Comprehensive Threat Exposure Management Platform
For too long, security has been a defensive game of whack-a-mole. A new threat appears, and we scramble to patch it. But what if we could see our organizations the way an attacker does? Attackers don’t care about your patching cadence or your CVSS scores. They look for the path of least resistance—a chain of misconfigurations, overlooked assets, and exploitable weaknesses that leads them to your most critical data. Adopting a proactive strategy for exposure management cybersecurity allows you to get ahead of them. It’s about systematically mapping your potential attack paths and shutting them down before they can be used against you. This article will explain how to build this attacker-centric view, helping you move from a reactive state of defense to a proactive one where you’re strategically reducing risk.
Think of exposure management as a continuous cycle for finding, evaluating, and fixing security risks across your entire digital footprint. It’s a proactive strategy that goes beyond simply listing vulnerabilities. Instead, it helps you understand how different weaknesses could chain together to create a real attack path that threatens your most critical assets. This approach shifts the focus from individual, isolated flaws to the bigger picture of your organization’s overall security posture.
The goal is to see your organization through an attacker’s eyes. By identifying and mapping out potential attack paths, you can get ahead of threats before they become incidents. This process involves a constant loop of discovery, prioritization, and validation, ensuring your security efforts are always directed at the most significant risks. A Continuous Threat Exposure Management (CTEM) program provides a framework for this, helping you move from a reactive state of patching fires to a proactive one where you’re strategically reducing your attack surface.
For too long, security teams have been stuck in a reactive cycle: a critical vulnerability is announced, and everyone scrambles to patch it. This approach is stressful, inefficient, and leaves you constantly on the defensive. Proactive security flips the script. By continuously identifying and addressing exposures, you can shut down potential attack paths before they are ever exploited by malicious actors.
This shift allows you to move from a rush-to-fix mentality to a more strategic one. Instead of just reacting to the latest threat, you can focus your resources on the weaknesses that pose a genuine risk to your business. This not only strengthens your defenses but also helps your team work more effectively, preventing burnout and making your security program more resilient in the long run.
A strong exposure management program is built on five key steps that form a continuous cycle. It starts with scoping, where you define which assets are most critical to your business and need protection. Next is discovery, which involves mapping your entire digital attack surface to find every asset, known and unknown.
Once you have a complete picture, you move to prioritization, where you assess which risks are most important to address based on factors like exploitability and business impact. Then comes validation, where you test if these prioritized risks are actually exploitable in your environment. Finally, mobilization is about getting the right information to the right teams so they can efficiently remediate the confirmed exposures.
If you feel like you’re hearing the term “exposure management” everywhere, you’re not alone. While it might seem like just another industry buzzword, it represents a fundamental shift away from older, more reactive security practices. Think of it as an evolution. Traditional vulnerability management is a critical piece of the puzzle, but exposure management is about seeing the entire picture. It moves your security program from a reactive checklist of patching CVEs to a proactive strategy focused on protecting what matters most to your business.
Instead of just asking, “Are we vulnerable?” exposure management asks, “How could an attacker get to our most critical assets, and what’s the most effective way to stop them?” This approach connects technical weaknesses to real business impact, helping you make smarter, faster decisions. It’s about understanding your entire attack surface and focusing your team’s limited time and resources on the threats that pose a genuine risk to your organization. This strategic view is what separates a good security program from a great one.
For years, vulnerability management has been the standard. You scan your assets, get a long list of CVEs, and try to patch them, usually starting with the highest CVSS scores. The problem is, this approach often lacks context. A “critical” vulnerability on a non-essential, isolated server isn’t nearly as risky as a “medium” one on your primary database server. Traditional methods can lead to a constant, overwhelming cycle of patching without a clear sense of which fixes actually reduce the most risk. This focus on individual vulnerabilities means you might miss how attackers chain weaknesses together to create a pathway to your most sensitive data.
