Comprehensive Threat Exposure Management Platform
Running a vulnerability scan can feel like opening Pandora’s box. You’re suddenly faced with a report listing thousands of potential weaknesses, and the pressure to “fix everything” is immense. But this approach is a recipe for burnout, leaving your team chasing low-impact issues while a real threat slips through the cracks. A truly effective security program isn’t about eliminating every single vulnerability; it’s about systematically reducing risk. So, what is vulnerability management when it’s done right? It’s a continuous, intelligent process that helps you cut through the noise, focus on the threats that actually matter, and proactively strengthen your defenses before an attacker finds a way in.
Let’s break it down. At its core, vulnerability management is the ongoing process your team uses to find, evaluate, report on, and fix security weaknesses across your entire IT environment. Think of it as a continuous cycle, not a one-off project with a start and end date. It’s about proactively identifying potential entry points for attackers—like unpatched software, misconfigured systems, or insecure code—before they can be exploited. This isn’t just about running a scanner and getting a long list of problems. A solid vulnerability management program gives you a clear, organized way to understand your security posture and systematically reduce your exposure to threats. It’s a fundamental practice for any organization that wants to protect itself from both known and emerging cyber threats. By making it a core part of your security operations, you move from a reactive stance of putting out fires to a proactive one where you’re actively preventing them from starting. This continuous loop of discovery, prioritization, and remediation is what keeps your defenses strong and resilient against an ever-changing threat landscape. It provides the critical visibility you need to make informed decisions, allocate resources effectively, and demonstrate due diligence to stakeholders and regulators. It’s less about achieving a perfect, vulnerability-free state and more about maintaining a manageable and acceptable level of risk.
The main goal is simple: to reduce your organization’s risk of a cyberattack or data breach. It’s about systematically closing the windows and locking the doors that attackers could use to get in. This is an important distinction from patch management. While patching is a critical part of the process, the goal of vulnerability management isn’t just to apply every single update available. Instead, it’s about using a risk-based approach to prioritize which weaknesses to fix first. A mature strategy focuses on addressing the vulnerabilities that pose the greatest threat to your business, helping you use your team’s time and resources more effectively.
Vulnerability management is a foundational pillar of any modern cybersecurity program. It’s not a siloed task for one team; it’s a continuous process that provides critical intelligence to your entire security operation. The data gathered from identifying and assessing vulnerabilities informs everything from your incident response plans to your overall risk management strategy. Failing to integrate these efforts with your other security tools is a major oversight. Your vulnerability management program acts as the “ground truth” for your security posture, giving you a clear picture of your weaknesses so you can build a stronger, more resilient defense across the board with a unified platform.
Let’s be honest: vulnerability management can feel like a never-ending game of whack-a-mole. A new vulnerability pops up, you knock it down, and two more appear. It’s easy to get stuck in a reactive cycle, just trying to keep up. But shifting your perspective is key. Prioritizing vulnerability management isn’t just about patching software; it’s about fundamentally reducing your organization’s risk. It’s the difference between constantly putting out fires and building a fire-resistant structure in the first place. A strong program moves you from a state of guessing what might be a threat to confidently taking action on what truly matters.
By making vulnerability management a priority, you’re doing more than just checking a box for the security team. You’re actively protecting the business from disruption, safeguarding its reputation, and ensuring you meet the standards expected by customers and regulators. It’s a core function that helps you stay ahead of attackers who are actively looking for easy ways in. A mature approach to threat exposure management provides a unified view of your cyber risks, allowing you to focus your limited time and resources on the vulnerabilities that pose an imminent threat. This proactive stance is what separates resilient organizations from those who are just one exploit away from a major incident.
The most obvious reason to prioritize vulnerability management is to keep the bad guys out. Attackers are opportunistic; they scan for known weaknesses and exploit them. A proactive approach means you’re finding and fixing those security gaps before they can. As Microsoft Security puts it, it’s a “continuous, proactive cybersecurity process… to prevent cyberattacks.” This isn’t about reacting to an alert after a breach has already happened. It’s about systematically reducing your attack surface so there are fewer doors and windows for an attacker to even try to open. It’s your first line of defense in a constantly evolving threat landscape.
