Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Do you know every single digital asset your organization owns? For most security leaders, the honest answer is no. Between shadow IT, forgotten development servers, and complex cloud environments, your true attack surface is full of blind spots. These unknown and unmanaged assets are where attackers find their easiest entry points. Attack Surface Intelligence (ASI) is the continuous process of eliminating those blind spots. It provides the comprehensive discovery needed to map your entire digital footprint, from on-premise systems to the far corners of your cloud infrastructure. By creating a complete and always-current inventory, you establish the foundation for identifying the most dangerous attack surface intelligence exposures and taking confident, proactive steps to reduce your risk.
Think of Attack Surface Intelligence (ASI) as your organization’s security-focused GPS. It’s the ongoing process of discovering, analyzing, and managing your entire digital footprint—every internet-facing asset, from IP addresses and domains to cloud services and applications. It’s not just about listing what you own; it’s about understanding how an attacker sees those assets and what weaknesses they might exploit. In a world of sprawling cloud environments, remote work, and complex supply chains, your attack surface is constantly changing. Without a clear map, you’re essentially flying blind.
ASI provides that map by continuously scanning for both known and unknown assets. It helps you see your organization from the outside in, identifying potential entry points before a threat actor does. This proactive stance is a game-changer. Instead of just reacting to alerts, you can get ahead of threats by understanding your exposure in real-time. A strong Total Attack Surface Management strategy is built on this foundation of intelligence, allowing you to see everything you need to protect and focus your resources where they matter most. It’s about transforming a chaotic, ever-expanding list of assets into a manageable and defensible perimeter.
The journey to Attack Surface Intelligence began with Attack Surface Management (ASM). Think of ASM as the first step: the continuous process of finding, inventorying, and monitoring all of your organization’s digital and physical assets. It answers the fundamental question, “What do we have that’s exposed?” This was a huge leap forward from periodic scans, giving security teams a much better handle on their digital presence.
But just knowing what you have isn’t enough. That’s where Attack Surface Intelligence (ASI) comes in. ASI is the evolution of ASM. It takes that comprehensive inventory and adds a critical layer of context and analysis. It doesn’t just tell you what you have; it tells you what it means. ASI enriches asset data with threat intelligence, vulnerability information, and business context to help you understand your risk.
At its heart, Attack Surface Intelligence helps you see your digital weaknesses exactly as an attacker would. It’s about shifting your perspective from an internal, checklist-based view to an external, adversarial one. ASI brings together several key functions into a single, cohesive picture. It starts with comprehensive discovery to find every connected asset, including forgotten servers or unsanctioned cloud instances.
Then, it moves to analysis, where it assesses these assets for vulnerabilities, misconfigurations, and potential exposures. Finally, it provides the intelligence needed to prioritize remediation. By combining these elements, a platform like Uni5 Xposure gives you a unified view of your external security posture, making it easier to manage and defend.
The biggest difference between ASI and traditional security lies in one word: proactivity. Traditional security methods are often reactive. They rely on known signatures, established firewalls, and responding to alerts after a potential threat has been identified. It’s a necessary part of defense, but it often leaves you a step behind the attackers.
Attack Surface Intelligence, on the other hand, is inherently proactive. It aims to find and predict threats before they can be exploited. Instead of waiting for a vulnerability to be announced, ASI helps you identify the underlying exposures that could become tomorrow’s breach. This approach allows for much smarter vulnerability and threat prioritization, as you can focus on fixing the weaknesses that pose the most realistic and immediate danger to your organization.
Think of your organization’s attack surface as the sum of all possible entry points an attacker could use to get into your systems. An attack surface exposure, then, is any one of those entry points that is left unguarded. It’s more than just a known vulnerability in a piece of software; it’s any weakness, misconfiguration, or oversight across your entire digital footprint that could be exploited. These exposures can be as complex as a zero-day flaw or as simple as an open database port, an expired security certificate, or a forgotten development server still connected to the internet.
The real challenge is that your attack surface is constantly changing. Every time a new employee connects a device, a developer spins up a cloud instance, or a marketing team adopts a new SaaS tool, your attack surface grows and shifts. Without a continuous process for total attack surface management, these changes create new, unknown exposures. Managing these risks isn’t about playing a defensive game of whack-a-mole; it’s about proactively and continuously mapping your entire environment to find and fix these weak points before an attacker does.
