Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Relying on periodic security scans is like checking your rearview mirror once every ten miles on a busy highway. You get a snapshot of what’s behind you, but you miss the real-time dangers closing in. This reactive approach leaves dangerous gaps for attackers to exploit, keeping your security team in a constant state of catch-up. Shifting to a continuous threat monitoring (CTM) strategy changes the game entirely. It provides a live, always-on view of your entire digital environment, moving you from reacting to yesterday’s problems to proactively identifying and neutralizing threats as they emerge. This guide will walk you through how to build a CTM program that gives you constant visibility and control.
Continuous Threat Monitoring (CTM) is a security strategy that involves constantly keeping an eye on your entire digital environment to spot and handle threats in real time. Think of it as a 24/7 security watch, but for your networks, systems, and applications. The main goal is to catch security issues as they happen—or even before—so you can address them before they turn into full-blown crises. In a world where new cyber threats pop up daily, waiting for a problem to announce itself is no longer a viable option. CTM gives your security team the ability to be proactive, continuously scanning for anomalies and potential attacks across your entire attack surface.
This isn’t about running a scan once a week and hoping for the best. It’s an active, ongoing process. By continuously collecting and analyzing data from every corner of your IT infrastructure, you can identify suspicious patterns and potential vulnerabilities that might otherwise go unnoticed. This allows you to move from a reactive stance, where you’re always playing catch-up, to a proactive one. A solid Threat Exposure Management Platform is the foundation for this approach, helping you confidently manage your security posture instead of just reacting to incidents.
Effective Continuous Threat Monitoring isn’t magic; it’s built on a stack of powerful technologies working together. Tools like Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Network Traffic Analysis (NTA) are the workhorses of CTM. They act as your eyes and ears, automatically gathering and correlating data from your servers, laptops, cloud services, and network devices. This creates a unified stream of information that gives your security team the visibility needed to see what’s really happening across your total attack surface and respond to potential threats with speed and precision.
The biggest shift with Continuous Threat Monitoring is moving from a reactive to a proactive mindset. Traditional security models often function like a fire department—they respond after the alarm has been pulled. They rely on periodic scans and react to alerts once a breach has already occurred. CTM, on the other hand, is more like a smoke detector that also patrols for arsonists. It focuses on identifying suspicious behavior and potential threats before they can do any real damage. This real-time detection allows your team to neutralize threats as they emerge, drastically reducing the likelihood and impact of a successful attack.
Continuous Threat Monitoring (CTM) isn’t a single product you install and forget; it’s a dynamic, cyclical process that gives you a live view of your security landscape. Think of it as your organization’s security heartbeat monitor. It works by constantly gathering information from across your entire digital environment, analyzing it for signs of trouble, and integrating with your other tools to create a unified defense. This approach moves you away from periodic, snapshot-in-time security checks and toward a state of constant awareness.
The core idea is to see everything as it happens. Instead of waiting for a quarterly penetration test to tell you where you’re vulnerable, CTM provides a steady stream of insights. This process involves three key stages that work in a continuous loop: collecting and analyzing data in real time, automating threat detection to keep up with the volume of information, and integrating with your existing security stack to make the data actionable. By implementing a platform like Uni5 Xposure, you can orchestrate this entire process from a single place, ensuring no threat goes unnoticed. This constant vigilance is what allows security teams to spot and stop attacks before they can cause significant damage.
The foundation of any CTM program is its ability to pull in and make sense of data from every corner of your IT environment. This is an ongoing, real-time process of collecting information from your networks, endpoints, cloud instances, applications, and user activities. The goal is to create a comprehensive picture of what “normal” looks like so you can instantly spot deviations that might signal a threat. This data includes everything from system logs and network traffic patterns to configuration changes and access records. By continuously analyzing this information, you can detect potential issues as they emerge, rather than discovering them weeks or months later during a forensic investigation. This is a core part of total attack surface management, ensuring you have visibility across all your assets.
