Comprehensive Threat Exposure Management Platform
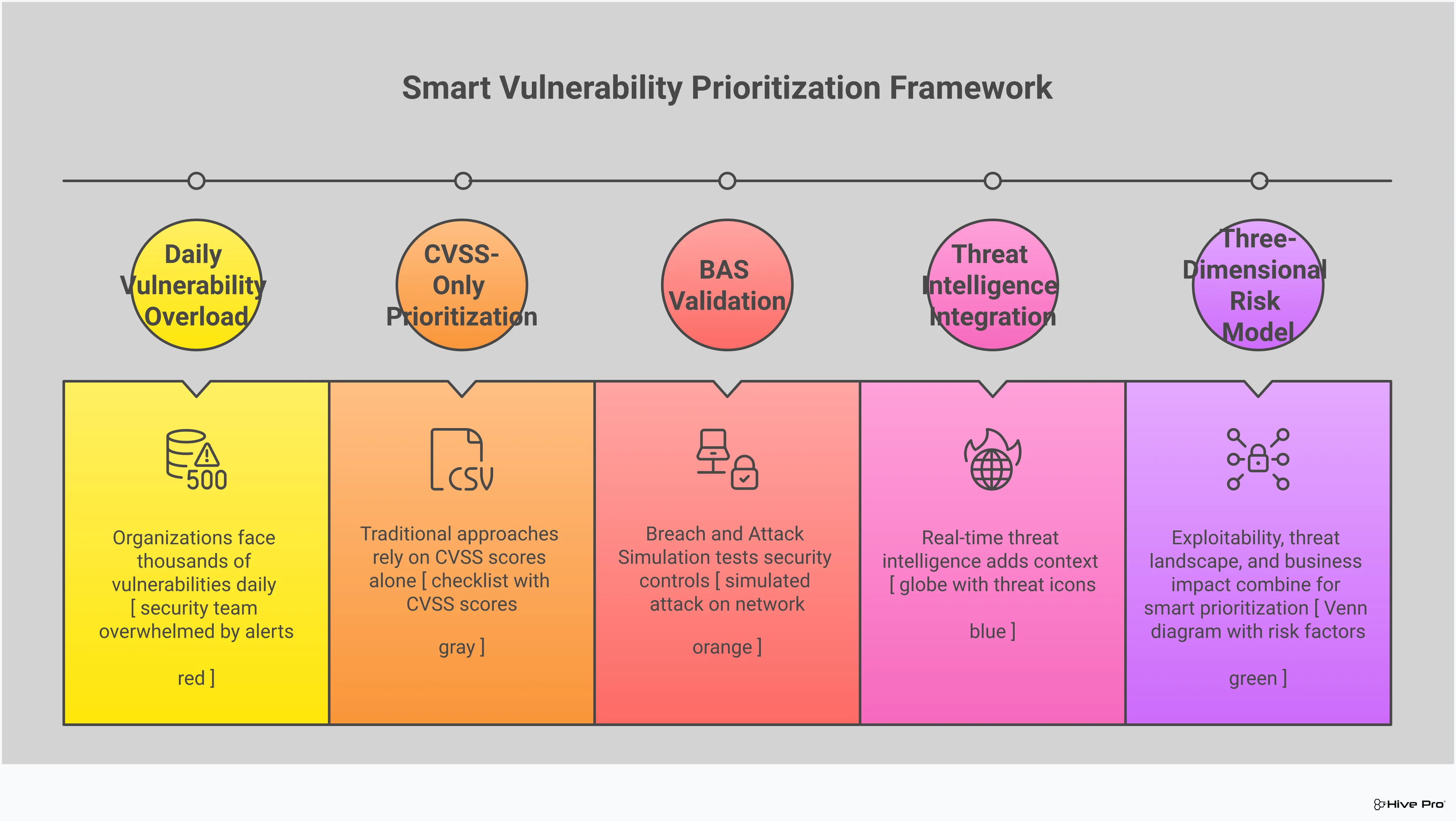
Your vulnerability scanner just produced a report with hundreds of “critical” CVEs. Now what? For most security teams, this is where the guessing game begins. You know you can’t fix everything at once, so you’re forced to make tough calls based on CVSS scores and gut feelings, all while hoping you picked the right ones to patch first. The real challenge isn’t finding vulnerabilities; it’s knowing which ones an attacker can actually use against you. This is where Breach and Attack Simulation (BAS) changes the game. It moves you beyond theoretical risk scores to provide hard evidence of exploitability. This is exactly how BAS helps threat exposure management: by showing you which weaknesses create real, viable attack paths in your environment, allowing you to focus your resources on the gaps that truly matter.
