Comprehensive Threat Exposure Management Platform
If your security team is drowning in a sea of vulnerability alerts and struggling to make sense of multiple risk scores, you know that more data doesn’t always mean more clarity.
“The right threat exposure management platform should cut through the noise, not add to it.”
When evaluating your options, you’ll inevitably encounter two major players: Tenable and Hive Pro. Making the right choice depends entirely on your team’s workflow, budget, and security goals. We’ll examine the critical differences in the Tenable vs Hive Pro, how they compare discussion, from their integration strategies to their approach to Breach and Attack Simulation, helping you find the solution that truly empowers your team to act decisively.
When you’re looking for a platform to manage your organization’s cyber risk, Tenable and Hive Pro are two names that often come up. Both are powerful tools designed to help you understand and reduce your threat exposure, but they approach the problem from different angles. Think of it this way: Tenable has built a massive, mature ecosystem focused on providing the widest possible visibility across your entire digital footprint. It’s a long-standing leader in the vulnerability management space, known for its comprehensive scanning and broad coverage.
Hive Pro, on the other hand, offers a more modern, integrated approach focused on proactive threat and vulnerability exposure management. It’s designed to not only find vulnerabilities but to show you which ones attackers are most likely to exploit and how to block them instantly and fix them efficiently. It shifts the conversation from “How many vulnerabilities do we have?” to “Which exposures pose a real, immediate threat to our business?” Understanding their core philosophies is the first step in figuring out which platform is the right fit for your team’s specific needs and security maturity level.
Tenable is a giant in the cybersecurity industry, best known for its comprehensive vulnerability scanning capabilities. Its primary goal is to give security teams a unified view of their entire attack surface, from traditional IT infrastructure to modern cloud environments and operational technology. The platform uses AI and machine learning to analyze the massive amount of data it collects, helping teams prioritize the risks that matter most based on various metrics. Many organizations, especially those with complex, sprawling environments and strict compliance requirements, rely on Tenable for its broad visibility and quick deployment. It’s a mature, well-established solution that excels at identifying vulnerabilities across a wide range of assets.
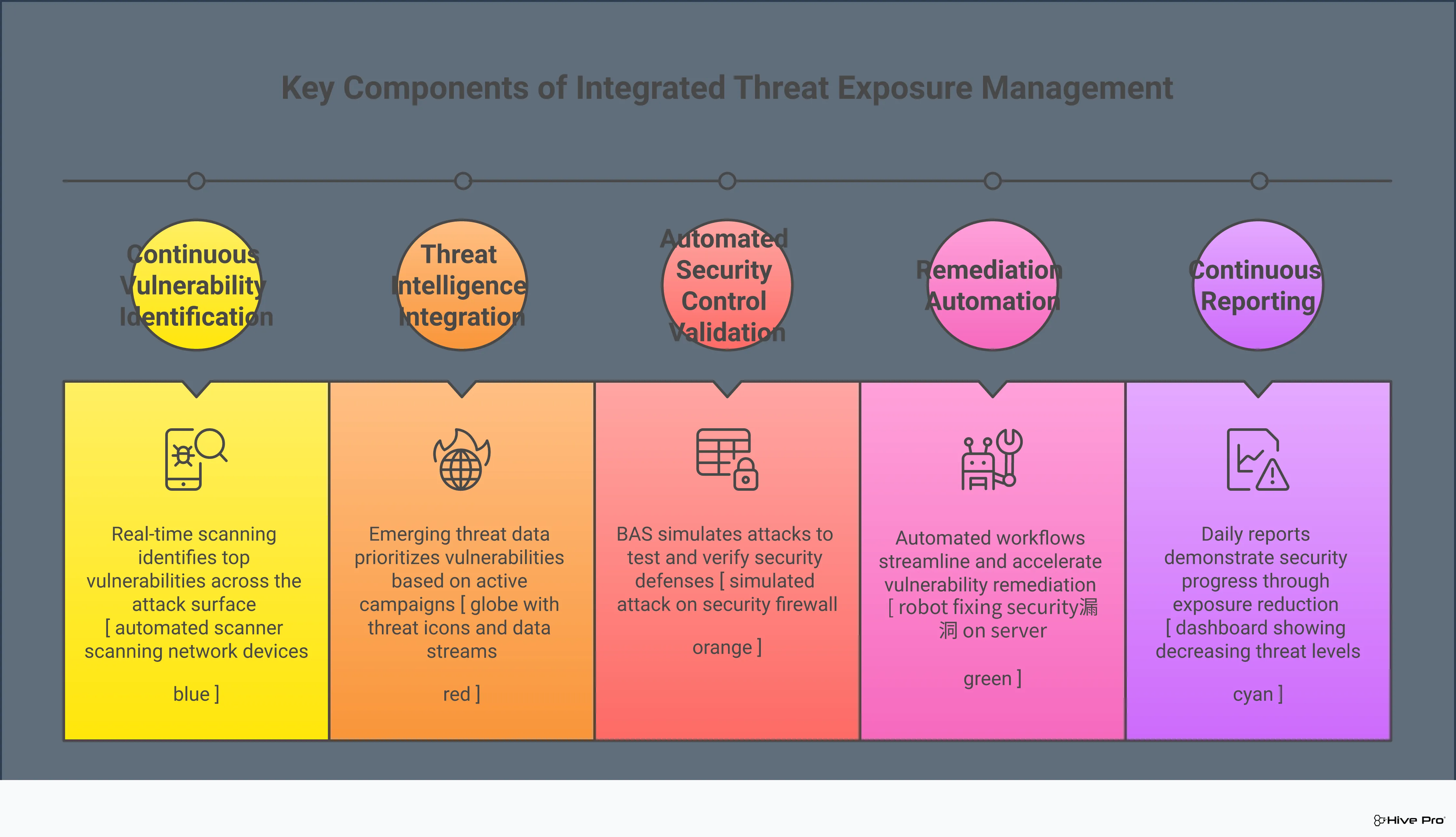
Hive Pro takes a more focused approach centered on proactive threat exposure management. For Hive Pro, vulnerability scanning and discovery are tablestakes, it is not about just the data but the actionable intelligence and instant action. Instead of just cataloging vulnerabilities, the Hive Pro Platform is built to help you see your organization through an attacker’s eyes. It prioritizes weaknesses based on their likelihood of being exploited and the potential business impact, moving beyond standard risk scores. This is powered by in-house threat intelligence from HiveForce Labs and an understanding of attacker techniques mapped to frameworks like MITRE ATT&CK. Hive Pro also delivers exposure validation capabilities using Breach and Attack Simulation (BAS) into its core platform to test the attack feasibility and security controls effectiveness, giving you a single tool to not only find but also validate and remediate your most critical exposures.