Exposure management steps back to look at the entire landscape. It goes beyond just software vulnerabilities to include misconfigurations, identity and access issues, cloud security gaps, and other weaknesses across your digital environment. It’s about understanding all the potential entry points and attack paths an adversary could use. By adopting a more holistic view, you can see how different exposures connect and which ones create the most dangerous opportunities for attackers. This comprehensive perspective is the foundation of a modern threat exposure management program, allowing you to see your organization through the eyes of an attacker and secure it accordingly.
This is where exposure management truly changes the game. Instead of relying solely on static severity scores, it prioritizes remediation based on actual business risk. It answers the crucial questions: Is this vulnerability on a business-critical asset? Is there evidence of it being actively exploited by threat actors? Could it be combined with other exposures to cause a major incident? By layering threat intelligence and business context onto your vulnerability data, you can create a prioritized list of actions that directly addresses the most significant threats to your organization. This ensures your team is always working on the fixes that matter most, not just the ones that look scariest on paper.
Exposure management isn’t a one-time project you can check off a list; it’s a continuous, cyclical process that helps your security program mature. Think of it as a strategic loop that keeps you ahead of threats by constantly refining your understanding of your security posture. By breaking it down into distinct phases, you can create a repeatable framework for systematically discovering, prioritizing, and fixing the security gaps that attackers are most likely to exploit. This approach moves your team from a reactive state of constantly fighting fires to a proactive one where you’re strategically reducing your attack surface.
Each step in the process builds on the last, creating a comprehensive picture of your organization’s exposure. It starts with understanding what you have, then figuring out how it could be attacked, deciding what to fix first, and finally, taking action. This methodical approach ensures that your team’s efforts are always focused on the risks that pose the most significant threat to your business. It’s about working smarter, not just harder, to build a more resilient and defensible security posture.
You can’t protect what you don’t know you have. The first step is to get a complete inventory of every digital asset your company uses. This goes far beyond just servers and laptops. You need to account for everything, including cloud services, web applications, mobile devices, and even smart office equipment (IoT). Creating a comprehensive inventory is the foundation of any effective security program. This initial discovery phase gives you the baseline visibility needed to understand the full scope of your potential attack surface. Without this complete picture, critical assets can be left unmonitored and unprotected, creating blind spots that attackers can easily exploit.
Once you have a handle on all your assets, the next step is to see them from an attacker’s point of view. This involves discovering and mapping all the potential entry points into your organization. You’ll need to identify everything from public-facing services and open ports to leaked credentials and known software vulnerabilities. This process helps you understand how different assets connect and where the most critical pathways for an attack lie. A thorough mapping of your attack surface is essential for visualizing how a threat actor might move through your network, allowing you to identify and secure the most likely points of entry before they can be compromised.
Not all vulnerabilities are created equal. After identifying potential risks, you need to prioritize them based on their real-world threat level, not just a generic severity score. This means considering factors like whether a vulnerability is being actively exploited in the wild and what business impact a successful attack would have. This is where you can use a vulnerability and threat prioritization strategy to focus your resources on the issues that matter most. Validating these risks—confirming they are exploitable in your specific environment—ensures your team isn’t wasting time on theoretical threats and can instead concentrate on fixing the most critical exposures first.
This is where you turn insight into action. The final step in the cycle is to mobilize your teams to remediate the prioritized risks. Remediation isn’t just about patching. It can involve changing system configurations, updating security policies, or implementing new tools to mitigate a threat. The key is to take decisive, proactive measures to close the security gaps you’ve identified. This phase completes the loop, but it’s not the end. Effective exposure management requires you to continuously repeat this process, constantly refining your defenses as your attack surface and the threat landscape evolve.
Having a list of vulnerabilities is one thing; knowing which ones attackers are actually using is another. This is where threat intelligence comes in, acting as a powerful filter for the noise. It provides the real-world context you need to understand your true exposure. Instead of staring at a mountain of potential issues, you can pinpoint the specific weaknesses that threat actors are targeting right now.