Think of Breach and Attack Simulation (BAS) as an automated sparring partner for your security defenses. It’s a cybersecurity technology that automatically and continuously tests your security posture by emulating real-world attack techniques and tactics. Instead of waiting for an actual breach to find out where your weaknesses are, BAS proactively launches simulated attacks against your environment to see what breaks, what holds up, and where your security controls might fail.
This isn’t just about finding vulnerabilities; it’s about understanding their real-world impact. A BAS platform automatically emulates the full attack lifecycle—from initial compromise to lateral movement and data exfiltration—to give you a clear picture of how a real attacker could get in and what they could do once inside. This approach provides concrete, evidence-based insights into your security gaps, allowing you to move from a reactive stance to a proactive one. It’s a fundamental component of a modern adversarial exposure validation strategy, helping you answer the critical question: “Are our security tools actually working as expected?”
At its heart, a BAS tool acts like an automated hacker. It uses a library of pre-built “playbooks” that replicate known attack patterns, from common ransomware campaigns to sophisticated techniques used by specific advanced persistent threat (APT) groups. These playbooks are essentially scripts that simulate the steps an attacker would take: finding information, gaining initial access, moving through the network, escalating privileges, and attempting to steal data. This entire process is automated and runs safely within your environment, so you get the benefit of realistic attack testing without the risk of actual damage. The technology continuously challenges your security controls—like firewalls, EDR, and email gateways—to see if they can detect and block the simulated threats.
You might be thinking this sounds a lot like penetration testing or red teaming, and you’re on the right track. However, there are key differences. Traditional security tests are typically manual, expensive, and performed infrequently—maybe once or twice a year. They provide a valuable snapshot of your security at a single point in time. BAS, on the other hand, offers a more adaptive and continuous way to manage security. Because it’s automated, you can run simulations constantly, giving you an up-to-the-minute view of your security posture. While a pen test might identify a vulnerability, BAS goes a step further by attempting to exploit it, confirming whether it poses a genuine threat. This helps you focus your vulnerability and threat prioritization efforts on the issues that matter most.
Think of your security controls as a series of locked doors designed to keep attackers out. A vulnerability scan might tell you if a lock is old, but it won’t tell you if someone can pick it, find an open window next to it, or talk an employee into handing over the key. Breach and Attack Simulation (BAS) is like hiring a team to safely and continuously test every possible way in. It moves beyond theoretical weaknesses to show you which ones are genuine, exploitable entry points. By running controlled, real-world attack scenarios across your environment, BAS gives you a clear and constant picture of where your defenses hold strong and where they might crumble under pressure.
At its core, BAS technology automatically emulates the tactics and techniques used by actual attackers. Instead of just scanning for known CVEs, it launches safe, simulated attacks based on threat intelligence to see how your security stack responds. This process of adversarial exposure validation tests your defenses against everything from phishing attempts to lateral movement and data exfiltration. It’s a hands-on approach that answers the critical question, “Could an attacker actually do this in our environment?” By automating these simulations, you get consistent, repeatable tests that check your security posture against the latest threats without requiring a manual red team engagement for every scenario.
Traditional security assessments, like annual penetration tests, give you a snapshot in time. Your environment changes daily, and so do attacker methods. BAS platforms run tests continuously, giving you an almost real-time view of your security effectiveness. This constant validation helps you spot gaps that vulnerability scanners often miss, such as policy misconfigurations, firewall rule gaps, or flawed access controls. Because the simulations are always running, you can immediately see the impact of a new security tool, a configuration change, or a recently applied patch, ensuring your defenses are working as expected day in and day out.
A single vulnerability is one thing, but a chain of them is how major breaches happen. BAS excels at connecting the dots to map out potential attack paths through your network. Using attack “playbooks” that mirror how real adversaries operate, the platform simulates the entire attack lifecycle—from initial access and privilege escalation to lateral movement and achieving the final objective. This acts like a “virtual purple team,” running attacks and instantly reporting on how your defenses performed at each step. It shows you exactly how an attacker could navigate your environment, helping you prioritize the vulnerabilities that open up the most critical pathways.
