Comprehensive Threat Exposure Management Platform
You wouldn’t build a fortress without a blueprint. Yet, many organizations approach cybersecurity by simply buying tools—the digital bricks and mortar—without a clear plan for how they all fit together. This leaves gaps in your defenses that attackers are quick to find. A vulnerability management program is the blueprint for your entire security structure. It provides the methodical, repeatable process needed to systematically find, prioritize, and fix weaknesses across your environment. This guide will provide that blueprint, walking you through the essential steps to construct a strong, sustainable program that turns a collection of security tools into a formidable defense.
Think of a vulnerability management program as your organization’s ongoing, strategic plan for finding, evaluating, and fixing security weaknesses across your entire IT environment. It’s not a one-and-done project; it’s a continuous cycle designed to systematically reduce your cyber risk. The main goal is to shift your security posture from a reactive state—where your team is constantly putting out fires—to a proactive one where you identify and neutralize threats before they can be exploited by attackers. This means getting ahead of the problem instead of cleaning up after a breach.
This process provides a structured framework for dealing with the endless stream of new vulnerabilities that surface daily. Instead of getting overwhelmed by a massive backlog, you can methodically address weaknesses, protect your most critical assets, and demonstrate measurable improvements in your security. A modern approach uses a Threat Exposure Management Platform to unify all these moving parts, giving you a single, clear view of your risk landscape. By implementing a formal program, you create a repeatable, defensible process for securing your organization against an ever-changing threat landscape. It’s about building a resilient security foundation rather than just checking boxes on a compliance form.
A strong vulnerability management program is built on five key pillars that work together in a continuous loop. Each component is essential for creating a comprehensive and effective security strategy.
A vulnerability management program isn’t just a best practice—it’s a fundamental requirement for modern security. By proactively finding and fixing weaknesses, you can prevent attackers from gaining a foothold in your network. This proactive stance is far more effective and less costly than responding to a breach after the fact. Beyond preventing attacks, a formal program is often necessary for regulatory compliance, as frameworks like PCI DSS and HIPAA mandate these processes. It also helps you make smarter, risk-based decisions. Instead of trying to patch everything, you can focus your limited resources on the most critical threats. As your organization grows, a structured program is the only sustainable way to handle your total attack surface management and keep your critical assets secure.
A strong vulnerability management program isn’t just a series of one-off tasks; it’s a continuous cycle with distinct, interconnected stages. Think of it as a loop, not a straight line. Each part builds on the last, creating a system that helps you find, prioritize, and fix weaknesses before attackers can exploit them. Getting these core components right is the difference between a reactive, fire-fighting security posture and a proactive, strategic one. Let’s break down the four essential pillars that form the foundation of any effective program.
You can’t protect what you don’t know you have. The first step is always to create a comprehensive inventory of every single asset connected to your network. This includes all your hardware, software, cloud instances, applications, and IoT devices—everything that makes up your digital footprint. This complete inventory is your map. Without it, you’re flying blind, leaving unknown and unmonitored assets exposed. A clear understanding of your total attack surface is the non-negotiable starting point for identifying where your organization might be vulnerable and what you need to protect.
Once you know what’s on your network, the next step is to find the flaws. This involves regularly scanning all your inventoried assets to identify security weaknesses. An effective vulnerability management process uses a combination of tools, including vulnerability scanners, configuration management databases, and patch management systems, to get a full picture of potential exposures. This assessment phase isn’t just about finding CVEs; it’s about understanding the context of each weakness within your specific environment. This systematic detection is what feeds the rest of your program, providing the raw data you need to start making smart security decisions.
Not all vulnerabilities are created equal. A critical vulnerability on a non-essential internal server is less of a concern than a moderate one on your primary, customer-facing application. This is where prioritization becomes crucial. Instead of chasing every single alert, a risk-based approach helps you focus your limited resources on the threats that pose a genuine danger to your business. By enriching vulnerability data with real-world threat intelligence, you can see which weaknesses are actively being exploited in the wild. This allows you to perform effective vulnerability and threat prioritization and tackle the issues that attackers are most likely to target first.