This shift in perspective is fundamental to effective exposure management. It allows your team to move beyond generic severity scores and focus on the threats that pose a clear and present danger to your organization. By integrating up-to-the-minute data on attacker tactics, techniques, and procedures (TTPs), you can make informed, strategic decisions. This intelligence, often curated by dedicated research teams like HiveForce Labs, helps you allocate your resources precisely where they’ll have the greatest impact, ensuring you’re always working to stay ahead.
Threat intelligence transforms raw vulnerability data into actionable business insights. A high CVSS score doesn’t always mean high risk to your business. The critical question is: Is anyone actually exploiting it? Threat intelligence answers this by layering on crucial context, such as whether a public exploit is available, if it’s part of a known exploit kit, or if it’s being used in active ransomware campaigns. This allows for a much more nuanced vulnerability and threat prioritization process. You can start to see your risk not as a simple number, but as a dynamic reflection of the current threat landscape.
The most valuable insight threat intelligence offers is the confirmation that a vulnerability is being actively exploited in the wild. This is the signal that cuts through all the chatter. When you can correlate threat data from multiple sources and see that a specific weakness in your environment is on an attacker’s target list, it immediately becomes a top priority. Security teams can use this information to identify patterns that might indicate an impending attack. Access to timely threat advisories gives you the specific details needed to find and fix these critical exposures before they can be leveraged against you.
Ultimately, the goal is to fix what matters most, first. With a clear, intelligence-driven picture of your most critical exposures, your team can make data-driven decisions about where to direct their remediation efforts. This focused approach stops the endless cycle of patching low-risk vulnerabilities and allows you to concentrate on closing the gaps that attackers are actively targeting. Using a unified platform like Uni5 Xposure helps you operationalize this intelligence, streamlining the entire process from discovery to remediation and proving to leadership that you are effectively reducing the organization’s most significant risks.
After you’ve identified your most critical exposures using threat intelligence, the next logical question is: “Are our defenses actually strong enough to stop an attack?” This is where Breach and Attack Simulation (BAS) comes in. Think of it as a security fire drill for your digital environment. Instead of just assuming your security controls will work, BAS actively tests them by simulating the same tactics, techniques, and procedures (TTPs) that real-world attackers use.
This proactive approach is a game-changer for vulnerability management. It moves you beyond theoretical risk scores and into the realm of empirical evidence. By running controlled attack simulations, you can see exactly how your security stack performs against specific threats. This process of adversarial exposure validation is essential for understanding which weaknesses could actually be exploited to cause harm. It helps you find and fix gaps in your defenses—like misconfigured firewalls or ineffective endpoint protection—before a real adversary finds them for you. It answers the “so what?” for every vulnerability, showing you the potential impact in a way a simple severity score never could. This allows your team to prioritize with confidence, focusing resources on the fixes that will have the most significant impact on your overall security posture.
