Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the pdf file here
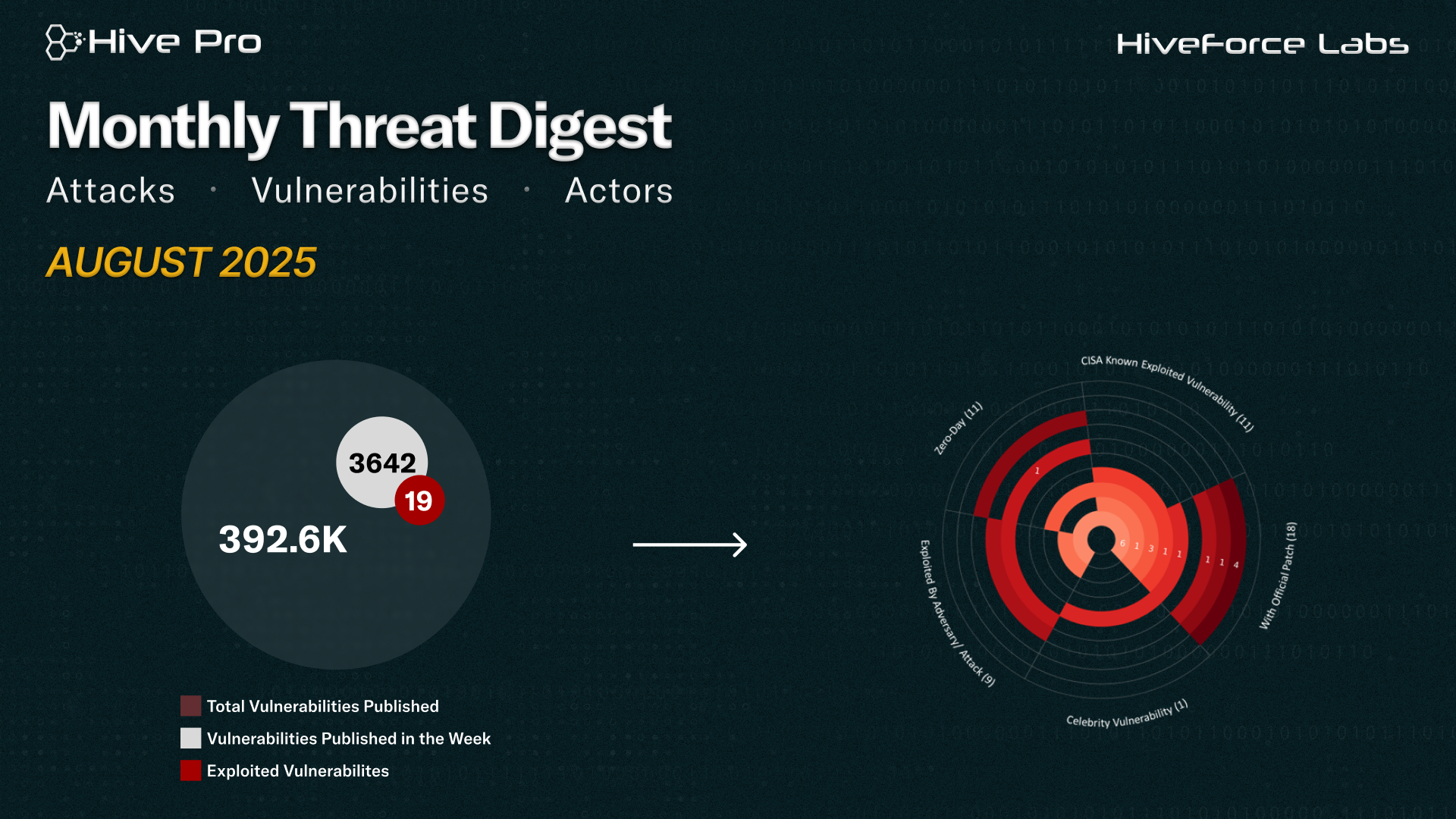
August proved to be a turbulent month for cybersecurity, marked by the emergence of a celebrity vulnerability called BadSuccessor alongside eleven newly discovered zero-days. Among the most pressing was CVE-2025-7775, a memory overflow flaw in Citrix NetScaler ADC and NetScaler Gateway that has already been weaponized in real-world attacks. The flaw enables unauthenticated remote code execution (RCE) or denial of service (DoS), making it a high-value target for threat actors. Another urgent case was CVE-2025-43300, a critical zero-day in Apple’s Image I/O framework. With little or no user interaction required, attackers can exploit this flaw by simply delivering a malicious image file, Apple has confirmed is being leveraged in targeted campaigns.
At the same time, state-aligned groups escalated their global operations. Salt Typhoon, a Chinese state-sponsored threat actor, widened its reach across more than 600 organizations in 80 countries, including 200 in the United States. Meanwhile, Storm-0501, pivoted away from conventional ransomware toward sophisticated cloud-focused attacks, taking advantage of identity misconfigurations and the fractured defenses of hybrid infrastructures. These shifts highlight how adversaries are adapting their strategies to exploit weaknesses in modern enterprise environments.
Elsewhere, Russian operations continued to loom large. Static Tundra, a Moscow-linked espionage group, was observed exploiting Cisco IOS’s long-standing Smart Install vulnerability (CVE-2018-0171), deploying advanced implants and custom tooling to seize control of unpatched devices. On another front, the cybercriminal collective COOKIE SPIDER unleashed SHAMOS, a customized variant of the Atomic macOS Stealer (AMOS), luring victims through malvertising campaigns and fraudulent tech support websites. Together, these campaigns underscore the urgency for organizations to reinforce their defenses and remain vigilant in a digital arena where threats grow sharper and more relentless with each passing month.