Traditional security assessments, like annual penetration tests, give you a valuable snapshot of your defenses. The problem is, that snapshot starts aging the moment the report is delivered. Your network changes, new assets come online, and attackers are always developing new methods. A point-in-time assessment simply can’t keep up with the pace of change, leaving you with a security posture that’s based on outdated information. You might feel secure based on a report from six months ago, but a new vulnerability or a misconfigured firewall rule could have opened a critical gap yesterday.
This is where continuous validation with Breach and Attack Simulation (BAS) makes a huge difference. Instead of relying on periodic check-ups, BAS provides a constant stream of feedback on how your security controls are performing against real-world threats. By running simulated attacks automatically and regularly, you get an up-to-date and accurate picture of your security posture. This approach helps your team move from a reactive stance, fixing issues found months ago, to proactively managing your security every single day. It closes the gap between when a weakness appears and when you discover it, giving you the agility to adapt as quickly as your adversaries.
Relying on annual or quarterly security tests is like checking the locks on your doors once a year and assuming they’ll stay secure. In reality, your environment is dynamic. New software is deployed, configurations are updated, and human error can accidentally create new openings for attackers. A one-time check can’t account for these daily shifts.
BAS platforms run continuously, providing constant checks on your security controls. This gives you immediate insight into whether a recent change has introduced a new risk or if a security tool has stopped working as expected. It transforms security validation from a periodic project into an ongoing, automated process that reflects the true state of your defenses.
Attackers don’t wait for your annual review cycle. New tactics, techniques, and procedures (TTPs) emerge constantly. Your security stack might be state-of-the-art, but is it configured to stop the threats that are active right now? BAS helps you answer that question with confidence.
BAS solutions are powered by up-to-date threat intelligence, allowing you to test your defenses against the latest attack patterns. This process of adversarial exposure validation ensures your security tools are not just present, but effective. By continuously simulating real-world threats curated by research teams like HiveForce Labs, you can confirm your security investments are delivering real value and are prepared for what attackers are actually doing in the wild.
Vulnerability management can often feel like a numbers game—a constant flood of CVEs, patches, and alerts. But not all vulnerabilities are created equal. The real challenge isn’t just finding them; it’s figuring out which ones pose a genuine threat to your organization. This is where Breach and Attack Simulation (BAS) becomes a powerful ally. By safely simulating real-world attack techniques, BAS moves your strategy from a theoretical checklist to a practical, evidence-based approach. It helps you see your environment through an attacker’s eyes, providing the context needed to focus your team’s time and resources on the risks that truly matter. Instead of chasing every potential weakness, you can concentrate on shoring up the defenses that are actively being tested by adversaries.
Your vulnerability scanner might generate a list of hundreds of “critical” issues, but how many of them can an attacker actually use to breach your defenses? BAS answers this question by attempting to exploit these vulnerabilities in a controlled, safe manner. This process helps you prioritize threats based on exploitability within your unique environment. If a simulated attack fails because a specific pathway is blocked or a compensating control is in place, you know that vulnerability is a lower priority. This allows your team to stop wasting cycles on theoretical risks and focus on the exploitable gaps that present a clear and present danger to your organization.
Deploying a patch is one thing; confirming it actually closed the security gap is another. After your team applies a fix, a BAS platform can run the same attack simulation that previously succeeded. If the attack now fails, you have concrete proof that your remediation efforts were effective. This continuous validation loop is crucial for ensuring your security controls are performing as expected. It provides tangible evidence for compliance audits and gives leadership confidence that the organization’s security posture is genuinely improving. This process of adversarial exposure validation transforms patching from a “fire and forget” activity into a measurable and verifiable security outcome.
Security teams are often overwhelmed by a constant stream of alerts, leading to fatigue and the risk of missing a real incident. Many of these alerts come from vulnerabilities that, while technically present, are not exploitable in your environment. BAS helps cut through this noise by validating which alerts correspond to genuine, exploitable risks. By focusing on proven attack paths, you can filter out the distractions and low-impact findings. This allows your security operations center (SOC) and vulnerability management teams to concentrate their efforts on investigating and remediating the threats that have a demonstrated potential to cause harm, making your entire security program more efficient and effective.
A Breach and Attack Simulation (BAS) platform is only as good as the intelligence that fuels it. Without a deep understanding of the current threat landscape, simulations are just shots in the dark. This is where threat intelligence becomes critical. It provides the context needed to run meaningful simulations that reflect what’s actually happening outside your network walls.