After identifying and prioritizing your vulnerabilities, it’s time to fix them. The remediation phase is where you take action to close the security gaps you’ve found. This might involve applying a patch, changing a configuration, or implementing a workaround. For each prioritized vulnerability, you’ll need a clear plan that outlines the steps for remediation, who is responsible, and a timeline for completion. The goal is to remediate weaknesses efficiently, starting with the most critical risks to systematically reduce your organization’s overall exposure. In some cases, you might mitigate the risk with a compensating control or formally accept it if the cost of fixing it outweighs the danger.
Putting a vulnerability management program into action doesn’t have to be a massive headache. The key is to follow a structured, repeatable process that turns your security strategy from reactive to proactive. Instead of scrambling to patch whatever is making headlines, you’ll have a clear, methodical approach to identifying, prioritizing, and fixing the weaknesses that truly matter to your organization. This four-step framework will help you build a solid foundation for a program that not only finds vulnerabilities but also effectively reduces your overall threat exposure. It’s about creating a continuous cycle of improvement, where each step informs the next. This approach moves you away from a checklist mentality and toward a dynamic strategy that adapts to your changing environment and the evolving threat landscape. By following these steps, you can create a system that is both manageable and highly effective, giving your team the clarity and direction needed to protect your most critical assets with confidence. This isn’t just about compliance; it’s about building genuine resilience against real-world attacks.
You can’t protect what you don’t know you have. The first and most crucial step is to create a comprehensive inventory of every asset connected to your network. This means cataloging all your hardware, software, cloud instances, applications, and connected devices. This complete inventory forms the baseline of your security program and gives you a clear picture of your total attack surface. Think of it as drawing a detailed map of your kingdom before you decide where to place your guards. Without this map, you’re operating with blind spots, leaving doors open for attackers to walk right in. A thorough asset inventory is the foundation upon which all other vulnerability management activities are built.
Once you know what’s on your network, it’s time to find the cracks. This is where vulnerability scanning comes in. Using automated tools, you can regularly check your systems for known weaknesses. These scans are designed to identify issues like unpatched software, system misconfigurations, or outdated protocols that attackers frequently exploit. The goal is to make scanning a continuous, automated process, not a one-off event. This consistent assessment ensures you have an up-to-date view of your security posture. As new vulnerabilities are discovered daily, regular scanning helps you identify weaknesses before an attacker does, giving you a critical head start on remediation.
After scanning, you’ll likely have a long list of vulnerabilities. Trying to fix everything at once is a recipe for burnout and inefficiency. Instead, you need a smart way to prioritize. A risk prioritization framework helps you decide which weaknesses pose the most significant threat to your business. This goes beyond just looking at a CVSS score. You need to consider factors like the asset’s criticality, the likelihood of exploitation, and the potential business impact. By focusing on the most dangerous issues first, you can make the best use of your team’s time and resources. This is where vulnerability and threat prioritization becomes a game-changer, allowing you to focus on what matters most.
Finding and prioritizing vulnerabilities is only half the battle; you also need a solid plan to fix them. A remediation workflow is a systematic process for addressing the weaknesses you’ve identified. This workflow should clearly define roles, responsibilities, and timelines for patching or mitigating each vulnerability. Always start with your highest-priority risks first. Your process should include steps for applying patches, making configuration changes, and verifying that the fix was successful. By creating a clear, repeatable workflow, you ensure that vulnerabilities are addressed efficiently and that nothing falls through the cracks, turning your vulnerability management program into a well-oiled machine.
A raw list of vulnerabilities is more overwhelming than helpful. With thousands of new CVEs published every year, trying to patch everything is a losing battle. The secret to getting ahead is context. Threat intelligence cuts through the noise by telling you which vulnerabilities pose a real, immediate threat to your organization. It’s the difference between chasing every potential issue and strategically dismantling the attack paths that adversaries are most likely to use. This shift in focus is what allows you to move from a reactive posture to a proactive one, using vulnerability and threat prioritization to guide your efforts.
