Comprehensive Threat Exposure Management Platform
Attackers don’t look for the strongest part of your defense; they look for the one you forgot about. An unmanaged server, a misconfigured cloud service, or an employee’s unsecured home device can become their front door. Poor cyber exposure visibility creates these hidden entry points. The best way to strengthen your security is to see your organization through an attacker’s eyes, finding and fixing the gaps before they can. This requires a systematic approach to uncovering every asset and understanding its potential weaknesses. Here, we’ll outline the crucial steps to improve cyber exposure visibility, giving you the blueprint to map your attack surface and close those dangerous blind spots.
Before you can build a strong defense, you need to know what you’re defending. That’s the core idea behind cyber exposure visibility. It’s about having a complete and accurate picture of all your digital assets and understanding how they might be exposed to potential threats. Think of it as creating a detailed map of your entire digital footprint—every server, laptop, cloud instance, and application. Without this map, you’re navigating a complex threat landscape with major blind spots, making it nearly impossible to protect your organization effectively.
Gaining this visibility is the first and most critical step in shifting from a reactive “firefighting” mode to a proactive security stance. When you can see everything clearly, you can start making informed decisions about where to focus your resources, how to prioritize vulnerabilities, and what steps will actually reduce your risk. It’s the foundation upon which a modern, resilient cybersecurity program is built.
Your digital attack surface is the sum of all your internet-facing hardware, software, and cloud assets that an attacker could potentially exploit. Exposure management is the process your organization uses to continuously find, assess, and fix security risks across these exposed assets. Every computer, application, and cloud service that’s visible to the outside world is part of this surface. The bigger and more complex your operations are, the larger your attack surface becomes, creating more potential entry points for threats. A complete attack surface management strategy is essential for understanding the full scope of your exposure and identifying where you are most vulnerable.
Poor visibility directly weakens your security posture. With the rise of remote work and the average company using over 1,000 cloud services, the digital landscape has become incredibly fragmented. This complexity makes it difficult to track all potential weak spots, and attackers are quick to take advantage of any gaps. Without a unified view of your assets and their vulnerabilities, your team is left guessing where the next attack might come from. Achieving clear cybersecurity visibility allows you to move from guesswork to confident action. It helps you see your environment through an attacker’s eyes, enabling you to find and fix the most critical exposures before they can be exploited with a threat exposure management platform.
When you can’t see your entire digital environment, you’re essentially leaving doors and windows unlocked for attackers. Poor cyber exposure visibility isn’t just a technical oversight; it creates tangible risks that can impact every corner of your business. Without a complete picture of your assets, vulnerabilities, and potential attack paths, you’re forced to make security decisions based on incomplete information. This reactive approach means you’re always one step behind, waiting for an alert to tell you something is wrong, by which time it’s often too late.
The consequences ripple outward, affecting your finances, legal standing, and even your ability to operate. Many organizations struggle with this because digital transformation has rapidly expanded their attack surface, creating more places for threats to hide. When teams work in silos and lack the threat intelligence to connect the dots, these hidden risks fester. Understanding the specific dangers of poor visibility is the first step toward building a security program that can proactively defend your organization instead of just reacting to incidents.
Every asset you can’t see is a potential entry point for an attacker. When you lack visibility, you can’t protect what you don’t know you have. This creates gaps that threat actors are skilled at finding and exploiting, leading directly to data breaches. The financial fallout from a single breach can be staggering, encompassing everything from incident response costs and regulatory fines to customer churn and brand damage. Losses from targeted cyberattacks, malware, and phishing campaigns can easily run into hundreds of thousands of dollars. Without a clear view of your environment, you’re unable to prioritize which threats to fix first, leaving critical systems exposed while your team chases down low-impact issues.
Regulatory bodies don’t accept “we didn’t know it was there” as an excuse. Frameworks like GDPR, HIPAA, and PCI DSS mandate that you know where your sensitive data resides and have controls in place to protect it. Poor visibility makes demonstrating this compliance nearly impossible. If you can’t account for all your assets and data stores, you can’t prove they’re secure, which can result in failed audits, hefty fines, and the loss of essential certifications. Effective cybersecurity requires a team effort from IT, legal, and HR, but without a shared, accurate view of your exposure, these teams can’t collaborate effectively to meet their obligations, putting the entire organization at legal and financial risk.