A security incident is never just a security incident—it’s a business disruption. A successful exploit can lead to system downtime, data loss, and a halt in operations, all of which directly impact your bottom line and customer trust. Effective vulnerability management is a critical part of maintaining operational integrity. By consistently identifying and fixing weaknesses, you prevent the kinds of disruptions that can derail projects and damage your reputation. As experts at IBM note, fixing these issues before they can be used by attackers is a fundamental part of any solid security plan, ensuring the business can continue to run without interruption.
For many organizations, vulnerability management isn’t just a good idea—it’s a requirement. Industry regulations and standards like PCI DSS, HIPAA, and GDPR mandate that organizations protect sensitive data, and a key part of that is managing security vulnerabilities. A well-documented vulnerability management program is tangible proof to auditors that you are performing due diligence. It demonstrates a commitment to maintaining a secure environment, which is crucial for avoiding hefty fines and legal trouble. A strong program, as CrowdStrike highlights, helps protect an organization by proactively finding and fixing weaknesses, making compliance a natural outcome of good security practices.
A solid vulnerability management program isn’t just a single activity; it’s a continuous cycle with distinct, crucial phases. Think of it as a loop, not a straight line. Each piece builds on the last, creating a system that gets smarter and more efficient over time. When you get these core components right, you move from constantly fighting fires to proactively managing your security posture. Let’s walk through the five key pieces that form the foundation of any effective program.
You can’t protect what you don’t know exists. That’s why the first step is always asset discovery. This means creating and maintaining a complete inventory of every device, application, server, and cloud instance connected to your network. It’s about getting a clear, comprehensive view of your entire digital footprint. Without this foundational map, you’re essentially trying to secure a house without knowing how many doors and windows it has. A complete picture of your total attack surface is the only real starting point for identifying where you might be vulnerable.
Once you know what you have, it’s time to find the weaknesses. This is where scanning and assessment come in. Using vulnerability scanning tools, you can systematically check your assets for known security flaws, misconfigurations, and other potential entry points for attackers. This process automates the detection of thousands of vulnerabilities, from missing patches on a server to outdated software on a laptop. The goal here is to move from the unknown to the known, creating a detailed list of all the security gaps that need your attention.
After a scan, you’ll likely have a very long list of vulnerabilities. Trying to fix everything at once is a recipe for burnout and inefficiency. This is where vulnerability and threat prioritization becomes your best friend. Instead of just looking at a severity score like CVSS, a risk-based approach helps you focus on what matters most. It involves analyzing which vulnerabilities pose the greatest actual threat to your organization based on factors like asset criticality, ease of exploitation, and whether attackers are actively using that exploit in the wild. This lets you direct your resources to the fixes that will have the biggest impact on your security.
Now it’s time to take action. Remediation is the process of actually fixing the vulnerabilities you’ve prioritized. This could mean applying a patch, changing a configuration, or updating a piece of software. Sometimes, a full fix isn’t immediately possible. In those cases, you can apply mitigation controls to make the vulnerability harder for an attacker to exploit. In rare instances, for low-risk issues, you might formally choose acceptance—acknowledging the risk and deciding not to fix it. The key is to have a clear plan for addressing each high-priority weakness.
Vulnerability management is never “done.” New assets come online, new software is installed, and new vulnerabilities are discovered every day. Continuous monitoring ensures your program keeps up. This involves regularly re-scanning your environment to verify that fixes have been effective and to catch any new weaknesses that have appeared. Reporting is just as important, as it provides visibility to your team and leadership on your security posture and the progress you’re making. This ongoing loop of discovery, prioritization, and remediation is what makes a threat exposure management platform so powerful.
Trying to tackle every vulnerability your scanner finds is a recipe for burnout. Not all vulnerabilities are created equal, and attackers certainly don’t target them randomly. This is where threat intelligence comes in. It adds a layer of real-world context to your vulnerability data, transforming an overwhelming list into a manageable, prioritized action plan. Instead of guessing which flaws pose the biggest threat, you can use data on active exploits, attacker tactics, and trending threats to focus your efforts where they will have the greatest impact. This approach is the core of modern vulnerability and threat prioritization, helping you work smarter, not just harder.