With data flowing in from countless sources, manually sifting through it all for threats is simply impossible. This is where automation becomes your best friend. CTM platforms use sophisticated tools and techniques—like correlation rules, machine learning algorithms, and user behavior analytics—to automatically identify suspicious patterns and potential threats. For example, an automated system can flag an employee logging in from an unusual location at an odd hour or detect a server communicating with a known malicious IP address. This automation allows your security team to focus on investigating and responding to credible threats instead of getting lost in a sea of raw data. It’s the engine that powers effective vulnerability and threat prioritization, helping you focus on what matters most.
CTM doesn’t replace your existing security tools; it makes them smarter and more effective. A strong CTM strategy involves integrating with your entire security ecosystem, including your Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Security Orchestration, Automation, and Response (SOAR) platforms. This integration creates a powerful feedback loop. For instance, when your CTM system detects a threat, it can automatically send that information to your SIEM for deeper analysis, trigger an EDR agent to isolate a compromised endpoint, or kick off a response playbook in your SOAR. This creates a cohesive defense where your tools work together, sharing context and enabling a faster, more coordinated response to incidents.
Shifting from periodic security scans to a continuous monitoring model is one of the most impactful changes you can make to your security program. Instead of getting a snapshot in time, you gain a live feed of your security posture, allowing you to see and act on threats as they emerge. This proactive approach doesn’t just make your team more efficient; it fundamentally changes how you manage risk. By implementing a Continuous Threat Exposure Management (CTEM) program, you can move from a reactive state of defense to a confident, proactive one. The benefits ripple across your entire security operations, from faster detection to stronger compliance.
The biggest advantage of continuous threat monitoring is speed. Traditional security methods often rely on scheduled scans, which can leave dangerous gaps of time for attackers to exploit. Continuous monitoring closes these windows by providing an ongoing, real-time process for collecting and analyzing data across your entire IT environment. This means your team can spot anomalies, misconfigurations, and potential threats the moment they happen, not hours or days later. By identifying vulnerabilities as they appear, you drastically reduce an attacker’s dwell time and stop potential breaches before they can escalate into major incidents.
Continuous monitoring gives you a clear, up-to-the-minute view of your cyber risk. This real-time visibility allows you to assess your security posture constantly, helping your team find and fix security gaps before they become critical vulnerabilities. This isn’t just good security practice; it’s also essential for meeting regulatory requirements. Many compliance frameworks, such as PCI DSS and HIPAA, mandate continuous monitoring. By automating the process of checking your controls and configurations, you can more easily demonstrate compliance and make audit cycles much smoother. It turns compliance from a periodic scramble into a consistent, manageable process.
When you detect threats faster, you can respond faster. Continuous monitoring tools work by automatically collecting and analyzing data, feeding your security team high-fidelity alerts through dashboards and integrations. This means your team isn’t just getting more data; they’re getting better, more contextual information to act on. This allows them to quickly investigate potential threats and initiate an effective response. A faster, more informed response is critical for containing a threat and minimizing its impact, reducing the potential for data loss, financial damage, and harm to your reputation.
Adopting a continuous threat monitoring (CTM) program is a major step forward for any security team, but it’s not without its hurdles. Simply flipping a switch on a new tool won’t solve all your problems. Like any significant operational shift, implementing CTM requires careful planning and an honest look at your resources, processes, and existing technology.
Many teams run into similar roadblocks when getting started. They might struggle with the sheer volume of data, find it difficult to integrate new tools with their current stack, or realize they don’t have the in-house expertise to manage the system effectively. Recognizing these potential challenges ahead of time is the best way to create a strategy that sets your team up for success from day one. Let’s walk through some of the most common issues and how you can prepare for them.
CTM platforms are powerful, but they’re not magic. They generate a massive amount of data that needs to be interpreted, contextualized, and acted upon. This requires skilled security analysts who can connect the dots between a low-level alert and a potential business-wide threat. Without the right people to manage and analyze the output, even the most advanced CTM tool becomes little more than a source of noise.