Instead of treating every vulnerability as equally urgent, threat intelligence provides the critical data needed to rank them based on real-world risk. It answers questions like: Is there a public exploit for this? Are threat actors actively using it in campaigns? Does it affect systems that are critical to our business operations? By layering this intelligence over your vulnerability data, you create a clear, actionable roadmap for remediation. This data-driven approach not only strengthens your security posture but also helps you communicate risk more effectively to stakeholders, justifying why certain actions are being taken over others. It transforms vulnerability management from a compliance-driven chore into a strategic security function.
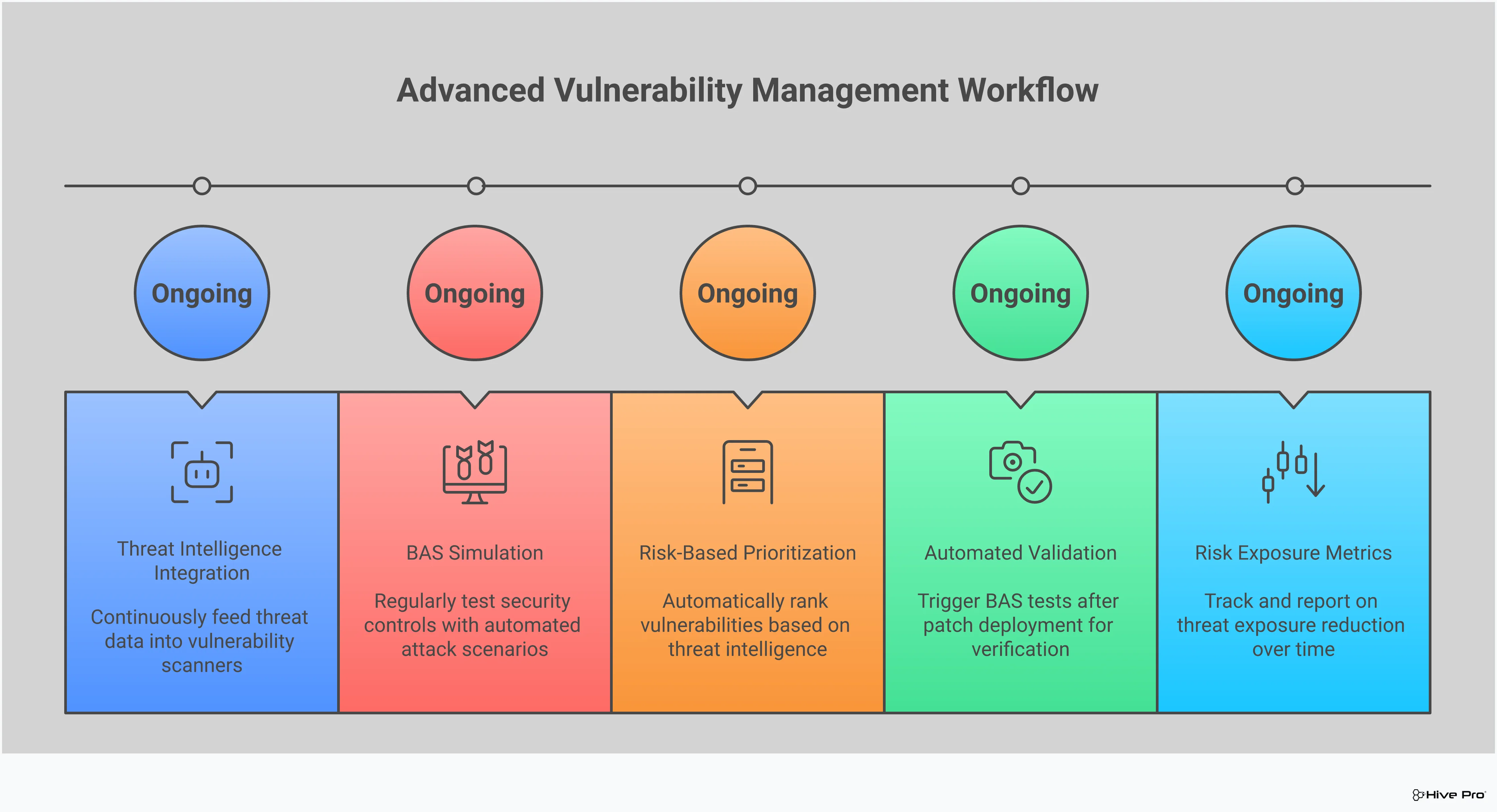
Think of threat intelligence as the “so what?” behind every vulnerability score. A high CVSS score is one thing, but knowing that a specific vulnerability is being actively discussed in underground forums or has a readily available exploit kit changes the game entirely. This real-world data allows you to make smarter, evidence-based decisions. Instead of relying solely on a technical severity rating, you can prioritize based on the actual threat landscape. This approach, informed by dedicated research from teams like HiveForce Labs, helps you allocate your resources effectively and clearly justify your team’s priorities to leadership.
