Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Is your security team spending more time chasing low-level alerts than hunting for genuine threats? It’s a common problem that leads to burnout and allows critical risks to slip through the cracks. The most significant advantage of AI cybersecurity tools is their ability to restore focus. By automating the repetitive, high-volume work of data analysis and threat triage, these systems act as a force multiplier for your team. They handle the noise so your skilled analysts can concentrate on what they do best: complex investigations, strategic planning, and proactive threat hunting. This guide explains how to choose and implement the right AI tool to make your team more efficient, reduce response times, and build a more forward-thinking security program.
At its core, an AI cybersecurity tool uses artificial intelligence to protect your organization’s digital assets. Think of it as a massive upgrade to your security stack. These tools are designed to monitor networks, spot threats, automate responses, and even predict future attacks. They work by sifting through enormous amounts of data to find anomalies and patterns that would be impossible for a human team to catch. You’ve likely heard of some of them, like Microsoft Security Copilot or Darktrace, which use AI to deliver real-time insights and build a more proactive defense. Instead of just reacting to alerts, these systems help you get ahead of threats before they can cause damage.
The integration of AI is fundamentally changing how we approach security. It’s not just about building higher walls; it’s about making them smarter. AI systems can enhance threat detection by learning what normal network activity looks like and instantly flagging deviations. This dramatically cuts down response times, allowing security teams to act faster and more decisively. AI also analyzes data at a speed and scale that humans simply can’t match, turning a flood of information into clear, actionable intelligence. This shift allows organizations to move from a reactive posture to a proactive one, anticipating threats instead of just cleaning up after them.
Let’s be honest: traditional security measures are struggling to keep up. They often fall behind on persistent threats like sophisticated phishing campaigns, new malware variants, and the simple-but-effective weak password. These ongoing cybersecurity challenges show why a more dynamic approach is necessary. The problem is that legacy tools often generate a mountain of alerts, leaving teams to manually sort through the noise. Furthermore, the effectiveness of any AI system hinges on the quality of its data. Without clean, relevant data, even the most advanced AI can produce misleading results and send your team down the wrong path.
Adopting AI-powered security tools brings some significant advantages to the table. The most immediate benefit is the combination of real-time analysis and automation. This pairing leads to much faster threat detection and response, helping your team stay ahead of fast-moving cyber threats. These tools don’t just look at the present; they analyze historical data to predict future attacks, which strengthens your overall preparedness. By automating routine tasks and prioritizing the most critical vulnerabilities, AI frees up your security professionals to focus on strategic initiatives. This is the core idea behind a modern threat exposure management platform, which helps you focus on imminent risks instead of chasing every single alert.
When you’re ready to add an AI-powered tool to your security stack, it’s easy to get lost in technical specs and marketing promises. Not all AI solutions are built the same, and the right one for your organization should feel less like another piece of software and more like a highly intelligent extension of your team. The goal is to find a tool that doesn’t just add another layer of complexity but actually simplifies your operations and strengthens your defenses in a measurable way.
Think of your evaluation process as a checklist for a new strategic partner. You need a tool that is fast, forward-thinking, and efficient. It must work well with the systems you already have in place and be capable of growing alongside your organization. Most importantly, it needs to be usable. A powerful engine is useless if your team can’t interpret the data it produces. As you assess different options, focus on these core capabilities. They are the difference between a tool that creates more noise and one that delivers clear, actionable intelligence to keep you ahead of threats. We’ll break down exactly what to look for in each of these key areas.
Modern cyberattacks move at machine speed, and your defenses need to do the same. The single biggest advantage of AI is its ability to process and correlate massive amounts of data in real time. Look for a tool that can continuously monitor your network traffic, user behavior, and system logs to spot anomalies the moment they occur. This isn’t just about flagging known signatures; it’s about identifying subtle deviations from the baseline that could indicate a novel or emerging threat. An effective AI tool automates threat detection and response, enabling a proactive defense that can neutralize threats before they cause significant damage.