Your security team can’t fix everything at once, so the first question should always be, “What are attackers actually exploiting right now?” Threat intelligence answers this by highlighting vulnerabilities with known exploits in the wild. For instance, a recent study from Google Cloud’s Mandiant team analyzed vulnerabilities exploited in 2023 and found that attackers consistently favor specific types of flaws. By integrating this kind of insight, you can immediately elevate the vulnerabilities that pose a clear and present danger. This allows you to cut through the noise of theoretical risks and direct your resources toward the handful of issues that are actively being used to breach networks like yours.
Knowing a vulnerability is being exploited is one thing; understanding how quickly it becomes a weapon is another. Data shows that attackers move fast. In 2023, a quarter of high-risk CVEs were exploited on the very day they were published. This is why real-time threat advisories are so critical. They provide the context you need to understand the urgency of a patch. When you can see that a specific vulnerability is being exploited remotely and that threat actors are already using it, you have a clear business case for dropping everything and deploying the fix immediately. This focus on real-world attack patterns ensures your remediation efforts are always aligned with the current threat landscape.
Ultimately, threat intelligence is the engine that drives smarter prioritization. It enriches your vulnerability data with context, allowing you to score risks based not just on a technical severity score (like CVSS) but on the likelihood of exploitation. This intelligence, often curated by research teams like HiveForce Labs, can be fed into your exposure management platform to automate the prioritization process. Instead of manually sifting through thousands of alerts, your team gets a clear, evidence-backed list of what to fix first. This makes your entire vulnerability management program more efficient, effective, and capable of keeping up with the ever-evolving tactics of attackers.
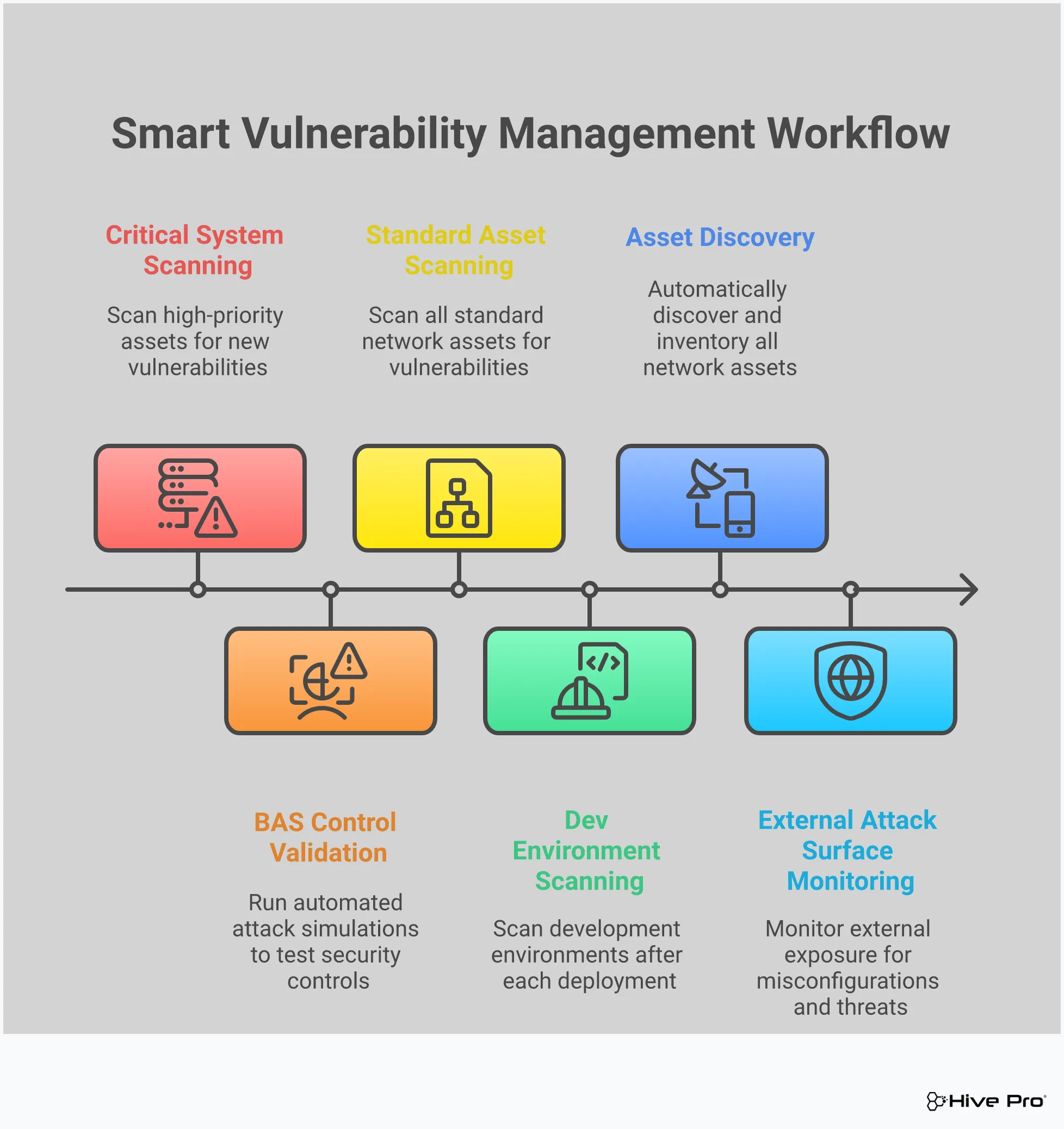
You’ve used threat intelligence to create a smart, prioritized list of vulnerabilities. That’s a huge step. But how do you know your security controls will actually stop an attack targeting those weaknesses? This is where Breach and Attack Simulation (BAS) comes in. Think of it as a security fire drill. Instead of just assuming your defenses will work, BAS lets you safely test them against the kinds of attacks you’re likely to face. It moves you from a theoretical understanding of your risk to a practical one by continuously running simulated attacks to validate your security posture. It’s a crucial part of a modern adversarial exposure validation strategy.