High-fidelity threat intelligence, like the research from HiveForce Labs, transforms a BAS tool from a generic testing utility into a strategic defensive asset. It ensures your simulations are based on the real-world tactics, techniques, and procedures (TTPs) that attackers are using right now. This allows you to test your defenses against relevant, timely, and specific threats, not just theoretical ones. By integrating threat intelligence, BAS helps you anticipate an attacker’s next move and validate your controls before an actual incident occurs. This continuous testing model ensures your defenses are always ready for new and evolving attack methods.
Effective BAS platforms don’t just throw random attacks at your infrastructure; they meticulously replicate the methods of real-world adversaries. By leveraging up-to-date threat intelligence, these simulations can mimic the exact exploit chains and lateral movement techniques used by known threat actor groups. This means you’re not just checking for a vulnerability, but testing whether your security controls can actually stop a multi-stage attack in its tracks. This process of adversarial exposure validation gives you a true measure of your defensive capabilities against the attacks you’re most likely to face. It’s the difference between knowing a window is unlocked and knowing if a burglar can actually climb through it without setting off an alarm.
Your vulnerability scanner probably produces a list of issues so long it feels impossible to tackle. Threat intelligence helps BAS cut through that noise by focusing on what matters most: the vulnerabilities actively being exploited in the wild. Attackers tend to follow the path of least resistance, often reusing the same exploits across multiple campaigns. By simulating attacks based on the latest threat advisories, you can quickly identify and prioritize the exposures that present a clear and present danger to your organization. This allows your team to direct its limited resources toward fixing the gaps that attackers are targeting today, rather than getting lost in a sea of low-risk CVEs.
Different industries face different adversaries. A financial institution might be targeted by sophisticated financially motivated groups, while a healthcare organization might be a target for ransomware gangs. Threat intelligence allows you to tailor your BAS campaigns to simulate the specific threat actors that pose the greatest risk to your business. By understanding their motivations, tools, and common attack vectors, you can test your defenses against a realistic opponent. This alignment ensures your security posture is hardened against your most likely threats, helping you build a more resilient and informed defense strategy as part of your overall threat exposure management program.
Adopting a Breach and Attack Simulation (BAS) platform doesn’t mean you have to rip and replace the security tools you already rely on. In fact, it’s quite the opposite. BAS acts as a force multiplier, making your entire security stack more effective by providing the real-world context and validation it needs to perform at its best. Think of it as a verification layer that sits across your existing investments, ensuring they are configured correctly and working together to stop actual threats.
Instead of operating in a silo, a BAS platform integrates with your key systems to create a feedback loop. It tests your defenses, feeds the results back into your operational tools, and helps you fine-tune your security posture based on hard evidence, not assumptions. This integration is what transforms BAS from a simple testing tool into a central pillar of a proactive security strategy, helping you get more value from the solutions you already have in place.
Your Security Information and Event Management (SIEM) tool is the central nervous system of your security operations, collecting logs and firing off alerts. But how do you know if it will actually detect a sophisticated attack? BAS answers this question by running safe, controlled attack simulations. When a simulation runs, you can check to see if your SIEM generated the expected alert. If it didn’t, you know there’s a detection gap or a misconfiguration you need to fix—before a real attacker exploits it.
This validation extends directly to your Security Orchestration, Automation, and Response (SOAR) platform. A SIEM alert often triggers an automated playbook in your SOAR. BAS allows you to test these automated responses to ensure they’re working correctly. This process of adversarial exposure validation helps you continuously refine your detection and response capabilities, making sure your automated workflows are ready for a real incident.
Your vulnerability scanner gives you a list of potential weaknesses, but it often lacks the context to tell you which ones matter most. Integrating BAS with your vulnerability management platform bridges this gap. While a scanner identifies a CVE, a BAS platform can simulate an attempt to exploit it, confirming whether the vulnerability is a genuine, exploitable risk in your specific environment. This helps you see beyond the CVSS score and focus on what attackers can actually leverage.
This integration is key to effective vulnerability and threat prioritization. BAS can also uncover risks that traditional scanners might miss, like security misconfigurations or dangerous combinations of lower-risk vulnerabilities that create a viable attack path. By providing evidence of exploitability, BAS helps your team cut through the noise of thousands of alerts and concentrate remediation efforts on the exposures that pose a clear and present danger to your organization.
Ultimately, BAS provides the continuous validation needed to support your broader risk management goals and a mature Continuous Threat Exposure Management (CTEM) program. It delivers objective, evidence-based answers to the critical question from your board and leadership: “Are we secure?” Instead of relying on annual penetration tests, you can demonstrate an always-on, validated security posture. This data is invaluable for tracking security improvements over time and making informed decisions about where to invest resources.
