Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the pdf file here
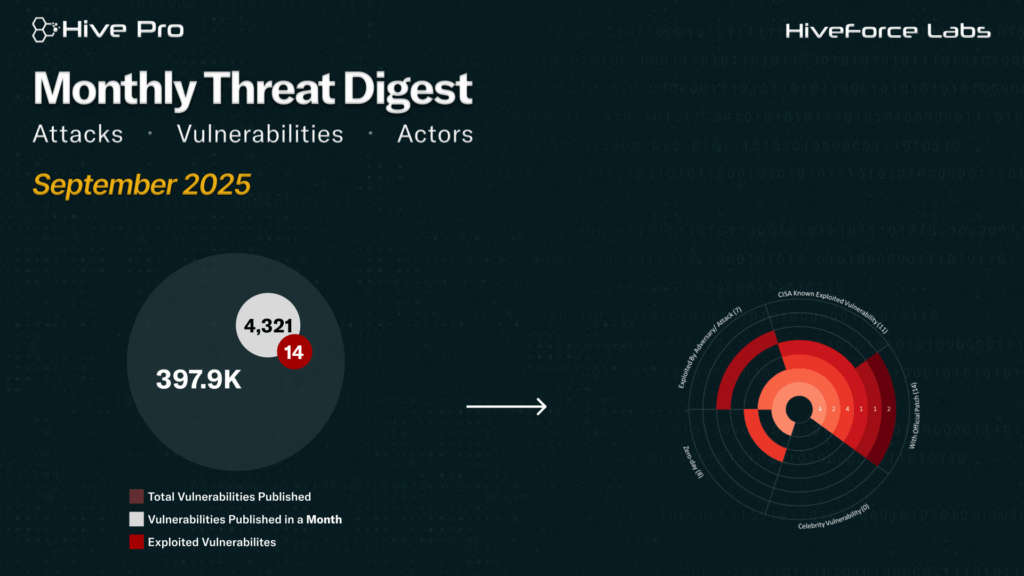
September proved to be one of the most turbulent months in cybersecurity, marked by the active exploitation of eight zero-day vulnerabilities. Among the most critical was CVE-2025-53690 in Sitecore, which is under active attack in the wild to deploy the WEEPSTEEL malware. Another high-profile case involved a zero-click vulnerability in WhatsApp’s iOS and macOS applications (CVE-2025-55177). This flaw was exploited as part of a sophisticated zero-day exploit chain in conjunction with Apple’s CVE-2025-43300, highlighting the growing risks of seamless, user-independent attack vectors.
In parallel, ransomware operations continue to escalate. The NightSpire Ransomware-as-a-Service (RaaS) group has been exploiting vulnerabilities such as CVE-2024-55591 in FortiOS to gain initial access. Meanwhile, PromptLock ransomware, the first known AI-driven ransomware written in Golang, demonstrates how cybercriminals are weaponizing large language models to generate adaptive malicious code.
Meanwhile, GhostRedirector, a newly attributed China-aligned actor, has been targeting Windows servers globally. By mid-2025, the group had compromised at least 65 servers using SQL injection vulnerabilities, privilege escalation exploits, and the deployment of custom malware. Organizations must prioritize proactive defense strategies, patch critical vulnerabilities without delay, and adopt behavior-driven security frameworks to stay ahead in an ever-evolving digital battleground.