Here’s a fact that might surprise you: only a small fraction of disclosed vulnerabilities are ever actively exploited in the wild. Your team’s time and energy are finite, so why waste them on issues that attackers are ignoring? Threat intelligence helps you zero in on the vulnerabilities that matter most—the ones being used in active campaigns. By concentrating your remediation efforts on these high-risk threats, you can dramatically shrink your attack surface and reduce the window of opportunity for an attacker. This focused approach is a cornerstone of modern threat exposure management and is detailed in regular threat advisories.
To be truly effective, threat intelligence can’t be something you check once a week. It needs to be a living, breathing part of your daily operations. Integrating real-time threat feeds directly into your vulnerability management workflow ensures your team always has the most current context when making decisions. This means that as new threats emerge, your prioritization framework automatically adjusts. A platform that provides this continuous visibility, like the Uni5 Xposure Platform, embeds this intelligence directly into the process, ensuring your team can respond to the latest threats without missing a beat.
A solid vulnerability management program tells you where your weaknesses are. But how do you know if your defenses can actually stop an attack that targets those weaknesses? That’s where Breach and Attack Simulation (BAS) comes in. Think of it as a continuous, automated sparring partner for your security infrastructure. Instead of waiting for a real attack to test your defenses, you can proactively and safely simulate them.
BAS platforms move your security posture from theoretical to practical. A vulnerability scan might tell you a server is missing a patch, but a BAS tool can show you the exact path an attacker could take to exploit that server and move laterally through your network. This approach provides the evidence you need to understand your true exposure. By adding adversarial exposure validation to your program, you stop guessing about your security controls’ effectiveness and start getting real answers. It’s a fundamental shift that helps you confirm your defenses are working as expected and find the gaps before an attacker does.
You’ve invested heavily in firewalls, endpoint detection and response (EDR), and other security tools. But are they configured correctly? Are they actually blocking the threats they’re supposed to? BAS tools help you answer these questions with confidence. They allow you to continuously test your security controls against real-world attack scenarios, giving you clear insights into how they would perform during an actual breach.
Instead of relying on vendor claims or annual penetration tests, you can run simulations of specific malware or ransomware attacks to see if your defenses hold up. This provides you with concrete, actionable data on misconfigurations or gaps in your security stack. It’s the proof you need to fine-tune your tools and demonstrate their value.
Patching a vulnerability is a critical step, but it’s not the final one. How can you be certain the fix was applied correctly and fully closed the security gap? This is where BAS creates a powerful feedback loop for your remediation efforts. After your team deploys a patch, you can run a specific attack simulation that targets the vulnerability you just addressed.
If the simulated attack fails, you have definitive proof that your remediation was successful. If it succeeds, you know immediately that the issue isn’t resolved—perhaps the patch failed on some assets or didn’t fully mitigate the risk. By simulating attacks, you can assess the effectiveness of your remediation efforts, ensuring that your hard work is genuinely reducing your organization’s exposure.
Attackers don’t just exploit a single vulnerability; they often chain together multiple weaknesses to create an attack path to their target. A standard vulnerability scan might not see this bigger picture. BAS helps you identify these critical exposure gaps by mimicking the tactics, techniques, and procedures (TTPs) used by real adversaries. It allows you to see your environment from an attacker’s point of view.
