Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the PDF file here
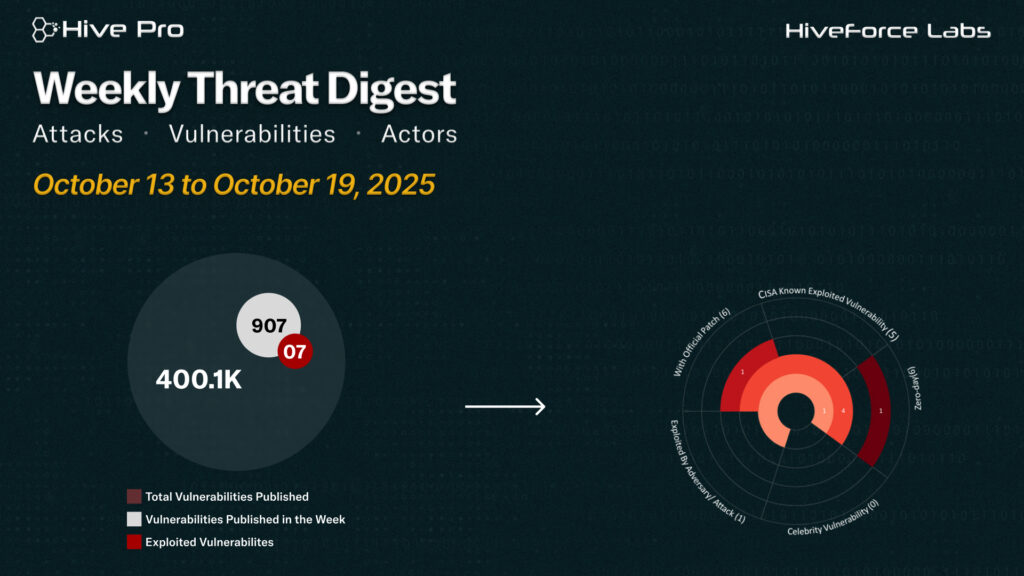
HiveForce Labs has recently made significant advancements in identifying cybersecurity threats. Over the past week, seven major attacks were detected, seven critical vulnerabilities were actively exploited, and two threat actors were closely monitored, reflecting an alarming escalation in malicious activities.
Microsoft’s October 2025 Patch Tuesday fixes 196 vulnerabilities, including three zero-days across Windows and Microsoft products, requiring urgent patching. CVE-2025-11371 is an unauthenticated LFI in Gladinet CentreStack/TrioFox that exposes the ASP.NET machine key (via Web.config), enabling RCE when chained with CVE-2025-30406, actively exploited since Sept 2025 and unpatched, posing critical enterprise risk.
Additionally, TA585 is a financially motivated group targeting finance & accounting firms with precision social-engineering and renting MonsterV2, a $800–$2,000/month MaaS offering remote access, data theft, and SonicCrypt-protected surveillance, making it a highly adaptive 2025 threat. In August 2025, a suspected China-linked actor gained persistent access to F5 systems, exfiltrating source code and vulnerability data, highlighting serious risks to enterprises and government networks. These rising threats pose significant and immediate dangers to users worldwide.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.