Comprehensive Threat Exposure Management Platform
Traditional vulnerability management has taught us to look for weaknesses inside our own walls. But what if we flipped the script and started looking at our defenses from the outside in, just like an attacker does? Attackers don’t care about CVSS scores; they care about pathways. They look for the easiest, most effective way to achieve their objective. This shift in perspective is the core of a modern security strategy. Understanding what is Continuous Threat Exposure Management (CTEM) is about adopting that attacker-centric view. It’s a framework that moves beyond simple vulnerability scanning to provide a holistic, continuous view of your entire attack surface, helping you anticipate threats and close down attack paths before they can ever be exploited.
If your security team feels like it’s constantly playing catch-up, you’re not alone. The sheer volume of vulnerabilities can be overwhelming, making it tough to know where to focus. This is where Continuous Threat Exposure Management (CTEM) comes in. Think of it as a strategic workflow designed to get you ahead of attackers. Instead of just reacting to an endless list of potential threats, CTEM gives you a repeatable process to continuously find, prioritize, and fix the security gaps that matter most.
At its core, CTEM is a five-step cycle that helps you see your organization through an attacker’s eyes. It’s a shift from asking “What are we vulnerable to?” to “How likely are we to be attacked, and what would the impact be?” This approach helps you make smarter, risk-based decisions about where to invest your time and resources. By continuously evaluating your assets for accessibility, exposure, and exploitability, you can build a security program that is both proactive and aligned with your business goals.
So what does this framework actually look like? Gartner calls CTEM a “pragmatic and systemic approach” to managing your attack surface. In plain English, it’s a structured workflow that helps your team consistently evaluate how exposed your assets are. The framework moves beyond simple vulnerability scanning to consider the entire attack path. It helps you understand which assets are accessible to attackers, how they could be exploited, and what the potential business impact would be. This holistic view allows you to focus your team’s efforts on the exposures that pose a genuine threat.
The main reason your team needs CTEM is to cut through the noise. Traditional vulnerability management often leaves teams drowning in low-risk alerts. A CTEM program helps you prioritize vulnerabilities based on their potential impact on your specific business operations. It allows you to build a risk reduction strategy that continuously evaluates and improves your security controls. By focusing on the exposures that attackers are actively exploiting, you can reduce the likelihood of a breach and ensure your defenses are prepared for real-world threats. This means less time spent on low-priority issues and more time strengthening your overall security posture.
For years, vulnerability management has been the bedrock of many security programs. It’s a familiar cycle: scan your assets, find the flaws, and patch them. But as your attack surface expands and attackers get faster, this traditional approach starts to show its cracks. It’s like trying to patch a leaky boat in a hurricane—you’re always one step behind.
Continuous Threat Exposure Management (CTEM) isn’t just a new name for the same old process. It represents a fundamental shift in how we think about and manage risk. Instead of just cataloging vulnerabilities, CTEM provides a holistic, attacker-centric view of your entire environment. This helps you move from a defensive crouch to a confident, proactive stance. Let’s break down the key differences.
Traditional vulnerability management often puts security teams in a constant state of reaction. A scan runs, a report is generated, and the race to patch begins. You’re always responding to a list of known problems. CTEM flips the script by helping you anticipate threats before they become active incidents. It’s about understanding your potential exposure from an attacker’s perspective and closing those pathways before they can be used against you. This proactive approach allows you to get ahead of the cycle of vulnerability disclosures and focus on building a more resilient security posture.
Think about how much your IT environment changes in a month, or even a week. Traditional vulnerability management often relies on periodic scans—weekly, monthly, or quarterly. The problem is that these scans only provide a snapshot in time, creating dangerous blind spots between assessments. A new asset could be spun up or a critical vulnerability disclosed hours after a scan completes, leaving you exposed. CTEM is a continuous program that provides an always-on view of your attack surface. It constantly discovers assets and assesses their exposure, giving you a real-time understanding of your risk without waiting for the next scheduled scan.