At their core, both Tenable and Hive Pro are designed to help you get a handle on vulnerabilities. But how they get you from discovery to remediation is where the paths diverge. Think of it like two different navigation apps: both will get you to your destination, but they use different data, offer different routes, and present the information in unique ways. Tenable has built its reputation on the power of its Nessus scanner, a tool many security professionals know and trust for comprehensive asset discovery. It’s known for its ability to cast a wide net and give you a detailed inventory of what’s on your network.
Hive Pro, on the other hand, approaches the problem with a focus on prioritization from the very beginning. While it also provides robust scanning, its main goal is to immediately connect vulnerabilities to real-world threats and business context. This means it doesn’t just tell you what’s broken; it tells you what’s broken and likely to be exploited, helping you focus your team’s limited time and resources on the fixes that matter most. The key difference lies in the philosophy: one is about finding everything, while the other is about finding what’s most important first.
When it comes to finding what’s on your network, Tenable relies on Nessus, one of the most recognized scanners in the industry. It does an excellent job of providing a clear inventory of your assets, from traditional IT systems to cloud and operational technology. This comprehensive view is a major reason why Tenable is so established.
Hive Pro takes a slightly different angle on total attack surface management. While its scanning capabilities are thorough, the platform is built to immediately contextualize its findings. It excels at using real-time threat intelligence to determine which vulnerabilities pose the greatest risk. This allows it to predict potential attack paths and guide you toward fixing the weaknesses that attackers are most likely to target right now, rather than just presenting a long list of all possible issues.
Scoring is where the user experience between the two platforms really starts to feel different. Tenable uses multiple metrics, including its Cyber Exposure Score(CES), Vulnerability Priority Rating (VPR) and Asset Criticality Rating (ACR). While each score provides a specific data point, juggling these different numbers can be confusing for teams trying to make quick, decisive actions. These scores don’t always account for existing security controls or the practical difficulty of an exploit.
Hive Pro simplifies this with a single, unified “Real Risk Score” on a scale of 1 to 100. This score is designed to be more intuitive by rolling multiple factors into one number. It considers not just the severity of a vulnerability but also its age, the importance of the asset, and whether you already have compensating controls in place. This approach to vulnerability and threat prioritization gives you a clearer, more actionable picture of your true risk.
Validating your security controls is a critical step that often gets overlooked. This is where Breach and Attack Simulation (BAS) comes in, and it’s a key differentiator between Hive Pro and Tenable. Hive Pro includes BAS as a core feature within its standard license. This means you can continuously and automatically test whether your security tools are configured correctly and would actually stop an attack, without needing a separate budget or tool.
