Comprehensive Threat Exposure Management Platform
Attackers don’t care about your long list of CVEs. They look for the path of least resistance to your most valuable assets. So, why are we still managing security from a defender’s checklist instead of an attacker’s playbook? A modern security program needs to see the entire attack surface through an adversary’s eyes. This is the core principle of cyber threat exposure management (CTEM), a continuous five-stage cycle that helps you identify, prioritize, and validate the security gaps that pose a genuine threat. By simulating real-world attack paths and testing your security controls, you can move from theoretical risk to practical proof, giving you the confidence to fix what truly matters before it can be exploited.
Cyber Threat Exposure Management, or CTEM, is a continuous security program designed to help you see your organization from an attacker’s perspective. It moves beyond simply listing vulnerabilities by combining threat intelligence, attack surface monitoring, and risk-based analysis. The goal is to find, prioritize, and fix the security gaps that pose a real threat to your business before they can be exploited. This isn’t just about CVEs; an “exposure” can be anything an attacker could use, from a misconfigured cloud service and an exposed API to weak credentials. CTEM provides a framework for continuously asking, “What are our most critical assets, and what are the most likely ways an attacker could compromise them?” It’s a strategic, ongoing cycle rather than a one-off project, focused on building a security posture that is proactive and always adapting to the evolving threat landscape. This approach helps you cut through the noise of endless alerts to focus on what truly matters.
For years, security teams have been stuck in a reactive cycle: scan for vulnerabilities, get a massive list, and then scramble to patch everything. This approach is overwhelming and often leaves critical exposures unaddressed. CTEM flips the script by shifting the focus from reactive patching to proactive risk reduction. Instead of trying to fix every single flaw, you concentrate on the exposures that are most likely to be targeted and would cause the most damage. This forward-looking strategy helps you manage your threat exposure continuously, ensuring your team’s efforts are always directed at the most significant risks to your business-critical assets.
At its heart, CTEM is built on a five-stage lifecycle that provides a structured approach to reducing your threat exposure. These stages are Scoping, Discovery, Prioritization, Validation, and Mobilization. This framework guides you from identifying what’s most important to your business all the way through to confirming that a fix is effective. The core idea is to create a repeatable process that helps you find all your assets, prioritize risks based on real-world threats, validate that those risks are actually exploitable, and then mobilize your teams to take action. This continuous security process ensures you’re not just patching vulnerabilities, but actively strengthening your defenses against likely attacks.
If you’ve worked in cybersecurity for any length of time, you’re familiar with vulnerability management (VM). For years, it’s been the standard practice for finding and fixing software flaws. But as digital environments have grown more complex and attackers more sophisticated, the limitations of this traditional model have become painfully clear. It’s not just about finding vulnerabilities anymore; it’s about understanding your true exposure to threats.
Continuous Threat Exposure Management (CTEM) represents a fundamental shift from the reactive cycle of traditional VM. Instead of just scanning for known issues, a CTEM program provides a continuous, proactive way to see your organization through an attacker’s eyes. It moves beyond a simple list of CVEs to answer the most important questions: Which of these vulnerabilities actually matter to my business? Which ones are attackers actively using? And what is the real-world risk if we don’t fix them? This change in perspective helps security teams break free from the endless cycle of patching and focus their efforts where they will have the greatest impact.
Let’s be honest: traditional vulnerability management often feels like a losing battle. Security teams run scans and are handed a massive, overwhelming list of thousands—sometimes millions—of potential issues. The process becomes more about documenting problems than actually solving them. This approach is inherently reactive, focusing on software flaws in isolation without considering the broader context. It often prioritizes vulnerabilities based on a generic CVSS score, which doesn’t account for your unique environment, the presence of compensating controls, or whether a threat actor is even exploiting that flaw in the wild. This lack of context leaves teams struggling to decide what to fix first, leading to burnout and a constant state of chasing yesterday’s problems.