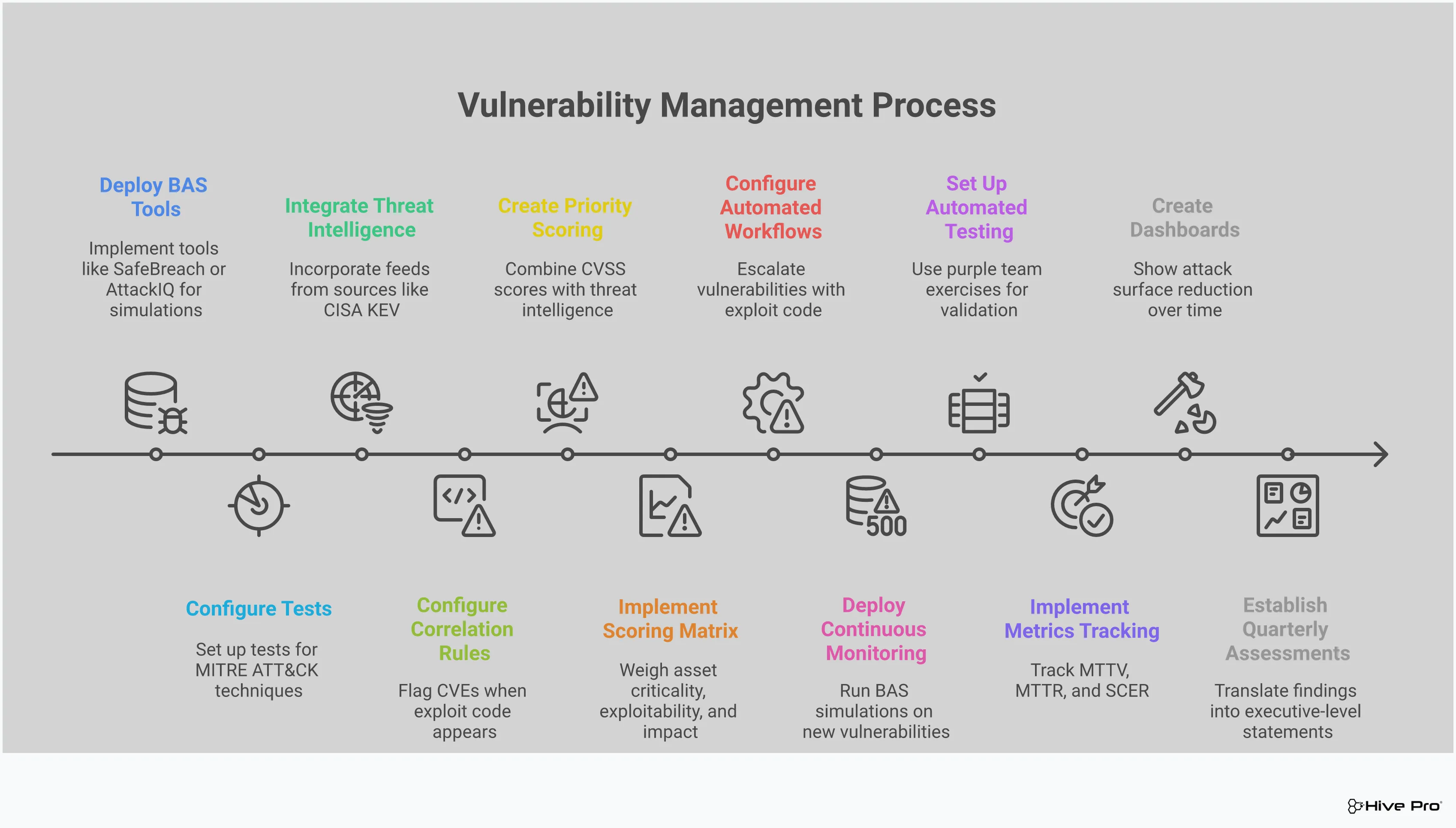
Having a suite of security tools is one thing; knowing they are configured correctly and working effectively is another. BAS provides the proof. It systematically tests your security controls—from firewalls and intrusion prevention systems to endpoint detection and response (EDR) tools—against a wide array of attack scenarios. This helps you answer critical questions like, “Did our SIEM generate an alert for this activity?” or “Did our EDR block this specific malware execution technique?” By validating your controls, you can confirm that your security investments are delivering the protection you expect and identify areas that need fine-tuning. This shifts the focus from simply having security tools to ensuring they provide measurable security outcomes.
One of the biggest advantages of BAS is its ability to test real-world attack scenarios without putting your production systems at risk. These simulations are not just theoretical; they replicate the actual attack paths that adversaries use to move from an initial entry point to your most critical assets. For example, a simulation might test if a phishing email could lead to credential theft, lateral movement, and ultimately, data exfiltration. This provides your team with invaluable, business-focused insights. Instead of just seeing a high CVSS score, you see a clear, demonstrable path an attacker could take, helping you prioritize the vulnerabilities that pose the most immediate and significant danger to your organization.