When we talk about digital assets, it’s easy to just think of servers and laptops. But your attack surface is much broader than that. Every digital asset connected to your organization is a potential target. This includes all of your known and unknown internet-facing assets, such as websites, domains, and subdomains. It also covers your network infrastructure, like open ports and security certificates that could be misconfigured or expired. Even your cloud assets—storage buckets, databases, and virtual machines—can be sources of exposure if not properly secured. Don’t forget about code repositories and other development resources that might contain sensitive information or credentials. Each one is a potential doorway for an attacker.
Exposures can pop up anywhere your organization has a digital presence. Your attack surface spans every system, location, and even person connected to your network. This includes your traditional on-premise data centers, which might house legacy systems with unpatched vulnerabilities. It also extends across your entire cloud environment, whether you’re using AWS, Azure, or a multi-cloud setup. Remote work has added another layer of complexity, with every employee’s home network and personal devices becoming part of your extended perimeter. And as more businesses connect IoT and operational technology (OT) to their networks, these devices introduce a whole new set of potential exposures that need to be monitored.
One of the biggest challenges in managing your attack surface is accounting for the assets you don’t even know exist. This is the problem of “Shadow IT”—the hardware, software, and cloud services employees use without official approval from the IT department. When a team signs up for a new project management tool or a developer uses a personal cloud account for work, they create assets that are completely invisible to your security tools. With some studies showing that Shadow IT exists in nearly every large organization, these unmonitored assets create significant blind spots, leaving unsecured entry points wide open for attackers to find and exploit.
Your attack surface doesn’t stop at your own digital front door. It extends to every vendor, partner, and third-party software provider in your supply chain. A vulnerability in a single open-source library or a security breach at one of your key suppliers can have a direct impact on your organization. Attackers are increasingly targeting the software supply chain because it allows them to compromise one target to gain access to many. This means that even if your own security is solid, an exposure in a partner’s system could become your problem. True exposure management requires visibility not just into your own assets, but into the risks introduced by your entire ecosystem.
Building a strong Attack Surface Intelligence (ASI) program isn’t about finding one perfect tool. Instead, it’s about creating a connected ecosystem of technologies that work together to give you a complete picture of your security posture. Each tool plays a specific role, from discovering your assets to assessing their weaknesses and protecting your brand online. When these tools are disconnected, you end up with data silos and blind spots—the very things you’re trying to eliminate.
The real power comes from integrating these different functions into a single, cohesive strategy. This approach allows you to move from simply collecting data to generating actionable intelligence. You can see how an external threat relates to an internal vulnerability on a critical asset, helping you prioritize what truly matters. Let’s walk through the key categories of tools you’ll need and explore why bringing them together is so important for managing your threat exposure effectively.
You can’t protect what you don’t know you have. That’s why the first step in any ASI strategy is a comprehensive asset inventory. Tools in this category, like Cyber Asset Attack Surface Management (CAASM) platforms, are designed to solve this exact problem. They continuously scan your environment to discover and catalog every device, application, cloud instance, and user account connected to your organization. This includes everything from sanctioned IT assets to forgotten servers and shadow IT. By creating a complete and always-current inventory, you establish the foundation for all other security activities and ensure you have full visibility across your entire digital attack surface.
Once you know what assets you have, the next step is to find their weaknesses. Vulnerability assessment platforms are built for this continuous process of identifying, assessing, and monitoring your digital assets for potential threats. These tools go beyond simple, one-time scans. They constantly check your systems for misconfigurations, missing patches, and known vulnerabilities that attackers could exploit. This ongoing assessment is crucial for understanding your risk posture in real time. By integrating this data, you can prioritize vulnerabilities based not just on their severity score, but on the business criticality of the asset they affect.
Your attack surface doesn’t stop at your network perimeter. It extends across the entire internet, where attackers can impersonate your brand, leak sensitive data, or plan attacks. Digital Risk Protection (DRP) services monitor the open, deep, and dark web for these external threats. They look for things like phishing sites using your logo, compromised employee credentials for sale on forums, and mentions of your company in hacker communities. Taking this proactive stance helps you get ahead of attacks before they reach your network, protecting both your infrastructure and your reputation.