With Tenable, gaining this kind of adversarial exposure validation would require a third party tool. This not only increases the total cost but also adds another layer of complexity to your security stack. By integrating BAS from the start, Hive Pro makes proactive control validation an accessible, everyday part of vulnerability management.
Managing threat exposure is about more than just finding vulnerabilities; it’s about understanding which ones truly matter to your organization and having a clear plan to address them. This is where the philosophical differences between Tenable and Hive Pro become most apparent. Both platforms aim to give you a handle on your security posture, but they get there in different ways. Your choice often comes down to what kind of insight you find most valuable: a comprehensive, data-rich overview of every potential weakness, or a highly focused, context-aware view of your most probable threats.
Tenable leans into providing a unified picture of security across your entire digital landscape, from traditional IT infrastructure to complex cloud environments. Their strategy is to gather as much data as possible and use machine learning to help you sort through it. On the other hand, Hive Pro’s Uni5 Xposure platform is built around the idea that not all vulnerabilities are created equal. It prioritizes context and real-world threat intelligence to cut through the noise, guiding your team to the risks that pose an immediate and credible danger. This distinction in approach directly impacts how your team will spend its time and resources.
Tenable’s platform is designed to give security teams a wide-angle lens on their entire attack surface. It functions as an AI-powered exposure management tool that pulls in data from across your IT and cloud systems to create a unified view of security. By leveraging machine learning, it helps teams make sense of a massive amount of information and prioritize risks based on a variety of metrics. This approach is valuable for organizations that need only comprehensive visibility. Even though Tenable has been a pioneer in the vulnerability assessment space, the CVE coverage for vulnerabilities is limited, they cover only 111K CVEs as compared to Hive Pro 326K CVEs as of January 2026.
Hive Pro takes a more direct route with its “Real Risk Score.” Instead of presenting multiple metrics that your team has to interpret, it distills complex risk factors into a single, intuitive score from 1 to 100. This score isn’t just based on a vulnerability’s severity. It provides a more holistic assessment by considering the age of the vulnerability, the business importance of the affected asset, the effectiveness of your existing security controls, and the real-world likelihood of an attack. This method gives you a clearer, more immediate understanding of your security posture, allowing you to make faster, more informed decisions.
A key part of Hive Pro’s strategy is its deep integration of threat intelligence for vulnerability and threat prioritization. The platform moves beyond traditional risk scores by focusing on the vulnerabilities that attackers are actively exploiting right now. By analyzing the potential business impact of a breach and the likelihood of exploitation, Hive Pro helps you concentrate your resources on the threats that matter most. This intelligence-led approach, powered by research from teams like HiveForce Labs, ensures your team isn’t just busy—it’s effective, tackling the most pressing dangers first.
When you’re comparing two major players in the cybersecurity space, it’s helpful to understand where each one truly shines. Both Tenable and Hive Pro have distinct advantages that appeal to different organizational needs and security philosophies. Tenable’s strength lies in its brand and established industry recognition because of its long presence in the market, while Hive Pro stands out with its modern, user-focused approach to threat exposure management.
Thinking about your team’s priorities—whether it’s broad compliance coverage or actionable, prioritized intelligence—will help you see which platform’s strengths align best with your goals. Let’s look at what makes each of them a strong contender.
Tenable has built a reputation on its comprehensive approach to vulnerability management. It’s a mature platform that excels at providing extensive visibility across diverse IT environments, making it a solid choice for large organizations that need to get up and running quickly. Tenable is particularly strong at integrating compliance requirements directly into its scanning capabilities. As one analysis notes, “Tenable combines finding assets, scanning for weaknesses, and deciding which ones are most important, all in one place. It’s good for cloud security and helps with following rules (compliance).” This all-in-one ecosystem is a significant advantage for teams that need to manage their security posture and meet regulatory demands efficiently.
Hive Pro differentiates itself with a user-centric design and a clear focus on cost-effectiveness. It’s built to offer a lower total cost of ownership (TCO) with a simpler pricing structure, making it an accessible choice for a wide range of organizations. The platform provides a single, unified view of your cyber risks, cutting through the noise that often plagues security teams. A key feature is its clear risk scoring, which “provides a single, easy-to-understand ‘Real Risk Score’ (from 1 to 100).” This score is enriched with specific threat information from HiveForce Labs, helping you understand which attackers might exploit a weakness. This focus on clarity and actionable vulnerability and threat prioritization makes Hive Pro a compelling choice for teams looking to move beyond simple scanning and take confident, proactive action.
