Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
For a detailed threat digest, download the PDF file here
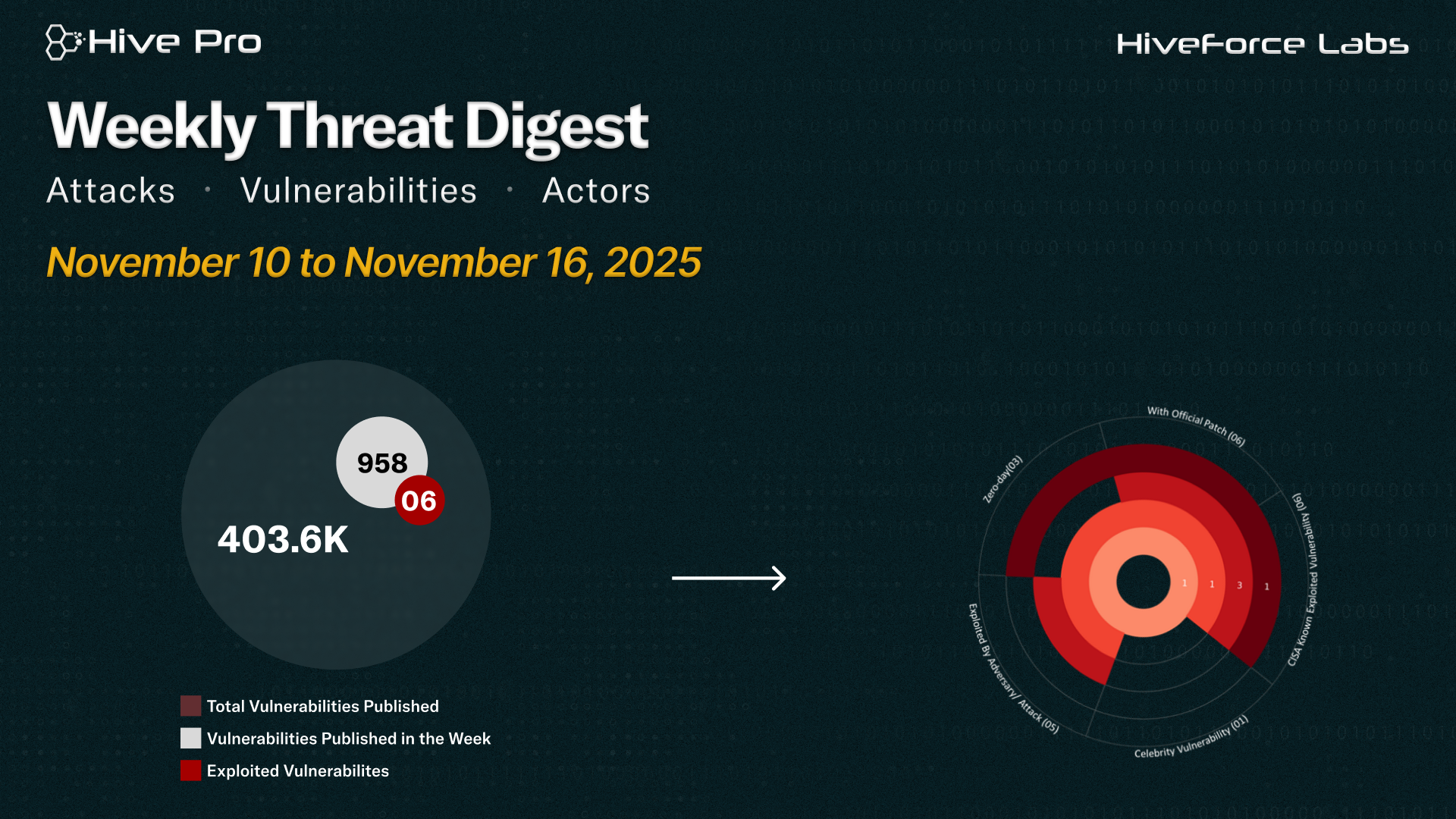
HiveForce Labs has recently made significant advancements in identifying cybersecurity threats. Over the past week, four major attacks were detected, six critical vulnerabilities were actively exploited, and three threat actor were closely monitored, reflecting an alarming escalation in malicious activities.
Microsoft’s November 2025 Patch Tuesday fixed 63 flaws, including a Windows Kernel zero-day, making rapid patching and verified ESU coverage critical to prevent remote attacks and privilege escalation. UNC6485’s exploitation of CVE-2025-12480 shows how a single Triofox flaw can enable full system takeover, letting attackers create rogue admins, deploy remote-access tools, and steal data, spotlighting the growing risks in remote-access and file-sharing platforms.
Additionally, APT41 exploited critical vulnerabilities to infiltrate a U.S. policy non-profit in April 2025, deploying stealthy tools for espionage in line with China’s ongoing targeting of U.S. policy institutions. Lazarus is targeting aerospace and defense firms with a macro-laden Word file that deploys an upgraded Comebacker backdoor, using multi-stage, memory-resident, and encrypted tactics to support stealthy espionage. These rising threats pose significant and immediate dangers to users worldwide.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.