Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
A vulnerability without context is just a data point. A medium-severity flaw might seem like a low priority, but what if you knew it was being actively used in a new ransomware campaign targeting your industry? This is why threat intelligence is so crucial. The answer to how does BAS improve vulnerability management is found in its ability to weaponize this intelligence for your defense. A Breach and Attack Simulation (BAS) platform takes the latest threat advisories and simulates those exact attacks against your environment. This gives you undeniable proof of which trending threats your organization is vulnerable to, making your prioritization decisions faster, smarter, and more effective.
Think of your security defenses as a fortress. You have walls, guards, and alarms, but how do you know if they’ll actually stop a clever intruder? That’s where Breach and Attack Simulation (BAS) comes in. BAS platforms are tools that let you safely and automatically simulate complex cyberattacks against your own environment. Instead of just looking for known vulnerabilities, BAS acts like a real attacker to test if your security controls are working as expected.
The goal isn’t to break things, but to find the weak spots before a real adversary does. These automated simulations run continuously, giving you a constant, real-world check on your security posture. It’s like having a dedicated red team on staff 24/7, constantly probing your defenses, testing your response plans, and providing clear data on where you need to improve. This proactive approach moves you from a reactive state of patching vulnerabilities to actively validating that your defenses can withstand the latest attack techniques. With BAS, you can answer the critical question: “Are we secure right now?”
At its heart, a BAS platform works by replicating the methods real attackers use. It doesn’t just scan for a missing patch; it mimics the entire attack sequence, from initial access and lateral movement to data exfiltration. These simulations are based on well-known frameworks of attacker tactics and techniques, ensuring the tests are grounded in real-world threat behaviors. This allows you to run specific scenarios to see exactly how your security tools and your team respond. The platform then provides detailed reports on what worked, what didn’t, and what you need to fix.
It’s easy to confuse BAS with vulnerability scanning, but they serve very different purposes. A traditional vulnerability scan is like checking the doors and windows of your house to see if any are unlocked. It identifies potential weaknesses but doesn’t try to exploit them. BAS, on the other hand, not only finds the unlocked window but also simulates an intruder climbing through it and moving through the house to see if your alarm system goes off. It’s an active test of your entire security ecosystem, validating that your controls can actually stop an attack in progress.
A traditional vulnerability scan is great at giving you a long list of potential weaknesses. But that list doesn’t tell the whole story. It can’t answer the most important question: “Could an attacker actually use this vulnerability against us?” This is where Breach and Attack Simulation (BAS) changes the game. Instead of just pointing out theoretical flaws, BAS platforms actively test your defenses to see if those vulnerabilities are truly exploitable in your specific environment. This approach transforms your vulnerability management program from a reactive, list-checking exercise into a proactive, evidence-based strategy. It provides concrete proof of which vulnerabilities pose a real threat, allowing your team to cut through the noise of thousands of alerts and focus on what’s urgent. By safely simulating real-world attack techniques, you can validate your security controls, identify the most likely attack paths, and direct your remediation efforts to the gaps that matter most. It’s the difference between knowing you have an unlocked door and knowing someone can actually walk through it to reach your most critical assets.
BAS platforms work by copying the exact methods real attackers use. Instead of just checking for a CVE, they run automated attack scenarios based on the latest threat intelligence and frameworks like MITRE ATT&CK. These simulations mimic the behavior of ransomware groups, nation-state actors, and other adversaries, testing how your security stack responds to specific, real-world threats. This automated approach allows you to continuously validate your security controls without needing a dedicated red team for every test. You can schedule simulations to run regularly, giving you a constant pulse on your security posture and ensuring your defenses are prepared for the latest attack techniques.
Attackers don’t limit themselves to a single entry point, and neither should your testing. A key strength of BAS is its ability to simulate attacks across your entire digital footprint—from phishing emails and malicious web downloads to compromised endpoints and misconfigured cloud services. By testing multiple vectors, BAS helps you understand how an attacker could chain together seemingly low-risk vulnerabilities to create a high-impact breach. It reveals the complex attack paths that a simple vulnerability scan would miss, giving you a complete picture of how an adversary could navigate your full attack surface to reach your critical data and systems.