The ongoing cybersecurity skills gap makes finding and retaining this talent a significant challenge for many organizations. Building a successful CTM program means investing not only in technology but also in your team. This could involve training current staff, hiring specialists, or partnering with a service that provides the necessary expertise to turn raw security data into actionable intelligence.
One of the first things teams notice after implementing a CTM solution is the firehose of alerts. While it’s great to have visibility into every potential issue, the sheer volume can quickly become overwhelming. This phenomenon, known as alert fatigue, is a serious problem. When your analysts are bombarded with hundreds or thousands of low-priority notifications every day, they can become desensitized, making it easier to miss the critical alerts that signal a real attack.
The key to overcoming this is effective prioritization. A good CTM strategy doesn’t just flag every anomaly; it helps you understand which threats pose the most immediate risk. By using a platform that offers advanced vulnerability and threat prioritization, you can filter out the noise and focus your team’s limited time and attention on the issues that truly matter.
Your security is only as strong as its weakest link, and blind spots are an attacker’s best friend. A common challenge in CTM implementation is ensuring complete coverage across your entire digital environment—from on-prem servers and cloud instances to employee laptops and IoT devices. If your monitoring solution only sees part of the picture, you’re left with dangerous gaps that attackers can exploit.
Furthermore, a CTM tool can’t operate in a silo. It needs to integrate smoothly with your existing security stack, including your SIEM, SOAR, and ticketing systems. Without proper integration, you create more work for your team, forcing them to manually correlate data across different dashboards. A truly effective program provides a unified view of your total attack surface, pulling everything together to give you a single, coherent picture of your risk posture.
Continuous threat monitoring is fantastic at telling you what’s happening across your attack surface, but it can’t always tell you why it matters. That’s where threat intelligence comes in. Think of it as the expert analysis layer that transforms raw data into actionable insight. Instead of just seeing a potential vulnerability or an odd network connection, you get the full story: who is exploiting this, how are they doing it, and are they targeting companies like yours?
Integrating a steady stream of high-fidelity threat intelligence helps your security team make smarter, faster decisions. It shifts your posture from purely reactive to proactive, allowing you to anticipate attacker moves instead of just cleaning up after them. By understanding the global threat landscape, you can fine-tune your monitoring tools to look for the right indicators of compromise. This intelligence, often curated by research teams like HiveForce Labs, provides the context needed to separate real threats from the everyday noise of a busy network.
If you’ve ever stared at a list of thousands of vulnerabilities, you know the feeling of being overwhelmed. Traditional scoring systems like CVSS are a good starting point, but they don’t tell you which flaws are actually being used in attacks right now. Threat intelligence cuts through that ambiguity by highlighting vulnerabilities with known exploits in the wild.
This real-world data allows you to move beyond theoretical risk and focus on immediate threats. You can confidently direct your team’s limited time and resources to patching the holes that attackers are actively targeting. This approach is the core of effective vulnerability and threat prioritization, ensuring you’re fixing the most critical issues first and measurably reducing your exposure.
Effective defense requires understanding your opponent. Threat intelligence gives you a direct line of sight into attacker tactics, techniques, and procedures (TTPs). It helps you understand what motivates different threat actor groups, what tools they use, and how they typically move through a network once they gain a foothold. This isn’t just interesting trivia; it’s critical information for configuring your defenses.
By learning how attackers operate, you can better tune your SIEM rules, EDR policies, and other security controls to detect their specific behaviors. You can read up on the latest campaigns in detailed threat advisories and use that knowledge to build more resilient systems. This proactive mindset helps you anticipate an attacker’s next move and strengthen the exact controls they’re likely to test.
One of the biggest challenges with continuous monitoring is alert fatigue. When your team is bombarded with hundreds or thousands of alerts a day, it’s easy for a critical one to slip through the cracks. Threat intelligence acts as a powerful filter, enriching your security alerts with the context needed to determine their true severity.