CTEM flips the script by implementing a proactive, continuous cycle. Instead of periodic scans, it offers a constant evaluation of your security posture across your entire attack surface. This isn’t a one-and-done project; it’s an ongoing strategy to identify, prioritize, and validate your exposures in near real-time. By adopting a risk-based view, you can move beyond just the technical severity of a flaw. A CTEM platform helps you understand the potential business impact of an exposure, allowing you to prioritize fixes that protect your most critical assets. This continuous loop ensures that your security efforts are always aligned with the current threat landscape and your specific business goals, helping you stay ahead of attackers.
The real power of CTEM lies in its ability to connect vulnerabilities to real-world threats. A simple scan can tell you a vulnerability exists, but it can’t tell you how dangerous it truly is. CTEM enriches vulnerability data by integrating it with attack surface management and up-to-the-minute threat intelligence. This fusion of information helps you see which weaknesses attackers are actively targeting and which parts of your infrastructure are most at risk. By understanding the real danger of an exposure, not just its theoretical severity, you can make much smarter decisions. This intelligence-driven approach to vulnerability and threat prioritization is what separates a modern exposure management program from a legacy VM tool.
A successful CTEM program follows a continuous, five-stage cycle. Think of it less as a linear checklist and more as a loop that constantly refines your security posture. Each stage builds on the last, helping you move from simply finding vulnerabilities to proactively reducing your real-world exposure. Let’s walk through what each stage looks like in practice.
You can’t protect what you don’t know is important. The first step is to define which of your digital assets are most critical to your business operations. This isn’t just about servers and databases; it includes customer data, intellectual property, and the applications that keep your business running. Scoping involves mapping out these key assets, both internal and external, and understanding their business value. This process sets the boundaries for your security efforts, ensuring you focus your resources on protecting the systems and data that matter most. It’s the foundational step that informs every decision you make down the line.
Once you know what’s critical, you need to see it from an attacker’s perspective. This stage involves continuously discovering and mapping your entire attack surface. This goes beyond traditional network scans to include cloud environments, on-premise infrastructure, and even third-party services connected to your operations. The goal is to uncover every potential exposure point—from unpatched software and system misconfigurations to exposed credentials and shadow IT. Because your environment is always changing, this discovery process can’t be a one-time event. It has to be a continuous effort to maintain an accurate, up-to-date inventory of your assets and their associated weaknesses.
Not all vulnerabilities are created equal. With thousands of potential issues, you need a smart way to decide what to fix first. This is where prioritization comes in. Instead of relying solely on generic CVSS scores, a CTEM approach uses threat intelligence to prioritize exposures based on real-world risk. You’ll focus on questions like: Is this vulnerability being actively exploited in the wild? Is it part of a known attacker’s playbook? What would be the business impact if it were compromised? By layering threat context over your vulnerability data, you can cut through the noise and direct your team’s attention to the handful of issues that pose a genuine, immediate threat.
Just because a vulnerability exists doesn’t mean it’s exploitable in your specific environment. The validation stage is where you test your assumptions. By simulating real-world attacks, you can confirm whether an identified weakness can actually be used to breach your defenses. This process, often done using Breach and Attack Simulation (BAS) tools, helps you understand how an attacker might move through your systems and whether your existing security controls are effective. It’s about moving from theoretical risk to practical proof. This step provides concrete evidence to justify remediation efforts and helps you fine-tune your security controls based on how they perform against realistic threats.
The final stage is all about taking action. Once you’ve identified, prioritized, and validated your most critical exposures, it’s time to mobilize the right people to fix them. This involves more than just sending a ticket to the IT team. Effective mobilization requires clear communication and streamlined workflows to ensure the right stakeholders are engaged and accountability is established. A central platform can help coordinate remediation by assigning tasks, tracking progress, and verifying that fixes have been implemented correctly. This closes the loop, ensuring that insights from the previous stages translate into a tangible reduction in your organization’s cyber risk.
A long list of vulnerabilities without context is just noise. It tells you what is broken, but not why it matters or what you should fix first. This is where threat intelligence comes in, acting as the critical filter that turns a flood of data into a clear, actionable plan. It’s the difference between chasing every potential weakness and strategically defending against actual, ongoing attacks. By integrating real-world threat data into your exposure management program, you shift from a reactive posture, driven by generic severity scores, to a proactive one, guided by how attackers are operating right now.