Your digital environment is constantly changing, and so is the threat landscape. New assets come online, configurations are updated, and attackers develop new techniques every day. Because of this, security validation can’t be a one-time event. Exposure management is a continuous program, and BAS is the engine that drives its validation cycle. By integrating automated and continuous simulations into your security operations, you can consistently check your security posture. This creates a constant feedback loop, allowing you to track your defensive capabilities over time, measure improvement, and ensure that your defenses remain effective against the latest threats targeting your industry.
Moving to an exposure management model isn’t just about changing processes—it’s about unlocking real, measurable benefits for your security program and the business as a whole. By shifting your focus from chasing individual vulnerabilities to understanding your complete risk picture, you can make smarter decisions, strengthen your defenses, and prove the value of your security efforts.
Instead of working from a never-ending list of vulnerabilities, exposure management gives you a clear, prioritized roadmap. It takes a holistic view of your entire attack surface, using threat intelligence to highlight which issues pose a genuine threat to your organization. This approach helps you cut through the noise of low-risk alerts and focus your team’s energy on the fixes that matter most. You can move from a reactive, patch-everything mindset to a strategic one, where every action is directly tied to reducing your most significant business risks. This makes your vulnerability and threat prioritization process much more straightforward and effective.
True security isn’t just about preventing breaches; it’s about ensuring the business can keep running even when faced with an attack. Exposure management helps you build this resilience. By mapping potential attack paths and understanding how threats could impact your most critical assets, you can design more robust defenses. This means you’re not just patching software; you’re protecting the core operations that keep your business afloat. Gaining a complete view of your total attack surface allows you to proactively secure the pathways that attackers are most likely to exploit, making your organization much harder to disrupt.
Security teams are often stretched thin, buried under a mountain of alerts and raw vulnerability data. Exposure management helps lighten that load by translating technical data into clear, business-focused insights. Instead of just reporting on the number of vulnerabilities patched, your team can show how they’ve reduced risk for specific business units or critical applications. A unified platform like Uni5 Xposure automates much of the discovery and prioritization work, freeing up your analysts to focus on strategic remediation and threat hunting. This transforms your security function from a cost center into a strategic business partner.
When a critical threat appears, every second counts. Mean Time to Remediation (MTTR) is a key metric that measures how quickly your team can neutralize a threat, and exposure management is one of the best ways to drive that number down. By continuously identifying and prioritizing your most significant exposures, you eliminate the guesswork. When a high-risk vulnerability needs fixing, your team already has the context to act immediately. This focused approach ensures your most valuable resources are spent on the most urgent problems, helping you close critical security gaps faster than ever before.
Shifting to a proactive exposure management strategy is a game-changer for any security program, but it’s not always a straight path. Many teams run into similar roadblocks when they start, from tracking a sprawling digital footprint to dealing with an overwhelming number of security alerts. The good news is that these challenges are well-understood, and with the right approach and tools, they are entirely solvable.
The goal isn’t just to find every single weakness but to build a sustainable program that helps you manage risk effectively over the long term. This means finding ways to work smarter, not just harder. Let’s walk through some of the most common hurdles security teams face in exposure management and discuss practical ways to clear them. By anticipating these issues, you can build a more resilient and efficient process from the ground up.
Your organization’s digital footprint is likely much larger than you think, and it’s growing every day. With the rise of cloud services, remote work, and connected devices, your attack surface is a moving target. Manually tracking every server, application, and user account is simply impossible. This is where assets fall through the cracks, creating shadow IT and unknown risks that attackers can exploit.
The solution is to implement a continuous attack surface management process. Instead of relying on periodic scans, a modern exposure management program uses ASM to constantly discover and inventory all your internet-facing assets. This gives you a complete, up-to-date map of your entire environment, ensuring you have full visibility into your exposure at all times.