You invest a lot in your security stack—firewalls, EDR, SIEMs—but are they doing their job? BAS answers that question with certainty. These platforms don’t just check for vulnerabilities; they actively try to exploit them using the same tactics, techniques, and procedures (TTPs) as real-world attackers. This allows you to see exactly how your defenses respond under pressure. You can find out if a specific malware strain would be blocked or if an attacker could move laterally across your network. It’s the difference between having a fire extinguisher on the wall and knowing it actually works when you pull the pin. This practical testing shows you precisely where your weaknesses are before an attacker does.
Your team just spent hours patching a critical vulnerability. The ticket is closed, and everyone moves on. But are you sure the fix worked? BAS provides the proof. After remediation, you can run a specific simulation that mimics an attack on that vulnerability. If the attack fails, you have concrete evidence that your patch was successful and the risk has been neutralized. This creates a powerful feedback loop for your vulnerability management program. It ensures that your team’s hard work is paying off and that you aren’t just closing tickets, but actually closing security gaps. This continuous validation turns remediation from a guessing game into a verified process.
Attackers don’t think in terms of isolated vulnerabilities; they look for attack paths. A low-priority issue on one server combined with a misconfiguration on another could create the perfect entry point. A standard vulnerability scan might miss this kind of chained threat. BAS helps you see your network from an attacker’s perspective. By simulating multi-stage attacks, it can uncover hidden gaps and complex pathways that lead to your critical assets. This proactive approach allows you to find and fix these weaknesses before they can be exploited. You get to stay a step ahead, hardening your environment against the creative and persistent methods of real adversaries.
Putting a solid vulnerability management program in place does more than just check a box for an audit. It delivers real, measurable value by shifting your security posture from reactive to proactive. When you get it right, you’re not just fixing problems; you’re building a more resilient, efficient, and secure organization. Let’s look at the key benefits you can expect.
Every unpatched vulnerability is like an unlocked door, giving attackers a potential way into your network. A consistent vulnerability management process helps you find and lock these doors before someone with bad intentions finds them first. This is the essence of proactive security. By continuously identifying and remediating weaknesses across your entire IT environment, you methodically reduce your overall attack surface. This makes your organization a much harder target for attackers, who often rely on finding the easiest entry points. A strong program gives you a clear view of your total attack surface and the control to systematically shrink it over time.
