Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Running generic security tests is like studying for the wrong exam. You might be prepared for something, but not for the threats you’re most likely to face. To build a truly resilient defense, you need to test your controls against the specific tactics, techniques, and procedures that adversaries are using right now. This is where threat intelligence transforms a Breach and Attack Simulation (BAS) platform from a useful tool into a strategic weapon. By fueling BAS with real-time data on active threat campaigns and exploited vulnerabilities, you can run simulations that are directly relevant to your industry and risk profile, ensuring you’re prepared for probable attacks, not just possible ones.
If you’ve heard the acronym “BAS” thrown around, you might be wondering what it actually means. Like many three-letter acronyms, its definition depends entirely on the context. You could be talking about building management, business software, or, in our world, a critical cybersecurity practice. Let’s clear up the confusion and focus on the meaning that matters most for security teams.
In the cybersecurity field, BAS stands for Breach and Attack Simulation. Think of it as an automated way to continuously test your security defenses. BAS tools are designed to safely simulate the real-world tactics, techniques, and procedures (TTPs) used by attackers. This allows you to see exactly how your security controls—like your firewalls, endpoint detection, and email gateways—would hold up against an actual attack. Instead of waiting for an annual penetration test, you can run these simulations all the time, giving you a constant, clear picture of your security posture and helping you validate your defenses against emerging threats.
Outside of cybersecurity, you’ll often hear BAS used to mean Building Automation System. This is a completely different technology, but it’s a common use of the acronym. A Building Automation System is the centralized network of hardware and software that controls a building’s environment. It manages everything from heating, ventilation, and air conditioning (HVAC) to lighting, access control, and security systems. The goal of a BAS is to improve occupant comfort, operate building systems efficiently, and reduce energy consumption. So, if you’re talking to a facilities manager, they’re probably not thinking about cyberattacks when they mention BAS.
Another definition you might encounter, particularly in IT or business operations, is Business Application Software. In this context, BAS refers to software created to help companies perform specific functions. This is a broad category that includes everything from accounting and inventory management software to customer relationship management (CRM) and project management tools. Essentially, any application that supports a business process can fall under this umbrella. It’s a good example of how the same acronym can have very different meanings depending on which department you’re in.
Just to show how varied acronyms can be, BAS has a few other meanings as well. For instance, in the military, it stands for Basic Allowance for Subsistence, which is a monthly stipend given to service members for food. You might also see it used for a Bachelor of Arts and Sciences degree or even in aviation contexts. The key takeaway is that context is everything. For the rest of our discussion, when we say BAS, we are talking exclusively about Breach and Attack Simulation in cybersecurity.
When we talk about BAS in cybersecurity, we’re referring to Breach and Attack Simulation. Think of BAS tools as a cornerstone of modern security practices. They give you a way to safely and continuously test your defenses against the kinds of attacks you’re likely to face. Instead of waiting for a real incident to find out where your security gaps are, BAS lets you proactively identify vulnerabilities and validate that your security controls are actually working as expected. It’s like having a dedicated red team on staff 24/7, constantly running drills to keep your defenses sharp.
This approach helps organizations shift from a reactive guessing game to a confident, proactive strategy. By simulating real-world attack scenarios, you can see exactly how your security stack—from firewalls to endpoint detection—performs under pressure. This continuous feedback loop is essential for understanding and reducing your overall risk posture. The goal is to find and fix weaknesses before an actual attacker can exploit them, making your entire security program more resilient. With a platform that provides adversarial exposure validation, you can test your controls against the latest threats and ensure your investments are paying off.
At its core, BAS technology works by automating the process of launching simulated cyberattacks against your own environment. An effective BAS tool doesn’t just run a single, generic test; it offers comprehensive coverage across all potential attack vectors, including your network, endpoints, cloud infrastructure, and email gateways. These simulations are run continuously and automatically, providing a constant stream of data on your security performance. The best platforms update their attack simulations with real-time threat intelligence, ensuring you’re testing against the most current and relevant threats. After running a simulation, the tool provides actionable suggestions for mitigation, helping you prioritize fixes and close gaps quickly. Many tools also integrate with frameworks like MITRE ATT&CK to map attack techniques and improve your defensive strategy.