If your security team feels like they’re drowning in alerts, they’re not alone. Many security tools generate a high volume of notifications, and it’s difficult to tell which ones represent a genuine, urgent threat. This constant noise leads to alert fatigue, where critical issues can be overlooked because your team is too busy chasing down false positives. With limited time and staff, you can’t afford to waste effort on low-impact vulnerabilities.
This is why intelligent vulnerability and threat prioritization is so crucial. An effective exposure management platform moves beyond basic severity scores. It enriches vulnerability data with real-world threat intelligence to show you which weaknesses are actively being exploited in the wild. This context allows your team to immediately focus on patching the holes that attackers are targeting right now.
Attackers don’t stand still. They are constantly developing new techniques and finding creative ways to bypass security controls. A defensive strategy that was effective last year might be obsolete today. Relying on outdated information or static security rules leaves your organization vulnerable to emerging threats that you haven’t prepared for. Staying ahead requires a dynamic approach that adapts as quickly as the threat landscape changes.
To counter this, you need to integrate timely and relevant threat intelligence into your daily operations. This goes beyond just knowing about new vulnerabilities. You need actionable insights into the latest attacker tactics, techniques, and procedures (TTPs). By leveraging a steady stream of Threat Advisories, your team can understand how new attacks work and proactively adjust your defenses to protect against them.
Most security teams use a variety of tools for different functions, from endpoint detection to cloud security. The problem is that these tools rarely communicate with each other, creating information silos. When your data is scattered across multiple dashboards, you can’t get a unified view of your overall risk posture. This fragmentation leads to visibility gaps, inefficient workflows, and a slower response when an incident does occur.
A Continuous Threat Exposure Management (CTEM) platform solves this by acting as a central hub for your security ecosystem. By integrating with your existing tools, a platform like Hive Pro’s Uni5 Xposure consolidates all your security data into a single, correlated view. This breaks down silos and provides a comprehensive picture of your exposure, allowing your team to manage risk more efficiently and effectively.
You can’t improve what you don’t measure. Shifting to an exposure management mindset is a great first step, but tracking your progress with clear metrics is what turns good intentions into a solid security strategy. It’s how you prove the value of your efforts and show your team is effectively reducing risk across the organization. Instead of guessing if your security posture is improving, you can point to hard data.
These metrics help you answer critical questions: Are we finding threats faster? Are we fixing the most critical issues quickly? Is our attack surface shrinking? Are our security tools actually working? By focusing on these key performance indicators, you can fine-tune your program, justify investments, and build a more resilient defense against threats.
You can’t fix a problem you don’t know you have. That’s why Mean Time to Identify (MTTI) and Mean Time to Detect (MTTD) are so important. These metrics track the average time it takes your team to become aware of a security incident from the moment it occurs. A lower MTTI/MTTD means your security tools and teams are working efficiently to spot potential threats before they can cause significant damage. Tracking this helps you understand the visibility you have across your environment and highlights gaps in your monitoring. It’s a direct measure of your team’s ability to see what’s happening and kick off an effective incident response plan.
Once you’ve found a vulnerability, how long does it take to fix it? That’s what Mean Time to Remediation (MTTR) tells you. This is one of the most vital metrics for showing the effectiveness of your vulnerability management process. A consistently low MTTR shows that your team can move from discovery to resolution efficiently, closing security gaps before they can be exploited. Improving your MTTR often starts with better prioritization—knowing which vulnerabilities pose a genuine threat versus which are just noise. A strong vulnerability and threat prioritization process ensures your team spends its time on fixes that truly reduce risk, which naturally shortens remediation timelines.
A core goal of exposure management is to shrink your attack surface. This metric is straightforward: you’re tracking the overall reduction in the number of exposed assets, open ports, and exploitable vulnerabilities over time. By continuously discovering and assessing your assets, you can identify and eliminate unnecessary points of entry for attackers. This proactive approach strengthens your security posture by making your organization a harder target. Regularly reporting on attack surface reduction provides a clear, tangible measure of how your exposure management program is making the business safer. It’s a powerful way to demonstrate progress and show that you’re not just patching vulnerabilities but actively reducing your overall risk profile.