Discovering threats is only half the battle; you also need to respond quickly and effectively. This is where automated response systems come in. These platforms, which often include Security Orchestration, Automation, and Response (SOAR) capabilities, help you streamline your security workflows. They can automatically create tickets for remediation, isolate compromised devices from the network, or block malicious IP addresses. By automating these routine tasks, you free up your security team to focus on more complex investigations and strategic initiatives, ensuring that you can validate your security controls and respond to threats at machine speed.
Using individual tools for each of these functions can leave your security team drowning in alerts and struggling to connect the dots. The key to effective ASI is integration. When your asset inventory, vulnerability data, external threat intelligence, and response actions all feed into a single platform, you gain a holistic view of your attack surface. This unified approach breaks down data silos and allows you to see the full context of each risk. A platform like Uni5 Xposure provides this single pane of glass, helping you prioritize the exposures that pose the greatest threat to your business and take confident, decisive action.
Adopting an Attack Surface Intelligence (ASI) strategy is a powerful move, but let’s be real—it’s not always a simple switch. Like any meaningful change in your security program, it comes with its own set of challenges. The good news is that these hurdles are common, and with the right approach, they are entirely surmountable. Understanding these potential roadblocks is the first step to building a resilient and effective ASI program that truly protects your organization.
The shift from a reactive security posture to a proactive one requires more than just new tools; it demands a change in mindset and process. From seeing your entire digital footprint to managing the complexities of a modern IT environment, each step presents a unique challenge. Let’s walk through the five most common hurdles security teams face when implementing ASI and discuss practical ways to clear them.
You can’t protect what you don’t know you have. This is the fundamental challenge of attack surface management. With assets spread across cloud environments, on-premise data centers, and remote endpoints, achieving a complete and accurate inventory is a massive undertaking. When you consider that a recent Armis report found 74% of organizations were breached in the last year, the need for total visibility becomes crystal clear. The goal is to eliminate the blind spots that attackers love to exploit. A comprehensive approach to Total Attack Surface Management provides the continuous discovery needed to map every connected asset, ensuring nothing slips through the cracks.
Even with the best intentions, security teams are often stretched thin. Implementing a new ASI program can feel like adding another mountain to climb when your team is already navigating a mountain range. The key isn’t just about securing more budget, but about investing in the right tools that act as a force multiplier for your team. Modern platforms can automate the heavy lifting of data collection and analysis. As an Ivanti report notes, the right tools can solve data problems by integrating disparate sources into a single, clear view. This allows your team to stop wasting time on manual data wrangling and focus their expertise on strategic risk reduction.
An ASI program can’t operate in a vacuum. One of the most significant gaps many organizations have is failing to integrate security assessments into their core business processes, especially vendor management. Research from Gartner® highlights a startling trend: despite a rise in supply chain attacks, security checks often aren’t part of procurement activities. This leaves a massive, uncontrolled entry point into your network. To overcome this, you must weave security into the fabric of your operations. Making adversarial exposure validation a standard step in your vendor onboarding process is a critical move to shrink your third-party risk and secure your supply chain from the start.
Modern IT infrastructure is a tangled web of cloud services, legacy systems, IoT devices, and operational technology. The sheer complexity can be overwhelming, making it difficult to know where to even begin securing your attack surface. As Coeo Solutions points out, this complexity is one of the primary challenges with Attack Surface Management. The answer isn’t to try and fix everything at once. It’s to use intelligence to focus your efforts. A strong ASI program helps you cut through the noise by providing data-driven vulnerability and threat prioritization, allowing you to address the most critical risks first and make steady, measurable progress.
Compliance isn’t just about ticking boxes for auditors; it’s a critical component of risk management. However, navigating the web of regulations like GDPR, HIPAA, and PCI DSS can be a major challenge. Each framework has specific requirements, and proving compliance requires clear evidence of your security controls and posture. An ASI program directly supports this by providing a continuous, data-backed view of your exposures. By aligning your ASI strategy with compliance requirements, you can streamline audits, reduce legal and financial risk, and demonstrate a commitment to protecting sensitive data. This turns compliance from a periodic scramble into a sustained, manageable process.