This process uncovers hidden pathways and complex scenarios that could lead to a breach. By understanding how different vulnerabilities could be combined, you can focus your vulnerability and threat prioritization on the issues that pose the most significant threat. It’s about finding and fixing the most critical weaknesses before they become part of a real-world attack chain.
Getting a proactive vulnerability management program off the ground is a significant undertaking, and it’s completely normal to hit a few bumps along the way. Even the most well-thought-out strategies can face hurdles that slow down progress and create frustration. The key is to anticipate these roadblocks so you can prepare for them. From wrangling the right resources to getting everyone on the same page, understanding these common challenges is the first step toward building a program that’s both effective and sustainable.
Most of the issues teams face fall into three main categories: not enough people or the right skills, dealing with complicated and disconnected tech stacks, and making the business case to leadership. Let’s break down what these challenges look like in the real world and how they can impact your efforts. By recognizing them early, you can build a strategy that addresses them head-on instead of letting them derail your program later.
One of the most common refrains in cybersecurity is, “We don’t have enough people.” Many organizations struggle to fix vulnerabilities simply due to conflicting priorities and a lack of resources. Your security team is likely already stretched thin, and adding the operational weight of a full-scale vulnerability management program can feel overwhelming. It’s not just about headcount; it’s also about having team members with the specialized skills needed to operate scanners, analyze data, and coordinate remediation across different departments.
This is a universal issue. Even large enterprises often lack the internal resources to implement effective scanning, prioritization, and remediation processes. When your team is constantly fighting fires, it’s tough to find the time for the proactive, strategic work that a strong program requires. This can lead to burnout and a perpetually reactive security posture.
Today’s IT environments are a mix of on-premise servers, cloud instances, IoT devices, and remote endpoints. This complexity makes it incredibly difficult to get a complete and accurate picture of your attack surface. On top of that, many teams rely on a patchwork of disconnected tools for scanning, asset management, and patching. Trying to implement, optimize, and manage this wide range of technologies creates data silos and forces your team to spend valuable time manually piecing together information.
When your tools don’t talk to each other, you get a fragmented view of your security posture. This makes it nearly impossible to correlate findings, prioritize effectively, and track remediation progress. A unified platform that brings all this information together is essential for cutting through the noise and seeing your true exposure. Without that single source of truth, you’ll always be a step behind.
You can have the best team and tools in the world, but without support from leadership, your program will struggle to succeed. Securing this buy-in requires translating technical risks into tangible business impact—something executives can understand and act on. It’s your job to show them how unpatched vulnerabilities can lead to data breaches, operational downtime, and financial loss. Clear communication and buy-in from these leaders will underpin the program and ensure timely remediation.
Without executive support, getting the budget you need for essential tools and talent is an uphill battle. It also makes enforcing remediation policies much harder, especially when you need cooperation from IT or DevOps teams who have their own priorities. Demonstrating a clear, risk-based approach to vulnerability and threat prioritization can help you make a compelling case, showing that you’re focusing resources on the threats that truly matter to the business.
Building a proactive vulnerability management program requires more than just a scanner. Your tech stack needs to work together to give you a clear, continuous view of your risk. The right tools automate tedious tasks, provide crucial context, and help your team act faster. Instead of juggling disconnected spreadsheets and alerts, a modern stack unifies your efforts, turning data into decisive action. It’s about creating a security ecosystem where each component enhances the others, from discovery and prioritization to remediation and validation. Let’s look at the core technologies that make this possible.
Think of a threat exposure management platform as the central nervous system for your program. These platforms go beyond traditional scanning by integrating asset discovery, vulnerability assessment, threat intelligence, and risk analysis into a single, unified view. Instead of just giving you a long list of CVEs, they help you understand which vulnerabilities pose a genuine threat to your specific environment. By combining these functions, modern platforms like Uni5 Xposure significantly shorten the time attackers have to exploit a weakness. This integrated approach is what separates a reactive, scan-and-patch cycle from a proactive strategy focused on reducing your overall exposure.