The best defense is knowing what’s coming next. Go beyond tools that only react to current threats and seek out those with strong predictive capabilities. Powered by machine learning, these systems analyze historical attack data and current threat intelligence to forecast potential future attacks. They use behavior-based analytics to understand what’s normal for your environment and can predict which vulnerabilities are most likely to be targeted by attackers. This foresight allows your team to shift from a reactive posture to a proactive one, focusing your resources on shoring up the weaknesses that pose the most imminent risk. This is a key part of vulnerability and threat prioritization.
Your security team is your most valuable asset, but they’re likely buried in manual tasks and drowning in alerts. A great AI security tool should lighten that load through intelligent automation. Look for features that can automate routine processes like threat triage, risk scoring, and even initial incident response actions. By handling the repetitive, high-volume work, the AI system frees up your human analysts to concentrate on what they do best: complex threat hunting, strategic planning, and in-depth investigations. This not only makes your team more efficient but also reduces the chance of human error and burnout, helping them protect your networks from emerging threats.
A new security tool should not create another data silo. For an AI solution to be truly effective, it must integrate smoothly with your existing security infrastructure, including your SIEM, SOAR, firewalls, and ticketing systems. This ensures a unified view of your security posture and allows for a more coordinated response. When evaluating tools, check their APIs and pre-built integrations. A solution that easily connects to your current stack will provide a much higher return on investment and a smoother workflow, preventing the need for costly custom development or hiring specialized experts just to get it running.
Your organization isn’t static, and your security tools shouldn’t be either. As your business grows, so will your attack surface, data volume, and the complexity of your IT environment. The AI security tool you choose must be able to scale effortlessly to meet these future demands without a decline in performance or an unexpected surge in costs. Ask potential vendors about their architecture—is it cloud-native? How does it handle increased data loads? A scalable solution ensures that your security capabilities can keep pace with your growth, providing consistent protection for your entire attack surface for years to come.
Advanced AI is incredibly complex, but using it shouldn’t be. The most powerful tool is ineffective if your team finds it difficult to use or interpret its findings. Look for a solution with a clean, intuitive user interface that translates vast amounts of data into clear, actionable insights. Dashboards should provide an at-a-glance view of your security posture, reports should be easy to generate and understand, and workflows should feel logical. A user-friendly interface empowers your entire team to make faster, more confident decisions, ensuring you get the full value out of the tool’s sophisticated capabilities.
Choosing the right AI security tool can feel overwhelming with so many options on the market. To help you cut through the noise, I’ve put together a list of some of the top platforms that security teams are relying on today. Each tool brings something different to the table, from proactive exposure management to real-time endpoint protection. Think about your specific needs—whether it’s simulating attacks, securing a cloud environment, or automating incident response—as you review these leading solutions.
Hive Pro’s Uni5 Xposure Platform is designed to shift your security posture from reactive to proactive. Instead of just waiting for alerts, it helps you get ahead of threats by continuously managing your threat exposure. A key feature is its advanced Breach and Attack Simulation (BAS) capability, which lets you safely mimic the attack paths and techniques that real adversaries use. This simulation helps you find and fix security gaps before they can be exploited. By providing a unified view of your cyber risks, Uni5 helps your team focus on the vulnerabilities that matter most, guiding you toward efficient and effective remediation. It’s a great fit for teams looking to transform their vulnerability management program.
For teams heavily invested in the Microsoft ecosystem, Microsoft Security Copilot acts as a powerful AI assistant. It processes vast amounts of security data to identify threats and recommend clear, actionable steps for remediation. Its main strength lies in its seamless integration with other Microsoft security tools, like Sentinel and Defender. This allows it to quickly summarize complex incidents, analyze scripts, and guide analysts through response workflows using natural language. It’s designed to help security teams work more efficiently by simplifying investigation and response, making it a valuable addition for organizations looking to get more out of their existing Microsoft security stack.
