Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the PDF file here
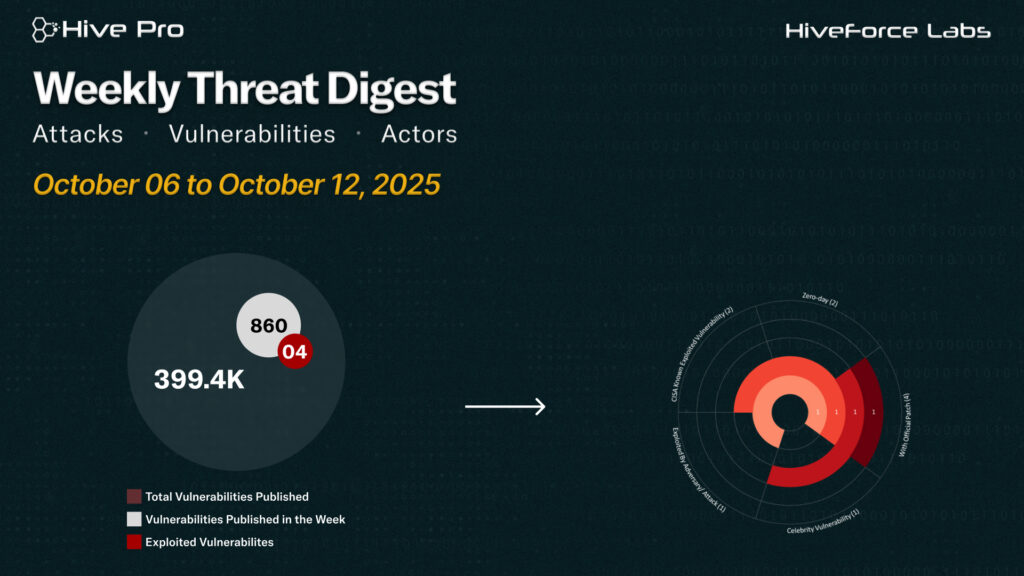
HiveForce Labs has reported a sharp rise in cybersecurity threats, highlighting the increasing complexity and frequency of global cyber incidents. Over the past week, six major attacks were detected, four critical vulnerabilities were publicly disclosed, and five active threat actor groups were monitored, signaling a concerning escalation in malicious activity.
One of the most severe vulnerabilities, CVE-2025-61882, is an unauthenticated remote code execution flaw in Oracle E-Business Suite (EBS). This weakness has been actively exploited by the Cl0p ransomware group since August 2025, with attack frequency surging after a proof-of-concept exploit was leaked in October 2025 by the collective known as Scattered Lapsus$ Hunters.
Earlier in 2025, an unidentified actor posing as the Libyan Navy’s Office of Protocol targeted Brazil’s military through a malicious calendar file exploiting a zero-day vulnerability in the Zimbra Collaboration Suite (CVE-2025-27915).
Another campaign tracked Water Saci, which spreads the SORVEPOTEL malware through WhatsApp, demonstrating the expanding reach of social engineering tactics. This underscores the growing importance of proactive security updates and robust monitoring to defend against sophisticated, rapidly evolving attacks.
Subscribe to receive our weekly threat digests and alerts directly in your inbox.