Beyond features and capabilities, the practical aspects of pricing and deployment are often the deciding factors when choosing a new security platform. How a tool fits into your budget and how easily it integrates into your existing environment can make or break its success. Let’s look at how Hive Pro and Tenable stack up when it comes to the total cost of ownership, deployment models, and the support you can expect to receive. These logistical details are just as important as the technology itself, as they directly impact your team’s resources, time, and overall effectiveness.
When you’re evaluating software, the initial price tag is only part of the story. The total cost of ownership (TCO) gives you a much clearer picture of your long-term investment. Hive Pro is designed with a simpler, more inclusive pricing model, which often results in a lower overall TCO. Core capabilities, like integrating data from other security tools and running Breach and Attack Simulations, are typically included in the base license. This all-in-one approach means you get a comprehensive toolset without the surprise of hidden costs or necessary add-ons.
Tenable, on the other hand, often structures its offerings with a core product that can be expanded by purchasing separate, specialized modules. While this offers flexibility, it can also lead to increased costs and complexity. To get features comparable to what Hive Pro includes out of the box, you might need to invest in additional products within the Tenable ecosystem, which can significantly raise your total cost.
How a platform is deployed across your network has a major impact on your IT team’s workload and system performance. Hive Pro uses an “agentless” approach, which means you don’t need to install and maintain software on every single device. This makes the initial setup much faster and simpler. More importantly, it avoids consuming resources on your endpoints, so there’s no risk of slowing down critical systems. This streamlined method is a key part of how Hive Pro provides total attack surface management without creating a heavy operational burden.
In contrast, Tenable often relies on a software agent that needs to be installed on each asset. This agent can be quite large—up to 4 GB—and requires ongoing management to ensure it’s updated and running correctly. For large, complex environments, managing thousands of agents can become a significant time sink for your team and introduce performance overhead on the machines it’s installed on.
When you’re rolling out a critical security tool, having reliable support is non-negotiable. The good news is that both Hive Pro and Tenable understand this and offer robust support options to help you get up and running and troubleshoot any issues that arise. You can expect to find similar tiers of support from both companies, including phone support for direct access, 24/7 live support for urgent problems, and extensive online resources like knowledge bases and documentation. Since their offerings are comparable here, the best choice often comes down to your team’s specific needs and preferences during the implementation process.
A security platform is only as good as its ability to work with the tools you already have. You need a solution that fits into your existing workflows, not one that forces you to build new processes from scratch. Both Tenable and Hive Pro understand this, but they approach integration from different angles. One focuses on a massive pre-built network, while the other prioritizes deep, flexible connections that unify your security data.
Tenable’s strength lies in its vast and mature partner ecosystem. If your priority is getting up and running quickly with broad visibility, this is a significant advantage. The platform is designed to connect with a wide array of third-party tools, which is especially helpful for organizations that need to meet strict regulatory and compliance frameworks. This extensive network of pre-built integrations means you can often plug Tenable into your existing environment and start seeing value almost immediately, making it a solid choice for teams that need wide-ranging compatibility out of the box.
Hive Pro takes a more modern, API-first approach to integration. This design philosophy is all about flexibility and creating a single, unified source of truth for your security posture. Instead of relying solely on a marketplace of partners, Hive Pro allows you to seamlessly connect your essential systems—like asset management, ITSM platforms, and even other security scanners. This means you can aggregate data from tools you already own, like Qualys or Rapid7, directly into its Uni5 Xposure platform without needing extra licenses. It’s a strategy built for streamlining your vulnerability management process and making your entire tech stack work more cohesively.
Hive Pro API connections go beyond vulnerability scanners and sources, it also includes EDR products such as CrowdStrike, SentinelOne, Microsoft to test the security controls as well as push the IOCs and recommend changes in IOA to instantly block the attacks.,
No platform is perfect for everyone, and understanding the potential drawbacks is just as important as knowing the strengths. Depending on your team’s size, budget, and existing processes, what works for one organization might be a roadblock for another. Let’s look at where Tenable and Hive Pro might present challenges.
While Tenable is a powerful and established player, its biggest challenge is often its complexity and cost structure. To get a complete threat exposure management picture, you frequently need to purchase separate, expensive products within their ecosystem, like TenableOne. This can lead to a higher total cost of ownership and a more complicated management experience as your team juggles different modules. Although Tenable is a strong option for large organizations that need quick deployment and have the budget for a comprehensive, multi-product suite, this approach can be a significant hurdle for teams looking for a more unified and cost-effective solution. The need to piece together different tools can create silos and make it harder to get a single, clear view of your risk posture without a hefty investment.