Darktrace takes a unique approach with its Enterprise Immune System. Instead of relying on predefined rules, its AI learns the normal pattern of life for your entire digital environment—from networks and cloud infrastructure to endpoints. Once it establishes this baseline, Darktrace can spot subtle deviations that signal an emerging threat, even from novel or sophisticated attackers. What makes it stand out is its ability to take autonomous action to contain threats in real time, neutralizing attacks before they can cause damage. This makes it particularly effective for catching insider threats and other tricky attacks that might otherwise go unnoticed by traditional security tools.
SentinelOne’s Singularity Platform is a leader in endpoint security, offering robust protection for a wide range of devices, from laptops and servers to cloud workloads. It uses AI-powered behavioral analysis to detect and stop ransomware, malware, and other advanced threats in their tracks. The platform excels at automating threat hunting and incident response. When a threat is detected, it can immediately kill the malicious process, quarantine the file, and even roll back the affected device to its pre-infection state. This real-time, autonomous response capability helps security teams contain threats quickly across their entire fleet of endpoints, significantly reducing the time to remediation and minimizing potential damage.
The CrowdStrike Falcon platform is another top contender in the endpoint security space, built from the ground up as a cloud-native solution. This architecture makes it lightweight, scalable, and easy to deploy without requiring on-premises hardware. Falcon combines next-generation antivirus, endpoint detection and response (EDR), and a 24/7 managed threat hunting service all in one platform. It leverages AI and a massive threat graph to analyze trillions of events per week, allowing it to detect and respond to threats with incredible speed and accuracy. Its strong integration of threat intelligence helps organizations stay ahead of emerging adversary tactics, making it a go-to choice for businesses of all sizes.
IBM QRadar is a well-established Security Information and Event Management (SIEM) platform that uses AI to make sense of the massive volumes of log and event data generated across an organization. It correlates information from network devices, servers, and applications to identify potential security incidents. Where AI comes in is by enhancing threat detection with user behavior analytics and automating the initial stages of incident analysis. This provides security teams with prioritized, actionable insights, helping them focus on the most critical threats. QRadar helps reduce alert fatigue and speeds up investigation times, making it a cornerstone for many security operations centers (SOCs).
Theory is great, but seeing how AI-powered security tools perform in the real world is what truly matters. Different industries face unique threats and compliance requirements, and AI’s adaptability makes it a powerful ally across the board. From protecting sensitive patient records to securing the power grid, AI is helping security teams get ahead of threats by providing context-aware, proactive defense. Let’s look at how AI is making a tangible difference in several key sectors.
The healthcare industry is a prime target for cyberattacks due to the high value of protected health information (PHI). AI-powered security tools are essential for safeguarding this sensitive data. By continuously analyzing network traffic and user behavior, AI can automate threat detection and identify anomalies that might indicate a breach, like unauthorized access to patient records. This allows security teams to respond faster and more effectively, fortifying their defenses against ransomware and other evolving risks. AI helps create a more proactive security posture, ensuring that patient data remains confidential and secure.
In financial services, the speed and security of transactions are paramount. A single breach can have devastating consequences. AI security systems are a massive help to security teams, offering real-time protection against emerging threats. These tools can analyze millions of transactions in seconds, detecting fraudulent patterns and suspicious activities that would be impossible for human analysts to catch. This is especially critical for safeguarding transaction data and maintaining customer trust. By using AI to prioritize threats, financial institutions can focus their resources on the most significant risks, protecting their networks and client assets.
Manufacturing environments increasingly rely on connected operational technology (OT), which creates new entry points for attackers. Protecting these systems is vital for preventing production shutdowns and ensuring safety. AI enhances industrial cybersecurity by automating threat detection and response in complex OT networks. It can learn the baseline behavior of industrial control systems and immediately flag any deviations. This allows companies to save time and resources, moving from a reactive to a proactive defense of their critical operational assets.