This continuous assurance has practical business benefits, too. For instance, when it comes time to renew your cyber insurance policy, providing BAS reports that prove your security controls are effective can lead to better terms and lower premiums. By validating your defenses against real-world threats, BAS helps you manage cyber risk more effectively and communicate your security posture with confidence.
Adopting Breach and Attack Simulation is a smart move, but let’s be real—it’s not always a simple plug-and-play process. Like any powerful tool, it comes with its own set of implementation hurdles. Being aware of these potential roadblocks from the start helps you choose the right solution and set your team up for success. The goal is to find a BAS platform that strengthens your security posture without creating unnecessary work for your already busy team.
The most common challenges usually fall into three buckets: managing the noise from simulated alerts, finding the time and talent to run the platform effectively, and getting it to play nicely with your existing security tools. A BAS tool that generates thousands of low-context alerts can quickly lead to fatigue, causing your team to tune out the noise and potentially miss a real threat. Similarly, a platform with a steep learning curve can sit on the shelf if no one has the bandwidth to master it. And if it doesn’t integrate with your SIEM or vulnerability scanner, you’ll be stuck trying to connect the dots manually. Thinking through these issues ahead of time will make your BAS implementation much smoother.
One of the first things teams notice when running BAS is the new stream of alerts. Because the platform is simulating attacks, it will naturally trigger your detection systems. The challenge is that these aren’t real threats, and if they aren’t handled correctly, they can contribute to alert fatigue. When your security operations center (SOC) is constantly chasing down alerts from planned simulations, they have less time and focus for genuine malicious activity. A good BAS solution should make it easy to distinguish between simulated and real events, either through clear tagging or tight integration with your SIEM, so your team can safely ignore simulation noise and stay focused on what matters.
Implementing and managing a BAS platform requires both time and specific expertise. For many organizations, security teams are already stretched thin, and adding another complex tool to the mix can feel overwhelming. Setting up simulations, interpreting the results, and translating them into actionable remediation steps requires a dedicated effort. This is a significant barrier for teams with limited resources or skill sets. When evaluating BAS platforms, look for one with an intuitive user interface, clear reporting, and actionable guidance. A solution that simplifies the process of adversarial exposure validation reduces the burden on your team and ensures you get value from your investment without needing to hire specialized staff.
A BAS platform doesn’t operate in a vacuum. To be truly effective, it needs to integrate smoothly with your existing security stack, including your SIEM, SOAR, and vulnerability management tools. This integration is what allows you to connect the dots between a simulated attack path and a specific vulnerability that needs patching. However, this can be complex, as BAS platforms require constant updates to keep their simulations relevant to the latest threats. When choosing a solution, prioritize one that offers robust, out-of-the-box integrations and is continuously updated with new threat intelligence. This ensures your security testing remains relevant and that the results are fed directly into your existing workflows, creating a more unified and efficient threat exposure management program.
Implementing a Breach and Attack Simulation (BAS) platform is a great first step, but how do you know it’s actually working? The real value comes from seeing measurable improvements in your security posture. It’s not enough to just run simulations; you need to track your progress to justify the investment and show your team’s hard work is paying off.
Measuring success helps you understand where your defenses are getting stronger and where they still need attention. By setting clear goals and tracking the right metrics, you can turn the insights from your BAS tool into a clear story of risk reduction. This data-driven approach helps you communicate your security wins to leadership and ensures your efforts are focused on what matters most: stopping real-world attacks before they happen. Let’s look at a few key ways to measure the impact of your BAS program.
Before you can measure success, you need to define what it looks like for your organization. Your Key Performance Indicators (KPIs) are the specific, measurable goals that will guide your BAS strategy. Since BAS assessments are designed to evaluate the performance of security controls and find gaps, your KPIs should reflect how well you’re closing those gaps.
Start by setting benchmarks based on your initial simulations. Good starting KPIs could include the percentage of security controls validated, the number of misconfigurations identified and fixed, or a reduction in the number of successful simulated attacks on critical assets. These metrics give you a clear baseline to measure against, helping you demonstrate concrete progress over time.
When an attack happens, every second counts. Two of the most critical metrics for any security team are Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). A successful BAS program should help you shrink both of these numbers significantly. By continuously running simulations, you can identify blind spots in your monitoring and find bottlenecks in your incident response process.