You can’t patch what you can’t see, and you can’t patch everything at once. This is where patch management and automation tools come in. These tools are essential for operationalizing your remediation plan. Once your exposure management platform has prioritized a vulnerability, automation kicks in to coordinate the patching process. Good vulnerability management automation tools stay current with emerging threats, helping you deploy patches quickly and efficiently across your entire environment. This not only saves your team countless hours but also ensures that critical fixes are applied consistently, closing security gaps before they can be widely exploited.
Your vulnerability management program shouldn’t operate in a vacuum. Integrating it with your Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms creates a powerful feedback loop. This connection allows you to correlate vulnerability data with real-time threat activity detected by your SIEM. When a potential exploit is detected, a SOAR playbook can automatically query your vulnerability data to check the patch status of the targeted asset. This seamless security ecosystem enables your security operations team to respond with greater speed and context, making your entire security posture more resilient and responsive.
You’re putting in the work to find and fix vulnerabilities, but how do you prove your program is actually making the organization safer? Without the right data, you’re just guessing. Measuring your program’s success isn’t about vanity metrics; it’s about demonstrating tangible risk reduction, justifying your budget, and identifying areas for improvement. When you can show leadership a clear downward trend in critical risks, you’re no longer just a cost center—you’re a strategic business partner.
Tracking key performance indicators (KPIs) helps you tell a compelling story about your team’s effectiveness. It allows you to move beyond simply counting vulnerabilities and start measuring what truly matters: how quickly you close security gaps and how effectively you lower the organization’s overall threat exposure. This data-driven approach is what separates a reactive, check-the-box program from a proactive, continuously improving one. By focusing on the right metrics, you can fine-tune your processes, optimize resource allocation, and build a more resilient security posture.
Think of Mean Time to Remediate (MTTR) as your program’s core speed metric. It measures the average time it takes for your team to fix a vulnerability from the moment it’s discovered. A low MTTR is a strong indicator of an efficient process, showing that you can close security gaps before attackers have a chance to exploit them. This is one of the most critical vulnerability management metrics because it directly reflects your ability to reduce risk swiftly.
However, speed isn’t everything. You also need to track your resolution rate. This metric tells you what percentage of discovered vulnerabilities are actually being remediated within a given timeframe. A high resolution rate proves that your team is not just fast but also thorough, ensuring that critical issues don’t fall through the cracks or get lost in a backlog. Together, MTTR and resolution rates provide a balanced view of both the efficiency and the effectiveness of your remediation efforts.
While speed is important, the ultimate goal is to reduce risk. One of the best ways to measure this is by tracking the overall number of critical and high-severity vulnerabilities in your environment over time. Is that number trending downward? This simple trend line is a powerful visual for demonstrating your program’s impact to stakeholders. It shifts the conversation from “how many vulnerabilities we found” to “how much risk we eliminated.”
Another fundamental metric is patch compliance. Are your systems being patched in a timely manner according to your policies? Tracking patch compliance rates across different asset groups shows how well you’re maintaining basic security hygiene. Effectively communicating these metrics is key to protecting the organization’s assets and showing leadership how your team’s work directly supports broader business objectives. It’s proof that your program is making the entire organization more secure.
Metrics aren’t just for report cards; they’re your roadmap for getting better. By consistently tracking your performance, you can pinpoint bottlenecks in your workflow, evaluate the effectiveness of your security tools, and make a data-backed case for additional resources. For example, if your MTTR for a specific application team is consistently high, it might signal a need for more training or better tools. This focus on data helps you achieve proactive protection.
The goal is to create a feedback loop where you measure, analyze, and refine your processes. A modern Threat Exposure Management Platform can centralize this data, giving you a single dashboard to monitor your program’s health and identify opportunities for optimization. This continuous improvement cycle is what transforms a good vulnerability management program into a great one, ensuring it adapts and matures along with the evolving threat landscape.
