Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the pdf file here
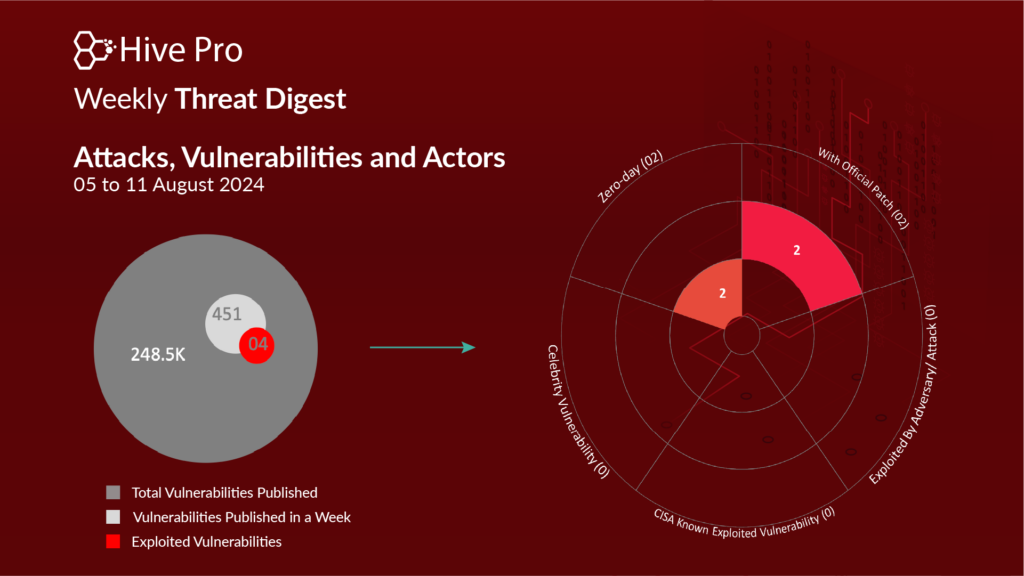
HiveForce Labs has recently made significant progress in uncovering cybersecurity threats. Over the past week alone, the lab detected eighteen executed attacks, reported four exploited vulnerabilities, and identified four active adversaries. These findings underscore the persistent and escalating danger of cyber intrusions.
Furthermore, Hunters International, a Ransomware-as-a-Service (RaaS) operation suspected of being a rebranding of Hive ransomware, emerged in October 2023 and has claimed responsibility for 134 attacks in early 2024. A pre-authentication remote code execution vulnerability, CVE-2024-38856, has also been uncovered in Apache OFBiz, posing a severe risk to organizations utilizing this open-source enterprise resource planning (ERP) system.
Moreover, several critical security flaws in Progress Software’s WhatsUp Gold, particularly CVE-2024-4885, are being actively exploited. The Bloody Wolf threat group has been targeting organizations in Kazakhstan since late 2023 using STRRAT malware. The “0.0.0.0 Day” vulnerability is another critical security flaw affecting major web browsers like Chromium, Firefox, and Safari, allowing malicious websites to exploit localhost APIs through the 0.0.0.0 IP address. Two new zero-day vulnerabilities in Windows, CVE-2024-38202 and CVE-2024-21302, allow attackers to revert systems to outdated, unpatched versions, making them vulnerable to previous exploits. These growing threats present an immediate and significant danger to users worldwide.
Subscribe to receive our weekly threat digests and newsletters directly in your inbox.