For organizations that rely on operational technology (OT), the risks of poor visibility extend into the physical world. A cyberattack on an unseen or unmanaged OT asset—like a controller on a manufacturing floor or a sensor in a power grid—can halt production, disrupt supply chains, and endanger public safety. Managing OT cyber risk is incredibly challenging without a complete inventory of your connected devices and their vulnerabilities. An attack that exploits one of these blind spots can cause operational disruptions that lead to significant revenue loss and damage your reputation as a reliable partner or provider.
You can’t protect what you can’t see. It’s a simple truth that’s at the heart of cybersecurity, yet many organizations struggle with it. Before you can prioritize vulnerabilities or test your defenses, you need a complete and accurate picture of your digital footprint. This process of finding all your exposed systems and assets is the foundational first step in building a proactive security program. It’s about moving from guesswork to a clear, comprehensive understanding of your attack surface, which is the sum of all potential entry points an attacker could use to breach your network.
This isn’t just about running a quick scan of your known servers. True asset discovery means finding everything that’s connected to the internet—the web applications you built, the cloud instances your dev team spun up for a project, the marketing site hosted by a third party, and even the forgotten server in a dusty data center. Many security incidents start with an unknown or unmanaged asset. By systematically identifying every internet-facing system, you can begin to manage the risk they introduce. The following steps will walk you through how to build that complete inventory and map out your external attack surface, turning operational blind spots into areas of control.
The first order of business is to create a complete inventory of every digital asset your organization owns. Think of it as a census for your entire digital ecosystem. Your goal is to find all your systems and devices that can be reached from the internet, leaving no stone unturned. This includes web servers, applications, cloud storage, APIs, domains, and even IoT devices. A thorough discovery process gives you a single source of truth, which is essential for understanding your total attack surface. Without a complete and continuously updated asset inventory, you’re essentially flying blind, hoping attackers don’t find the gaps you don’t know exist.
Once you have a baseline inventory, it’s time to dig deeper by actively scanning your network. Using automated tools to scan your IP ranges and cloud environments helps you enumerate the specific services, open ports, and software versions running on each discovered asset. This process turns a simple list of devices into a detailed map of potential entry points. As Bitsight notes, using specialized tools to automatically find these risky areas allows you to approach remediation in a much more strategic way. This detailed enumeration is what provides the context you need to later identify and prioritize specific vulnerabilities on each asset.
One of the biggest challenges in asset discovery is finding what you don’t know you have. “Shadow IT” refers to systems and software used within an organization without explicit approval from the IT or security department. These can be anything from a cloud database set up by a developer for a quick test to a marketing team’s new analytics tool. As CISA points out, many organizations accidentally leave systems open due to misconfigurations, default passwords, or outdated software—all common characteristics of shadow IT. These rogue assets often lack proper security controls, making them low-hanging fruit for attackers and a major source of organizational risk.
After you’ve discovered and enumerated all your assets, the final step is to put it all together into a coherent map of your external attack surface. This isn’t just a list; it’s a dynamic view of how your organization looks from an attacker’s perspective. According to CrowdStrike, a key part of exposure management is figuring out how each asset could be attacked. Mapping your attack surface helps you visualize the connections between assets and identify potential attack paths. This holistic view, often provided by a unified platform like Uni5 Xposure, is what allows you to see the bigger picture and begin prioritizing your security efforts based on where you are most exposed.
Once you have a clear map of your assets, the next step is to figure out where the cracks are. Not every vulnerability carries the same weight, and your team doesn’t have unlimited time or resources. Trying to fix everything at once is a recipe for burnout and leaves you exposed where it matters most. The key is to move from a simple list of weaknesses to a prioritized action plan that focuses on the threats most likely to impact your business.
This process involves more than just running a scan and looking at the highest severity scores. True prioritization requires context. You need to understand which vulnerabilities are actively being exploited by attackers in the wild, which assets are most critical to your operations, and what the potential business impact of a breach would be. By combining automated scanning with real-world threat intelligence and a deep understanding of your own environment, you can create a focused strategy. This approach helps you direct your remediation efforts effectively, addressing the most significant risks first and building a more resilient security posture.
