Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the pdf file here
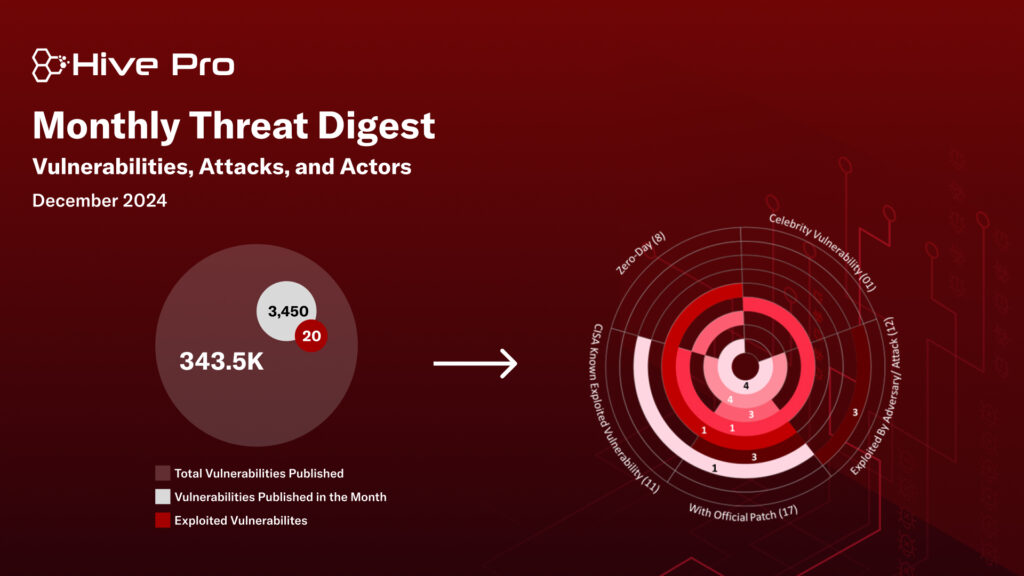
December saw a surge in cybersecurity threats, with the discovery of eight zero-day vulnerabilities and critical flaws in widely used platforms. Notably, two critical zero-day vulnerabilities CVE-2024-50623 and CVE-2024-55956 were identified in Cleo’s file transfer products Harmony, VLTrader, and LexiCom. These vulnerabilities, currently being exploited by threat actors, allow unrestricted file uploads and downloads, potentially enabling remote code execution (RCE). Organizations using these tools for secure file transfers are at significant risk, with the Cl0p ransomware gang actively targeting these flaws.
Ransomware attacks also spiked in December, with groups like Helldown and Black Basta leading aggressive campaigns. These incidents underscore the growing complexity of ransomware tactics, highlighting the critical need for strong backup systems, disaster recovery plans, and continuous employee training to identify and avoid phishing attempts.
In addition, at least eight distinct threat actors carried out targeted operations throughout the month. Among them was Secret Blizzard, also known as Turla, a Russian cyber-espionage group that has leveraged tools and infrastructure from at least six other threat actors over the past seven years. Known for maintaining long-term access to systems, Turla deploys advanced backdoors like TwoDash and TinyTurla, often focusing on politically sensitive intelligence and cutting-edge research. Meanwhile, Cloud Atlas introduced a sophisticated, previously unknown toolset, using phishing emails to exploit a known vulnerability. This attack chain drops malicious files, such as the VBShower and PowerShower backdoors, allowing attackers to infiltrate systems with stealth.
Subscribe to keep up on a weekly basis with our weekly threat digests and newsletters.