An alert about an unusual outbound connection is one thing. An alert showing that same connection is communicating with an IP address known to be a command-and-control server for a ransomware group is another entirely. This enrichment allows your security operations team to instantly triage events, escalate genuine threats, and dismiss false positives with confidence. It makes your entire security stack smarter and your response efforts far more efficient.
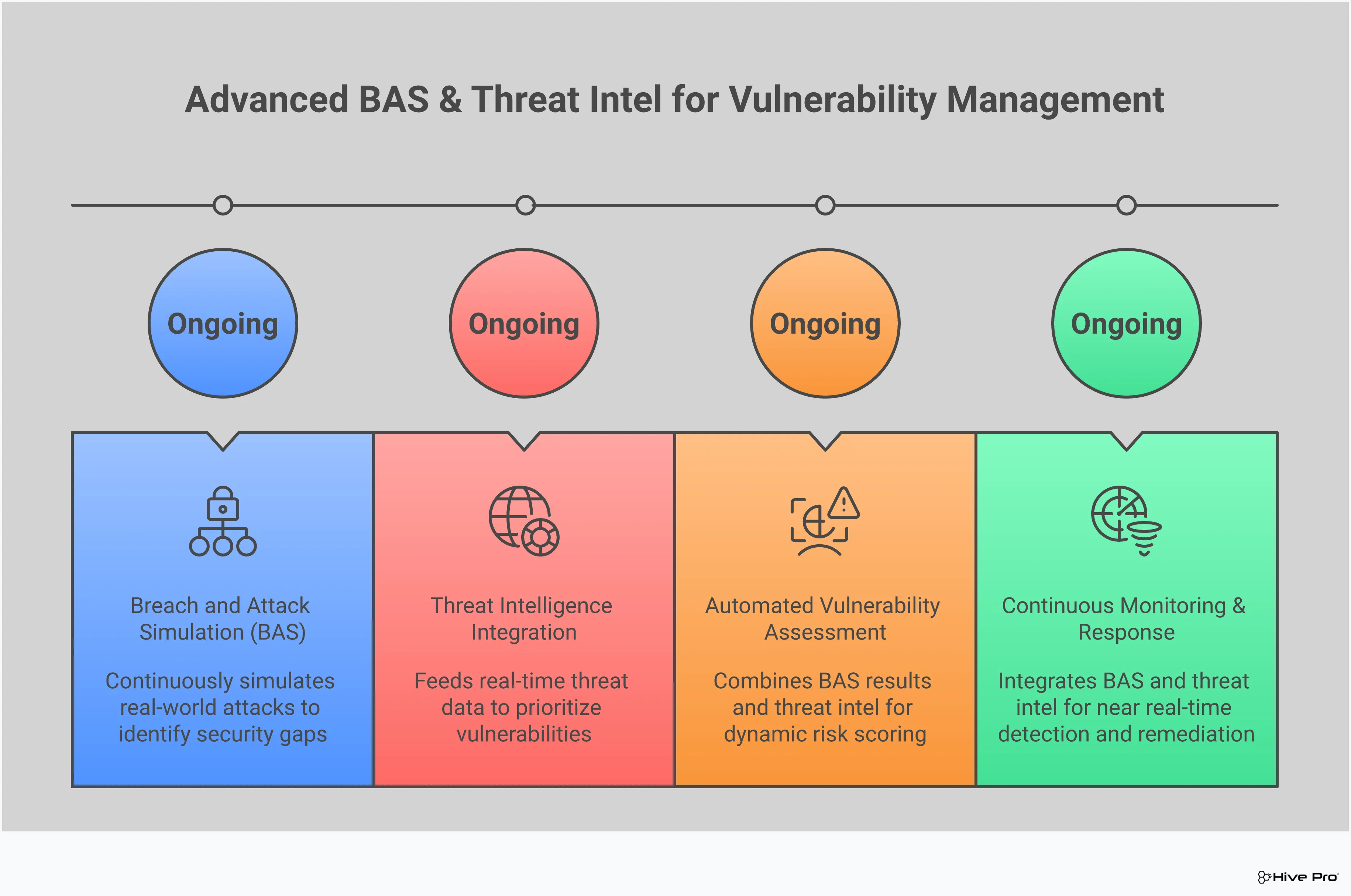
Continuous threat monitoring is more than just watching alerts roll in. To truly understand your security posture, you have to actively test it. That’s where Breach and Attack Simulation (BAS) comes into play. Think of it as a continuous, automated sparring partner for your security defenses. Instead of waiting for a real attacker to show you where you’re weak, BAS platforms safely launch simulated attacks based on the latest real-world threats and techniques.