Retail businesses handle enormous volumes of customer data, from personal details to payment information, making them attractive targets for cybercriminals. AI is a game-changer for retail cybersecurity, automating the detection of threats like sophisticated phishing campaigns aimed at stealing credentials. By analyzing customer behavior and transaction patterns, AI can quickly identify and block fraudulent activities. This automated defense is critical for protecting sensitive customer information at scale, helping retailers build a secure shopping experience and maintain their brand reputation. A strong threat exposure management platform can provide the unified view needed to manage these diverse risks.
The energy sector underpins our entire economy, making its cybersecurity a matter of national security. Attacks on critical infrastructure can have widespread and catastrophic effects. AI tools are indispensable for providing the real-time monitoring and proactive defense needed to protect these vital systems. By analyzing data from across the attack surface, AI can identify potential threats before they can cause damage. This strategic approach is essential as industrial enterprises face a rising tide of cybersecurity threats and attacks, ensuring the grid remains stable and secure.
As AI becomes more integrated into cybersecurity, it’s easy to get tangled in the hype and misconceptions. You’ve probably heard claims that sound too good to be true—or so daunting they make you hesitant to adopt the technology. Let’s clear the air and separate fact from fiction. Understanding what AI can and can’t do is the first step to building a security strategy that’s both realistic and effective. By addressing these common myths, you can make more informed decisions and set your team up for success.
This is one of the most persistent myths out there. The reality is that AI is a powerful partner for your security team, not a replacement. Think of it as a force multiplier that handles the heavy lifting of sifting through massive datasets to find potential threats. This frees up your analysts to focus on what they do best: strategic thinking, complex investigation, and decision-making. AI is designed to augment human capabilities, handling the repetitive tasks so your experts can apply their skills where it matters most. Your team’s intuition and experience are irreplaceable.
AI is incredibly powerful, but it isn’t perfect. An AI system’s effectiveness is directly tied to the quality of the data it’s trained on. If the data is flawed or incomplete, the AI can produce misleading results or false positives, sending your team on a wild goose chase. This is why human oversight is critical. Your analysts must be able to validate the AI’s findings, fine-tune its algorithms, and provide the context that a machine might miss. Treat AI-generated alerts as highly qualified leads, not as absolute truths that require no further investigation.
While it’s true that building an AI security model from scratch is a complex undertaking, you don’t have to start there. Modern AI-powered security platforms are designed for easier integration into your existing stack. The key is choosing a solution that fits your environment and having a clear plan. While applying AI with high precision requires specialization, many vendors provide the support and expertise needed to get you up and running. The focus should be on finding the right tool and partner to guide your implementation, not on becoming a machine learning expert overnight.
The sticker price of an AI security tool can seem high, but it’s important to look at the bigger picture and consider the return on investment (ROI). High implementation costs are a valid concern, but they are often offset by significant long-term savings. Think about the cost of a major data breach, the hours your team spends manually investigating low-level alerts, or the financial impact of operational downtime. AI-driven automation reduces incident response times, improves your team’s efficiency, and helps you proactively stop threats before they cause real damage.
No single tool can offer 100% protection, and AI is no exception. It’s a powerful component of a defense-in-depth strategy, but it’s not a silver bullet. AI excels at identifying patterns and anomalies, but it should be part of a broader security framework that includes firewalls, endpoint protection, and, most importantly, a skilled security team. The most effective security posture is one where AI complements existing security measures, creating a layered defense that is much harder for attackers to penetrate. AI enhances your capabilities, but it doesn’t replace the need for a comprehensive security program.