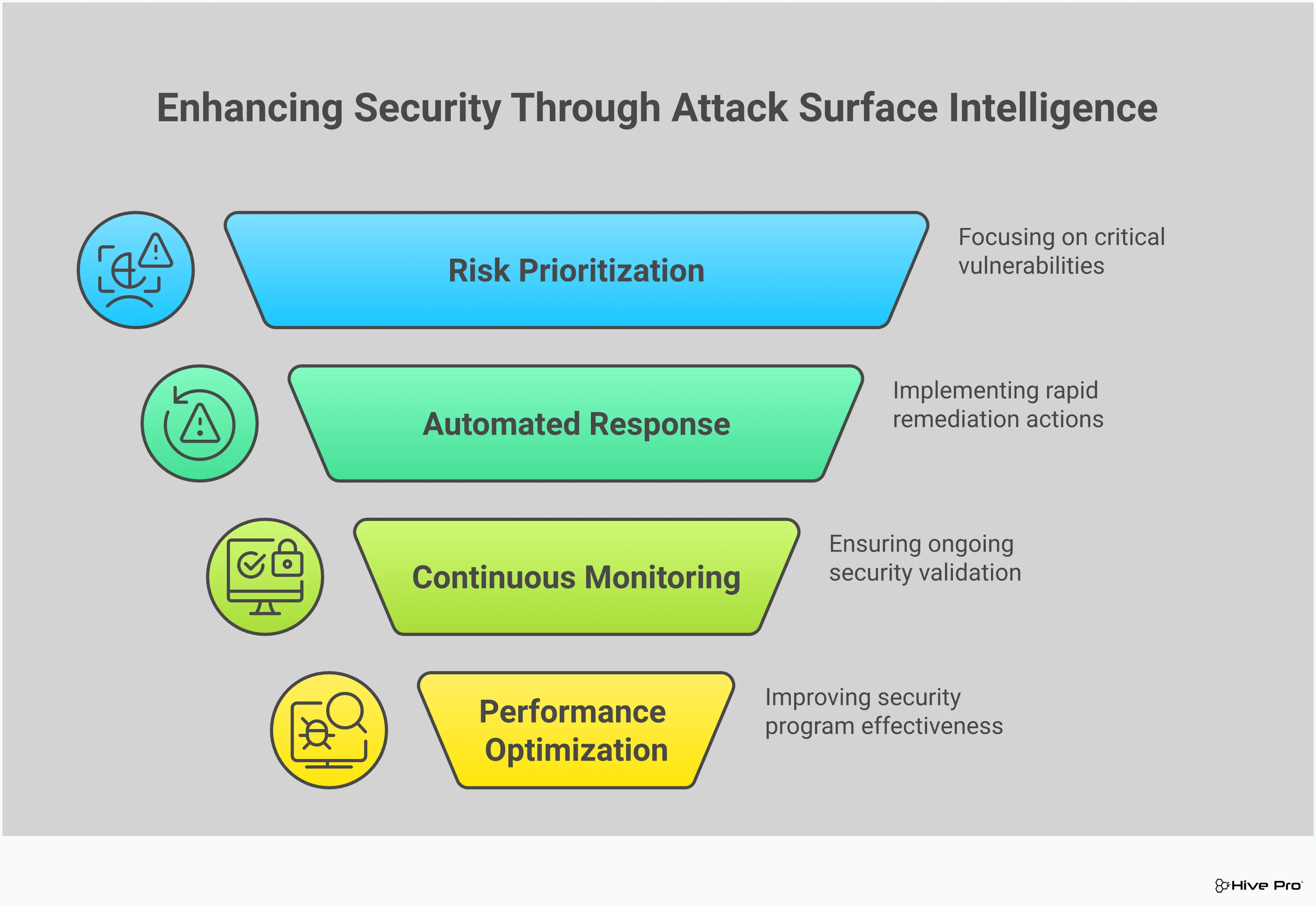
An effective Attack Surface Intelligence strategy isn’t just about buying a new tool; it’s about building a new, more dynamic process. It requires a fundamental shift from the old ways of periodic, reactive scans to a continuous, proactive security posture. A solid strategy is built on a foundation of constant vigilance, smart prioritization, and actionable intelligence that connects directly to your business context. When you have these elements in place, you can move from simply managing an endless list of vulnerabilities to truly reducing your organization’s exposure to threats that matter.