If your team is drowning in a sea of “critical” vulnerabilities, you know the limitations of relying on CVSS scores alone. A high score doesn’t always equal high risk to your business. Traditional methods often lack the context to tell you what to fix first. CTEM changes the game by moving beyond static scores. It enriches vulnerability data with threat intelligence and business context to help you with Vulnerability & Threat Prioritization. This means you can focus on the flaws that are actively being exploited in the wild and that exist on your most critical assets, ensuring your remediation efforts have the greatest possible impact.
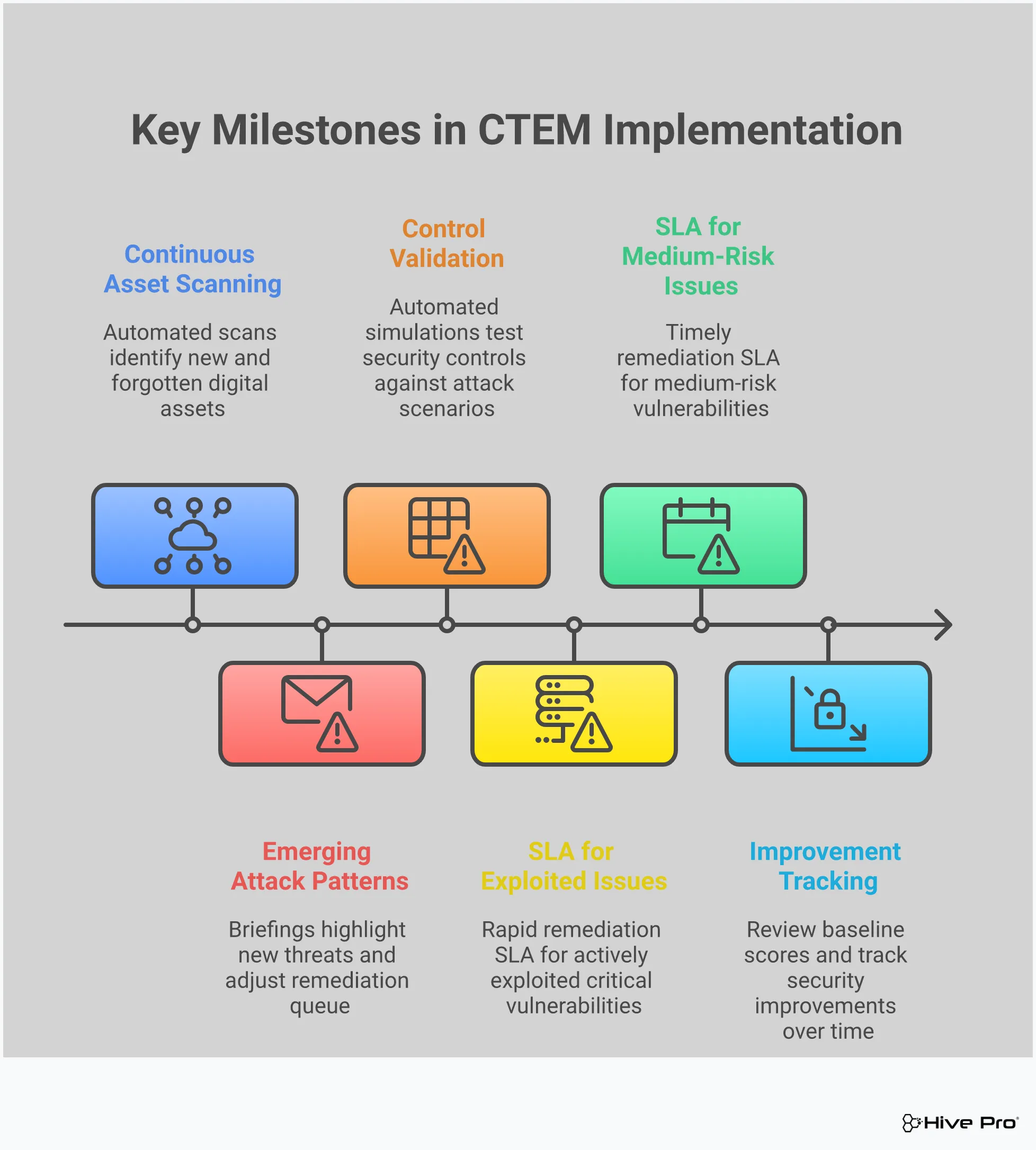
A Continuous Threat Exposure Management (CTEM) program isn’t a one-off project; it’s a cyclical, strategic framework designed to give you a consistent and clear view of your security posture. Think of it as a five-step loop that helps your team move from a reactive state of putting out fires to a proactive one where you’re strategically reducing your attack surface. Each phase builds on the last, creating a repeatable process that helps you measure progress and communicate wins to leadership. This structured workflow provides a strategic way for security leaders to manage cyber threats and risks effectively. By adopting this approach, you can systematically identify, prioritize, and address the threats that pose a genuine risk to your organization, ensuring your resources are always focused on what matters most. It’s about creating a sustainable rhythm for security that aligns with your business objectives, rather than just chasing the latest vulnerability alert. This continuous cycle ensures that as your attack surface evolves, so does your understanding of its exposures, allowing you to make informed, risk-based decisions consistently.