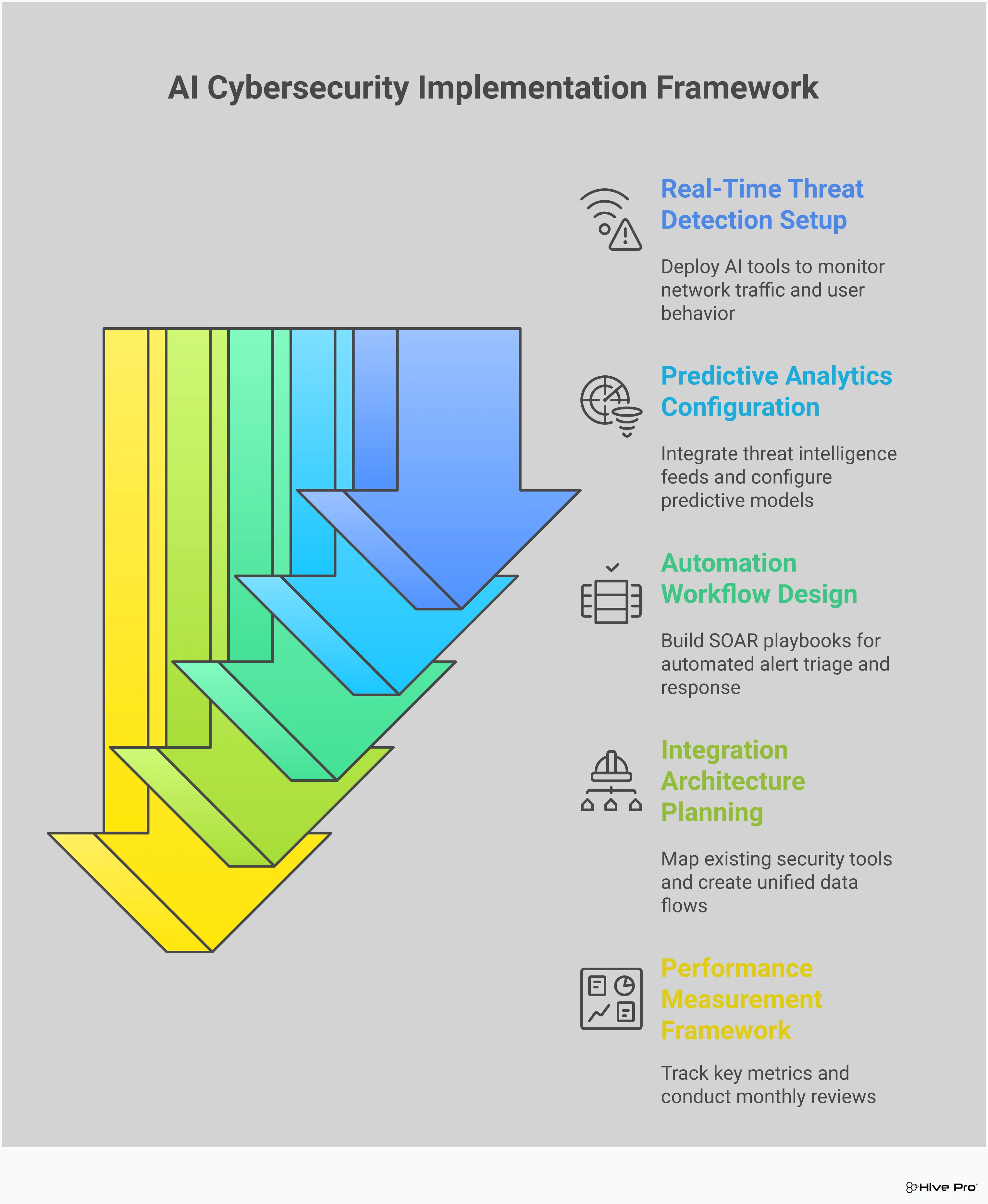
Bringing a new AI-powered tool into your security stack is more than just a technical update—it’s a strategic move that can redefine your team’s effectiveness. But simply buying the best software isn’t enough. A successful implementation requires a clear plan that covers everything from initial evaluation to ongoing performance monitoring. Without a thoughtful approach, even the most advanced tool can fall short of its potential, creating more noise than clarity. Let’s walk through the key steps to ensure your new AI security tool delivers real value from day one, helping you move from a reactive posture to proactive defense.
