Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
For a detailed threat digest, download the PDF file here
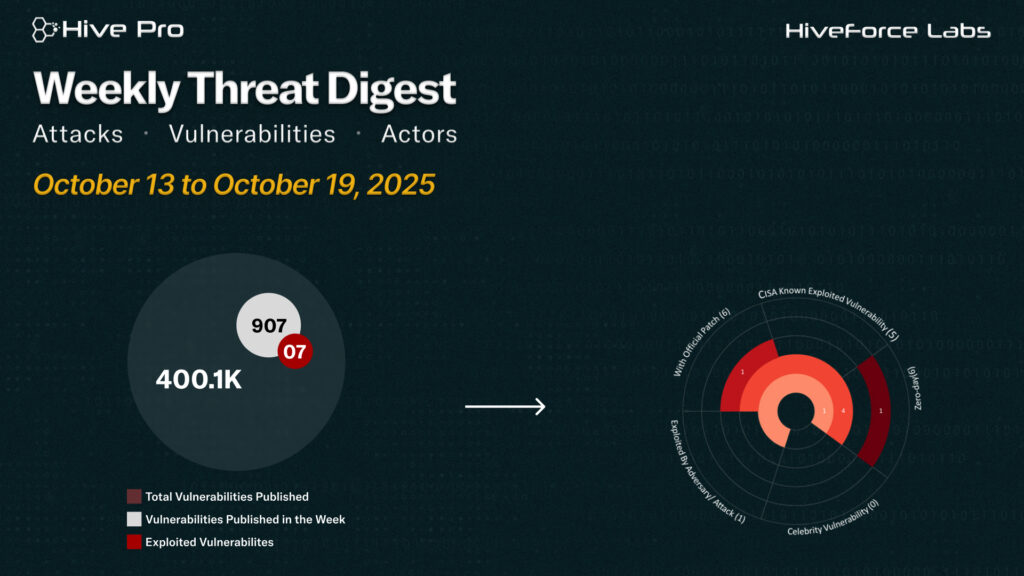
HiveForce Labs has observed a sharp spike in cyber threats, making it clear that attacks are becoming more frequent and more sophisticated. In just the past week, detected five major security incidents, tracked two active threat actor groups, and confirmed active exploitation of two vulnerabilities. The situation underscores how quickly the threat landscape continues to escalate, with attackers aggressively targeting exposed systems and misconfigurations to gain a foothold.
Two critical vulnerabilities are currently under active exploitation. SessionReaper (CVE-2025-54236) in Adobe Commerce and Magento Open Source enables unauthenticated attackers to hijack customer accounts and potentially execute malicious code on targeted systems. Meanwhile, CVE-2025-61932 affects Motex’s Lanscope Endpoint Manager (on-premises), allowing remote adversaries to run arbitrary commands on endpoints by sending specially crafted packets, a threat leveraged in real-world attacks since April 2025. Additionally, Azure Blob Storage has emerged as a major target, as attackers take advantage of misconfigurations, stolen credentials, or vulnerable automation triggers to steal or manipulate sensitive data, deploy ransomware, and maintain persistence in cloud environments.
The week also brought attention to high-profile espionage campaigns. Iran-linked MuddyWater has been phishing government and critical infrastructure entities across the Middle East and North Africa, deploying the Phoenix backdoor for intelligence collection. Moreover, North Korea’s Lazarus group continues to expand Operation DreamJob, shifting its focus toward European defense companies shaping next-generation drone technology. These developments reinforce a critical message for organizations everywhere: proactive defense, swift patching, and strong cyber hygiene are no longer optional; they are essential for survival in today’s hostile digital world.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.