This proactive approach lets you see exactly how your security controls—from firewalls and endpoint detection to your SIEM—perform against specific attack scenarios. It moves you from a state of hoping your defenses will work to knowing where they will and where they won’t. By integrating BAS into your CTM strategy, you can continuously validate your security stack, train your team, and find gaps before an adversary does. It’s a fundamental part of a modern adversarial exposure validation program, turning assumptions about your security into hard data you can act on.
You’ve invested heavily in a suite of security tools, but how can you be sure they’re configured correctly and doing their job? Breach and Attack Simulation tools give you the answer by allowing you to continuously test your security controls and validate their effectiveness against real-world attack scenarios. A BAS platform can simulate thousands of attacker behaviors, from initial access attempts using phishing links to lateral movement and data exfiltration.
This process provides concrete evidence of your security performance. For example, a simulation might show that your web application firewall successfully blocks an SQL injection attempt but fails to stop a cross-site scripting attack. This kind of specific, actionable insight allows you to fine-tune configurations, update policies, and justify security investments with clear data.
An incident response plan that only exists in a document is just a theory. BAS gives you a safe environment to put that theory into practice. By simulating various attack vectors, BAS can help you assess the effectiveness of your incident response playbooks and ensure your team is prepared for an actual breach. When a simulated attack is launched, it should trigger the same alerts and processes as a real one, forcing your team to go through the motions.
This is your chance to see how your team performs under pressure. Do they know who to contact? Are the right people getting the alerts? Can they quickly identify the scope of the simulated breach and take the correct steps to contain it? Running these drills regularly helps identify communication gaps and process bottlenecks, allowing you to refine your playbooks and build the muscle memory needed to respond effectively when it counts.
You can’t stop an attack you can’t see. One of the most critical functions of BAS is identifying gaps in your monitoring and visibility. An attacker’s goal is to operate in the shadows, and blind spots across your network, cloud environments, and endpoints are the perfect places for them to hide. By using BAS, you can systematically identify gaps in your monitoring capabilities, ensuring no potential attack vectors are overlooked.
For instance, a BAS simulation might reveal that lateral movement between two critical servers in your data center doesn’t generate a single alert. Or perhaps a simulated data exfiltration attempt from a cloud storage bucket goes completely unnoticed. These findings are invaluable. They point you directly to where you need to improve logging, adjust alert rules, or deploy new monitoring tools, helping you achieve the comprehensive visibility needed for a strong security posture.
Implementing a continuous threat monitoring program is more than just deploying new software; it’s about building a strategic framework that supports your security goals. Think of it as creating a living, breathing system that adapts to your environment and the ever-changing threat landscape. A successful CTM strategy doesn’t just generate alerts—it provides the context and clarity your team needs to act decisively. By focusing on a few core practices, you can transform your security operations from a reactive fire drill into a proactive, intelligence-driven function.
The goal is to create a feedback loop where you continuously monitor your environment, validate your defenses, and refine your approach based on what you learn. This moves your team away from chasing endless alerts and toward a state of confident action. These practices will help you establish a solid foundation for your CTM program, ensuring it delivers real value by reducing noise, speeding up response times, and giving you a clear, ongoing picture of your organization’s threat exposure. Let’s walk through the key pillars that hold up a strong CTM strategy.