An effective BAS platform is built on a few key components working in synergy. First is the simulation engine, which is the heart of the system responsible for executing the thousands of simulated attacks. This engine needs to be safe, controlled, and capable of mimicking a wide range of attacker behaviors. Second is a robust threat intelligence feed. This component ensures the simulations are not just random tests but are based on real-world threats, active campaigns, and exploited vulnerabilities seen in the wild. Third, you have the control validation module, which assesses whether your existing security tools—like your SIEM, EDR, and firewalls—are configured correctly and are actually detecting and blocking the simulated attacks. Finally, a clear reporting and analytics dashboard ties it all together, translating the raw data into actionable insights and remediation guidance.
It’s helpful to understand how Breach and Attack Simulation differs from traditional penetration testing. While both are designed to find security weaknesses, their approach and frequency are very different. Think of a pen test as a point-in-time assessment—a deep, manual audit that happens maybe once or twice a year. It provides valuable insights but only offers a snapshot of your security posture at that moment. BAS tools, on the other hand, provide continuous testing and validation. Because BAS is automated, it can run thousands of tests on an ongoing basis, giving you a real-time, dynamic view of your security effectiveness. This allows you to catch configuration drifts or new vulnerabilities much faster than you would by waiting for the next annual pen test.
If your vulnerability management program feels like a constant game of whack-a-mole with an endless list of CVEs, you’re not alone. Traditional scanning tells you what could be a problem, but it doesn’t answer the most important questions: Can an attacker actually exploit this weakness in my environment? And are my security controls configured to stop them if they try? This is where Breach and Attack Simulation (BAS) changes the game.
Integrating BAS into your vulnerability management strategy shifts your focus from a theoretical checklist of vulnerabilities to a practical, evidence-based understanding of your true exposure. Instead of just finding weaknesses, BAS actively tests them using safe, controlled attack simulations. It essentially puts on an attacker’s hat to show you exactly how your defenses would hold up against a real threat. This allows you to move beyond guessing which vulnerabilities to fix first and start prioritizing based on which ones pose a clear and present danger to your organization. It’s about validating your security posture, not just scanning it.
You’ve invested heavily in firewalls, EDRs, and other security tools, but how do you know they’re working correctly day-to-day? A misconfiguration, a missed update, or a policy change can create a gap in your defenses without you even realizing it. BAS acts as your automated, 24/7 testing team, continuously running simulations to verify that your security stack is performing as expected. This process of adversarial exposure validation provides ongoing assurance that your controls can actually block the latest attack techniques, giving you real proof that your security investments are delivering value.
BAS doesn’t just test for generic vulnerabilities; it simulates the specific tactics, techniques, and procedures (TTPs) used by actual adversaries. Drawing from threat intelligence frameworks like MITRE ATT&CK, BAS platforms replicate the multi-stage attack chains of real-world threat actors. This allows you to see precisely how a ransomware attack or data breach could unfold in your environment. By running these realistic scenarios, you can identify and close security gaps along the entire attack path, not just at the initial point of entry. This proactive approach is informed by up-to-date threat advisories that detail active campaigns.
Traditional security assessments like penetration testing are essential, but they’re also time-consuming, expensive, and only provide a point-in-time snapshot of your security posture. It’s simply not feasible to run them frequently. BAS automates the security testing process, allowing you to run thousands of attack simulations on a continuous basis across your entire network. This automation provides consistent and scalable testing without overburdening your security team. It frees up your analysts from repetitive manual tasks so they can focus on strategic remediation and improving your overall security posture.
Security teams are drowning in alerts. The sheer volume makes it nearly impossible to distinguish real threats from low-risk notifications, leading to critical alerts being missed. BAS helps cut through the noise by providing context. When a simulated attack is successful, you know there’s a genuine, exploitable pathway that needs immediate attention. This evidence-based approach helps with vulnerability and threat prioritization, allowing your team to focus their efforts on fixing the issues that matter most. By validating which alerts correspond to real risks, you can significantly reduce alert fatigue and improve your team’s response effectiveness.
If your vulnerability management program feels like a constant game of catch-up, you’re not alone. Traditional methods often leave teams reacting to an endless list of vulnerabilities without a clear sense of which ones pose a genuine threat. This is where Breach and Attack Simulation (BAS) changes the game. By actively testing your defenses against simulated real-world threats, BAS helps you move from a reactive stance to a proactive one, fundamentally transforming how you manage and reduce risk. It’s about getting ahead of attackers by thinking like them.