This means creating a sustainable cycle: you continuously monitor all your assets, identify the most critical risks based on real-world threat data, and have clear, repeatable protocols for responding. It’s about making informed decisions quickly and consistently, so your team isn’t wasting time on low-impact issues. Think of it as the difference between having a map that’s updated once a year versus a live GPS that reroutes you around traffic jams in real time. A strong ASI strategy is your security program’s live GPS. Let’s walk through the five essential pillars you need to construct a robust ASI strategy that delivers real results and helps your team focus on what matters most.
Your attack surface is not static—it changes every time a new device is added, a cloud instance is spun up, or a developer pushes new code. That’s why your ASI strategy must begin with continuous monitoring. This isn’t about running a scan once a quarter; it’s about having a constant, automated process that checks your entire digital presence for security risks. Think of it as a 24/7 watchtower for your domains, certificates, open ports, and cloud configurations. A continuous approach ensures you can find and fix hidden problems before an attacker does, giving you an up-to-date view of your total attack surface at all times.
Once you have visibility, the next challenge is figuring out what to fix first. A raw list of vulnerabilities can be overwhelming and often misleading. Effective prioritization is about adding context. An ASI strategy helps you do this by evaluating which weaknesses are most important to address based on factors like asset criticality, potential business impact, and active threats in the wild. Instead of treating every vulnerability as equally urgent, you can focus your team’s limited resources on the exposures that pose a genuine, immediate risk to your organization. This is the core of vulnerability and threat prioritization—turning noise into a clear, actionable plan.
Great security decisions are driven by great data. An ASI strategy moves beyond just identifying vulnerabilities; it integrates threat intelligence to help you understand your weaknesses from an attacker’s perspective. This means knowing which vulnerabilities are being actively exploited, what tactics threat actors are using, and how a specific exposure could be chained with others in an attack. By leveraging intelligence from security research teams like HiveForce Labs, you can connect potential attacks to specific sources and make smarter, faster decisions about where to direct your defensive efforts. It’s about understanding the “why” behind the risk, not just the “what.”
In a fast-moving threat landscape, manual responses are often too slow. A key part of a modern ASI strategy is establishing automated response protocols to handle routine and high-priority issues. This doesn’t mean taking humans out of the loop, but rather empowering them by automating the initial steps of the remediation process. For example, you can set up workflows to automatically create a ticket for a critical vulnerability, assign it to the right team, and even validate that a patch has been applied correctly. This approach ensures that risks are addressed consistently and quickly, freeing up your security team to focus on more complex investigations and strategic initiatives.
You can’t improve what you don’t measure. To ensure your ASI strategy is effective, you need to track your performance and demonstrate its value to the business. This involves setting clear key performance indicators (KPIs) to measure your progress. Metrics like mean-time-to-remediate (MTTR), the number of critical exposures reduced over time, and the percentage of assets covered by your program can provide tangible proof of your success. Using a unified platform to track these metrics helps break down traditional silos, giving you a clear view of your security posture and helping you communicate your program’s impact to leadership.
Transitioning to a proactive security posture requires a clear, structured approach. Building an effective exposure management program isn’t about flipping a switch; it’s about implementing a continuous cycle of discovery, prioritization, validation, and remediation. This process helps you move beyond simply reacting to threats and allows you to get ahead of them by understanding and reducing your attack surface. Many teams struggle with siloed tools and overwhelming data from different scanners, which makes it hard to see the big picture of risk. By following a methodical plan, you can break down this complexity, connect disparate security data, and create a sustainable framework that strengthens your defenses over time.
A comprehensive platform like Uni5 Xposure can unify these steps, but the strategy behind the tools is what truly drives success. It provides a single source of truth, helping you manage the entire exposure lifecycle from one place instead of juggling multiple dashboards. This unified view is critical for making informed decisions quickly and efficiently. Let’s walk through the five essential steps to build a program that gives you a true picture of your cyber risk and helps you take confident, decisive action.