You can’t spot an intruder in your house if you don’t know what it looks like when everything is in its right place. The same principle applies to your network. Setting a security baseline means defining what “normal” looks like across your entire IT environment. This is the foundational step of any CTM program. It involves mapping out your assets, understanding typical data flows, and establishing acceptable performance thresholds.
This baseline becomes your tripwire. By continuously collecting and analyzing data in real time, your monitoring tools can instantly flag any deviations—like an unusual login time or a spike in outbound traffic—that could signal a threat. Without a clear baseline, you’re just collecting data without context, which quickly leads to a flood of meaningless alerts.
In a security incident, every second counts. Relying on manual processes to respond to threats is a recipe for falling behind. That’s where automation comes in. By creating automated response workflows, you empower your team to handle routine threats instantly while freeing them up to focus on more complex investigations. This could be as simple as automatically creating a trouble ticket and enriching it with threat intelligence, or as decisive as isolating a compromised endpoint from the network.
Automating your controls and responses allows you to assess your cyber risk posture in real time, not hours or days later. This ensures a consistent and speedy reaction to common threats, drastically reducing the potential impact of a breach and making your entire security operation more efficient and effective.
The threat landscape isn’t static, and neither should your CTM program be. Continuous monitoring is a cycle, not a one-time setup. Your program needs regular care and feeding to remain effective. This means continuously assessing your tools, processes, and rules to ensure they are still aligned with your security goals and the current threats you face. Are your alerts providing actionable information, or are they just creating noise? Are there new TTPs you should be monitoring for?
Regularly review your program’s performance, incorporate new threat intelligence, and use techniques like Breach and Attack Simulation to test your defenses and find blind spots. This ongoing optimization ensures your CTM strategy evolves alongside your organization and the adversaries targeting it, keeping you prepared for what’s next.
How is Continuous Threat Monitoring different from just using a SIEM? Think of it this way: a SIEM is a powerful tool, but CTM is the overall strategy. A SIEM is fantastic at collecting and correlating logs from all over your network. CTM is the broader, active process of using that data—along with information from your other tools—to constantly hunt for threats in real time. It’s the difference between having a library of security events and having a security team that reads them, understands the context, and acts on them before a problem escalates.
My team is already drowning in alerts. Won’t CTM just add to the noise? This is a completely valid concern, and it’s a sign that your current tools lack context. A well-designed CTM program actually reduces noise instead of creating more. By integrating high-quality threat intelligence, it enriches raw alerts with crucial information about real-world threats. This helps you automatically filter out the low-risk chatter and prioritize the handful of events that truly require your team’s attention, turning a firehose of alerts into a focused to-do list.
We already perform regular vulnerability scans. Why do we need CTM? Scheduled scans are like taking a photograph—they give you a great snapshot of your vulnerabilities at a specific moment. CTM, on the other hand, is like a live video feed. It provides constant visibility, allowing you to see not just static vulnerabilities but also active misconfigurations and suspicious behaviors as they happen. This closes the dangerous gaps between scans, which is precisely when attackers often make their move.
How do Breach and Attack Simulation (BAS) and threat intelligence work with CTM? They are essential partners that make your CTM program smarter and more effective. Threat intelligence provides the “why,” giving you context on which vulnerabilities are being exploited in the wild and what attacker tactics are trending. BAS then provides the “how,” allowing you to safely and automatically test if your defenses can actually stop those specific attacks. Together, they transform CTM from a passive listening post into an active, self-improving defense system.
What’s the most important first step when starting a CTM program? The most critical first step is to establish a clear baseline of what “normal” looks like in your environment. You can’t spot abnormal activity if you don’t know what’s considered typical for your network, servers, and users. This involves understanding your assets and mapping out standard data flows and user behaviors. This baseline becomes the benchmark against which your CTM tools can accurately identify deviations that might signal an attack.