This is where BAS delivers its greatest value. A vulnerability scanner might flag a critical CVE, but a BAS platform will try to safely exploit it to confirm if it’s a genuine threat in your environment. Your existing security controls, like a firewall or an IPS, might already block the attack path, making the vulnerability a much lower priority. This real-world validation provides the context you need to prioritize your remediation efforts effectively. By focusing on proven, exploitable vulnerabilities, you can direct your team’s limited time and resources to fixing the problems that pose an immediate danger to the business, rather than chasing down every single finding.
Finding vulnerabilities is one thing; figuring out which ones to fix first is another challenge entirely. When your team is staring at a list of thousands of potential weaknesses, it’s easy to feel overwhelmed. This is where Breach and Attack Simulation (BAS) becomes a game-changer for vulnerability management. Instead of just adding to the noise, BAS helps you cut through it by showing you which vulnerabilities pose a genuine, immediate threat to your organization. It moves you from a theoretical “what if” to a practical “what is” by testing for real-world exploitability.
Your team is likely familiar with standard scoring systems like CVSS. While it’s a useful baseline, a CVSS score is generic and doesn’t tell the full story of a vulnerability’s risk to your specific business. A critical vulnerability on a system that’s completely isolated from the internet poses a much lower risk than a medium one on your main web server. BAS provides this missing context. By simulating attacks, it validates whether a security flaw can actually be used in your live environment, considering your network access, security controls, and system configurations. This allows you to prioritize threats based on tangible business risk, not just a theoretical number.
Beyond your internal context, you also need to know what’s happening in the outside world. What are attackers actually doing right now? Modern BAS platforms integrate up-to-the-minute threat intelligence to inform their attack simulations. This means you’re not just testing against random vulnerabilities; you’re testing against the specific tactics, techniques, and procedures (TTPs) that threat actors are currently using in the wild. This intelligence, often curated by expert teams like HiveForce Labs, helps you understand which of your systems are most at risk and what kinds of attacks are most likely to target your industry. It helps you focus your efforts on the threats that matter most.
Let’s be direct: most successful cyberattacks exploit known vulnerabilities that organizations simply haven’t patched yet. With hundreds of new weaknesses discovered daily, it’s impossible to fix everything at once. BAS helps you zero in on the vulnerabilities that are not only present in your environment but are also being actively exploited by attackers. By running simulations based on the latest threat advisories, you can confirm if your systems are susceptible to ongoing campaigns. This allows your team to direct its limited time and resources to closing the exact security gaps that attackers are trying to breach right now, turning your defense from reactive to truly proactive.
Vulnerability scanners give you a long list of potential weaknesses, but they often lack crucial context, leaving you to guess which issues to tackle first. This is where threat intelligence comes in. Think of it as your direct line to what’s happening on the front lines of cyber warfare. It provides the real-world data you need to understand which threats are theoretical and which ones are actively being used to breach networks right now. This intelligence transforms your vulnerability data from a simple list into a strategic roadmap for remediation.
Threat intelligence is like getting real-time news about cyber threats; it tells you about new weaknesses, how attackers work, and which ones they’re actively trying to use. Instead of just seeing a CVE score, you get the full story. For example, intelligence from research teams like HiveForce Labs can show that a medium-severity vulnerability is part of a new, widespread ransomware campaign. This context immediately transforms a lower-priority item into an urgent threat. It allows you to see risks through an attacker’s eyes and make smarter, faster decisions about where to focus your team’s limited time and resources.
Let’s be realistic—your team can’t patch everything at once. You have to focus on what matters most. Many successful attacks happen because hackers exploit known weaknesses that companies haven’t fixed yet. Threat intelligence cuts through the noise by highlighting which vulnerabilities are currently being weaponized by threat actors. By integrating up-to-date threat advisories into your workflow, you can see which CVEs are trending on the dark web or being packaged into popular exploit kits. This helps your team move beyond relying solely on CVSS scores and prioritize the vulnerabilities that pose a clear and present danger to your organization, effectively closing the window for attackers.