This intelligence-led approach is the core of modern cybersecurity. Instead of treating all vulnerabilities equally, you can pinpoint the ones that pose a genuine, immediate threat to your organization. This means understanding which weaknesses are being actively exploited in the wild, who is exploiting them, and what their motives are. With this insight, your security teams can stop wasting time on low-risk issues and concentrate their efforts where they will have the greatest impact: on the exposures that attackers are most likely to target. This strategic focus not only strengthens your defenses but also makes the most of your team’s limited time and resources.
A vulnerability’s CVSS score tells you its potential severity in a vacuum, but it doesn’t tell you if it’s a real threat to your specific environment. Threat intelligence adds that essential real-world context. It helps you understand if a particular vulnerability on a critical, internet-facing server is part of a known attack chain. This process of vulnerability and threat prioritization transforms your perspective, allowing you to see risks through the eyes of an attacker. You can then map these threats directly to your assets, validate their exploitability, and make informed decisions based on tangible risk rather than theoretical severity.
Attackers don’t use every vulnerability in existence; they focus on a select few that offer the most reliable path to their objectives. A key function of threat intelligence is to identify which vulnerabilities are currently being exploited “in the wild.” This information, often gathered by security research teams like HiveForce Labs from sources like the dark web and global honeypot networks, is a game-changer. It allows your team to immediately separate the handful of actively exploited vulnerabilities from the thousands of theoretical ones. This focus ensures you are always working on fixing the security gaps that present the most immediate danger to your organization.
Effective defense requires knowing your enemy. Threat intelligence provides deep insights into how attackers operate, including their preferred tactics, techniques, and procedures (TTPs). By analyzing this data, you can understand if a threat actor group known for targeting your industry is using a specific vulnerability in their campaigns. This context helps you anticipate their next move and strengthen your defenses accordingly. For instance, knowing a vulnerability is typically used for initial access versus lateral movement informs not just your patching schedule but also your monitoring and incident response plans, as detailed in regular threat advisories.