Manually searching for vulnerabilities across thousands of assets is impossible. This is where automated scanning tools come in. These systems continuously check your networks, applications, and devices for known weaknesses, giving you a baseline understanding of your exposure. Think of it as your first line of defense in the identification process. Using specialized tools to automatically find these risky areas allows you to build a comprehensive inventory of potential threats. This automation frees up your team to focus on the more strategic work of analysis and remediation instead of getting bogged down in manual discovery. A good vulnerability and threat prioritization process starts with a solid, automated foundation.
A long list of vulnerabilities can be overwhelming, but not all of them pose an immediate threat. This is where threat intelligence becomes your most valuable asset. By correlating data from various sources, you can identify patterns and trends that show which vulnerabilities attackers are actively targeting right now. This insight helps you cut through the noise and focus on the weaknesses that have a higher probability of being exploited. Instead of just relying on a generic severity score, you can use intelligence from research teams like HiveForce Labs to see which threats are trending and direct your attention to the vulnerabilities that attackers are actually using in their campaigns.
A critical vulnerability on a non-essential test server is less of a concern than a medium-risk one on your primary customer database. This is why context is everything. To truly prioritize, you need to score vulnerabilities based on their potential business impact. Figure out how critical each asset is by considering the sensitivity of the data it holds, its importance to daily operations, and the financial or reputational damage an attack could cause. A modern threat exposure management platform helps you combine this business context with threat intelligence and vulnerability data, giving you a true risk-based view so you can confidently decide what to fix first.
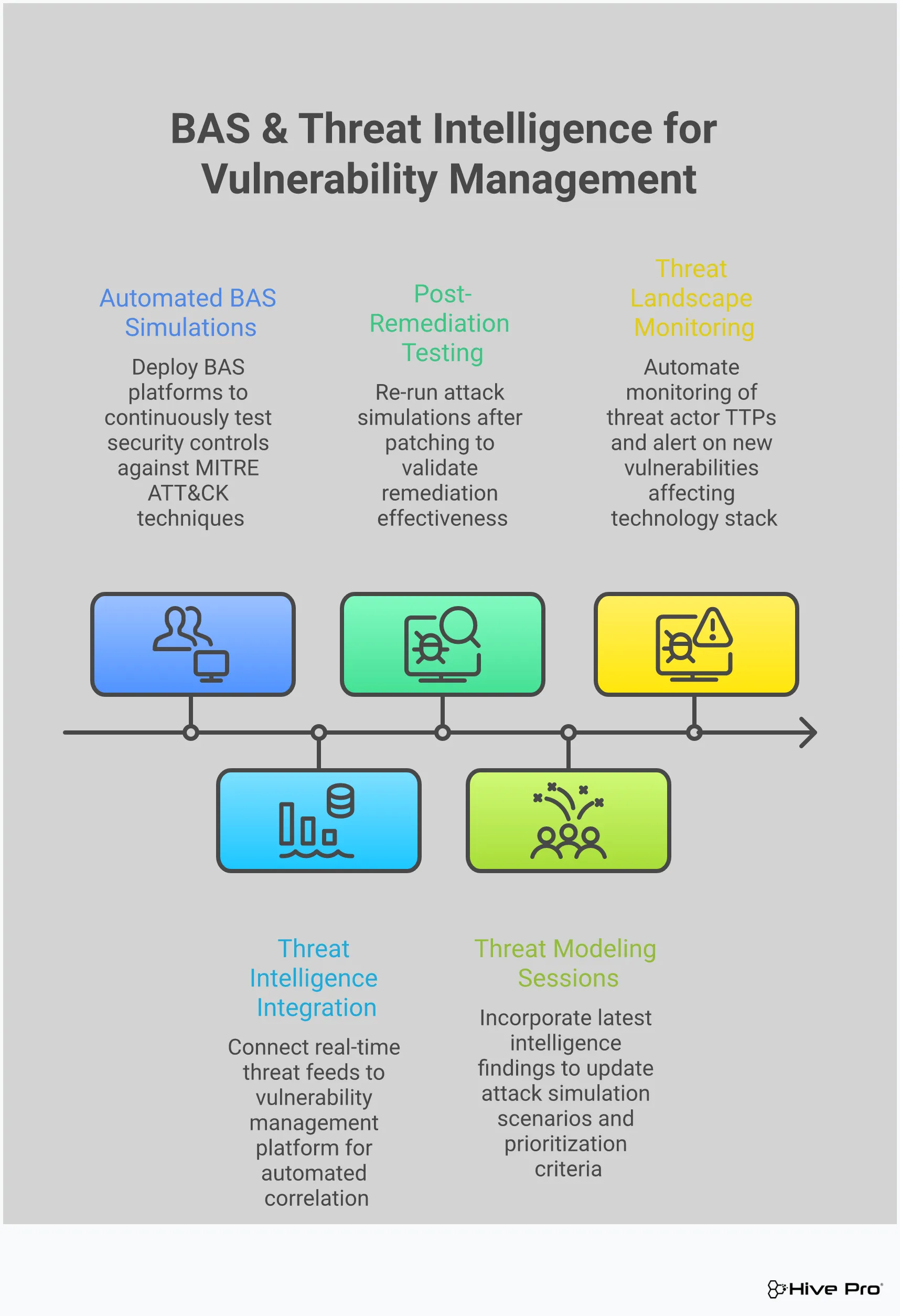
Once you’ve identified your assets and prioritized vulnerabilities, the next step is to see how your defenses actually perform against a real attack. This is where Breach and Attack Simulation (BAS) comes in. Think of it as a continuous, automated way to pressure-test your security posture. Instead of just scanning for known vulnerabilities, BAS platforms actively simulate the tactics, techniques, and procedures (TTPs) used by real-world attackers.
This proactive approach gives you a clear, evidence-based picture of your security effectiveness. You’re no longer just assuming your firewalls, EDR, and other controls are working correctly—you’re actively verifying them. By running safe, controlled attack scenarios across your environment, you can see exactly where your defenses hold up and where they fall short. This process of adversarial exposure validation is crucial for moving beyond a theoretical understanding of your risk to a practical one. It gives you visibility not just into what is vulnerable, but how it’s vulnerable and what the actual impact would be. Instead of a long list of CVEs, you get a prioritized list of attack paths that are confirmed to be exploitable in your specific environment.