You can’t protect what you don’t know you have. The first phase of any solid CTEM program is all about scoping—getting a complete and continuous inventory of your entire digital footprint. This goes beyond your on-prem servers and known devices. It means discovering and mapping every internet-facing asset, including cloud instances, web applications, APIs, and even forgotten subdomains. The goal is to create a comprehensive, up-to-date map of your total attack surface. This foundational step is critical because any blind spots here will carry through the entire process. Without a full picture of your assets, you’re essentially leaving doors open for attackers to find before you do.
Once you have a clear map of your attack surface, the next step is to identify the vulnerabilities and exposures within it. This discovery phase involves continuous scanning and assessment of all the assets you identified in the scope phase. It’s about finding the weaknesses—like unpatched software, misconfigurations, or insecure protocols—that an attacker could potentially exploit. Unlike traditional, scheduled vulnerability scans, a CTEM approach makes this a continuous process. As your environment changes with new deployments and updates, you need a system that constantly looks for new weaknesses, ensuring you have a real-time understanding of your security gaps across your entire digital landscape.
This is where CTEM truly changes the game. Instead of getting buried under a mountain of vulnerabilities with high CVSS scores, the prioritization phase helps you focus on what actually matters. It answers the question: “Of all our vulnerabilities, which ones are most likely to be exploited by an attacker right now?” This requires enriching vulnerability data with real-world threat intelligence. By understanding which vulnerabilities have active exploits in the wild and are being used by threat actors, you can perform vulnerability and threat prioritization that directs your team’s limited time and resources to the most critical risks, dramatically reducing your exposure to imminent threats.
You have firewalls, EDR, and other security tools in place, but are they configured correctly and actually working as expected? The validation phase is all about testing your defenses. Using techniques like Breach and Attack Simulation (BAS), you can safely simulate real-world attack paths to see how your security controls hold up. This process helps you identify gaps in your defenses, such as misconfigurations or policies that aren’t blocking malicious activity. By continuously performing adversarial exposure validation, you can confirm that your security investments are providing the protection you need and find weaknesses before an actual attacker does, allowing you to fine-tune your controls for better efficacy.
The final phase is all about action. Finding, prioritizing, and validating exposures is pointless if you can’t fix them efficiently. The mobilization phase focuses on streamlining your remediation workflow. This means getting the right information to the right teams—whether it’s IT, DevOps, or network security—with clear instructions on how to fix the issue. A mature CTEM program integrates with ticketing and patch management systems to automate and track the remediation process. This creates a structured, repeatable system that not only speeds up response times but also provides measurable data to show how you’re actively reducing risk and improving your security posture over time.
A CTEM program is only as good as the data that fuels it. Without the right context, a list of vulnerabilities is just noise—a long to-do list with no clear starting point. This is where threat intelligence comes in. It transforms your CTEM strategy from a simple inventory of potential weaknesses into a focused, proactive defense plan. By integrating real-world threat data, you can stop guessing which vulnerabilities matter and start focusing on the ones attackers are actively using right now.
Think of it this way: your attack surface is a map of your city, and vulnerabilities are all the unlocked doors and windows. Threat intelligence provides the real-time crime reports, showing you exactly which neighborhoods—and which types of entry points—burglars are targeting. This allows you to dispatch your limited security resources to the most critical areas first. Instead of trying to secure every single window at once, you can prioritize the ones most likely to be exploited. This intelligence-driven approach is the core of an effective CTEM program, helping you cut through the alert fatigue, make smarter decisions, and reduce your true exposure to threats.