Ultimately, threat intelligence allows you to focus your resources on what’s actually being attacked. By combining data on active exploits with an understanding of threat actor behavior and the context of your own environment, you can build a highly effective, risk-based remediation plan. This intelligence-driven approach, central to a Continuous Threat Exposure Management (CTEM) platform, moves you beyond the noise of endless alerts. It helps your team confidently answer the most important question: “Of all the things we could fix, what do we need to fix right now to prevent a breach?”
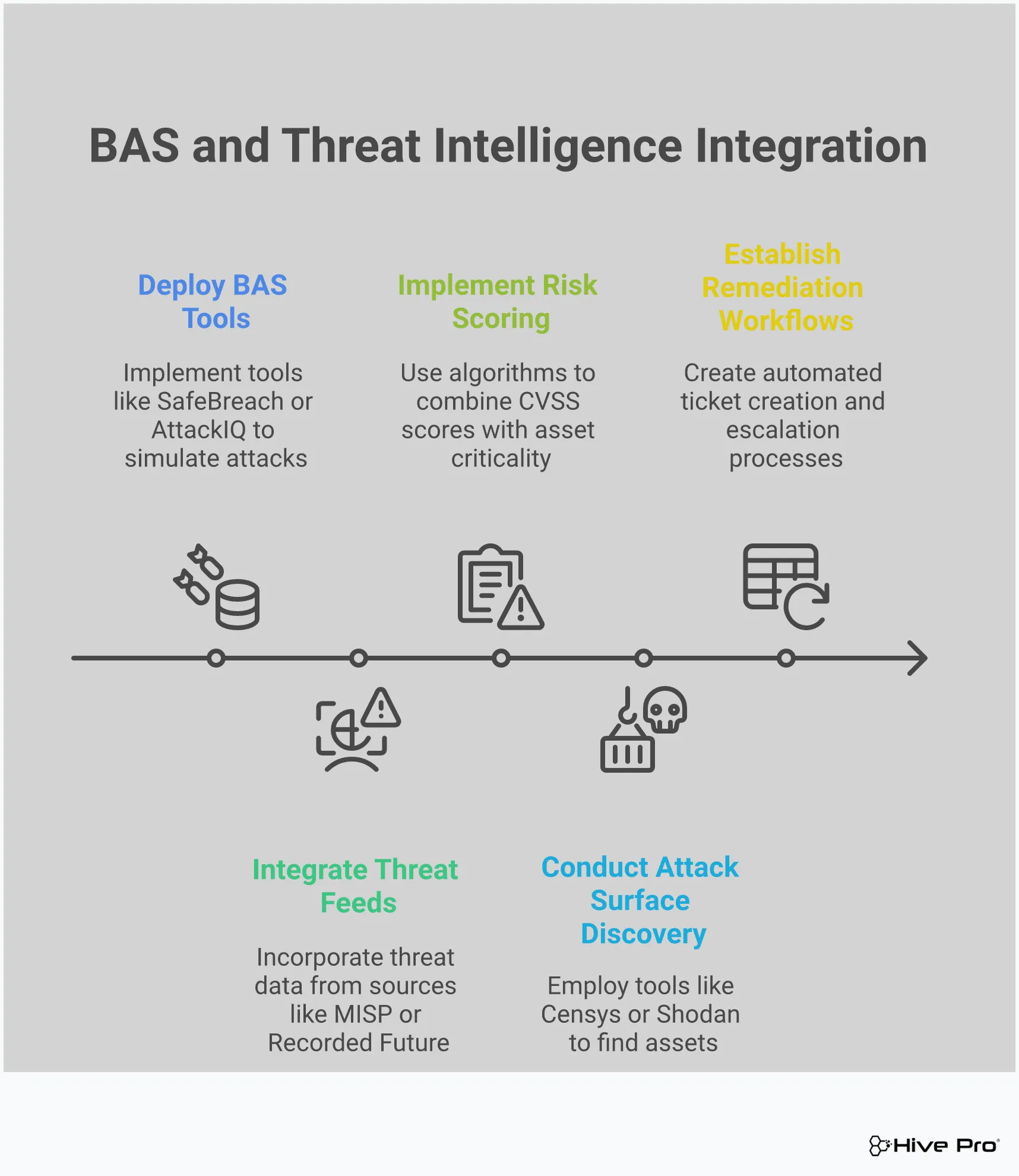
After you’ve prioritized your vulnerabilities using threat intelligence, the next logical step is to validate them. This is where Breach and Attack Simulation (BAS) comes in. Think of it as a reality check for your security posture. While vulnerability scans tell you where the cracks are, BAS tells you if an attacker could actually slip through them. It moves you from a theoretical understanding of risk to a practical one. BAS platforms safely and automatically simulate the techniques real attackers use, from initial access to lateral movement. This process helps you see exactly how your defenses would hold up against a genuine threat. Instead of just having a list of CVEs, you get a clear picture of the attack paths an adversary could take through your network. This adversarial exposure validation is a core part of a modern CTEM program because it helps you confirm which exposures present a clear and present danger. It answers the crucial “so what?” question for every vulnerability, providing the evidence needed to drive action and prove that your security investments are working, allowing you to focus your remediation efforts where they will have the most impact.
It’s one thing to know a vulnerability exists; it’s another to know if it’s exploitable in your specific environment. A vulnerability might be technically severe, but if it’s on an isolated system with multiple layers of security controls in front of it, the actual risk could be low. BAS helps you cut through the noise by running controlled, simulated attacks against your assets. This testing confirms whether a potential weakness can actually be used by an attacker to compromise a system or move through your network. It’s the difference between having a long list of possibilities and a short, actionable list of certainties.
You’ve invested heavily in firewalls, endpoint detection and response (EDR), and other security tools. But are they configured correctly? Are they actually working as intended? BAS helps you answer these critical questions by putting your security stack to the test. By simulating real-world attack scenarios, you can see if your controls detect and block malicious activity as expected. This process often reveals misconfigurations, policy gaps, or tools that aren’t performing up to par. It’s like running a fire drill for your security team and technology, ensuring everything works together to protect your organization when a real attack happens.