When you know how attackers operate, you can build stronger defenses that are ready for actual threats, not just theoretical ones. Adding threat intelligence to your vulnerability management helps you find and fix problems faster, often before an attack campaign even gains momentum. This proactive approach means your remediation efforts are always aligned with the current threat landscape. Instead of just working through a backlog based on generic severity ratings, your team can confidently address the most critical exposures first. This strategic focus strengthens your security posture and ensures your resources are used for maximum impact, which is the core of effective vulnerability and threat prioritization.
Finding vulnerabilities is one thing, but knowing if your security controls can actually stop an attack is another. This is where Breach and Attack Simulation (BAS) becomes a game-changer. It moves you from a passive, theoretical stance to an active, evidence-based approach. By safely simulating real-world attack techniques, you can pressure-test your defenses and see exactly how your security stack holds up against a determined adversary. This validation gives you the confidence that your security investments are working as intended.
You’ve invested in firewalls, EDR, and SIEMs, but are they configured to detect real threats? BAS answers this by running controlled attack scenarios. These simulations copy the methods that real attackers use, from initial access to data exfiltration, to see if your tools raise the alarm. It’s a practical way to validate that your security ecosystem is working as expected. This process of adversarial exposure validation helps you find misconfigurations and blind spots in your detection capabilities, ensuring your technology investments are delivering the protection you need.
An incident response plan that only exists on paper is just a theory. BAS acts as a continuous fire drill for your security team. When a simulated attack triggers an alert, you get to see your incident response playbook in action. Does your team follow the correct procedures? Are communication channels clear? These simulations help find any missing skills or process bottlenecks before a real crisis hits. By regularly testing your people and processes against realistic threats, you can refine your playbooks and build the muscle memory your team needs to respond effectively when it matters most.
Your attack surface is vast, and the list of vulnerabilities can feel endless. BAS helps you cut through the noise by showing you which vulnerabilities are actually exploitable in your environment. By continuously simulating attacks, you can identify the paths an attacker could take to compromise your systems. This allows you to focus your limited time and resources on the security gaps that pose a genuine, immediate threat. It’s a smarter way to manage risk, helping you proactively close dangerous entry points before an attacker finds them and align your efforts with a clear vulnerability and threat prioritization strategy.
Beyond just testing your technology, a Breach and Attack Simulation (BAS) platform is one of the best tools for preparing your people. It provides a safe and controlled environment for your security team to practice their skills against realistic threats, turning theoretical knowledge into practical experience. Think of it as a sparring partner that helps your team build the muscle memory needed to defend against a real attack. By continuously running these drills, you can identify and close skill gaps, refine your processes, and ensure everyone knows exactly what to do when a real incident occurs. This proactive training is what transforms a good security team into a great one.
The best way to prepare for a real attack is to practice against one. BAS platforms allow you to do just that by running simulations that mimic the exact tactics, techniques, and procedures (TTPs) used by today’s threat actors. These aren’t just theoretical exercises; they are hands-on drills that test your team’s ability to detect and respond to threats in real time. By running these realistic attack scenarios, your team can practice their response actions, validate their playbooks, and identify areas for improvement without any actual risk. This continuous practice sharpens their defensive skills and builds the confidence they need to act decisively during a high-pressure security event.
You can’t find what you don’t know to look for. BAS is incredibly effective at honing your team’s threat-hunting skills by showing them what an active attack looks like within your specific environment. As simulations run, your team can practice identifying subtle indicators of compromise, tracing the steps of a simulated attacker, and understanding how threats move laterally across your network. This process helps pinpoint skill gaps before a real breach forces the issue. It gives analysts the hands-on experience they need to become more effective hunters, enabling them to proactively search for and neutralize threats before they can cause significant damage.
An incident response plan is only as good as its execution. BAS allows you to pressure-test your plans to make sure they hold up. By simulating attacks that exploit known vulnerabilities, you can evaluate the effectiveness of your incident response processes from start to finish. Can your team detect the initial breach? Are they able to contain the threat quickly? Do they know the right steps for remediation and recovery? Answering these questions during a simulation is far better than trying to figure them out during a live incident. Regular testing helps refine your playbooks, clarify roles and responsibilities, and ensure your team can respond to an actual attack with speed and precision.