You’ve invested heavily in a suite of security tools, but are they configured to stop the latest threats? BAS helps you answer that question with confidence. These tools allow you to continuously test your security controls against a library of real-world attack scenarios. By simulating everything from phishing attempts to ransomware deployment, you can assess how well your defenses respond and pinpoint weaknesses in your security posture. This isn’t a one-time check; it’s an ongoing process that ensures your controls remain effective as the threat landscape and your own environment evolve. It’s the difference between having a fire alarm and actually testing it to make sure it works.
Patching a vulnerability is one thing; confirming the fix actually works is another. After your team addresses a critical vulnerability, how do you know the risk is truly gone? BAS provides a straightforward way to validate your remediation efforts. By re-running the specific attack simulation that targeted the vulnerability, you can get immediate confirmation that the fix was effective. If the simulated attack fails, you have concrete proof that you’ve closed the gap. This creates a powerful feedback loop that strengthens your entire vulnerability management program and ensures your efforts are making a real impact on your security posture.
Even the best preventative controls can sometimes be bypassed. That’s why your ability to detect and respond to threats is just as important. BAS is an excellent tool for identifying gaps in your detection capabilities. By analyzing how quickly and accurately your security systems detect the simulated attacks, you can get a clear sense of your team’s readiness. Did your SIEM generate an alert? Was it a high-fidelity alert that your SOC team could act on, or was it lost in the noise? These insights allow you to fine-tune your detection rules, improve alert mechanisms, and shorten your overall incident response times.
Gaining a clear view of your cyber exposure isn’t something you can do with spreadsheets and manual checks alone. You need the right technology to automate discovery, analyze risk, and provide a complete picture of your attack surface. The right tools don’t just show you what you have; they help you understand where your most significant risks are so you can act decisively. Think of these tools as your command center, bringing all the critical data together so you can make smarter, faster security decisions. Let’s look at a few key categories of tools that can give you the visibility you need.
Think of a Threat Exposure Management platform as the central nervous system for your security program. Instead of juggling multiple tools and dashboards, these platforms consolidate data from across your entire environment into a single, unified view. Hive Pro’s Uni5 Xposure Platform, for example, empowers security leaders with visibility into their attack surface, eliminating blind spots and providing actionable insights to manage vulnerabilities effectively. This holistic approach allows you to see how different risks connect and which ones pose the most immediate threat to your business, helping your team move from simply managing vulnerabilities to proactively reducing your overall exposure.