Your IT environment is constantly changing. New assets are added, software is updated, and configurations are modified. At the same time, attackers are always developing new techniques. A one-time security assessment or annual penetration test quickly becomes outdated. This is why continuous validation is so important. A CTEM program integrates BAS as an ongoing process, constantly testing your defenses against the latest threats. This continuous feedback loop allows your security team to find and address weaknesses as soon as they appear, making your entire security posture more resilient over time.
Ultimately, BAS transforms your security data from theoretical to practical. It takes the abstract concept of a vulnerability and shows you the concrete impact it could have on your business. By demonstrating a successful attack path, you can clearly communicate risk to stakeholders and justify the need for specific remediation actions. This moves your team away from a reactive cycle of just patching vulnerabilities and toward a proactive strategy of eliminating the most critical exposures. You can finally focus your resources on fixing the problems that truly matter.
Adopting a Continuous Threat Exposure Management (CTEM) program is more than just a procedural shift; it’s about fundamentally changing how your organization approaches security. Instead of constantly reacting to an endless stream of alerts, you can start making strategic, data-driven decisions that genuinely reduce risk. The real value of CTEM lies in its tangible outcomes: faster response times, a clearer understanding of your security landscape, and the ability to allocate your resources where they’ll have the greatest impact.
By moving away from traditional vulnerability management, which often leaves teams overwhelmed and unsure of where to start, CTEM provides a clear path forward. It helps you connect the dots between a specific vulnerability, the asset it affects, and the real-world threats targeting it. This context is a game-changer, allowing you to prioritize with confidence and communicate risk effectively to leadership. Ultimately, a CTEM program empowers your team to stop chasing ghosts and start neutralizing the actual threats that could disrupt your business. It’s about building a more resilient, proactive, and efficient security operation from the ground up.
One of the most immediate benefits of a CTEM program is the dramatic reduction in the time it takes to fix critical vulnerabilities. Instead of drowning in a sea of “critical” and “high” severity alerts, your team can focus on the small fraction of exposures that pose a genuine, immediate threat. With a platform that provides advanced vulnerability and threat prioritization, you can quickly pinpoint the 1% of risks where an attack is most likely to happen. This laser focus allows teams to cut through the noise and direct their efforts toward what truly matters, significantly speeding up remediation cycles and reducing your overall exposure in record time.
Traditional security tools often operate in silos, giving you a fragmented picture of your risk landscape. A CTEM program brings everything together, offering a unified and comprehensive view of your security posture. By continuously mapping your entire attack surface and correlating vulnerabilities with threat intelligence, you gain a clear understanding of how exposures align with your most critical business functions. This holistic perspective, available through a single threat exposure management platform, makes it easier to report on risk to the board, justify security investments, and ensure your cybersecurity efforts are directly supporting key business goals. You’re no longer just managing vulnerabilities; you’re managing business risk.
Every security team operates with finite resources—time, budget, and personnel. CTEM ensures you make the most of every one. By prioritizing threats based on real-world exploitability and business impact, you can stop wasting valuable time on low-risk issues. This focused approach means your team’s efforts are always directed at the most critical exposures, leading to a more efficient security operation and a stronger defense. Organizations that implement CTEM consistently experience fewer security incidents because they are proactively addressing the right problems. This shift not only strengthens security but also improves resource efficiency, allowing you to achieve more with the budget you have.
The core promise of CTEM is the shift from a reactive to a proactive security stance. Instead of waiting for an attack to happen, you can continuously identify and neutralize potential threats across your entire attack surface. CTEM is an ongoing, cyclical process of discovery, prioritization, validation, and remediation that keeps you one step ahead of attackers. This proactive strategy allows you to anticipate how a threat actor might target your organization and close those security gaps before they can be exploited. By embracing a continuous threat exposure management framework, you build a resilient security program that adapts to the ever-changing threat landscape.
Adopting a CTEM program is a game-changer, but let’s be real—it’s not always a simple plug-and-play process. Shifting from a traditional, reactive security model to a proactive one involves overcoming a few common hurdles. Understanding these challenges upfront is the first step to building a strategy that sidesteps them. From blind spots in your network to getting different teams to work together, here are the main obstacles you might face on your path to implementing CTEM.