Before you even look at demos, you need to define what success looks like for your organization. Start by identifying the specific security gaps you want to close. Are you struggling with alert fatigue? Do you need to shorten your mean time to respond (MTTR)? Are you trying to get a unified view of your entire attack surface? Your goals will become the foundation of your evaluation criteria. Remember, the effectiveness of any AI system depends on the quality of the data it ingests. A tool that can’t integrate with your existing data sources or make sense of your unique environment won’t be effective. Your framework should prioritize solutions that provide a clear, consolidated view of your cyber risks, like the Uni5 Xposure Platform, to ensure the AI has the right context to work with.
A new AI tool should feel like a natural extension of your security operations, not a clunky add-on. A solid integration strategy is crucial. Map out how the tool will connect with your existing security information and event management (SIEM), security orchestration, automation, and response (SOAR), and ticketing systems. Will it require custom APIs, or does it offer out-of-the-box integrations? Your goal is to create a seamless workflow where insights from the AI tool can be acted upon quickly. A well-planned integration prevents data silos and ensures that the tool’s automated capabilities can be fully utilized, turning threat intelligence into decisive action without disrupting your team’s current processes.
AI is here to empower your team, not replace it. However, your analysts need to understand how to work with these new capabilities. Effective training goes beyond learning a new user interface; it’s about teaching your team how to interpret the AI’s recommendations, validate its findings, and understand its limitations. Building AI models for cybersecurity requires trained experts who can assess key performance indicators (KPIs) and fine-tune the system. Invest in training that helps your team build trust in the tool and use its insights to make more informed decisions. When your team understands the “why” behind the AI’s output, they can operate with greater confidence and speed.
Once the tool is up and running, your job isn’t over. You need to continuously monitor its performance against the goals you set in your evaluation framework. Key metrics might include the reduction in false positives, the speed of threat detection, and the accuracy of vulnerability and threat prioritization. Applying AI in a real-world environment comes with unique challenges, and you’ll likely need to make adjustments along the way. Schedule regular check-ins to review the data, gather feedback from your team, and fine-tune the tool’s configuration. This iterative process ensures the tool remains aligned with your security objectives and continues to deliver a strong return on investment.
The conversation around AI tools often includes concerns about high implementation costs. To make a smart investment, you need to look beyond the initial price tag and consider the total cost of ownership (TCO). This includes expenses for integration, training, and ongoing maintenance. The best way to justify the cost is to demonstrate a clear return on investment (ROI). Calculate the potential savings from reduced manual effort, faster incident response, and the prevention of costly breaches. When you can show that the tool not only strengthens your security posture but also improves operational efficiency, it becomes a much easier conversation to have with stakeholders.
The world of AI in cybersecurity is moving incredibly fast. What felt like a futuristic concept just a few years ago is now a standard part of the modern security stack. But the innovation isn’t slowing down. As both attackers and defenders get more sophisticated with AI, the tools and strategies we use will continue to change. Staying ahead means understanding where the technology is headed. For security teams, this isn’t just about adopting new tools; it’s about preparing for a new paradigm of threat detection, response, and management. The future is less about reacting to alerts and more about proactively reducing exposure with intelligent, automated systems. Let’s look at some of the key trends shaping the next wave of AI in cybersecurity.
We’re moving beyond basic machine learning models into an era of more autonomous systems. The next generation of AI tools will rely on advanced techniques like deep learning for malware detection and behavior-based analytics that can spot an anomaly without needing a pre-existing signature. Think of it as shifting from a security guard who only checks IDs to one who can recognize suspicious behavior. These advancements are making autonomous threat detection a reality, where AI can not only identify a potential threat but also analyze its context and potential impact with minimal human intervention. This allows security teams to focus their energy on the most complex and critical incidents.
For years, cybersecurity has been a reactive field. An attack happens, and we respond. AI is flipping that script. The evolution of predictive analytics means we can now use AI to forecast where and how attacks are likely to occur. By analyzing vast datasets of historical threats, network traffic, and global threat intelligence, AI models can identify patterns that signal a future breach. This allows teams to proactively prioritize threats and patch vulnerabilities before they can be exploited. While this introduces challenges like managing potential false positives, the ability to anticipate an attacker’s next move is a massive advantage for any defense team.