Adopting a Breach and Attack Simulation platform is a game-changer for any security program. It shifts your posture from reactive to proactive and gives you a true, attacker’s-eye view of your defenses. But let’s be honest—integrating any new technology comes with its own set of hurdles. Thinking through these potential challenges ahead of time is the best way to ensure a smooth rollout and get the most value from your investment.
The main obstacles usually fall into three categories: technology, information, and people. First, you have to figure out how the BAS platform will fit into your existing security ecosystem. It can’t operate in a silo. Second, you need a strategy to handle the new stream of data it produces without overwhelming your team with yet another source of alerts. Finally, you need to consider your team’s current workload and skillset. A powerful tool is only useful if your team has the capacity and knowledge to wield it effectively. By anticipating these issues, you can choose a platform like Uni5 Xposure that is designed to solve them, turning potential roadblocks into stepping stones for a stronger security posture.
A BAS platform doesn’t replace your existing security stack; it validates it. That means it needs to play nicely with everything you already have, from your SIEM and SOAR to your vulnerability scanners and ticketing systems. The challenge is that many organizations are already struggling with outdated tools and incomplete asset visibility. The last thing you want is another disconnected dashboard that adds complexity instead of clarity. A successful implementation depends on creating a unified workflow where BAS findings automatically inform your other systems. Look for a platform with a robust API and pre-built integrations to ensure you can easily connect the dots and automate the flow of information across your entire security program, giving you a complete view of your total attack surface.
Your security team is already dealing with a mountain of alerts. The sheer volume of vulnerabilities makes it impossible to patch everything, and many teams lack clear visibility into the full remediation lifecycle. A poorly implemented BAS tool can make this problem worse by simply adding more noise. The goal isn’t to generate more data; it’s to generate better, more actionable insights. A strong BAS platform should cut through the noise by correlating simulation results with real-world threat intelligence. This helps you move beyond a simple high/medium/low rating and focus on the vulnerabilities that pose a genuine, immediate threat to your organization. This kind of intelligent vulnerability and threat prioritization turns overwhelming data into a clear, manageable to-do list.
Let’s face it: security teams are stretched thin. With budget constraints and a persistent cybersecurity skills shortage, most teams don’t have the bandwidth to become experts in yet another complex tool. A major challenge is finding the time and internal expertise to not only run attack simulations but also to interpret the results and coordinate remediation. This is where automation and usability become critical. The right BAS platform should feel like adding a new expert to your team, not another burden. By leveraging the built-in expertise from a dedicated research team like HiveForce Labs, you can augment your team’s capabilities, automate routine testing, and get clear, actionable guidance that empowers your existing staff to make a real impact without extensive training.
Let’s be honest: your security team is already stretched thin. The last thing they need is more manual, repetitive work. This is where the automation and continuous testing capabilities of a Breach and Attack Simulation (BAS) platform really shine. By automating attack simulations and running them continuously, you can move away from periodic, point-in-time assessments and embrace a more proactive security posture. This approach not only saves time but also provides a much clearer, more consistent picture of your defenses, helping you understand what an attacker could actually accomplish in your environment.
Keeping track of vulnerability identification, prioritization, and remediation manually is a huge challenge. It’s a recipe for burnout and, worse, human error. When your team is buried in spreadsheets and manual checks, it’s easy for a critical vulnerability to slip through the cracks. BAS platforms take this burden off your team by automating the entire testing process. Instead of spending weeks setting up and running manual tests, you can launch sophisticated attack simulations with a few clicks. This frees up your analysts to focus on what they do best: analyzing results, hunting for threats, and strengthening your defenses with a clear threat exposure management strategy.
How do you know if your security controls are working right now? Not last quarter, but today. Traditional methods like penetration testing give you a snapshot in time, but the results can vary based on the tester’s skill and scope. BAS provides consistent, repeatable security validation across your entire attack surface. These tools help you run specific tests to see how well your security team and tools respond to different attack scenarios. By running the same simulations regularly, you can benchmark your performance, track improvements over time, and ensure your defenses are configured correctly. This provides a reliable way to perform adversarial exposure validation at scale, without the inconsistencies of manual testing.