Security teams are often overwhelmed with a constant stream of alerts and an impossibly long list of vulnerabilities. A smart vulnerability management program cuts through the noise. Instead of trying to fix everything at once, your team can focus on the vulnerabilities that pose the greatest actual risk to your business. This targeted approach prevents burnout and makes your team’s efforts far more impactful. It’s also much more efficient to prevent an incident than to deal with the fallout of a breach. By addressing weaknesses proactively, you reduce the likelihood of system downtime and costly emergency responses, freeing up your team to work on more strategic security initiatives.
Meeting regulatory and industry standards like PCI DSS, HIPAA, or ISO 27001 is a non-negotiable part of doing business for many organizations. These frameworks almost always require a documented process for managing security weaknesses. A mature vulnerability management program provides the exact evidence auditors need to see. It creates a clear, auditable trail of how you identify, assess, and remediate vulnerabilities, demonstrating due diligence. This turns compliance from a stressful, periodic fire drill into a predictable, ongoing part of your security operations, making audits a much smoother experience for everyone involved.
Ultimately, vulnerability management is about reducing risk. By systematically finding and fixing security flaws, you lower the probability of a successful cyberattack and minimize its potential business impact. This isn’t about reacting to the latest exploit you read about online; it’s about making informed, data-driven decisions to strengthen your defenses over time. A continuous process helps you stay ahead of attackers by addressing problems before they can be exploited. This strategic approach to threat exposure management allows your business to operate with greater confidence, knowing that you have a handle on your security posture and can innovate safely.
Even with a solid plan, running a vulnerability management program is rarely a straight line from A to B. Most security teams, regardless of size or industry, run into the same frustrating hurdles. You might have the right goals, but legacy processes, resource constraints, and the sheer volume of threats can make progress feel slow and overwhelming.
Recognizing these common roadblocks is the first step toward building a more resilient and effective program. When you know what to look for, you can proactively address the issues that stall progress and leave your organization exposed. Let’s walk through the four biggest challenges that teams consistently face.
If you’ve ever run a vulnerability scan, you know the feeling. You’re suddenly faced with a report listing thousands of vulnerabilities across your assets, and it’s impossible to know where to start. The traditional mindset of “patch everything” is a recipe for burnout and failure. The goal isn’t to reach zero vulnerabilities—it’s to meaningfully reduce risk. But when your to-do list is endless, it’s easy to fall into a cycle of chasing low-priority fixes or feeling completely paralyzed by the noise. This is where effective Vulnerability & Threat Prioritization becomes your most important strategy, helping you filter out the distractions and focus on what truly matters.
Let’s be honest: most security teams are stretched thin. You’re tasked with protecting an ever-expanding attack surface against a growing number of threats, often without a corresponding increase in headcount or budget. There’s simply not enough time in the day to manually investigate every alert, coordinate with IT and DevOps teams for every patch, and report on progress. This constant state of firefighting prevents teams from doing strategic work. Without the right people and resources, even the most well-intentioned vulnerability management program can quickly fall behind, leaving critical systems exposed while your team struggles to keep its head above water.
Your security stack is likely a collection of powerful but disconnected tools. You have your vulnerability scanners, your SIEM, maybe a threat intelligence feed, and other solutions. The problem is, they rarely speak the same language or share data effectively. This forces your team to spend valuable time manually correlating information from different dashboards just to get a single, coherent view of a potential threat. This lack of integration creates blind spots and slows down your response. A modern approach requires a unified view of cyber risks in a single place, breaking down the silos between tools to give you the full context you need to act decisively.
When a major vulnerability hits the news, the pressure to patch immediately is intense. This often leads teams to rely on static metrics like CVSS scores to quickly sort through the chaos. While CVSS is a useful starting point, it doesn’t tell the whole story. It lacks the real-world context of whether a vulnerability is actively being exploited or if it’s relevant to your specific environment. Rushing to fix a CVSS 10 vulnerability that has no public exploit might cause you to ignore a CVSS 7 that attackers are using right now. True risk reduction requires balancing speed with accuracy, using real-time threat intelligence from sources like HiveForce Labs to make informed decisions instead of reactive ones.
Having a solid vulnerability management process is one thing, but you need the right technology to make it happen. The tools you choose can make the difference between feeling overwhelmed and feeling in control. They help you find, prioritize, and fix issues efficiently. Let’s look at the core components of a modern vulnerability management toolkit.