Having security controls in place is one thing; knowing they work is another. Security control validation rates measure how effective your defenses are against real-world threats and tactics. This involves regularly testing your controls—like firewalls, endpoint detection, and email security—to ensure they perform as expected. Using tools for adversarial exposure validation allows you to simulate attacks safely and see where your defenses hold up and where they fail. Consistently validating your controls helps you confirm they are configured correctly, reduces false positives, and gives you confidence that your security investments are providing real protection. It’s about moving from assuming you’re secure to proving it.
Putting a successful exposure management program into practice isn’t just about changing your mindset; it’s also about having the right technology to back you up. The goal is to move away from juggling spreadsheets and siloed data toward a unified, automated, and intelligent approach. The right tools give you the visibility to see your entire attack surface, the context to understand your biggest risks, and the streamlined workflows to fix them quickly. Without a centralized platform, security teams are often stuck reacting to alerts from disconnected systems, making it nearly impossible to see the bigger picture of their organization’s risk. This is where a dedicated suite of tools becomes a game-changer. A comprehensive platform like Hive Pro’s Uni5 Xposure brings these capabilities together, providing a central hub for your entire threat exposure management lifecycle. Think of these tools as the engine that powers your strategy, turning plans into concrete, protective actions that demonstrably reduce your attack surface and keep you ahead of potential threats.
A Continuous Threat Exposure Management (CTEM) platform is the cornerstone of a modern security program. Unlike traditional tools that perform periodic scans, a CTEM platform offers a persistent, ongoing view of your security posture. It’s a framework designed to help you continuously discover, prioritize, and validate your remediation efforts. These platforms pull data from across your environment to give you a single, coherent picture of your risk. This allows you to move beyond a reactive cycle of patching and instead proactively reduce your most critical exposures before they can be exploited by attackers. It’s about creating a sustainable, repeatable process for managing risk across your entire organization.
You can’t protect what you don’t know you have. That’s where Attack Surface Management (ASM) solutions come in. ASM tools go beyond traditional vulnerability scanning to provide a holistic view of your entire digital footprint from an attacker’s perspective. They continuously scan for and identify all your internet-facing assets, including forgotten servers, shadow IT, and misconfigured cloud services. This gives you a complete inventory of your potential entry points. By combining this external view with internal vulnerability data, you can get a much clearer understanding of your organization’s total attack surface and close the gaps that attackers love to find.
In a world of ever-expanding vulnerabilities, sorting through the noise is one of the biggest challenges for security teams. This is where AI and machine learning become essential. These technologies can analyze vast amounts of data—including threat intelligence feeds, asset criticality, and historical attack patterns—to identify the weaknesses an attacker is most likely to target. Instead of relying solely on static severity scores, AI-driven vulnerability and threat prioritization helps you focus your limited resources on the handful of issues that pose a genuine, immediate threat to your business. This intelligent approach ensures your team is always working on what matters most.
Your exposure management platform shouldn’t be another data silo. To be truly effective, it needs to integrate seamlessly with the security tools you already use every day. This includes your vulnerability scanners, cloud security platforms, ticketing systems, and SIEMs. Strong integrations create a unified workflow, allowing information to flow freely from discovery to remediation. When your tools can communicate, you can automate processes like ticket creation and verification, which frees up your team to focus on more strategic work. This connected ecosystem is key to building an efficient and responsive security control validation process that strengthens your entire security posture.
Transitioning to an exposure management model doesn’t have to be an overhaul of your entire security operation overnight. It’s a strategic shift you can approach in clear, manageable stages. By starting with a solid foundation and building a continuous cycle, you can move your team from a reactive stance to a proactive one, focusing your efforts where they’ll have the most impact. The goal is to create a sustainable program that matures with your organization and adapts to the ever-changing threat landscape. Here’s how you can begin.