For too long, security teams have been stuck in a reactive cycle: a new vulnerability is disclosed, a patch is released, and the race is on to deploy it before it’s exploited. BAS breaks this pattern by allowing you to continuously test your environment against the kinds of attacks you’re likely to face. Instead of waiting for a vulnerability scanner to tell you you’re exposed, you can proactively simulate attacks to see where your defenses hold up and where they fall short. This approach helps you identify and fix exploitable weaknesses before they become a real-world problem, turning your security program into a forward-thinking operation.
A typical vulnerability scan can generate thousands of alerts, leaving your team to sort through the noise. But not all vulnerabilities are created equal. BAS helps you cut through the clutter by showing you which ones are actually exploitable in your specific environment. By running simulations that mimic attacker techniques, you can validate whether a theoretical vulnerability poses a practical risk. This allows you to focus your team’s time and resources on the threats that matter most, ensuring your vulnerability and threat prioritization efforts have the greatest impact on your security posture.
Attackers don’t just exploit a single vulnerability; they chain them together to create an attack path from the perimeter to your most critical assets. BAS helps you see your organization through an attacker’s eyes by mapping out these potential pathways. By simulating multi-stage attacks, you can understand how an adversary could pivot through your network, escalate privileges, and reach their objective. This insight is crucial for strengthening your defenses at key points and disrupting the attack chain. It moves the focus from patching individual CVEs to securing the entire attack surface against complex threats.
Your digital environment is dynamic, with new assets and applications being added all the time. A point-in-time assessment like a traditional penetration test quickly becomes outdated. BAS provides the automated, continuous validation needed to keep pace with this change. It offers a constant feedback loop on your security controls’ effectiveness, ensuring they are configured correctly and performing as expected. This continuous validation is a cornerstone of a modern Continuous Threat Exposure Management (CTEM) program, helping you maintain a consistent and measurable security posture over time.
A Breach and Attack Simulation (BAS) platform is a powerful tool on its own, but it becomes truly transformative when you fuel it with high-quality threat intelligence. Think of it this way: a standard BAS tool can test your defenses against a wide range of known attack methods, which is great. But a BAS platform powered by threat intelligence tests your defenses against the specific attacks happening right now and targeting organizations just like yours. This intelligence provides the context you need to move beyond generic security testing and answer the questions that really matter.