The threat landscape doesn’t wait for your annual pen test. New vulnerabilities and attack techniques emerge daily. To keep up, you need a way to test your defenses continuously. BAS makes this possible by integrating security testing directly into your operations. Continuous scanning and simulation enable you to identify and address security gaps as they appear, not months after the fact. This real-time insight allows you to allocate resources more effectively, reducing overall risk. By focusing on what’s actually exploitable in your environment right now, you can transform your vulnerability and threat prioritization from a guessing game into a data-driven strategy, ensuring you’re always fixing what matters most.
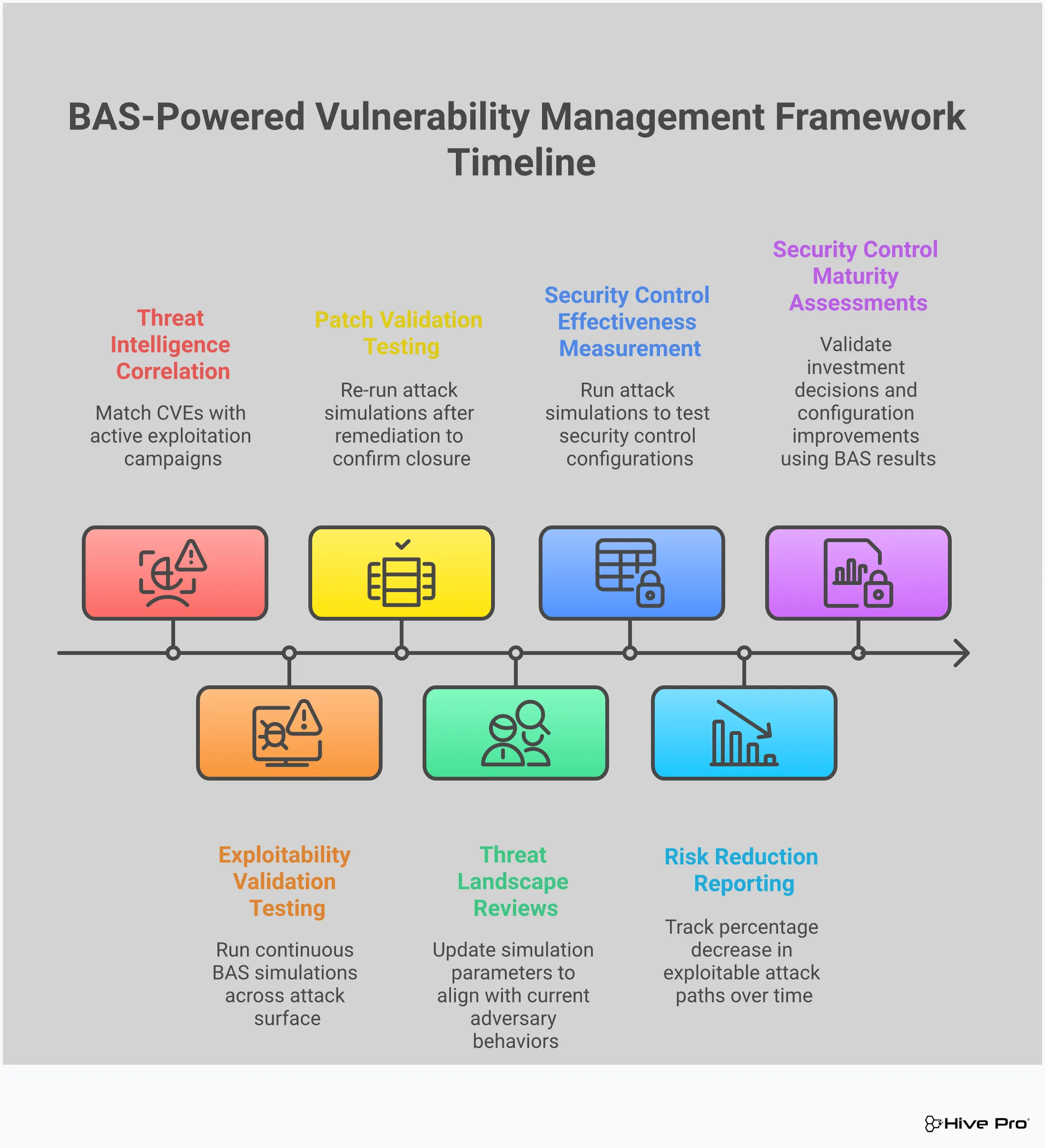
Running attack simulations is just the first step. To truly get value from your Breach and Attack Simulation (BAS) program, you need to measure its impact. Tracking the right metrics shows how BAS is strengthening your defenses, helps you justify the investment, and guides your strategy over time. It’s about shifting from simply finding issues to demonstrating tangible risk reduction and proving that your security posture is getting stronger every day. By focusing on clear outcomes, you can turn your BAS program into a powerful engine for continuous security improvement.
