.
To ensure your program meets high standards, align your KPIs with recognized security frameworks like those from NIST or CIS. This helps you benchmark your performance against industry best practices and demonstrates a mature approach to risk management. By constantly learning from your data and adapting your strategy, you can build a resilient, future-proof remediation process that evolves with the threat landscape.
Switching to an automated remediation process is a big step, and like any major operational shift, it comes with its own set of challenges. But don’t worry—these are common hurdles with clear solutions. By anticipating them, you can create a smoother transition for your team and your tech stack, ensuring your automation strategy succeeds from day one. Let’s walk through some of the most frequent obstacles and how to handle them.
Let’s be real: integrating new tools into your existing security stack can be tricky. You have systems that are already working together, and dropping in a new automation platform can feel like a complex puzzle. The key is to remember that implementing automated remediation doesn’t happen overnight. A great way to approach this is with an incremental crawl, walk, run approach that allows you to build confidence and work out kinks along the way. Platforms like Hive Pro’s Uni5 Xposure are designed for this dynamic reality, providing a constant feedback loop that helps you stay ahead of attackers and integrate seamlessly into your workflow.
A common concern is that setting up automation will drain team resources that are already stretched thin. In reality, the opposite is true. While there’s an initial investment of time, automated remediation ultimately frees up your team from repetitive, manual tasks. This allows them to focus on more strategic initiatives that require their expertise. Automation’s real-time reaction minimizes the time needed to deal with security issues, which improves your overall security posture. A unified platform enhances this by giving different teams—from SecOps to IT—a single source of truth, streamlining communication and making everyone’s job easier.
New technology can sometimes be met with skepticism. Your team might worry that automation will make their roles obsolete or that the system will make mistakes they’ll have to clean up. It’s important to address these concerns head-on. Reassure your team that even with automation, human experts are still very important for understanding tricky situations and making final decisions. Frame the change not as a replacement, but as a powerful tool that helps them do their jobs better. Adding new technology and ways of working can seem hard, but with a good plan and clear communication, it becomes much more manageable for everyone involved.
How do you ensure that automating remediation doesn’t lead to a drop in quality or create new risks? The answer lies in measurement and validation. Automated remediation uses technology to quickly find and fix cybersecurity problems, but you need to verify that it’s working as intended. This is where vulnerability management metrics become essential. By tracking key performance indicators (KPIs) like Mean Time to Remediate (MTTR) and vulnerability recurrence rates, you can get a clear picture of your program’s effectiveness. This data-driven approach ensures your automated processes are not just fast, but are also consistently meeting your high security standards.
Building an automated remediation process isn’t a one-and-done project. The threat landscape is constantly shifting, and your organization is always growing. To keep your defenses strong, your automation strategy needs to be built for the long haul. Future-proofing means creating a system that can adapt to new technologies, scale with your business, and get smarter over time. It’s about moving from a rigid, reactive setup to a flexible, proactive one that can handle whatever comes next. By thinking ahead, you ensure your investment in automation continues to pay off, keeping your security posture robust and resilient against emerging threats.
The tools and technologies in cybersecurity are in a constant state of evolution. What’s cutting-edge today could be standard practice tomorrow. A future-proof automation process relies on a platform that can adapt and integrate new capabilities as they emerge. Look for solutions that offer more than just basic automation, providing comprehensive features like total infrastructure scanning and security assessment orchestration. A platform like Uni5 Xposure is built to provide total asset exposure visibility, giving you a single, unified view of your environment. This approach ensures you aren’t left behind as technology advances, allowing you to manage your full attack surface effectively.
As your organization grows, so does its attack surface. More employees, more devices, and more applications mean more potential exposures. Your automated remediation process must be able to scale seamlessly to handle this increased volume and complexity without missing a beat. Scalability isn’t just about handling more data; it’s about maintaining speed and efficiency. An effective automated system enables rapid responses to vulnerabilities, no matter how many you’re dealing with. This real-time reaction is critical for minimizing the time attackers have to exploit a weakness, ensuring your security posture remains strong as you expand.
Your automation is only as effective as the information it acts on. Stale or generic data leads to weak, ineffective responses. To make your automation truly powerful, you need to fuel it with a steady stream of high-quality, real-time threat intelligence. Integrating a service like HiveForce Labs into your workflow empowers your team to build resiliency against threats with greater speed and confidence. This allows your system to move beyond simply reacting to known vulnerabilities and start proactively defending against the tactics and techniques being used by attackers right now.
Simple automation follows a script: if X happens, do Y. Advanced orchestration is about creating a symphony. It involves coordinating all your different security tools and processes into a single, cohesive response. This creates a dynamic feedback loop where your system continuously learns and adapts based on new information and the results of its actions. The goal is to build a system designed for today’s dynamic reality, one that helps you stay ahead of attackers instead of just reacting to them. This approach, often a core component of Continuous Threat Exposure Management (CTEM), transforms your security from a set of disconnected actions into an intelligent, self-improving defense strategy.
Is automated remediation just about patching vulnerabilities? Not at all. While patching is a huge part of it, a strong automation strategy addresses a much wider range of security exposures. Think of it as a system for correcting any weakness in your security posture. This includes fixing misconfigurations in your cloud services, enforcing security policies on new devices, and even revoking compromised credentials automatically. The goal is to systematically reduce your entire attack surface, not just apply software updates.
Will automation make my security team’s jobs obsolete? Absolutely not. The goal of automation is to empower your team, not replace it. It acts as a force multiplier by handling the repetitive, high-volume tasks that often consume your analysts’ time. This frees them up to focus on the work that truly requires human expertise, like complex threat hunting, investigating sophisticated incidents, and making strategic security decisions. Your team’s knowledge is still essential for setting the rules, managing exceptions, and providing the critical oversight that automation needs to be effective.
How do I get started with automation without disrupting our operations? The key is to start small and build momentum. You don’t want to flip a switch and automate everything at once. Begin with a pilot program focused on a low-risk area, such as patching a group of internal development servers or fixing a common misconfiguration on non-critical assets. This allows your team to learn the new tools, refine your workflows, and build confidence in the process within a controlled environment. Once you’ve demonstrated success there, you can gradually expand your automation to more critical systems.
What happens if an automated fix accidentally breaks a critical system? This is a valid and important concern, which is why a thoughtful implementation includes strong safeguards. Before any automated fix is deployed in a live environment, it should be thoroughly tested in a staging area that mirrors your production setup. More importantly, every automated workflow should have a clear and documented rollback plan. This ensures that if a change causes an unexpected issue, you have a quick and reliable procedure to revert it, minimizing any impact on business operations.
How can I measure the success of our automation program? Success should be measured with clear, data-driven results that you can share with leadership. The most important metric to track is your Mean Time to Remediate (MTTR), which is the average time it takes to fix a vulnerability after it’s discovered. A consistently decreasing MTTR is a powerful indicator that your program is working. You can also track the percentage of vulnerabilities fixed without manual intervention and the overall reduction in your organization’s risk score over time.