Instead of just asking, “Are our controls working?” you can ask, “Can our controls stop the latest ransomware strain targeting our industry?” This shift allows you to focus your resources on the threats that pose a genuine, immediate risk to your business. By integrating data on active threat campaigns, exploited vulnerabilities, and attacker TTPs, you can run simulations that are not just realistic, but directly relevant to your security posture today. This approach helps you validate your security controls against probable threats, not just possible ones. It’s the difference between preparing for a hurricane in Kansas versus preparing for one in Florida. Both are technically possible, but only one is a practical use of your time and resources. This targeted approach is a core component of building a proactive Continuous Threat Exposure Management (CTEM) program.
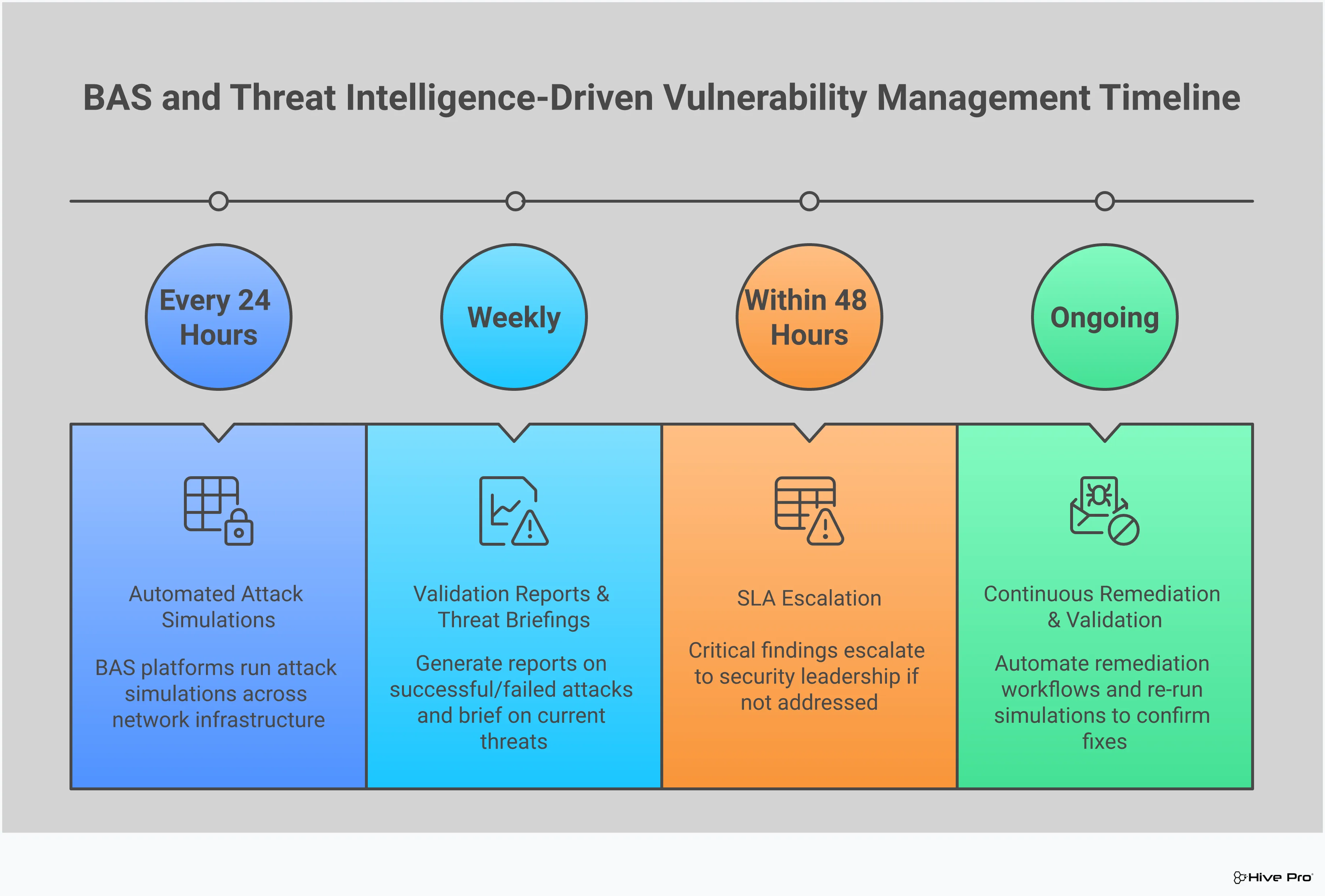
Threat intelligence gives your BAS platform a playbook of real-world attacks. Instead of running generic simulations, you can mimic the exact tactics, techniques, and procedures (TTPs) used by active threat groups. This allows you to see precisely how your defenses would hold up against a specific adversary targeting your industry. For example, you can simulate an attack chain used by a known ransomware group or a phishing campaign that’s currently making the rounds. This level of specificity helps you prepare for the threats you’re most likely to face, turning abstract risks into concrete, testable scenarios. You can find examples of this in regularly published threat advisories.
Your vulnerability scanner probably gives you a list of issues as long as your arm, and not all of them carry the same level of risk. Threat intelligence helps you cut through the noise. By feeding your BAS platform data on which vulnerabilities are actively being exploited in the wild, you can focus your simulations on the security gaps that attackers are actually using to breach networks. This is a critical step in effective vulnerability and threat prioritization. It helps your team stop wasting time on low-risk findings and directs their attention to patching the holes that present a clear and present danger to your organization.
When your BAS simulations are backed by hard data, it’s much easier to get everyone on the same page. Threat intelligence provides a common language for security, IT, and leadership teams to discuss risk. Instead of debating priorities based on abstract scores, you can point to specific, credible threats and show how they could impact the business. This data-driven approach helps you make informed decisions about where to invest your time and budget. It brings different teams together around a unified view of cyber risk, ensuring that everyone is working toward the same goal: defending against the most likely attacks.
The threat landscape changes by the minute, and your security testing needs to keep up. Integrating real-time threat intelligence from sources like HiveForce Labs ensures your BAS platform is always testing against the latest threats. When a new vulnerability is disclosed or a new malware variant appears, your BAS tool can immediately simulate attacks that leverage it. This gives you immediate feedback on your defensive capabilities against emerging threats, closing the gap between when a threat appears and when you know you’re protected against it. This real-time context is essential for maintaining a proactive and resilient security posture.