Not all vulnerabilities are created equal. A critical-rated vulnerability on an internal, air-gapped server might pose less of a real-world risk than a medium-rated one on your primary web application. This is why relying solely on CVSS scores can be misleading. Threat intelligence adds the essential layer of context your team needs to prioritize vulnerabilities based on actual risk to your business. It helps you answer the crucial questions: Is this vulnerability being actively exploited in the wild? Is it part of a known ransomware campaign? Are threat actors targeting our industry with this specific exploit? By layering this context over your vulnerability data, you can focus your remediation efforts on the exposures that present a clear and present danger to your operations.
To build a strong defense, you need to understand your opponent’s playbook. Threat intelligence gives you direct insight into what attackers are doing, which tools they’re using, and which vulnerabilities they favor. This information is critical for focusing your security enhancements where they’ll have the most impact. When you know that a specific threat actor is exploiting a particular vulnerability in Apache Struts, you can immediately check your environment and validate your controls against that exact attack vector. This proactive stance, powered by in-house intelligence, allows you to move beyond generic security hardening and build defenses specifically tailored to counter the most relevant and active threats targeting your organization.
Attackers are constantly innovating, which means your defenses can’t afford to be static. The threat landscape is always shifting as new vulnerabilities are discovered and new exploit techniques are developed. A successful CTEM program uses a continuous feedback loop of threat intelligence to stay ahead of these changes. This iterative approach allows you to constantly evaluate and refine your security controls to optimize your cyber defense. By integrating threat intelligence into a CTEM platform, you create a living security strategy that adapts in near real-time, ensuring your defenses remain effective against the threats of tomorrow, not just the ones from yesterday.
After you’ve identified and prioritized your most critical exposures, it’s time to validate your defenses. This is where Breach and Attack Simulation (BAS) comes in. Think of it as a security fire drill. You wouldn’t just install a fire alarm and assume it works; you’d test it. BAS does the same for your cybersecurity controls, moving you from “we think we’re secure” to “we know where our gaps are because we’ve tested them.”
BAS platforms safely and automatically simulate the real-world tactics, techniques, and procedures (TTPs) used by actual threat actors. This isn’t about running another vulnerability scan; it’s about testing if your existing security stack—your firewalls, EDR, SIEM, and other tools—can actually detect and block a real attack. This process of Adversarial Exposure Validation is a core part of the CTEM lifecycle. It provides concrete proof of your security effectiveness and shows you exactly where you need to focus your efforts to strengthen your posture against the threats that matter most.
It’s not enough to just have security tools in place; you need to know they are configured correctly and working as intended. BAS allows you to run realistic attack scenarios that mimic the exact methods used by known threat groups. For example, you can simulate a specific ransomware strain’s attack chain to see if your EDR solution blocks the malicious payload or if your firewall prevents communication with its command-and-control server. This provides a continuous feedback loop. You run a simulation, identify a control failure, make a change, and then run the simulation again to verify the fix. This iterative approach helps you continuously refine your security controls to keep pace with an ever-changing threat landscape.
A security breach tests more than just your technology; it tests your people and processes. It’s one thing to have a detailed incident response (IR) plan in a binder, but it’s another to see how your team performs under pressure. BAS simulations can put your IR plan to the test in a controlled environment. By simulating a breach from initial access to data exfiltration, you can see how your team responds in real-time. Did the SOC team receive and correctly triage the alerts? Did they follow the established procedures for containment and eradication? These drills help uncover gaps in your playbook and give your team the practice they need to respond quickly and effectively when a real incident occurs.
One of the biggest challenges in security is demonstrating improvement. BAS changes that by providing clear, measurable results. By running consistent and repeatable attack simulations, you can establish a security performance baseline. As your team works to remediate vulnerabilities and tune security controls, you can rerun the same simulations to get hard data on your progress. This allows you to track your exposure reduction over time and prove that your efforts are making a tangible difference. These metrics are invaluable for communicating security posture to leadership, justifying budget requests, and showing the direct ROI of your CTEM program. It’s how you report successes effectively and build a data-driven security strategy.