How do you know if your defenses will hold up against an AI-powered attack? You fight fire with fire. Breach and Attack Simulation (BAS) is getting a major upgrade with AI, making security validation more dynamic and realistic. Instead of running static, predictable tests, AI-driven platforms can simulate attacks that mimic the adaptive, unpredictable nature of modern adversaries. These smart simulations can probe your entire attack surface, identify weak points in your controls, and provide clear guidance on where to focus your remediation efforts. It’s the ultimate way to pressure-test your defenses and ensure you’re prepared for what’s coming.
As we integrate AI more deeply into our security operations, conversations around ethics and privacy are becoming essential. We have to ask critical questions: Is the AI model biased? How are we protecting the data used to train these systems? An AI model with inherent biases could inadvertently overlook certain types of threats or create blind spots in your defenses. Organizations must address these ethical considerations to build trust and ensure their AI tools are both effective and responsible. Expect to see more demand for transparency in how AI security tools make decisions, ensuring they operate fairly and without compromising user privacy.
AI is no longer just a feature; it’s becoming the foundation of modern cybersecurity. We’re seeing the rise of comprehensive, AI-powered solutions that unify different security functions into a single, intelligent system. Instead of juggling dozens of disconnected tools, security teams can use unified platforms that leverage AI across the board—from attack surface management and vulnerability prioritization to threat detection and response. This integration automates routine tasks, provides a holistic view of risk, and enables security teams to act with more speed and confidence. This trend will only accelerate as organizations seek more efficient and effective ways to manage their cyber risk.
Will AI security tools make my security team’s jobs obsolete? Not at all. Think of an AI tool as the most efficient junior analyst you’ve ever had, not a replacement for your seasoned experts. Its job is to handle the high-volume, repetitive work of sifting through data and flagging potential issues. This frees up your human team to focus on the work that requires critical thinking, like complex threat hunting, strategic planning, and making the final call on a response. The goal is to augment your team’s capabilities, not replace their invaluable experience and intuition.
My team is already overwhelmed with alerts. Won’t an AI tool just add more noise? This is a common concern, but a good AI tool should do the exact opposite. Instead of just generating more alerts, it intelligently correlates data from different sources to connect the dots. It learns what normal activity looks like in your specific environment, so it can distinguish a real threat from a harmless anomaly. The best systems prioritize findings based on actual risk, so your team can stop chasing down every minor alert and focus their attention on the vulnerabilities that truly matter.
What’s the real difference between a traditional security tool and one powered by AI? Traditional tools are generally reactive. They rely on known signatures and predefined rules to catch threats that have been seen before. An AI-powered tool is proactive. It uses machine learning to analyze behavior and identify patterns, allowing it to spot novel and emerging threats that don’t have a known signature. It moves beyond just blocking known bad actors to predicting where the next attack might come from, giving you a chance to fix weaknesses before they can be exploited.
How can I trust the recommendations an AI tool makes? Trust is built through transparency and validation. A quality AI tool won’t just give you an answer; it will show you its work by providing the context and data behind its recommendations. Your team’s expertise is crucial here. They should treat the AI’s output as a highly qualified starting point for their own investigation. Over time, as you fine-tune the system and validate its findings, your team will learn its strengths and build confidence in its ability to guide them toward the right decisions.
How do I start evaluating AI tools if I have a limited budget? You don’t need a massive budget to get started, but you do need a clear objective. Begin by identifying your single biggest security challenge, whether it’s slow incident response or a lack of visibility into your attack surface. Focus your search on tools that are specifically designed to solve that problem. Look for scalable, cloud-native solutions that don’t require a huge upfront investment in hardware. By demonstrating a clear return on investment on a specific pain point, you can build a strong case for expanding your use of AI in the future.