Comprehensive Threat Exposure Management Platform

We can’t patch everything, and not every risk is patchable. Threat exposure management extends beyond vulnerabilities to consider attack vectors not typically classified as vulnerabilities. Let’s evolve together to tackle the right risks and outsmart attackers.
The impact on your vulnerability management team’s performance and efficacy
Across Vulnerability Management Processes
Threat Exposure Risks
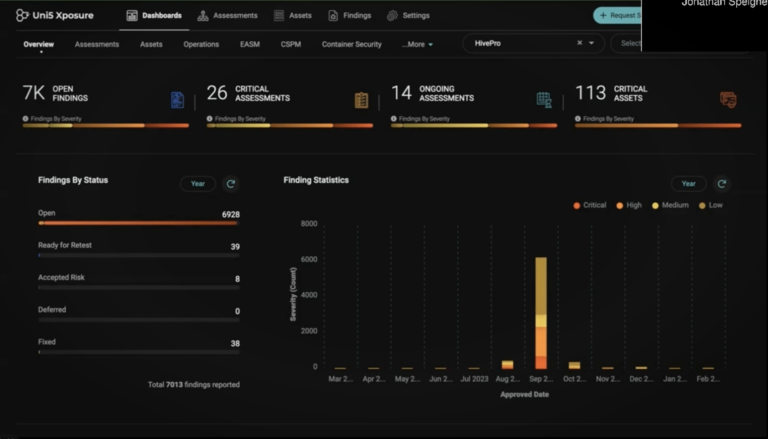
One Sticky Platform For All Tools
What if you could bring all of your scanners, tests, and assessments into one platform from any source? What if you could normalize the output into one risk language and take action fast?
Leverage the power of integrated platforms. Uni5 Xposure works seamlessly with various vulnerability scanners, patch management tools, and ITSM platforms.
View AllMoving from Risk-Based Vulnerability Management (RBVM) to Continuous Threat Exposure Management (CTEM) requires a proactive, adaptive approach that integrates real-time threat detection, prioritization, and mitigation with continuous monitoring and improvement.
Automated and Manual External Attack Surface Scans
Automated and Manual Out-of-the-box Security Scans: Code, Container, Cloud, Web, Network, Mobile
See our integrations here.
Surface control gaps, weak points and misconfigurations

You must know how well your controls are working to know where remediation matters most.
3700+ Attack Scenarios and Countless Playbooks at Your Fingertips
Surface and Dive into Faulty Controls and Where Attackers Find an In.
Leverage a Large Patch Database and Multi-Path Remediation Recommendations

Uni5 Xposure provides intelligence you can leverage to fortify assets and improve controls.
50,000+ Patch Database to Streamline Patches
Where patches are unavailable, leverage IoC intelligence to improve detection and response signatures.
Remediate according to your risk appetite, and track all decisions
Automated and Manual External Attack Surface Scans
Automated and Manual Out-of-the-box Security Scans: Code, Container, Cloud, Web, Network, Mobile
See our integrations here.
Surface control gaps, weak points and misconfigurations


You must know how well your controls are working to know where remediation matters most.
3700+ Attack Scenarios and Countless Playbooks at Your Fingertips
Surface and Dive into Faulty Controls and Where Attackers Find an In.
Leverage a Large Patch Database and Multi-Path Remediation Recommendations

Uni5 Xposure provides intelligence you can leverage to fortify assets and improve controls.
50,000+ Patch Database to Streamline Patches
Where patches are unavailable, leverage IoC intelligence to improve detection and response signatures.
Remediate according to your risk appetite, and track all decisions
Discover everything about Hive Pro features, benefits, and more.