Comprehensive Threat Exposure Management Platform
Threat actors are never deterred by a generic risk score. We tailor prioritization according to your threat exposure to fulfill the most important cyber security mandate: threat prevention.
Is your vulnerability exploitable? Wormable? A zero-day? Are threat actors actively exploiting? We look at all of this and more to prioritize what matters.
Organizations lacking advanced vulnerability prioritization rely on generic scoring systems that do not account for specific threat landscapes or real-time threat intelligence. This results in a prioritization that overlooks crucial factors such as wormability, zero-day status, and active discussions on the dark web, leading to inefficient and potentially ineffective remediation efforts.
Without the ability to monitor and analyze threat actor behavior and cluster vulnerabilities based on their exploitability, organizations operate reactively. They struggle to anticipate which vulnerabilities are most likely to be exploited, missing the opportunity to issue tailored Priority Incident Response (PIR) alerts and prepare for specific threats affecting their business vertical and geography.

Traditional vulnerability management systems often rely on static scoring and do not adapt to changing threat scenarios or the effectiveness of existing controls. This approach fails to dynamically reprioritize vulnerabilities as new data becomes available from simulations or changes in the threat landscape, potentially leaving critical vulnerabilities unaddressed.

Organizations without sophisticated vulnerability analysis tools, such as contextual assessments and continuous threat intelligence updates, frequently encounter high rates of false positives. This not only drains resources but also diverts attention from genuine threats, reducing the overall efficiency and accuracy of security operations.
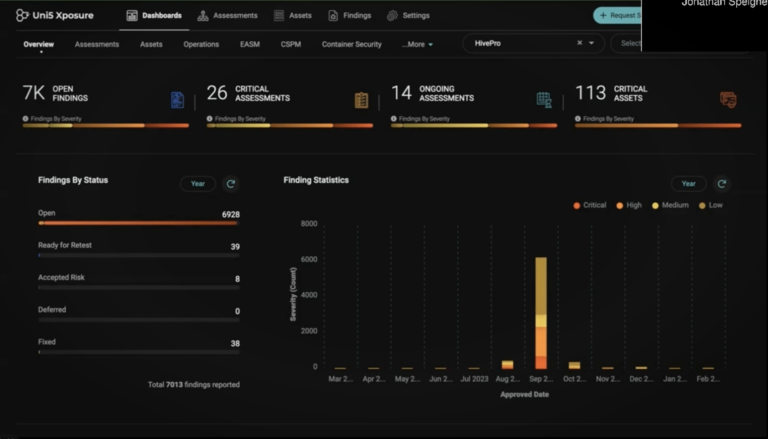
Organizations lacking advanced vulnerability prioritization rely on generic scoring systems that do not account for specific threat landscapes or real-time threat intelligence. This results in a prioritization that overlooks crucial factors such as wormability, zero-day status, and active discussions on the dark web, leading to inefficient and potentially ineffective remediation efforts.

Without the ability to monitor and analyze threat actor behavior and cluster vulnerabilities based on their exploitability, organizations operate reactively. They struggle to anticipate which vulnerabilities are most likely to be exploited, missing the opportunity to issue tailored Priority Incident Response (PIR) alerts and prepare for specific threats affecting their business vertical and geography.

Traditional vulnerability management systems often rely on static scoring and do not adapt to changing threat scenarios or the effectiveness of existing controls. This approach fails to dynamically reprioritize vulnerabilities as new data becomes available from simulations or changes in the threat landscape, potentially leaving critical vulnerabilities unaddressed.

Organizations without sophisticated vulnerability analysis tools, such as contextual assessments and continuous threat intelligence updates, frequently encounter high rates of false positives. This not only drains resources but also diverts attention from genuine threats, reducing the overall efficiency and accuracy of security operations.
CVSS or EPSS scores alone aren’t cutting it. No generic framework is good enough. Holistic risk assessments take into account active threats, your exposure points to threats, and the potential of your controls to defend.
Uni5 Xposure sharpens focus by filtering out the noise of false positives, duplicate alerts, and de-prioritizing low risks. This means your team spends time where it counts, enhancing the effectiveness of your security measures.
Stay Nimble, Stay Secure: Adapt with AgilityAs threats evolve, so does Uni5 Xposure. By dynamically adjusting vulnerability priorities based on fresh simulation insights and control checks, your defenses are always up-to-date and focused.
Anticipate, Don't React: Proactive Threat InsightsLeveraging extensive CVE data, threat intelligence and threat actor tracking, Uni5 Xposure helps you anticipate and prepare for threats before they strike, enabling a proactive rather than reactive security posture.
Master Your Threat Landscape, Make Smarter DecisionsWith detailed insights from over 210,000 CVEs, 270+ threat actor profiles, IoCs, TTPs and more, we arm you with the right intelligence to fix what matters, bolster your defenses and evade threats.
Book a free demo and find out more about how Hive Pro can double your operational efficiency
Book a DemoDiscover everything about Hive Pro features, benefits, and more.