Your digital attack surface is constantly changing as new devices connect, software is updated, and cloud environments scale. Continuous monitoring and scanning solutions are designed to keep up with this dynamic pace. You can use automated tools to find assets, check risks, prioritize, and guide remediation. This is crucial because manual checks are far too slow to catch fleeting vulnerabilities or misconfigurations that could open the door for an attacker. By continuously scanning your total attack surface, these solutions provide a real-time feed of your security posture, allowing you to spot and fix issues as they appear, not days or weeks later.
You can’t protect what you don’t know you have. Asset discovery and vulnerability management systems are the foundational tools for building visibility. Asset discovery tools automatically find and catalog every device, application, and cloud service connected to your network, including shadow IT. Once you have a complete inventory, vulnerability management systems scan those assets for known weaknesses. Modern systems go a step further by helping you with vulnerability and threat prioritization. They use threat intelligence and business context to pinpoint which flaws are most likely to be exploited, so your team can focus on fixing the problems that matter most.
Setting up continuous monitoring means moving away from periodic, point-in-time security checks and toward a state of constant vigilance. Your digital environment is always changing—new assets come online, software is updated, and configurations are tweaked. A
Manual security checks can’t keep up with the scale and speed of modern IT environments. That’s why automated scanning is the backbone of any continuous monitoring program. These tools work around the clock to identify vulnerabilities, misconfigurations, and other security weaknesses across your entire digital footprint, from on-premise servers to cloud instances. The key is to configure these systems to not only find issues but also to generate immediate, context-rich alerts. This ensures the right information gets to the right team quickly, cutting down the time between discovery and remediation. A well-implemented attack surface management process automates this discovery so you can focus on fixing what matters.
A long list of vulnerabilities isn’t very useful on its own. To make it actionable, you need to know which of those vulnerabilities attackers are actively exploiting. Integrating real-time threat intelligence feeds into your monitoring process provides that crucial context. This data helps you see your vulnerabilities through the eyes of an attacker, highlighting the ones that pose an immediate and genuine threat to your organization. By correlating your scan data with up-to-the-minute intelligence, you can prioritize threats based on real-world risk, not just a generic severity score. This allows your team to focus their limited resources on fixing the most critical exposures first.
Automation is powerful, but it needs to be guided by a clear strategy. Scheduling regular reassessments ensures your continuous monitoring program remains effective and aligned with your business goals. These reviews are an opportunity to validate that your security controls are working as intended, identify any gaps in your visibility, and adjust your scanning and alerting rules. This is also the perfect time to run adversarial simulations to test your defenses against the latest attack techniques. Because both your environment and the threat landscape are constantly evolving, these periodic check-ins are essential for maintaining a strong and adaptive security posture.
You can’t manage what you can’t measure. As you work to improve your cyber exposure visibility, you need clear metrics to track your progress. Without them, you’re just guessing whether your efforts are paying off. Measuring your improvements helps you demonstrate the value of your security program, justify investments in new tools, and show leadership that you’re effectively reducing risk. It transforms security from a cost center into a strategic business function.
The right metrics give you a baseline to compare against, allowing you to see tangible results over time. Are you finding critical threats faster? Are you closing security gaps more efficiently? Are you seeing more of your attack surface than you were last quarter? These are the questions you need to answer with hard data. By focusing on a few key performance indicators (KPIs), you can create a clear narrative about your security posture and how it’s maturing. This data-driven approach helps you refine your strategy, allocate resources more effectively, and keep your team focused on what truly matters: protecting the organization from real-world threats.
One of the most direct ways to measure visibility is to track how long it takes your team to spot a potential threat. Key metrics like Mean Time to Identify (MTTI) and Mean Time to Detect (MTTD) are your best friends here. These aren’t just buzzwords; they are critical indicators of your security team’s efficiency. A lower MTTD means you’re finding threats faster, giving attackers less time to move through your network. Tracking these figures over time shows whether your new tools and processes are actually sharpening your detection capabilities. A consistently decreasing trend is a clear sign that your visibility is improving and your security posture is getting stronger.