Adopting a CTEM framework is a powerful move for any security program, but let’s be real—making a big strategic shift isn’t always a straight line. It’s common to run into a few challenges along the way, from finding the time and people to manage the program to getting all your existing tools to play nicely together. The good news is that these hurdles are well-known, and with the right approach, you can clear them easily.
Thinking about these potential roadblocks ahead of time helps you build a smoother, more effective CTEM program from day one. It’s not about avoiding challenges entirely, but about having a smart plan to address them so you can focus on what really matters: proactively reducing your organization’s threat exposure. Let’s walk through some of the most common issues and how to handle them.
Many security teams feel like they’re constantly playing catch-up. You’re stretched thin, and it’s easy to get pulled into chasing vulnerabilities that are making headlines but pose little actual risk to your specific environment. This is where a CTEM program changes the game. Instead of needing a team of specialists to analyze every potential threat, a good CTEM platform does the heavy lifting for you.
It provides the risk-based context needed to focus your team’s limited time and energy on the exposures that matter most. By automating the discovery and analysis process, you can prioritize threats based on real-world exploitability and business impact. This allows even small teams to operate with the efficiency and focus of a much larger security organization.
Your security stack is probably already crowded. The last thing you need is another siloed tool that adds complexity instead of clarity. The idea of implementing a new platform can feel daunting, especially when you’re worried about how it will integrate with your existing scanners, asset inventories, and security controls. A true CTEM platform isn’t just another tool to add to the pile—it’s a unifying layer that brings all your data together.
The goal is to create a single source of truth for your entire threat exposure. Look for a platform that offers broad integrations and presents a unified view of your cyber risks. This approach breaks down data silos, eliminates blind spots, and turns a chaotic collection of tools into a streamlined, cohesive security ecosystem.
Effective security is a team sport, but too often, security, IT operations, and development teams work in separate worlds. They have different priorities, speak different languages, and use different tools, which can create friction and slow down remediation efforts. A CTEM program helps bridge these gaps by creating a shared understanding of risk that everyone can rally around.
When you can clearly show how a specific vulnerability in a piece of code impacts a critical business application, it’s no longer just a “security problem”—it’s a business problem that everyone is motivated to solve. CTEM provides the data and context to facilitate these conversations, helping to foster collaboration and build a culture where security is a shared responsibility across the entire organization.
Implementing a Continuous Threat Exposure Management (CTEM) program is a huge step forward, but how do you know it’s actually working? Proving the value of your security efforts requires more than just a gut feeling; it requires clear, consistent metrics. Tracking the right key performance indicators (KPIs) shows how your program is reducing risk, improving efficiency, and strengthening your overall security posture. It also helps you tell a compelling story to leadership about why these investments matter.
A successful CTEM program isn’t measured by a single number. Instead, it’s about looking at a collection of metrics that, together, paint a picture of progress. By focusing on a few key areas, you can move beyond simply counting vulnerabilities and start measuring what truly counts: your ability to find, fix, and validate your defenses against real-world threats. These metrics help you refine your processes, demonstrate improvement over time, and ensure your team is focused on the actions that have the greatest impact on your organization’s security.
You can’t fix a problem you don’t know you have, and the longer a threat lingers, the more damage it can do. That’s why two of the most critical metrics for any security program are Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). MTTD measures how quickly your team identifies a potential threat or exposure, while MTTR tracks how long it takes to remediate it. A strong CTEM program should shrink both of these timelines dramatically. The goal is to move from a detection window of weeks or months to just hours, giving attackers far less time to operate. A unified platform that centralizes exposure data is key to speeding up this entire cycle.
Finding vulnerabilities is only half the battle; fixing them is what actually reduces risk. Measuring remediation effectiveness helps you understand how well your team is closing security gaps. Instead of just tracking the number of open tickets, focus on metrics like the remediation rate for critical vulnerabilities or the reduction in your overall attack surface over time. A structured, repeatable process ensures your team can respond to issues faster and more consistently. This not only improves your security but also makes it easier to report successes to management and demonstrate the program’s direct impact on risk reduction.