As you fine-tune your security controls and streamline your workflows based on BAS findings, you should see your detection and response times drop. Tracking these improvements provides solid proof that your team is getting faster and more efficient at handling threats. This is a powerful way to show how adversarial exposure validation directly strengthens your ability to defend against active attacks.
Ultimately, the goal of BAS is to improve your overall security posture. You can track this by monitoring the results of your simulations over time. A great metric to watch is the ratio of blocked attack simulations to successful ones. As you fix vulnerabilities and harden your controls, you should see the percentage of blocked simulations steadily increase.
This provides a high-level view of your defensive capabilities. By continuously validating that your security controls are configured correctly and working as intended, you can build a more resilient environment. A platform that provides a unified view of cyber risks makes it easier to see these enhancements across your entire attack surface, giving you confidence that your security posture is genuinely improving.
Getting started with Breach and Attack Simulation is more than just flipping a switch. To get real value from your BAS platform, you need a thoughtful approach. It’s about integrating the technology into your security program in a way that provides continuous insight and drives meaningful improvements. By focusing on the right deployment, preparing your team, and setting a smart testing schedule, you can turn your BAS tool from a simple testing utility into a core component of your threat exposure management strategy. Here are a few best practices to get you started.
Your BAS platform’s effectiveness hinges on how you deploy it. The goal is to move away from one-off security checks and toward continuous validation. Because BAS tools can run tests frequently, you get a near-constant pulse on how your defenses are performing, not just a snapshot from an annual penetration test. Choose a deployment model that supports this cadence. Whether it’s agent-based or agentless, the system should allow for automated, regular testing across your entire attack surface. This approach ensures your security control validation is always current, reflecting the true state of your environment as it changes.
A BAS platform is a powerful tool, but your team is what makes it effective. Use the simulations as practical training exercises. Instead of just seeing if a control works, measure how long it takes your security team to detect and respond to the simulated incident. This shifts the focus from a simple pass/fail on technology to a real-world test of your people and processes. You can also use these controlled simulations to help other employees understand how attacks happen, which strengthens your company’s overall security awareness. It’s a great way to test your incident response plan without waiting for a real attack.
Your security posture isn’t static, and neither are the threats you face. That’s why your BAS testing schedule needs to be consistent and frequent. Unlike traditional tests that happen quarterly or annually, BAS platforms are built to run all the time. Schedule your simulations to run daily, weekly, or monthly, depending on how quickly your environment changes. This continuous testing rhythm ensures you can quickly spot new gaps that appear after a configuration change or software update. By making these tests a regular part of your operations with a platform like Uni5 Xposure, you can stay ahead of attackers and adapt your defenses to the evolving threat landscape.
How is Breach and Attack Simulation different from a traditional penetration test? Think of a penetration test as an in-depth annual physical—it’s a manual, point-in-time assessment that gives you a valuable snapshot of your health. Breach and Attack Simulation, on the other hand, is like wearing a fitness tracker every day. It’s an automated and continuous process that gives you constant feedback on your security posture, helping you see how changes in your environment or new threats impact your defenses in near real-time.
Is it safe to run simulated attacks in our live production environment? Yes, it is. BAS platforms are designed to be non-disruptive. The simulations mimic the techniques attackers use but do so in a controlled and safe manner without using actual malicious payloads. The goal is to test your security controls and identify weak points without impacting your systems’ stability or availability. It’s the security equivalent of a fire drill—you test your response plan without having to start a real fire.
We already use a vulnerability scanner. Why do we also need BAS? A vulnerability scanner is great at creating a list of potential problems, like telling you which doors in your building have old locks. A BAS platform takes the next step by actually trying to jiggle the handles and pick the locks to see if anyone can get in. It moves beyond theoretical weaknesses to confirm which vulnerabilities are truly exploitable in your specific environment, giving you the context needed to focus on real risks.
My security team is already swamped with alerts. Won’t BAS just create more noise? It’s a valid concern, but a good BAS platform actually helps reduce noise. By showing you which of the hundreds of “critical” alerts from your scanner are actually exploitable, it helps you filter out the distractions. This allows your team to stop chasing down theoretical issues and concentrate their time and energy on the proven attack paths that pose a genuine threat to your organization.
How does BAS help us prioritize which vulnerabilities to fix first? BAS provides hard evidence to guide your remediation efforts. Instead of relying solely on a generic severity score, you can see exactly which vulnerabilities an attacker could chain together to breach your defenses. This allows you to prioritize fixes based on the actual risk they pose to your critical assets, ensuring your team is always working on the most impactful issues first.