Before you can chart a new course, you need to know your starting point. The first step is to get a comprehensive and honest look at your current security posture. This means going beyond simple vulnerability scans to truly understand your organization’s attack surface. You need to identify all your digital assets—from servers and endpoints to cloud services and applications—and assess the vulnerabilities associated with them. This initial assessment provides a baseline, helping you map your entire attack surface and see your organization through the eyes of an attacker. It’s a critical discovery phase that informs every subsequent step of your exposure management program.
Once you have a clear picture of your current state, you can start building a formal program. This isn’t just about buying a new tool; it’s about creating a framework for making smarter, data-driven security decisions. An effective exposure management program consolidates data from various security tools into a single, unified view. This allows you to prioritize threats based on business context, not just technical severity scores. By establishing clear processes and responsibilities, your program will help your team cut through the noise, focus on the most critical risks, and streamline your security operations for better efficiency and faster response.
Exposure management is not a one-and-done project—it’s a continuous cycle. The threat landscape is always changing, and so is your attack surface. That’s why the final step is to establish a process for ongoing improvement. This involves implementing a framework like Continuous Threat Exposure Management (CTEM), which guides your team through a recurring loop of scoping, discovery, prioritization, validation, and mobilization. A key part of this process is integrating threat intelligence to inform your decisions. By continuously correlating data and tracking trends, you can prioritize vulnerabilities that pose an immediate threat, ensuring your security posture remains strong and resilient over time.
My team is already swamped with vulnerability alerts. How does exposure management help with that instead of just adding more to our plate? This is a common concern, but exposure management is designed to solve that exact problem. Instead of adding more work, it helps you filter the noise. It shifts the focus from an endless list of potential issues to the handful of weaknesses that pose a genuine, immediate threat to your business. By using threat intelligence and business context, you can confidently ignore the low-risk alerts and direct all your team’s energy toward fixing the vulnerabilities that attackers are actually exploiting right now. It’s about working smarter, not harder.
Is this just about prioritizing vulnerabilities with higher CVSS scores? Not at all. While CVSS scores are a useful starting point, they don’t tell the whole story. A “critical” vulnerability on an isolated, non-essential server is far less risky than a “medium” one on your main customer database. Exposure management adds the crucial layers of context that CVSS scores lack. It answers questions like: Is this asset critical to our business? Is there an active exploit for this vulnerability in the wild? Could this weakness be chained with others to create a path to our sensitive data? This approach helps you prioritize based on actual business risk, not just a generic severity rating.
What’s the real difference between validating a risk and just patching it? Patching is the act of fixing a known weakness, which is always an important step. Validation, however, is the process of confirming that a weakness is actually exploitable in your specific environment. Think of it this way: a vulnerability scan might tell you a window is unlocked, but a validation test (like a Breach and Attack Simulation) tries to open that window to see if it leads anywhere important. This step proves the risk is real and helps you prioritize the fixes that shut down confirmed attack paths, ensuring your team isn’t wasting time on theoretical threats.
Do I need to rip and replace my current security tools to adopt exposure management? Definitely not. A strong exposure management program doesn’t replace your existing tools—it makes them work better together. The goal is to integrate your current security stack, including vulnerability scanners, cloud security tools, and SIEMs, into a single, unified platform. This breaks down the data silos between different tools and gives you a comprehensive, correlated view of your risk. It’s about enhancing the investments you’ve already made, not starting from scratch.
What’s the single most important first step to get started if our resources are limited? If you can only do one thing to start, focus on visibility. You can’t protect what you don’t know you have. The most critical first step is to get a complete and continuous inventory of your entire attack surface, especially all of your internet-facing assets. This initial discovery process gives you the foundational map you need to understand your potential exposure. Once you know what you have, you can begin to effectively prioritize and protect it.