You can’t secure what you can’t see. Your true attack surface is the complete and constantly changing sum of all points an attacker could use to enter your environment. It’s more than just a list of known vulnerabilities; it includes forgotten assets, misconfigured cloud services, and overlooked digital entry points. A Breach and Attack Simulation (BAS) platform moves beyond simple scanning to provide a clear, attacker-centric view of your entire environment. It helps you understand not just what assets you have, but how they could be compromised. This clarity is the first step toward building a proactive security strategy.
Your organization likely has more assets than you realize. From shadow IT spun up by development teams to legacy servers still running in a forgotten corner of the network, these unknown devices create significant blind spots. BAS tools help you build a comprehensive and accurate asset inventory by actively probing your environment just like an attacker would. This process uncovers everything connected to your network—both known and unknown. Having a complete picture of your total attack surface is foundational. It ensures that every potential entry point is accounted for, so you can start managing the actual risk across your entire organization instead of just the parts you already knew about.
Once you have a full inventory, the next step is to understand how these assets are exposed. A BAS platform doesn’t just find vulnerabilities; it maps the potential attack paths an adversary could take to exploit them. By simulating real-world attack techniques, it shows you exactly how a threat actor could move from one system to another, chaining together minor weaknesses to achieve a major breach. This process of adversarial exposure validation provides critical context that a simple vulnerability scanner can’t. You get a practical map of your digital exposures, showing which security controls are working and where the critical gaps are in your defenses.
Your environment is constantly changing, which means your risk profile is too. New assets come online, configurations are updated, and fresh threats emerge every day. Relying on periodic assessments like annual penetration tests leaves you vulnerable between checks. BAS allows you to assess risk dynamically by continuously testing your defenses against the latest attack scenarios. This ongoing validation gives you a near real-time understanding of your security posture. Instead of working with a static snapshot of risk, you can make informed decisions based on current, actionable data, allowing for more effective vulnerability and threat prioritization that focuses on what truly matters right now.
Effective security isn’t a one-time project; it’s a continuous process. A BAS platform automates the ongoing monitoring of your attack surface, alerting you to new exposures as they appear. Whether it’s a newly deployed application with a weak configuration or a firewall rule change that inadvertently opens a port, continuous monitoring ensures you catch these issues immediately. This approach is a core principle of a Continuous Threat Exposure Management (CTEM) program. By using a unified platform like Uni5 Xposure, you can maintain constant vigilance, adapt quickly to changes, and ensure your security controls remain effective over time, keeping you ahead of potential threats.
Integrating a Breach and Attack Simulation (BAS) platform into your vulnerability management program isn’t just about adding another tool; it’s about fundamentally changing how you approach security. Instead of reacting to threats, you start anticipating them. BAS provides a continuous, automated way to test your defenses against the latest attack techniques, giving you a clear, evidence-based picture of your security posture. This shift allows you to move beyond guesswork and make data-driven decisions that truly reduce your organization’s risk.
The benefits extend across your entire security organization. By automating the validation of security controls, you free up your team to focus on strategic initiatives rather than manual testing. You also gain the ability to prioritize vulnerabilities based on which ones are actually exploitable in your environment, ensuring your resources are directed where they’ll have the most impact. Ultimately, BAS helps you build a more resilient, efficient, and proactive security program.
One of the most significant advantages of BAS is its ability to continuously test and validate your security controls. Traditional vulnerability assessments might tell you where your weaknesses are, but BAS shows you how an attacker could exploit them. By running simulated attacks that mimic real-world adversary tactics, you can proactively identify vulnerabilities and gaps in your defenses before a real attacker does. This constant validation ensures your firewalls, EDR, and other security tools are configured correctly and working as expected. It moves your team from a reactive stance—patching after a breach—to a proactive one, where you are constantly hardening your defenses against emerging threats.
Security teams are often stretched thin, bogged down by a flood of alerts and manual tasks. BAS helps lighten that load by automating the process of security testing. Instead of spending weeks on manual penetration tests, you can run continuous simulations that provide immediate feedback. This automation frees up your analysts to concentrate on higher-value activities like threat hunting and incident response. By reducing false positives and providing clear context around identified risks, BAS allows your team to work smarter, not harder, focusing their energy on addressing the most critical issues without getting lost in the noise.