Building a vulnerability management program is a great first step, but turning it into a lasting security function requires commitment. It’s not about a single project with a finish line; it’s about creating a sustainable cycle of improvement that protects your organization day in and day out. These practices will help you build a program that stands the test of time and becomes a core part of your security strategy. By focusing on continuous assessment, teamwork, and adaptability, you can move from a reactive stance to a truly proactive one, ready for whatever comes next.
Your security posture isn’t static, and your vulnerability management program shouldn’t be either. New threats pop up constantly, and your own environment changes with every new device, user, and application. That’s why continuous monitoring is essential. Think of it as an ongoing, active process that keeps a constant watch for new weaknesses. A strong program helps you manage risks as your systems grow and become more complex, finding vulnerabilities faster and using data to improve how you fix them. This isn’t about running a scan once a quarter; it’s about integrating continuous threat exposure management into your daily operations to stay ahead of potential threats.
Vulnerability management isn’t just a job for the security team. A truly effective program involves collaboration across multiple departments, including IT, DevOps, and even business leaders. When everyone understands their role in security, you create a much stronger defense. Getting support from top leadership is crucial, as it ensures you have the resources and authority you need. Remember, weaknesses aren’t just in technology; they can be in processes and people, too. By making sure your security, IT, and development teams are working together, you can close gaps faster and build a culture of security that permeates the entire organization.
The threat landscape changes in the blink of an eye. Attackers are always finding new ways to exploit weaknesses, which means your program must be agile enough to keep up. Sticking to old methods, like relying solely on traditional scanners, can leave you with blind spots and a long list of false positives. A modern approach means staying informed about which vulnerabilities are actively being used in the wild. By integrating real-world threat intelligence into your process, you can focus your efforts on fixing the most critical issues first. Regularly reviewing and updating your program ensures it remains effective against the threats you face today, not the ones from last year.
My team is overwhelmed by the number of vulnerabilities we find. Is just focusing on the ones with high CVSS scores enough? That’s a common feeling, and the short answer is no—relying only on CVSS scores isn’t enough. A high score tells you a vulnerability is technically severe, but it doesn’t tell you if anyone is actually exploiting it. By adding threat intelligence to your process, you gain crucial context. This helps you see which weaknesses are being used in active attack campaigns, allowing you to prioritize the vulnerabilities that pose a real, immediate danger to your business instead of just chasing high numbers.
How is Breach and Attack Simulation (BAS) different from a traditional penetration test? Think of it as the difference between an annual physical and a 24/7 heart rate monitor. A penetration test is a point-in-time assessment, usually done once or twice a year, that gives you a snapshot of your defenses. Breach and Attack Simulation, on the other hand, is a continuous and automated process. It constantly runs safe, simulated attacks against your security controls to give you real-time feedback on whether they’re working as expected, helping you find and fix gaps before an attacker can.
This all sounds great, but my organization is starting from scratch. What’s the most important first step? If you’re just starting out, your first and most critical step is to get a complete inventory of all your assets. You simply can’t protect what you don’t know you have. Before you even think about scanning or prioritizing, you need a clear and comprehensive map of every device, application, and cloud instance connected to your network. This complete inventory is the foundation for every other part of your program.
Our IT and DevOps teams see remediation requests as a disruption. How can I get them on board? The key is to shift the conversation from “you need to fix this” to “here’s how this specific risk impacts the systems you manage.” When you can provide clear data showing that a vulnerability is actively being exploited and could lead to a service outage or data breach, it’s no longer just a security task—it’s a shared operational risk. Frame your remediation requests with this business context and work with them to integrate patching into their existing workflows to make the process as smooth as possible.
The post mentions both threat intelligence and BAS. How do they work together in a vulnerability management program? They work together to answer two different but equally important questions. Threat intelligence helps you look outward to see what attackers are doing in the wild, answering the question, “What should we fix first?” It helps you prioritize your efforts on the most relevant threats. BAS helps you look inward to test your own defenses, answering the question, “Can we actually stop that attack?” By using them together, you can prioritize the right vulnerabilities and then validate that your fixes and security controls are truly effective.