Comprehensive Threat Exposure Management Platform

Beat them to it. Simulate the most likely attack campaigns and exploits against your critical assets to surface security gaps, misconfigured and weak controls. Build your defenses with confidence.
The only way to know if you’re secure is to test your security–not once, but continuously in a secure, non-disruptive environment.
Without continuous simulations using up-to-date threat intelligence (CVEs, malware, MITRE TTPs), organizations cannot effectively map out attack paths, especially in complex hybrid and cloud environments. This blind spot allows attackers to exploit unnoticed vulnerabilities and misconfigurations, leading to undetected access to critical assets.
Without insights from simulated attack scenarios that reveal how attackers could chain vulnerabilities to reach critical assets, remediation efforts often target less strategic vulnerabilities. This misprioritization leads to wasted efforts on low-impact fixes while leaving the most exploitable pathways open, directly increasing the risk of significant breaches.

In the absence of continuous, automated testing of their security posture against the latest adversary techniques, organizations remain reactive, only addressing vulnerabilities after an exploit has been attempted or succeeded. This lack of foresight prevents preemptive strengthening of defenses and allows attackers to exploit gaps that could have been closed.

Security teams without the ability to validate and filter alerts based on realistic attack simulations are inundated with false positives and irrelevant alerts. This overwhelming flow consumes valuable resources and detracts from focusing on alerts that signify real threats to critical systems.
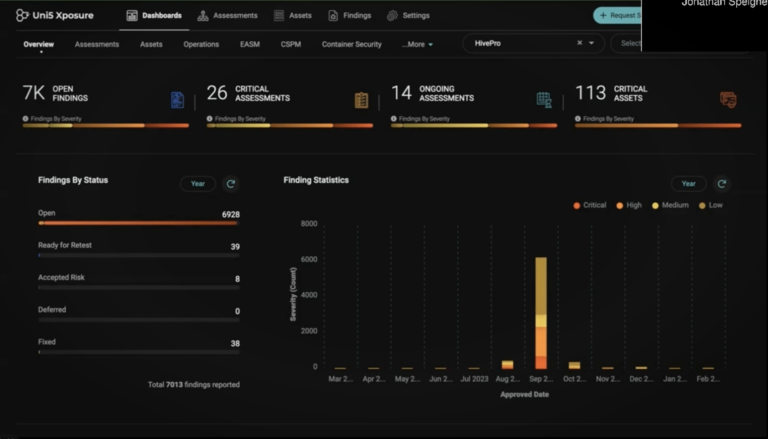
Without continuous simulations using up-to-date threat intelligence (CVEs, malware, MITRE TTPs), organizations cannot effectively map out attack paths, especially in complex hybrid and cloud environments. This blind spot allows attackers to exploit unnoticed vulnerabilities and misconfigurations, leading to undetected access to critical assets.

Without insights from simulated attack scenarios that reveal how attackers could chain vulnerabilities to reach critical assets, remediation efforts often target less strategic vulnerabilities. This misprioritization leads to wasted efforts on low-impact fixes while leaving the most exploitable pathways open, directly increasing the risk of significant breaches.

In the absence of continuous, automated testing of their security posture against the latest adversary techniques, organizations remain reactive, only addressing vulnerabilities after an exploit has been attempted or succeeded. This lack of foresight prevents preemptive strengthening of defenses and allows attackers to exploit gaps that could have been closed.

Security teams without the ability to validate and filter alerts based on realistic attack simulations are inundated with false positives and irrelevant alerts. This overwhelming flow consumes valuable resources and detracts from focusing on alerts that signify real threats to critical systems.
Best guesses don’t cut it. Simulate attacks, identify the real dangers, and neutralize threats before they can strike. From misconfigurations to hidden exposures, we continuously test and help seal security gaps that put your enterprise at risk.
Leverage the latest collection of CVEs, malware, and MITRE TTPs to simulate attacks and visualize real attack paths, enabling security teams to proactively identify and close critical vulnerabilities before they can be exploited. We focus on what really matters by validating threats that can reach your critical assets.
Comprehensive Security Posture AssessmentRegularly validate your security measures against the widest range of attack scenarios, providing a continuous assessment of your security posture. This allows for immediate identification and closure of any security gaps, significantly reducing cyber risk exposure and enhancing overall security resilience.
Optimized Remediation EffortsBy simulating attack chains, your teams can see exactly which vulnerabilities to prioritize for remediation based on their direct path to critical assets, ensuring resources are allocated to mitigating the highest risks first.
Streamlined Alert ManagementReduce alert fatigue by using simulated attack scenarios to prioritize alerts based on their potential impact on critical assets, allowing security teams to focus on genuine threats rather than getting overwhelmed by false alarms.
Book a free demo and find out more about how Hive Pro can double your operational efficiency
Book a DemoDiscover everything about Hive Pro features, benefits, and more.