Not all vulnerabilities are created equal. A BAS platform helps you understand which ones pose a genuine threat to your organization by testing their exploitability. This allows you to move beyond CVSS scores and focus on what truly matters. With clear, evidence-based data on which attack paths are open, you can prioritize remediation efforts and allocate your budget and personnel to the most critical risks. This targeted approach ensures that your resources aren’t wasted on low-priority vulnerabilities, leading to more efficient security operations and a greater return on your security investments.
Demonstrating the effectiveness of your security program to leadership can be a challenge. BAS provides the concrete data you need to show progress and justify security spending. With detailed reporting on security control performance, risk levels over time, and the impact of remediation efforts, you can present clear, measurable outcomes. This data helps you track your security posture improvements and communicate the value of your team’s work in business terms. By using a comprehensive platform, you can gain a unified view of cyber risks and turn security into a quantifiable and strategic part of the business.
One of the most significant advantages of bringing a Breach and Attack Simulation (BAS) platform into your security stack is the power of automation. Security teams are often stretched thin, bogged down by manual processes and an overwhelming number of alerts. BAS helps lighten that load by automating the repetitive, time-consuming tasks involved in security validation, allowing your team to shift their focus from routine checks to strategic defense. Instead of scheduling periodic, point-in-time tests, you can run continuous simulations that provide a constant, real-time pulse on your security posture. This automated approach transforms security from a reactive scramble into a proactive, streamlined operation. By handling the continuous testing and validation, BAS empowers your team to work smarter, not harder, ensuring your defenses are always optimized against the latest threats without causing burnout.
Traditional security testing, like manual penetration tests, gives you a snapshot of your defenses at a single moment. A BAS platform, on the other hand, works like a 24/7 automated red team. It continuously runs simulations of real-world attack tactics and techniques against your security controls. This allows you to proactively identify vulnerabilities and gaps as they emerge, not just during a quarterly assessment. By automating these ongoing assessments, you get a dynamic and up-to-date view of your security effectiveness. This constant validation ensures your firewalls, EDRs, and other controls are configured correctly and performing as expected against the latest threats, all without requiring constant manual intervention from your team.
Finding a weakness is only half the battle; fixing it is what truly matters. Effective BAS tools don’t just tell you what’s broken—they provide clear, actionable guidance on how to fix it. When a simulation successfully bypasses a security control, the platform generates detailed mitigation advice tailored to the specific issue. This guidance can include vendor-specific configuration changes, policy updates, or patching instructions. This automated remediation advice eliminates the guesswork and lengthy research that often follows a security finding. It empowers your security and IT teams to resolve issues quickly and efficiently, drastically reducing the mean time to remediate (MTTR) and closing critical security gaps before they can be exploited.
A BAS platform doesn’t operate in a silo. Its true power in automation is realized through its ability to integrate with your existing security ecosystem. By connecting with your SIEM, SOAR, ticketing systems, and other security controls, BAS can create a powerful, closed-loop workflow. For example, when a BAS simulation identifies a misconfigured firewall rule, it can automatically send an alert to your SIEM, create a ticket in your ITSM platform, and even trigger a SOAR playbook to quarantine an affected device. This level of integration ensures that the insights generated by BAS are fed directly into your established security operations, making your entire security control validation process more cohesive and responsive.
By combining continuous testing, automated remediation guidance, and seamless integrations, BAS fundamentally streamlines your security workflows. It replaces cumbersome manual processes with an efficient, automated cycle of testing, detection, and response. This frees up your analysts from the repetitive work of validating controls, allowing them to concentrate on more complex threat hunting and incident response activities. The detailed reporting also simplifies communication with leadership, providing clear metrics on security posture and risk reduction over time. Ultimately, automating these workflows not only improves your team’s efficiency but also enhances your organization’s overall resilience against cyber threats by ensuring defenses are consistently validated and optimized.
Choosing the right Breach and Attack Simulation (BAS) solution is about more than just ticking boxes on a feature list. You’re looking for a partner in your security strategy—a platform that not only finds weaknesses but also helps you build a stronger, more resilient defense. The best BAS tool for your team will integrate smoothly into your current workflows, provide intelligence that’s actually useful, and scale as your organization grows. As you evaluate your options, think about how each platform will empower your team to move from simply managing vulnerabilities to proactively reducing your overall threat exposure. Focus on solutions that provide clear, actionable guidance and help you prove the value of your security investments to the rest of the business.
