Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action

From the Silk Road’s ancient trade routes to today’s global networks, supply chains have shaped empires, fueled revolutions, and driven economies. Now, in an age of digital transformation, they’ve evolved from logistical backbones into dynamic, tech-driven ecosystems. Powered by digital networks, AI, IoT, and blockchain, modern supply chains are intelligent systems that adapt, predict, and respond in real time. Their evolution highlights their critical role in industries and societies, while introducing new challenges and opportunities in the digital age. Modern supply chains involve intricate webs of suppliers, manufacturers, and distributors, creating numerous potential entry points for digital exploitation. From cyber intrusions targeting software updates to physical tampering with hardware, the methods of attack have evolved, often combining traditional tactics with cutting-edge technology. A recent, alarming example is the Lebanon Pager Attack, where compromised devices led to catastrophic outcomes, including loss of lives. In this blog, you’ll learn about the types of supply chain attacks occurring today. This background will be supported by our Lebanon Pager Attack case study where you’ll understand theory manifest into reality.
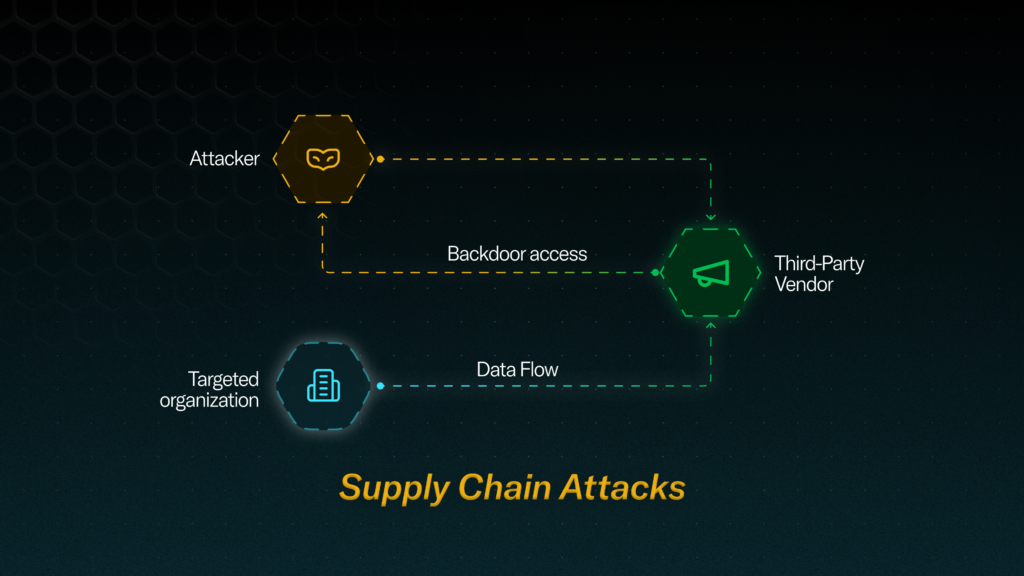
Supply chain attacks occur when adversaries infiltrate an organization by exploiting vulnerabilities in its third party vendors or suppliers. These attacks leverage the trust and access organizations grant to third-party providers, using them as entry points for malicious activities.

They’re Complex and Sprawling : Modern supply chains are vast networks where one weak link can open the door for attackers.
Trust Can Be a Double-Edged Sword : Organizations grant suppliers special access to systems, but this trust can be exploited by attackers.
Visibility is a Blind Spot : Many companies lack insight into suppliers’ cybersecurity practices, creating blind spots that expose supply chains.
A supply chain attack exploits these vulnerabilities by targeting the interconnected web of third-party relationships, turning trusted partnerships into avenues for malicious activity.
The Lebanon Pager Attack, which occurred on September 17-18, 2024, stands as one of the most chilling examples of a supply chain attack in recent history. This attack unfolded against the backdrop of the Israel-Hezbollah conflict, leveraging seemingly simple communication devices to unleash destruction on a massive scale. By targeting pagers used by Hezbollah operatives, attackers exploited a critical weak point in Hezbollah’s operations, causing widespread devastation.
Hezbollah, seeking to avoid digital surveillance, had turned to pagers and other low-tech devices for communication. Pagers, relying on older radio signals, were perceived as safer alternatives to modern smartphones. However, Israeli intelligence operatives allegedly identified this vulnerability and infiltrated Hezbollah’s supply chain through shell companies based in Hungary. These companies manufactured pagers embedded with explosives, under the guise of legitimate licensing agreements with a Taiwanese firm.
The compromised pagers were then distributed to Hezbollah operatives and sympathizers across Lebanon and Syria. On September 17 and 18, these devices were remotely detonated using electromagnetic signals, leading to widespread destruction. The explosions claimed 37 lives, injured over 3,450 people, and caused significant damage in areas like southern Beirut and the Beqaa Valley. Civilians, including children, were among the casualties, amplifying the tragedy.
Although Israel initially denied involvement, subsequent admissions by Israeli Prime Minister Benjamin Netanyahu revealed the operation as part of a broader strategy to weaken Hezbollah. The attack has since raised global concerns about the weaponization of everyday devices and the vulnerabilities inherent in modern supply chains.


The ripple effects of supply chain attacks go far beyond the immediate target, creating a cascade of consequences that are hard to contain. They can be financially devastating to companies that would face hefty fines as a result. The fallout of a damaged reputation, and massive cleanup costs that can take years to recover from also have resounding effects. The operational impacts is equally as crippling.
Take the NotPetya malware attack for instance– it brought global logistics giants to their knees, freezing operations for weeks and throwing entire supply chains into chaos. But the stakes are even higher when these attacks spill into the geopolitical arena. The Lebanon Pager Attack, for instance, didn’t just devastate lives and communities—it fanned the flames of an already volatile conflict, showing how supply chain vulnerabilities can become powerful weapons in international disputes.
The Lebanon Pager’s Attack shows how even simple technology, like pagers, can be turned into powerful weapons. By hiding explosives in communication devices, the attackers used supply chain weaknesses to cause serious harm. Hezbollah thought pagers were safer than smartphones, but this strategy backfired, making them more vulnerable instead.
Supply chain security must be a core priority. Organizations, industries, and governments need robust defenses, from global regulations to secure-by-design practices. Threat Exposure Management (TEM) plays a critical role by identifying vulnerabilities, prioritizing risks, and providing actionable solutions. By adopting TEM, organizations can foster resilience, safeguarding supply chains and protecting communities from the cascading effects of future attacks.
Cybersecurity practitioners are invited to experience the power of Hive Pro’s EASM solution. Start a free trial or get a free assessment of your attack surface today to see how Hive Pro can enhance your organization’s security posture.
For more information on how Hive Pro’s EASM solution can enhance your cybersecurity posture, visit www.hivepro.com/free-easm-assessment