As a more recent innovator in the cybersecurity space, Hive Pro doesn’t have the same long-standing market presence as a giant like Tenable. For some organizations that prioritize brand legacy, this might feel like a risk. However, this position allows Hive Pro to be more agile and focused. The platform was designed from the ground up to provide a streamlined, all-in-one experience without the baggage of legacy architecture. Hive Pro’s approach centers on a single, easy-to-understand ‘Real Risk Score’ that simplifies vulnerability and threat prioritization. While it may be the newer name, its seamless integration with over 27 common security and IT tools ensures it fits right into your existing tech stack, offering a modern, cost-effective alternative.Additionally, Hive Pro has been recognized by all the major analyst firms including Gartner in their first Magic Quadrant for EAP, Forrester, IDC, etc.
Making the final call between two strong platforms comes down to your team’s specific goals and priorities. Both Tenable and Hive Pro offer powerful tools, but they excel in different areas. Think about what your organization needs most right now: Is it broad compliance and quick deployment, or is it a more proactive, intelligence-led approach to reducing your actual risk? Answering that question will point you in the right direction.
Your choice will shape how your team identifies, prioritizes, and responds to threats. Let’s break down the ideal user for each platform to help you see where your team fits.
Tenable is a great fit for organizations that need to get up and running quickly with a solution that offers wide visibility across different environments. If your primary goals are centered on comprehensive asset discovery, broad scanning capabilities, and maintaining strong compliance, Tenable has a proven track record. It combines these functions into a single, established platform. Teams that are heavily focused on cloud security and need a tool that integrates well with existing compliance frameworks will find that Tenable meets their requirements effectively. It’s a solid choice for those who prioritize a mature, all-in-one system for traditional vulnerability management.
Hive Pro is designed for security teams who want to move beyond simply finding vulnerabilities and start proactively defending against threats. If your team is looking to consolidate security tools, simplify your tech stack, and reduce overall costs, Hive Pro offers a compelling alternative. Its unified platform provides a single, easy-to-understand ‘Real Risk Score’ that gives you a clearer picture of your true exposure by factoring in asset importance, existing security controls, and the likelihood of an attack. Choose Hive Pro if your team wants to leverage advanced intelligence to predict and get ahead of cyber threats, transforming your security program from reactive to proactive.
My team is overwhelmed with alerts. How do Tenable and Hive Pro help with prioritization? This is the core difference between the two. Tenable provides multiple data points, like its Vulnerability Priority Rating (VPR), to help you sort through findings. It’s powerful but can require your team to connect the dots between different metrics. Hive Pro simplifies this by using a single “Real Risk Score.” This score is designed to give you an immediate, clear answer by considering not just the vulnerability’s severity but also real-world threat intelligence, the importance of the asset, and your existing security controls. The goal is to point you directly to the fires you need to put out first.
What exactly is Breach and Attack Simulation (BAS), and why does it matter that it’s included with Hive Pro? Think of Breach and Attack Simulation as automated, safe “fire drills” for your security tools. It continuously tests if your defenses, like your firewall or endpoint protection, are configured correctly and would actually stop a real attack. It matters because finding a vulnerability is only half the battle; you need to know if your defenses work. Hive Pro includes BAS as a core feature, so you can validate your controls without buying a separate, expensive tool. With other solutions, this capability is often a costly add-on.
If Hive Pro is newer, does that mean it’s less powerful or only for smaller companies? Not at all. Being newer means Hive Pro was built from the ground up to solve modern security challenges without being weighed down by older architecture. Its focus is on providing a streamlined, all-in-one platform that is both powerful and easy to use. Instead of piecing together different products, you get a unified view of your risk. This modern approach is valuable for organizations of any size that want to move beyond traditional scanning and adopt a more proactive security posture.
We already use other scanners. Can Hive Pro work with them? Yes, absolutely. Hive Pro has out of box and plug-n-play integrations available with Tenable, Qualys, Rapid7 and many more. You can feed data from other scanners, like Qualys or even Nessus, directly into the Hive Pro platform. This allows you to centralize all your security findings in one place and apply Hive Pro’s advanced prioritization and threat intelligence to get a single, unified view of your risk across your entire environment.
How is Hive Pro’s ‘Real Risk Score’ different from other scoring methods like Tenable’s VPR? While a score like VPR is great at telling you how severe a vulnerability is in general, the “Real Risk Score” adds critical business context. It answers the next set of questions your team would ask anyway: Is this vulnerability on a critical server or a test machine? Are attackers actively exploiting this in the wild right now? And do we already have other security measures in place that might reduce the risk? By combining all these factors, it gives you a score that reflects the true, immediate risk to your specific organization.