A BAS platform shouldn’t be another isolated island of data. To be truly effective, it needs to connect with the security tools you already use every day. Look for a solution with robust API access and pre-built integrations for your SIEM, SOAR, and ticketing systems. When your BAS platform can automatically share findings with your other tools, you create a more cohesive security ecosystem. This allows your team to streamline remediation workflows, enrich alerts with crucial context, and get a unified view of your security posture without constantly switching between different dashboards. The goal is to make security testing a seamless part of your operations, not an additional burden.
A BAS solution is only as good as the intelligence that fuels it. Static, generic attack simulations won’t prepare you for the dynamic threats you face in the real world. Prioritize platforms that are powered by continuous, up-to-date threat intelligence. This means the system should be constantly updated with information on the latest attacker tactics, techniques, and procedures (TTPs). An effective BAS tool will offer comprehensive coverage of attack vectors and map its simulations to industry-standard frameworks like the MITRE ATT&CK framework. This ensures you’re testing your defenses against the most relevant and current threats, not just hypothetical scenarios.
Data is useless without clarity. A top-tier BAS solution will translate complex simulation results into clear, actionable insights through intuitive dashboards and detailed reports. You should be able to quickly understand your security gaps, identify which vulnerabilities pose the greatest risk, and see potential attack paths through your network. Look for reporting features that not only highlight problems but also provide concrete remediation guidance. These analytics are crucial for helping your team prioritize its efforts effectively and for communicating your security posture and progress to leadership in a way that’s easy to understand.
Your business isn’t static, and your security tools shouldn’t be either. As your organization grows—adding new assets, expanding to the cloud, and supporting a remote workforce—your BAS solution must be able to scale with you. Ensure the platform can handle an expanding and evolving attack surface without compromising performance. It should be able to continuously assess a diverse range of assets, from on-prem servers to cloud workloads and web applications. A scalable solution gives you the flexibility to adapt your security testing strategy as your needs change, ensuring you maintain complete visibility and control over your digital exposures.
How is Breach and Attack Simulation different from a penetration test? Think of a penetration test as a deep, manual audit that happens once or twice a year. It gives you a valuable snapshot of your security at that specific moment. A BAS platform, on the other hand, provides continuous, automated testing. It’s like having a security drill running 24/7, constantly checking for new gaps or misconfigurations as your environment changes. Both are useful, but BAS gives you a real-time, dynamic view of your security posture instead of a static, point-in-time report.
Will a BAS platform just add more alerts for my already busy team? That’s a fair question, but the goal of BAS is actually the opposite. It’s designed to reduce noise, not create more of it. Your team is likely already dealing with a flood of alerts from various tools. BAS provides crucial context by showing you which of those alerts correspond to a genuine, exploitable risk in your environment. By validating which vulnerabilities can actually be used in an attack, it helps your team focus on the critical issues that need immediate attention, making their efforts more effective and reducing alert fatigue.
We already use CVSS scores to prioritize. How does BAS improve on that? CVSS scores are a helpful starting point for understanding the theoretical severity of a vulnerability. However, they don’t account for your specific environment. A vulnerability with a “critical” score might be unexploitable because of a security control you have in place. BAS bridges that gap by testing if a vulnerability can actually be exploited within your network. It adds real-world context to the theoretical score, allowing you to prioritize based on proven risk to your organization, not just a generic number.
Is it safe to run these attack simulations in our live production environment? Yes, absolutely. BAS platforms are designed to be safe and non-disruptive. The simulations mimic the techniques and tactics used by attackers without deploying actual malicious payloads or causing any damage to your systems. Think of it as firing blanks instead of live rounds. This allows you to safely test your production defenses in a controlled manner to see how they would perform during a real incident, without introducing any operational risk.
What makes threat intelligence so important for a BAS solution? A BAS platform without good threat intelligence is testing against a generic list of potential attacks. When you power it with real-time threat intelligence, you start testing against the specific attacks that are happening right now and targeting organizations like yours. It ensures your simulations are relevant and timely, focusing on the vulnerabilities actively being exploited in the wild and the tactics used by current threat groups. This intelligence turns your security testing from a general exercise into a strategic defense against your most likely adversaries.