Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the PDF file here
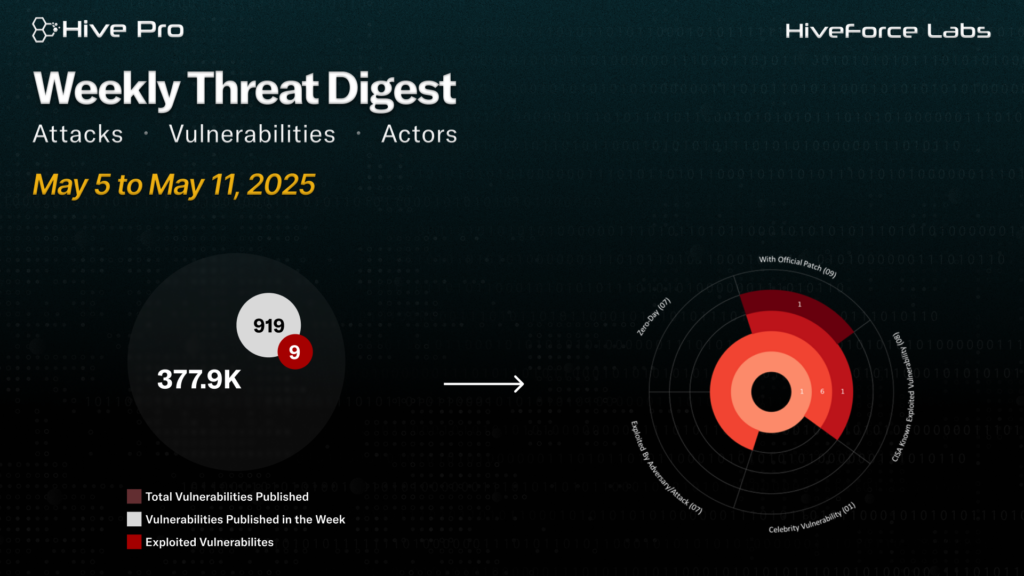
HiveForce Labs has identified a surge in cyber threats, with ten attacks executed, nine vulnerabilities uncovered, and three active adversaries exposed in the past week alone highlighting the relentless nature of cyberattacks.
HiveForce Labs has uncovered a surge in cyber threats, headlined by CVE-2025-3248, a critical unauthenticated remote code execution (RCE) vulnerability in Langflow. Public proof-of-concept exploits are already available, and active attacks have been observed. Meanwhile, attackers exploited a Windows privilege escalation flaw (CVE-2025-29824) to breach a U.S.-based organization. Using a custom-built infostealer named Grixba and stealthy tools, they silently harvested sensitive data and navigated the network undetected demonstrating a calculated and evasive approach to compromise. Moreover, ransomware groups are evolving fast.
DragonForce, which emerged in late 2023, has grown into a formidable Ransomware-as-a-Service (RaaS) platform, attracting cybercriminals with a streamlined business model and low affiliate cuts, offset by advanced tooling and aggressive exploitation tactics including past use of Log4Shell. At the same time, the Agenda (Qilin) gang is deploying layered attacks with NETXLOADER and SmokeLoader, leveraging memory injection and stealthy payload delivery to evade defenses before launching full-scale ransomware encryption. These developments signal a clear message: organizations must prioritize rapid patching, threat detection, and cybersecurity resilience to stay ahead of increasingly sophisticated adversaries.
Subscribe to receive our weekly threat digests and newsletters directly in your inbox.