You can’t protect what you don’t know you have. The first step is to gain a complete and continuously updated inventory of every asset across your organization. This goes far beyond servers and laptops. You need to account for every piece of your digital footprint, including cloud services, IoT devices, mobile endpoints, and even third-party connections. A thorough attack surface management process is foundational. Once discovered, assets must be classified based on their criticality to the business. This context is crucial for later steps, as it helps determine which vulnerabilities pose the most significant threat to your operations.
With a full asset inventory in hand, the next step is to identify weaknesses. This involves maturing your traditional vulnerability management program into a more holistic exposure management strategy. Instead of just running scans and generating lists of CVEs, this process involves understanding the broader context of security weaknesses. It means looking at misconfigurations, policy violations, and potential attack paths that an adversary could exploit. Defining a regular cadence for assessments and integrating different data sources will give you a much richer, more accurate view of your actual exposure.
Not all vulnerabilities are created equal. A critical CVE on a non-critical, internal-facing asset may be less of a priority than a medium-severity flaw on a public-facing, mission-critical application. This is where effective vulnerability and threat prioritization comes in. Your method should focus on exploitability and potential business impact. Use threat intelligence to understand which vulnerabilities are actively being targeted in the wild. By combining asset criticality, threat intelligence, and vulnerability severity, you can focus your team’s limited resources on the risks that truly matter most to your organization.
Finding a critical exposure is only half the battle; fixing it is what reduces risk. Establishing clear, efficient remediation workflows is essential for closing security gaps quickly. This involves assigning ownership for specific assets, setting realistic SLAs for patching, and providing teams with the context they need to implement fixes correctly. Beyond patching, remediation can also include proactive measures like implementing the principle of least privilege to limit an attacker’s access if a system is compromised. You can also use adversarial exposure validation to test whether your remediation efforts and security controls are actually effective against real-world attack techniques.
Exposure management is not a one-time project but a continuous lifecycle. The final step is to measure, review, and optimize your program regularly. Track key metrics like mean time to remediate (MTTR), the number of critical vulnerabilities over time, and your overall risk score. Use this data to identify bottlenecks in your workflows and areas for improvement. A mature program breaks down the traditional silos between security and IT operations, fostering collaboration and a shared understanding of risk. This ongoing feedback loop ensures your security posture evolves and adapts to the ever-changing threat landscape.
Once you have a solid grasp of your attack surface, the real work begins. The landscape of cybersecurity is constantly shifting, and staying ahead means adopting more sophisticated strategies. This is where advanced Attack Surface Intelligence (ASI) techniques come into play, moving your security program from a reactive stance to a proactive one. Instead of just mapping your assets and vulnerabilities, you can start predicting where attackers will strike next and automating your defenses to stop them.
These advanced methods leverage technologies like machine learning, predictive analytics, and real-time threat intelligence to provide a much deeper understanding of your risk profile. Think of it as upgrading from a standard map to a dynamic, 3D model that shows you not only the terrain but also weather patterns and potential roadblocks ahead. By integrating these forward-looking capabilities, you can prioritize your efforts more effectively, respond to threats faster, and build a more resilient security posture. The goal is to make intelligent, data-driven decisions that reduce your exposure before an incident ever occurs. A modern exposure management platform brings these elements together to give you a unified view of your cyber risks.
Machine learning (ML) is a game-changer for Attack Surface Intelligence because of its ability to process and find patterns in enormous amounts of data. Your security environment generates a constant stream of information—from network logs to asset configurations—and it’s impossible for human teams to analyze it all. As noted in recent industry analysis, “machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate potential vulnerabilities or threats.” This allows your organization to proactively address issues before they can be exploited. ML models can spot subtle deviations from normal behavior that might signal a misconfiguration or an emerging threat, giving your team a critical head start.