You can’t protect what you don’t know you have. One of the biggest initial challenges is getting a complete picture of your attack surface. It’s no longer just about the servers in your data center; it’s about cloud instances, SaaS applications, partner APIs, and remote employee devices. If your discovery process misses these assets, you’re left with dangerous blind spots. An effective CTEM program starts with a continuous and comprehensive asset discovery process that sees everything, both internally and externally, so you have a true inventory of what needs protecting.
A long list of vulnerabilities is more noise than signal. Your scanner might flag thousands of issues, but without context, it’s impossible to know where to start. Which vulnerabilities are actively being exploited by threat actors right now? Which ones expose your most critical business applications? Just knowing a CVE exists isn’t enough. The real challenge is connecting that vulnerability to its potential business impact and the likelihood of an attack. This is where you need to prioritize threats based on real-world intelligence, not just a generic severity score, to focus your team’s efforts where they count.
Your security stack can sometimes feel like a collection of tools that refuse to talk to each other. When your asset inventory, vulnerability scanner, and threat intelligence platform operate in silos, your team is left to manually connect the dots. This patchwork approach is not only inefficient but also prone to error, making it difficult to get a clear and accurate picture of your true exposure. A successful CTEM program relies on a unified view that brings all this disparate data together, automating the correlation process and giving you a single source of truth for your security posture.
Implementing CTEM isn’t just a technical project; it’s a cultural shift. Often, the biggest hurdle is getting buy-in from different teams that are used to working in their own worlds. Security, IT operations, and development teams may have different priorities and processes. Getting everyone to collaborate effectively requires clear communication and shared goals. The key is to frame CTEM not as another security mandate, but as a way to make everyone’s job easier by focusing remediation efforts on the risks that truly matter to the business, reducing alert fatigue and wasted cycles for all involved.
Putting a Continuous Threat Exposure Management (CTEM) program into practice is less about flipping a switch and more about adopting a new mindset. It’s a strategic shift that aligns your security efforts with your business goals, moving your team from a reactive cycle of patching and praying to a proactive state of control. Success hinges on a few core pillars: comprehensive visibility, clear processes, strong collaboration, and the right technology to tie it all together. By focusing on these areas, you can build a sustainable framework that not only identifies your most critical risks but also gives you a clear path to addressing them before they can be exploited.
You can’t protect what you don’t know you have. The first step in any successful CTEM program is getting a complete, continuous picture of your entire attack surface. This means looking beyond your on-premise servers and known applications. You need total visibility into everything, from internal software and cloud assets to external-facing infrastructure and even third-party systems that connect to your network. A comprehensive approach to Total Attack Surface Management combines asset discovery, vulnerability scanning, and digital risk monitoring to create a single, unified inventory. This foundational view is what allows you to accurately scope, discover, and ultimately manage your true exposure.
Finding and prioritizing vulnerabilities is only half the battle. Once you know what needs fixing, you need a clear and efficient process to get it done. This means establishing well-defined remediation workflows that connect your security findings to your IT and DevOps teams. When a critical exposure is identified, who is responsible for the fix? What’s the SLA? A solid CTEM program integrates with ticketing and IT service management systems to automate ticket creation and assign tasks to the right people. This removes manual handoffs and ensures that your team’s vulnerability and threat prioritization efforts translate directly into swift, decisive action.
Cybersecurity is a team sport, not a siloed function. An effective CTEM program requires breaking down the walls between security, IT operations, development, and even business leaders. When these teams work together, everyone has a shared understanding of the risks and their potential impact on the business. Fostering this collaboration involves creating channels for regular communication and using a centralized platform where everyone can see the same data. When your security team can clearly articulate why a specific vulnerability is a priority and your IT team understands the context, remediation becomes a shared goal rather than a point of friction.
The right technology underpins every stage of the CTEM lifecycle. A powerful platform should do more than just scan for vulnerabilities; it should provide the context and validation needed to make smart decisions. Look for a solution that offers an end-to-end framework, covering everything from discovery and prioritization to validation and mobilization. The Hive Pro Uni5 Xposure platform, for example, implements the entire Gartner-defined CTEM framework in a single place. This consolidation eliminates tool sprawl and provides a unified view of your cyber risks, helping your team focus on the threats that truly matter and take confident, proactive action.