Effective visibility isn’t just about finding vulnerabilities; it’s about how well you manage them. Instead of just counting the number of open CVEs, focus on metrics that show effectiveness. How long does it take your team to patch critical vulnerabilities after they’re discovered? What percentage of your most severe exposures are remediated within your policy timeframe? Using a vulnerability and threat prioritization tool helps you focus on the risks that matter most, so you can measure your team’s performance against the threats that are actively being exploited. This shifts the conversation from “how many” to “how well,” which is a much better indicator of your program’s maturity.
You can’t protect what you don’t know you have. A foundational metric for visibility is asset coverage—the percentage of your digital environment that you are actively monitoring. The first step is to create a complete inventory of all your digital assets, including everything from web apps and APIs to cloud services and IoT devices. From there, you can measure what percentage of those assets are covered by your security tools. Aim to continuously increase this number. A high coverage percentage means you have fewer blind spots, which is essential for building a comprehensive total attack surface management program and reducing the chances of an unknown asset becoming your next entry point.
Even with a solid strategy, certain operational realities can create visibility gaps. The modern IT landscape is constantly changing, with new devices, cloud services, and remote work setups adding layers of complexity. These shifts can quickly outpace traditional security measures, leaving you with blind spots where you can least afford them. Addressing these common challenges head-on is not just about plugging holes; it’s about building a more resilient and adaptive security posture.
The key is to recognize that visibility isn’t a one-time project. It requires a continuous effort to adapt to new technologies and working models. From the explosion of remote endpoints to the dynamic nature of cloud infrastructure, each area presents unique hurdles. By focusing on these specific challenges, you can develop targeted strategies to ensure your visibility keeps pace with your organization’s growth and evolution. This proactive approach helps you stay ahead of potential threats that thrive in the shadows of your network.
The shift to remote and hybrid work has dissolved the traditional network perimeter. Your attack surface now includes employee home networks, personal devices, and various SaaS applications. Without a centralized way to monitor these distributed assets, it’s easy for unmanaged devices or misconfigured software to become entry points for attackers. Good visibility is essential to keep these setups secure, as unseen vulnerabilities can expose your company’s sensitive data to malware or unauthorized access.
To close these gaps, you need a solution that provides a unified view of your entire digital footprint, no matter where assets are located. This means implementing tools that can continuously discover and assess endpoints, cloud services, and on-premise systems. By maintaining a comprehensive inventory, you can ensure that security policies are applied consistently across your entire total attack surface and that you can quickly identify and respond to threats emerging from your remote workforce.
Cloud adoption has been a game-changer for business agility, but it also introduces significant visibility challenges. Cloud environments are ephemeral and highly dynamic, with resources being spun up and down in minutes. This constant change makes it difficult for traditional scanning tools to keep up, often leading to an incomplete or outdated picture of your cloud assets and their associated vulnerabilities. As your organization’s digital transformation increases the attack surface, you need a way to see and secure these new environments effectively.
Managing cloud exposure requires a modern approach that combines continuous monitoring with contextual threat intelligence. Instead of relying on periodic scans, you need a platform that automatically discovers new cloud assets and assesses them for vulnerabilities in real time. The Uni5 Xposure platform helps you identify threats across multi-cloud and hybrid environments, giving you the clarity needed to prioritize and remediate the most critical risks before they can be exploited.
Technology can solve many visibility problems, but the human element remains a critical factor. Many cyberattacks succeed because of simple human error, such as an employee clicking on a phishing link or using a weak password. While you can’t monitor every single action, improving visibility into system configurations and user access patterns can help you identify risky behaviors that could lead to a breach. A strong security awareness program is your best defense against these types of threats.
Fostering a culture of security empowers your employees to become active participants in defending the organization. Regular training can teach them how to spot phishing attempts, use strong authentication, and handle sensitive data responsibly. When your team understands the “why” behind security policies, they are more likely to follow them. This creates a powerful combination: a well-informed workforce supported by technology that provides the visibility needed to catch mistakes before they become disasters.
Maintaining clear visibility across your digital landscape isn’t a one-and-done project; it’s a continuous discipline. Think of it like maintaining a garden. You can’t just plant the seeds and walk away; you have to consistently weed, water, and watch for pests. Similarly, a strong security posture requires ongoing attention to your asset inventory, regular assessments of your defenses, and clear communication channels across your entire organization.