A foundational goal of CTEM is to give you a complete and accurate picture of your security landscape. After all, you can’t protect what you can’t see. Gauging your visibility means tracking how much of your attack surface you can actually monitor. Key metrics here include the percentage of assets covered by your scanning tools, the number of previously unknown or unmanaged assets discovered, and the reduction of security blind spots. Improving your attack surface management provides the situational awareness needed to make smarter, faster decisions, refine security controls, and communicate risk more clearly across the entire organization.
Shifting to a Continuous Threat Exposure Management program is a strategic move, not just a technical one. It’s about building a sustainable cycle that strengthens your security posture over time. Think of it as a roadmap with clear, actionable steps. By focusing on the right platform, fostering collaboration, and committing to continuous improvement, you can build a CTEM program that moves your team from a reactive stance to a proactive one. Here’s how to get started.
Your CTEM platform is the engine of your program, so choosing the right one is critical. Look for a solution that provides a unified view of your entire attack surface, from your on-premise networks to your cloud environments. The goal is to eliminate blind spots. A strong platform should offer automation to help your team quickly identify coverage gaps and focus on security enhancements that actually matter. Instead of just collecting data, the right tool will provide the context you need to turn that data into a clear, prioritized action plan for your team.
CTEM isn’t just a security team initiative; it’s a business-wide strategy. Your program’s success depends on breaking down the traditional silos between security, IT, and development teams. This means creating workflows to share findings and work together on remediation. As Team Cymru notes, CTEM involves managing risks “in collaboration with stakeholders.” A central platform that provides a single source of truth makes this much easier, ensuring everyone is working from the same data. This collaborative approach helps you refine processes and take remedial action based on a shared understanding of the risks.
A CTEM program is never truly “done.” It’s an ongoing, iterative process of evaluation and refinement. The threat landscape is always changing, and your defenses need to adapt. This means regularly testing your security controls, validating your defenses against real-world attack scenarios, and using those results to make improvements. This cycle of continuous improvement is what makes CTEM so effective. It provides a proactive approach to optimizing your cyber defense by constantly measuring your progress and refining your security controls to keep pace with emerging threats.
How is CTEM really different from the vulnerability management I’m already doing? Think of it as a shift in perspective. Traditional vulnerability management often gives you a long list of problems to fix, usually sorted by a technical severity score. CTEM changes the focus from “what’s broken” to “what’s most likely to be attacked.” It’s a strategic workflow that incorporates real-world threat intelligence and business context to help you see your organization through an attacker’s eyes and fix the issues that pose a genuine, immediate risk.
Is a CTEM program realistic for a small security team? Absolutely. In fact, CTEM is incredibly valuable for smaller teams because it helps you focus your limited time and resources where they will have the most impact. Instead of trying to address thousands of “critical” vulnerabilities, a CTEM program helps you pinpoint the handful that are actively being exploited and pose a direct threat to your most important assets. It’s all about working smarter, not harder.
Do I have to rip and replace my current security tools to implement CTEM? Not at all. A good CTEM platform isn’t meant to replace your existing scanners, EDRs, or firewalls. Instead, it acts as a unifying layer that integrates with those tools. It pulls data from your entire security stack to give you a single, clear view of your exposure, eliminating blind spots and making your current tools even more effective.
What’s the difference between vulnerability prioritization in CTEM and just using CVSS scores? While CVSS scores are a useful starting point, they only tell you about the theoretical severity of a vulnerability, not the real-world risk it poses to your business. CTEM provides much-needed context by layering in threat intelligence. It answers questions like, “Is anyone actually exploiting this?” and “Is this vulnerability on a critical, internet-facing server?” This allows you to prioritize based on actual, imminent threats rather than a static, generic score.
How does Breach and Attack Simulation (BAS) fit into the daily CTEM workflow? Breach and Attack Simulation is the validation step of the CTEM cycle. After you’ve identified and prioritized a critical exposure, BAS lets you safely test if your security controls can actually stop an attack that exploits it. It’s a continuous feedback loop. You can run a simulation, see where a control fails, apply a fix, and then run the simulation again to confirm that the gap is truly closed.