Choosing the right Continuous Threat Exposure Management (CTEM) platform is a big decision. It’s not just about adding another tool to your stack; it’s about fundamentally changing how you approach security. The goal is to move from a reactive, checklist-driven process to a proactive, risk-focused strategy. But with so many options out there, it can be tough to know what really matters. A great CTEM platform should feel like a true partner, giving you the clarity and confidence to act decisively.
Instead of just generating more alerts, the right platform should provide a unified view of your entire attack surface, from your cloud environments to your on-premise assets. It needs to do more than just find vulnerabilities—it must help you understand which ones pose a genuine threat to your business. Look for a solution that cuts through the noise and helps you focus your team’s efforts where they will have the most impact. The best platforms integrate smoothly with the tools you already use, making your entire security ecosystem stronger and more cohesive. Think of it as the central nervous system for your security operations, connecting data points and turning them into actionable intelligence.
In security, timing is everything. A vulnerability discovered weeks ago is old news to an attacker who found it yesterday. That’s why your CTEM platform must provide real-time data. Static, point-in-time scans just don’t cut it anymore. You need a continuous, live feed of your exposure across your entire attack surface. This means the platform should constantly monitor your assets, assessing and flagging new vulnerabilities as they appear. This continuous approach allows you to respond to emerging threats immediately, closing security gaps before they can be exploited. It’s the difference between reading last month’s newspaper and watching a live news broadcast—one keeps you informed, while the other helps you react to events as they unfold.
Not all vulnerabilities are created equal. A critical flaw on a non-essential test server is far less concerning than a medium-risk vulnerability on your primary payment processing system. This is where business context becomes your most powerful tool. A strong CTEM platform doesn’t just use a generic CVSS score; it helps you prioritize threats based on their potential impact on your specific business operations. By understanding which assets are most critical, you can focus your remediation efforts on the vulnerabilities that pose the greatest risk. This approach ensures your team is always working on the most important tasks, allocating your limited time and resources for maximum effect.
If your team spends its days manually sifting through thousands of vulnerabilities, you’re fighting a losing battle. The sheer volume of threats makes manual analysis impossible. This is where automated and intelligent risk scoring comes in. A top-tier CTEM platform uses automation to do the heavy lifting, analyzing threat intelligence and asset criticality to pinpoint the small fraction of vulnerabilities that are most likely to be exploited. For instance, Hive Pro’s Uni5 Xposure Platform can quickly identify the top 1% of risks you’re most likely to be attacked on. This frees up your security professionals to focus on strategic remediation and threat hunting instead of getting lost in spreadsheets.
Your security program is an ecosystem of different tools, each with a specific job. A CTEM platform shouldn’t operate in a silo; it should be the thread that ties everything together. Look for a platform that offers seamless integration with your existing security stack, including vulnerability scanners, SIEMs, and ticketing systems. The ability to pull in data from various sources and push out remediation tasks creates a more efficient and cohesive workflow. A truly unified platform can enhance or even replace some of your existing tools, breaking down data silos and giving you a single, comprehensive view of your security posture without forcing you to rip and replace your entire infrastructure.
You can’t improve what you don’t measure. For your Cyber Threat Exposure Management (CTEM) program to be effective, you need a clear way to track its performance and demonstrate its value. Moving from a reactive stance to a proactive one requires knowing if your efforts are actually reducing risk or just creating more noise. Solid metrics help you justify your security investments, guide your strategy, and show tangible progress to leadership. Instead of just reporting on the number of vulnerabilities patched, you can start telling a story about how you’re making the organization safer.
A successful CTEM program isn’t a one-and-done project; it’s a continuous cycle of improvement. The right metrics act as your guide, highlighting what’s working and where you need to focus your attention. By tracking key performance indicators (KPIs), you can ensure your team is spending its time on the exposures that pose a genuine threat to your business. This data-driven approach helps you move beyond guesswork and make confident, informed decisions about your security posture. The goal is to build a resilient security program that adapts to the ever-changing threat landscape, and measurement is the only way to know if you’re succeeding.