To measure success, you first have to define what it looks like. Move beyond vanity metrics like the number of simulations run and focus on key performance indicators (KPIs) that reflect real security outcomes. A great place to start is by tracking Mean Time to Remediate (MTTR) for critical vulnerabilities identified by BAS. Other powerful metrics include the percentage reduction in exploitable attack paths and improved security control effectiveness scores. Implementing a platform that offers full asset visibility and defined accountability helps you track these KPIs and show exactly how your team’s efforts are paying off.
Your BAS platform generates a lot of data, but the real story is in the trends. Many organizations struggle to get a clear view of their vulnerability management lifecycle, making it difficult to see progress. By providing consistent data on your security gaps, BAS helps solve this. Tracking this data over time lets you analyze trends like a decrease in the number of critical vulnerabilities or a faster patch deployment rate for issues BAS identifies as exploitable. This trend analysis provides concrete proof that you are actively reducing risk and helps you prioritize threats more effectively.
Ultimately, the goal of a BAS program is to improve your overall security posture for the long haul. This means moving from periodic, reactive scanning to a state of continuous validation. Your metrics should tell this story. Report on how BAS has helped you close previously unknown security gaps, validate the effectiveness of new security controls, and reduce your overall attack surface over months and quarters. By showing this sustained improvement, you demonstrate that your BAS program is a core part of a mature, proactive threat exposure management strategy, not just a point-in-time assessment tool.
How is Breach and Attack Simulation (BAS) different from a traditional vulnerability scan? Think of it this way: a vulnerability scanner checks if your doors and windows are unlocked, giving you a list of potential entry points. A BAS platform actually tries to gently open the unlocked window, sneak inside, and see how far it can get before your alarm system goes off. It moves beyond a simple list of theoretical weaknesses to actively test if those weaknesses can be exploited and if your security controls can actually stop an attack in progress.
My security team is already swamped with alerts. Won’t a BAS platform just create more noise? That’s a fair concern, but a good BAS platform does the opposite—it helps you cut through the noise. Instead of just adding more findings to your list, it provides crucial context by showing you which vulnerabilities are actually exploitable in your specific environment. By correlating its findings with real-world threat intelligence, it helps you focus on the handful of issues that pose an immediate danger, turning a mountain of alerts into a clear, prioritized action plan.
Do I need a dedicated red team to use a BAS platform effectively? Not at all. One of the biggest advantages of modern BAS platforms is that they automate the work that would typically require a specialized red team. These tools are designed to be used by your existing security and vulnerability management teams. They provide pre-built attack scenarios based on the latest threat intelligence, allowing you to run sophisticated tests continuously without needing deep expertise in offensive security.
How does threat intelligence fit into all of this? Threat intelligence is the fuel that makes a BAS platform so effective. Without it, you’re just testing against random attack methods. With it, you’re simulating the exact tactics and techniques that threat actors are using in the wild right now. This intelligence ensures your simulations are relevant and helps you prioritize remediation based on which of your vulnerabilities are being actively targeted by real-world adversaries.
Is BAS just for finding technical flaws, or does it help our team’s performance too? It absolutely helps your team. BAS is one of the best training tools you can have because it provides a safe environment for your security team to practice their response skills. When a simulation triggers an alert, your team gets a real-world opportunity to run through their incident response playbooks, identify communication gaps, and sharpen their threat-hunting abilities—all without the pressure of a live breach.