Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the PDF file here
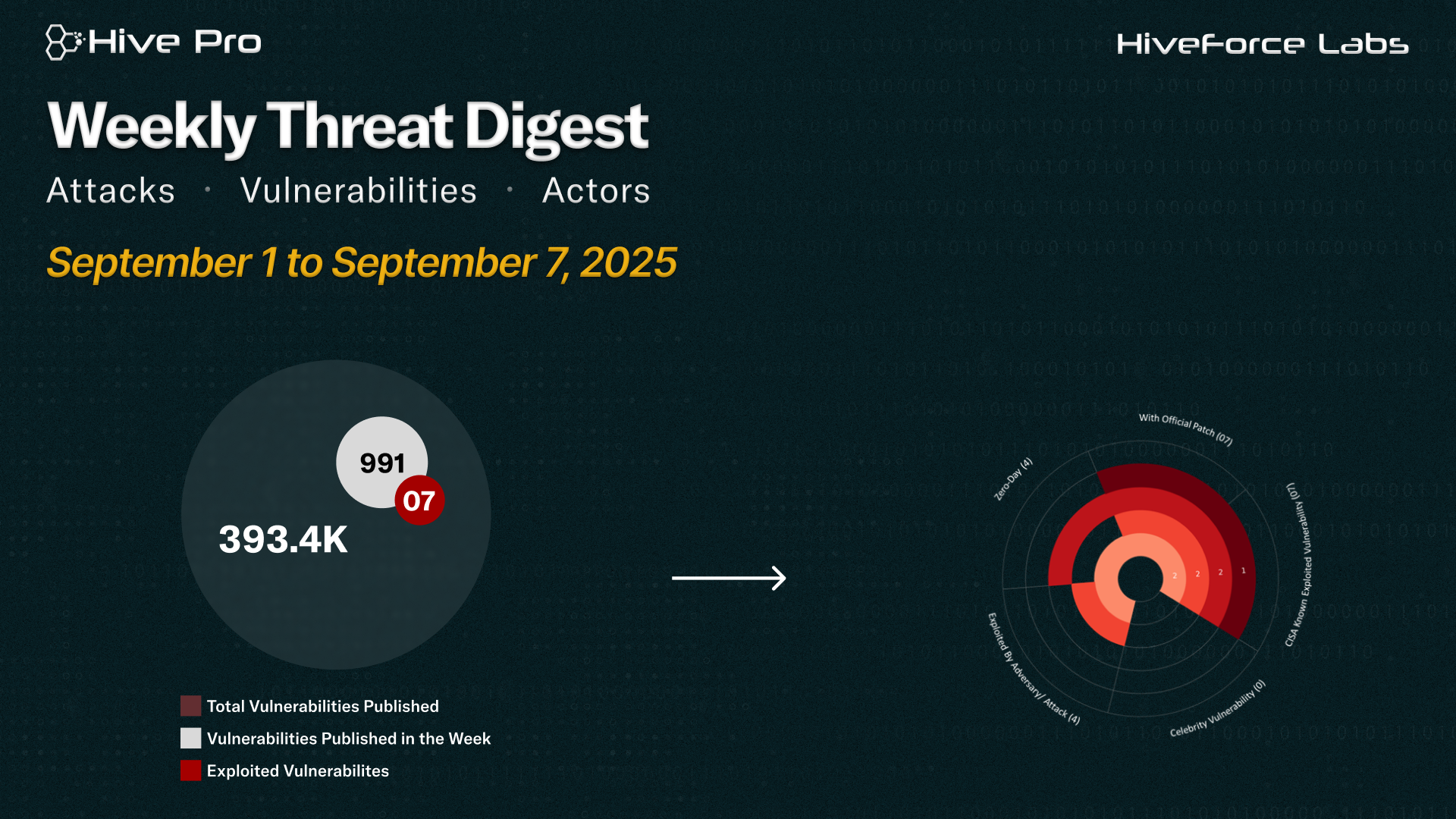
HiveForce Labs has observed a significant surge in cybersecurity threats, underscoring the growing complexity and frequency of cyber incidents. Over the past week, ten major attacks were detected, seven critical vulnerabilities were actively exploited, and three threat actor groups were closely monitored, reflecting an alarming escalation in malicious activities.
Among the most alarming discoveries is a zero-day vulnerability in Sitecore, CVE-2025-53690, actively exploited in the wild. By leveraging a hidden ViewState deserialization flaw, attackers deployed the WEEPSTEEL malware, quietly mapping networks, exfiltrating configuration files, and probing deep into Active Directory environments. Meanwhile, a flaw in WhatsApp’s iOS and macOS apps (CVE-2025-55177) has been exploited in targeted zero-day campaigns, often chained with Apple’s CVE-2025-43300, demonstrating how attackers are blending multiple vulnerabilities to maximize impact.
The threat landscape is further complicated by emerging actors like GhostRedirector, a China-aligned group targeting Windows servers globally since 2024, which has compromised at least 65 servers by mid-2025. Using SQL injection flaws, public exploits, and deploying backdoors like Rungan alongside IIS malware Gamshen, the group exemplifies the growing scale of cyber aggression. Meanwhile, the Quad7 botnet is actively exploiting two critical TP-Link router flaws (CVE-2023-50224 and CVE-2025-9377) to steal credentials and launch large-scale password spray attacks on Microsoft 365 accounts. Collectively, these developments highlight the urgent need for proactive defense, rapid patching, and resilient cybersecurity strategies in an increasingly hostile digital environment.
These rising threats represent an immediate and global cybersecurity risk.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.