Putting these practices into place helps you move from a reactive state of putting out fires to a proactive one where you can anticipate and neutralize threats before they cause damage. It’s about building a resilient security program that adapts as your business and the threat landscape evolve. By embedding these habits into your operations, you create a sustainable framework for managing and reducing your cyber exposure over the long term.
You can’t protect what you don’t know you have. That’s why a complete and accurate asset inventory is the foundation of any effective security program. In today’s dynamic environments—with cloud services, remote endpoints, and IoT devices constantly connecting to your network—manually tracking every asset is nearly impossible. Finding all your systems and devices that can be reached from the internet is the critical first step.
An automated approach to total attack surface management is essential for keeping up. These tools continuously scan your environment to discover and catalog every asset, from servers and laptops to cloud instances and web applications. This gives you a real-time, comprehensive view of your entire digital footprint, ensuring no system is left unmonitored or unprotected. An accurate inventory is the single source of truth that informs every other security activity.
Once you know what assets you have, the next step is to understand how well they’re protected. Regular security posture assessments are like routine health check-ups for your organization. They go beyond simple vulnerability scans to evaluate the effectiveness of your security controls, configurations, and overall defense strategy. These checks help you confirm that your security plans are working as intended and identify new risks that may have emerged.
Conducting these assessments helps you answer critical questions: Are our firewalls configured correctly? Are our access controls too permissive? Are our endpoint detection systems actually catching threats? By regularly validating your defenses through methods like adversarial exposure validation, you can find and fix weaknesses before an attacker does. This proactive approach ensures your security posture remains strong and resilient against evolving threats.
Cybersecurity is a team sport, and your IT or security department can’t go it alone. Effectively managing cyber exposure requires input and collaboration from across the business. It’s important to form a cross-functional team that includes members from IT, legal, communications, sales, and HR to manage and respond to security challenges together. Each department brings a unique perspective and set of responsibilities to the table.
For example, your legal team needs to understand the compliance implications of a vulnerability, while your communications team must be prepared to manage public perception during an incident. Building clear, documented workflows ensures everyone knows their role and can act quickly and cohesively when a threat arises. A platform that provides a unified view of cyber risks can serve as a common ground, giving all stakeholders the shared data they need to make informed decisions and work together effectively.
What’s the real difference between just scanning for vulnerabilities and having true cyber exposure visibility? Think of vulnerability scanning as making a list of all the unlocked doors and windows in your house. It’s a critical step, but it’s just a list. True cyber exposure visibility is like having the complete architectural blueprints. It shows you not only the unlocked windows but also how someone could get to them from the street, what valuable items are in that room, and whether the motion sensors in that area are actually working. It connects the dots between a single weakness and the potential business impact.
My team is overwhelmed with vulnerabilities. How does threat intelligence help us focus on what actually matters? Threat intelligence acts as a filter that separates the theoretical risks from the actual, immediate threats. Your scanner might find a hundred vulnerabilities, but threat intelligence can tell you that attackers are actively and successfully exploiting only three of them in your industry right now. This allows you to stop chasing every single alert and instead direct your team’s limited time and energy toward fixing the specific problems that are most likely to cause a breach.
How is Breach and Attack Simulation (BAS) different from a regular vulnerability scan? A vulnerability scan tells you where you have a weakness, like an unlocked door. A Breach and Attack Simulation actually tries to open that door, walk inside, and see what it can access. BAS platforms safely mimic the actions of real attackers to test if your security controls—like your EDR or firewall—are configured correctly and would actually stop an attack. It validates your defenses and shows you the entire attack path, not just the initial entry point.
We have a lot of remote workers. Where should we start to get a better handle on our visibility gaps? The first and most important step is to get a complete inventory of all the assets being used, regardless of their location. You need to find all the laptops, cloud applications, and personal devices that connect to your company data. Once you have that full picture, you can start applying consistent security policies and monitoring to everything, not just what’s inside the old office network. This closes the gaps created when your perimeter dissolved.
Why is a complete asset inventory considered the foundation for everything else? Simply put, you can’t secure what you don’t know exists. An accurate and continuously updated asset inventory is your single source of truth. Without it, every other security effort is based on incomplete information. You might have the best vulnerability scanner and the most skilled security team, but if they don’t know about a server a developer spun up in the cloud, that server remains unpatched, unmonitored, and a wide-open door for an attacker.