You can’t protect what you don’t know you have. That’s why one of the most fundamental metrics for any CTEM program is asset visibility and coverage. This metric answers a simple question: How much of our potential attack surface are we actually seeing? A successful program continuously works to close the gap between known and unknown assets. You should track the percentage of your digital footprint—including cloud instances, applications, and on-premise devices—that is under continuous monitoring. As your Total Attack Surface Management matures, you should see this coverage percentage steadily increase, proving you have a more complete and accurate picture of your organization’s exposure.
Speed matters in cybersecurity. The longer an exposure exists, the more time an attacker has to find and exploit it. That’s why tracking the time it takes to detect and remediate vulnerabilities is so critical. This is often broken down into two parts: Mean Time to Detect (MTTD) and Mean Time to Remediate (MTTR). Your goal should be to consistently lower these numbers, especially for your most critical assets. An effective CTEM program helps you do this by providing clear vulnerability and threat prioritization, so your team can immediately focus on fixing the issues that pose the greatest risk, rather than getting lost in a sea of low-priority alerts.
Simply counting the number of patched vulnerabilities doesn’t tell the whole story. A more meaningful metric is your organization’s overall risk reduction rate. This involves assigning a risk score to your exposures based on factors like exploitability, asset criticality, and potential business impact. From there, you can track how your total risk score changes over time. A downward trend is a powerful indicator that your CTEM program is working. This metric helps shift the conversation with leadership from technical details to business outcomes, clearly demonstrating how your security efforts are reducing the company’s overall risk profile and protecting its bottom line.
Having security controls in place is one thing; knowing they actually work is another. This is where you need to measure the effectiveness of your defenses. By using techniques like Breach and Attack Simulation (BAS), you can safely test your controls against the same tactics used by real-world attackers. The key metric here is the success rate of your security stack—firewalls, EDR, SIEM—in preventing or detecting these simulated attacks. This process of Adversarial Exposure Validation provides concrete proof of your security posture, helping you identify and close gaps before they can be exploited in a real incident.
Is CTEM just another name for vulnerability management? Not at all. While they’re related, think of traditional vulnerability management as creating a long to-do list of every potential crack in your walls. CTEM, on the other hand, is like having a security expert who shows you which of those cracks an intruder is most likely to use to break in, based on their tools and motives. It shifts the focus from a simple list of flaws to a strategic understanding of your actual risk, incorporating your entire attack surface and real-world threat intelligence.
My team is already swamped with alerts. How does CTEM help with that? This is exactly the problem CTEM is designed to solve. Instead of adding to the noise, a CTEM program cuts through it by using threat intelligence and business context to prioritize what truly matters. It helps you zero in on the small percentage of exposures that are actively being exploited or that target your most critical assets. This means your team stops chasing thousands of low-risk alerts and can focus its energy on fixing the handful of issues that could actually lead to a breach.
What’s the difference between an “exposure” and a “vulnerability”? A vulnerability is typically a specific software flaw with a CVE number, like a bug in a piece of code. An exposure is a much broader term that includes any weakness an attacker could use. This could be a vulnerability, but it could also be a misconfigured cloud service, an exposed database, weak credentials, or a forgotten server that’s still connected to the internet. CTEM looks at this bigger picture to understand all the potential ways an attacker could get in.
How is the ‘validation’ stage different from a regular penetration test? A penetration test is usually a point-in-time, manual engagement that happens maybe once or twice a year. The validation stage in CTEM, often using Breach and Attack Simulation (BAS), is an automated and continuous process. It’s like having a virtual red team constantly testing your defenses against the latest attack techniques. This gives you a real-time, ongoing assessment of whether your security controls are working as expected, rather than a snapshot that quickly becomes outdated.
Do I need to rip and replace all my existing security tools to adopt CTEM? No, and a good CTEM platform shouldn’t force you to. The idea is to unify your security data, not start from scratch. A strong CTEM platform integrates with the tools you already have, like your vulnerability scanners and asset inventories. It pulls that data into a single place, enriches it with threat intelligence and business context, and gives you a unified view of your risk. This makes your existing tools more valuable by putting their findings into a clear, actionable context.