If machine learning helps you understand the present, predictive analytics helps you forecast the future. This technique uses historical data to identify trends and anticipate potential attack vectors. By analyzing past incidents, vulnerability data, and threat actor behavior, you can build models that predict where you’re most likely to be targeted next. This approach helps you “strengthen their defenses against future threats” by focusing resources on the most probable points of failure, according to research from Tenable. Instead of treating all vulnerabilities equally, you can prioritize those that are most likely to be exploited, making your remediation efforts far more efficient and impactful.
Your attack surface doesn’t exist in a bubble. To truly understand your risk, you need to see it through the eyes of an attacker. This is where integrating threat intelligence becomes essential. Real-time data on emerging threats, active campaigns, and newly exploited vulnerabilities provides the external context needed for effective prioritization. As one industry report highlights, this integration gives organizations “real-time insights into emerging threats, allowing them to prioritize vulnerabilities based on the latest threat landscape.” By connecting your internal vulnerability data with external intelligence from sources like HiveForce Labs, you can focus on fixing the weaknesses that attackers are actively targeting right now.
Discovering a critical vulnerability is important, but the clock starts ticking on remediation the moment it’s found. Automation is key to shrinking that window of exposure. By setting up automated workflows, you can streamline the entire response process, from creating a ticket to deploying a patch or updating a security control. These automation tools can “streamline the response to identified vulnerabilities, enabling organizations to quickly remediate issues.” This not only accelerates your response time but also reduces the chance of human error and frees up your security professionals to focus on more complex, strategic initiatives instead of getting bogged down in repetitive tasks.
The tools you use for ASI are evolving just as quickly as the threats they’re designed to combat. Traditional vulnerability scanners are giving way to comprehensive platforms that offer a more holistic view of exposure. These emerging security tools provide continuous monitoring and deep visibility across all of an organization’s digital assets. Modern Continuous Threat Exposure Management (CTEM) platforms integrate asset discovery, vulnerability assessment, threat intelligence, and remediation workflows into a single, unified system. This provides security teams with a centralized command center for identifying, prioritizing, and mitigating risks across their entire attack surface, making it easier to manage a complex and ever-changing environment.
What’s the main difference between the vulnerability management I’m doing now and a full exposure management program? Think of it this way: traditional vulnerability management gives you a list of problems, like known software flaws (CVEs). An exposure management program gives you a story about your actual risk. It takes that list of flaws and adds critical context, like which assets are most important to your business, whether a vulnerability is actually exploitable in your environment, and if attackers are actively using it in the wild. It helps you see the entire potential attack path, not just the individual weak spots.
My team is already swamped with alerts. Won’t this just add more noise? That’s a fair question, and it’s a concern I hear a lot. The goal of a strong Attack Surface Intelligence program is actually the opposite—it’s designed to cut through the noise. Instead of giving you thousands of low-level alerts to chase, it uses intelligence to prioritize the handful of exposures that pose a genuine, immediate threat to your business. By focusing on the intersection of a critical asset, a known threat, and an exploitable weakness, you can direct your team’s limited time and energy to fixing what truly matters.
Is Attack Surface Intelligence just a new name for Attack Surface Management? Not quite. Think of Attack Surface Management (ASM) as the foundational first step: it’s the process of discovering and creating an inventory of all your assets. It answers the question, “What do we own?” Attack Surface Intelligence (ASI) is the next evolution. It takes that inventory and enriches it with data about vulnerabilities, threat actor activity, and business context. ASI answers the more important question, “What does our attack surface mean to an attacker, and what should we do about it?”
How do I get started if I don’t even have a complete inventory of all my assets? You’re not alone—this is the most common starting point for almost every organization. The good news is that you don’t need a perfect inventory to begin. The first step of building an exposure management program is implementing a continuous discovery process. Modern tools are designed to automate this for you, scanning your environment to find everything from sanctioned servers to forgotten cloud instances. The process itself helps you build and maintain that complete inventory over time.
How does an ASI strategy help me communicate risk to our leadership team? This is one of the most powerful benefits. Instead of presenting the board with a spreadsheet of thousands of technical vulnerabilities, an ASI strategy allows you to tell a clear, concise story about business risk. You can present data-driven insights on your organization’s most critical exposures, show how they align with potential business impact, and demonstrate a clear plan for remediation. It helps you translate complex security data into the language of business, making it easier to justify resources and show measurable improvement in your security posture.