Think of vulnerability scanners as your foundational tools. Their job is to systematically test your systems and networks to find common weaknesses. These tools are essential for getting a baseline understanding of your security posture by identifying known vulnerabilities in your software, applications, and network devices. While they are a critical first step, their main function is discovery. They generate a list of potential problems, but they don’t always provide the context you need to decide what to fix first.
This is where you move from just finding vulnerabilities to understanding your actual risk. A Threat Exposure Management platform goes beyond a simple scan. It integrates vulnerability data with real-world threat intelligence to show you which weaknesses are most likely to be exploited by attackers. Instead of just giving you a long list, these platforms help you find, prioritize, and fix security problems before they become active threats. This holistic view allows you to focus your team’s limited time and resources on the issues that pose a genuine danger to your organization.
Let’s be honest: no one has time to manually sift through thousands of alerts. Automation is what makes modern vulnerability management scalable. These tools help you streamline everything from scanning schedules to ticketing and remediation workflows. Using automated tools to quickly address critical security problems, especially when an exploit is already public, is essential for staying ahead. By automating repetitive tasks, you free up your security team to concentrate on more strategic work, like threat hunting and improving your overall security defenses.
Knowing the principles of vulnerability management is one thing; putting them into practice is another. A successful program isn’t built on a single tool or a one-time audit. It’s built on consistent, smart habits that become part of your security culture. If you’re looking to refine your approach, here are four essential practices that can make a significant difference in reducing your organization’s exposure to threats.
The old way of handling vulnerabilities was like playing whack-a-mole—a new threat pops up, and you scramble to knock it down. A modern approach is much more strategic. True vulnerability management is a “continuous, proactive cybersecurity process” that involves constantly identifying, assessing, and fixing weaknesses to prevent attacks before they happen. This means moving away from a purely reactive stance. Instead of waiting for a critical alert, you should be actively hunting for potential issues, validating your security controls, and integrating security into every stage of your IT and development lifecycle. This proactive mindset helps you stay ahead of attackers by closing security gaps before they can be exploited.
If you try to fix every single vulnerability, you’ll quickly burn out your team. The key isn’t to fix everything, but to fix the right things first. This is where a risk-based approach comes in. Instead of relying solely on CVSS scores, risk-based vulnerability management considers the business context. It asks critical questions: How important is the affected asset? Is there active exploitation of this vulnerability in the wild? What would be the actual impact on our business if it were compromised? Using a platform that provides vulnerability and threat prioritization helps you focus your limited time and resources on the threats that pose a genuine danger to your organization, not just the ones that look scary on paper.
Vulnerability management is a team sport. Your security team can’t do it alone. Success requires clear communication and collaboration between security, IT operations, and development teams. It’s crucial to establish a shared understanding of the goals. For instance, a vulnerability management strategy is focused on reducing overall cyber risk, while a patch management plan might just aim to get every system updated. These aren’t the same thing. By creating shared dashboards, setting clear expectations for remediation timelines, and ensuring everyone understands the “why” behind a high-priority ticket, you can break down silos and create a more effective, unified defense against threats.
Threats don’t take a break, and neither should your defenses. Vulnerability management is not a one-time project; it’s a continuous cycle. New assets come online, software configurations change, and new vulnerabilities are discovered every day. To keep up, you need a consistent and comprehensive scanning schedule. Regular scanning is essential for identifying and addressing weaknesses as they appear. This means having a plan for continuously monitoring your entire attack surface—from your cloud environments and on-prem servers to your web applications and employee devices. A consistent cadence ensures you always have an up-to-date picture of your security posture and can spot new risks before they become major problems.
You’re scanning, patching, and prioritizing, but how do you know if any of it is actually making a difference? A successful vulnerability management program isn’t just about being busy; it’s about showing real, measurable improvement in your security posture. Moving from a reactive cycle of firefighting to a proactive state of control requires you to step back and look at the data. Proving the value of your program—to your CISO, your board, or even just your own team—comes down to tracking the right things.
The goal is to tell a story with data. Are you getting faster at fixing critical issues? Is your overall attack surface shrinking? Answering these questions helps you understand what’s working, where the bottlenecks are, and how to make intelligent decisions about where to invest your time and resources. It’s the difference between simply running a program and strategically managing your organization’s exposure to threats. By focusing on clear metrics, you can turn your vulnerability management efforts from a cost center into a proven security asset.
If you can’t measure it, you can’t improve it. Tracking progress is essential for understanding the health of your vulnerability management program. Think of it as a continuous feedback loop. You need to keep records and create reports not just for compliance, but to see how quickly problems are found and fixed. Start by tracking your scan coverage—are you actually looking at all your assets? From there, monitor the number of open critical and high-severity vulnerabilities over time. A downward trend is a clear sign of progress. Also, look at vulnerability density, or the average number of vulnerabilities per asset, to see if you’re making systems more secure from the start.
Speed and accuracy are everything in remediation. The most common metric here is Mean Time to Remediate (MTTR), which tells you the average time it takes your team to fix a vulnerability after it’s been discovered. You should track this for different severity levels—your MTTR for critical vulnerabilities should be much lower than for low-priority ones. But fixing things fast is only half the battle. You also need to ensure the fix actually worked. After patching, it’s critical to validate your remediation efforts by rescanning the asset to confirm the vulnerability is gone and that the patch didn’t introduce any new issues. This closes the loop and ensures your hard work truly reduced risk.
A good VM program finds and fixes vulnerabilities. A great one learns and adapts to become more proactive. Maturing your program means shifting from simply managing a list of CVEs to strategically reducing your overall threat exposure. This involves regularly reviewing security incidents and program results to find gaps and make your security better. Are certain teams or departments consistently slower at patching? Are specific types of vulnerabilities reappearing? Answering these questions helps you address root causes, not just symptoms. A truly proactive approach helps protect your organization by finding and fixing weaknesses before they can be exploited, turning your VM program into a cornerstone of your security strategy.
What’s the difference between vulnerability management and patch management? Think of it this way: patch management is a specific task, while vulnerability management is the entire strategy. Patching is the act of applying an update to fix a known flaw, which is a crucial part of the process. Vulnerability management, however, is the complete cycle of discovering all your assets, scanning them for weaknesses, using intelligence to prioritize which ones actually pose a threat, and then overseeing the remediation, which includes patching. It’s the difference between simply fixing a broken window and having a full security plan for your entire house.
Is a high CVSS score the only thing I should focus on for prioritization? A high CVSS score is a good starting point, but it shouldn’t be the only factor you consider. A CVSS score tells you how severe a vulnerability could be in a perfect scenario, but it doesn’t tell you if attackers are actually using it in the real world. A vulnerability with a lower score that is being actively and easily exploited is a much bigger threat than a CVSS 10 that has no known exploit. This is why incorporating threat intelligence is so important—it adds the real-world context you need to focus on the threats that are a clear and present danger to your business.
How is Breach and Attack Simulation (BAS) different from a regular vulnerability scan? A vulnerability scan is like checking to see if you left any doors or windows unlocked in your house. It identifies potential weaknesses. Breach and Attack Simulation, on the other hand, is like safely simulating a break-in to see if your alarm system, locks, and cameras actually work as expected. BAS actively tests your security controls by mimicking the techniques real attackers use, helping you confirm that your defenses can stop an attack and that the fixes you’ve applied are truly effective.
My team is small and overwhelmed. What’s the most important first step to take? The most impactful first step is to stop trying to fix everything. Instead, shift your focus to a risk-based approach. You can immediately cut through the noise by using threat intelligence to identify the small percentage of vulnerabilities that are actively being exploited by attackers. By concentrating your limited time and resources on this short, high-priority list, you make a much bigger impact on your organization’s security than if you tried to tackle a massive list based on severity scores alone. It’s about focusing on the fixes that matter most right now.
How do I prove to my leadership that our vulnerability management program is actually working? You can prove its value by telling a story with data. Instead of just reporting on the number of patches applied, track metrics that show a clear reduction in risk. Focus on your Mean Time to Remediate (MTTR) for critical vulnerabilities, demonstrating that your team is getting faster at closing your most dangerous security gaps. You can also show a downward trend over time in the total number of high-risk, actively exploited vulnerabilities in your environment. This provides clear, tangible evidence that your program is making the organization a harder target for attackers.