Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
Running short on time but still want to stay in the know? Well, we’ve got you covered! We’ve condensed all the key takeaways into a handy audio summary. Our AI-driven podcasts are fit for on the go.
In April 2025, a single phone call didn’t just ‘help crash’ Marks & Spencer’s operations; it shattered them, costing a staggering £300 million. This wasn’t a sophisticated zero-day attack. This was Scattered Spider, a teenage-led cybercrime group, exposing the brutal truth: human error remains the ultimate vulnerability. They’re redefining social engineering, and your organization could be next.
Scattered Spider, also known as UNC3944, Octo Tempest, and several other aliases, is among the most formidable and adaptive threat actors in the cybercrime world today.. Their tactics have evolved from data theft for extortion to full-blown ransomware deployments in collaboration with ransomware gangs like ALPHV/BlackCat and DragonForce.
One of their most impactful alleged operations in 2025 involved British retailer Marks & Spencer (M&S), though official attribution has not been confirmed. The incident caused widespread operational disruption and projected financial losses of £300 million (about $400 million). This blog unpacks the group’s tactics, explores the M&S incident in depth, and draws out key lessons.
A Decentralized, Youth-Driven Cyber Threat
This isn’t your typical APT. Scattered Spider, a ruthless collective of young adults aged 16 to 22 and many based in English-speaking countries (mostly from the UK and US) is dismantling defenses not with malware alone, but with manipulation and cunning. Their financial motivation drives increasingly aggressive and technically advanced operations across multiple sectors, from telecom and retail to insurance, more recently, airlines. One of their defining strategies is its focus on targeting one specific sector at a time, executing coordinated campaigns before shifting to new industries.
Despite arrests of suspected members, the group’s decentralized and fluid structure makes them difficult to dismantle. Although some of their early collaborators, such as ALPHV/BlackCat and RansomHub, have since become defunct, Scattered Spider has continued to evolve, now aligning with active ransomware groups like DragonForce and Qilin.
This shift signals an escalation in both capability and impact, as Scattered Spider adapts and partners with leading ransomware-as-a-service (RaaS) operations to extend its reach and effectiveness.
Unlike traditional attackers who rely on software vulnerabilities, Scattered Spider excels at exploiting people. Their hallmark is highly targeted, human-centric attacks, often using AI to craft convincing messages and personas.
Common tactics include:
THESE TACTICS EXPOSE A PAINFUL TRUTH, NO TECHNOLOGY CAN FULLY PROTECT AGAINST A SINGLE MOMENT OF HUMAN ERROR.
Sectoral Targeting Pattern
Scattered Spider’s hallmark is a relentless, sector-by-sector targeting, systematically dismantling defenses across telecommunications, technology, financial services, hospitality, retail, the US insurance, and most recently the airlines sector.

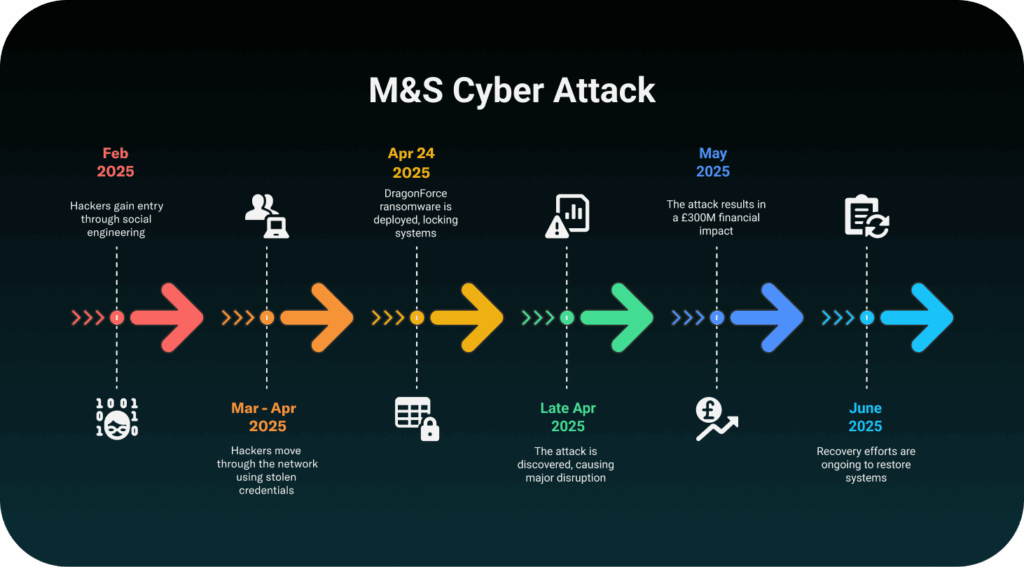
In April 2025, British retail giant Marks & Spencer (M&S) suffered a major cyberattack that severely disrupted its operations. The attack affected online shopping, payment systems, Click & Collect services, and warehouse operations, leading to an estimated financial loss of around £300 million.
According to M&S CEO Stuart Machin, the recent breach was the result of a phishing attack targeting a third-party contractor. Investigators believe that the attackers may have used vishing, impersonating IT or support staff over the phone, to trick help desk personnel and gain login credentials as early as February 2025. With these credentials, they accessed internal systems and exfiltrated the NTDS.dit file, a critical database containing hashed passwords from the company’s Active Directory.
Using these credentials, the hackers moved laterally across the network and eventually deployed DragonForce ransomware, targeting VMware ESXi hosts, the systems that run many of M&S’s virtual machines, responsible for critical operations. This led to widespread disruption, particularly in payment processing and logistics.
In addition to locking systems, the attackers may have stolen customer data, including names, contact details, and order histories, although payment information was reportedly not affected. M&S has launched a comprehensive recovery effort and aims to fully restore e-commerce functionality by July 2025.
ONE BREACH. MULTIPLE FAILURES. £300 MILLION LOST. A LESSON IN EVERY LAYER OF DEFENSE.
In early June 2025, Scattered Spider shifted its focus from UK retail victims to major U.S. insurance companies, including Aflac, Erie Insurance, and Philadelphia Insurance. Within weeks, by late June, the group expanded into the commercial airline industry, targeting Hawaiian Airlines, WestJet, and breaching Qantas, compromising data belonging to nearly six million customers. What stands out is not just the range of industries affected, but the fact that their attack tactics have remained largely unchanged.
Across these sectors, as in previous campaigns against telecom, finance, and retail, Scattered Spider relied on high-pressure social engineering to gain initial access. Attackers impersonated internal IT staff through vishing calls or used adversary-in-the-middle (AiTM) phishing pages to steal authentication tokens. Once inside, they manipulated help desk agents into resetting credentials or approving rogue devices, effectively bypassing multi-factor authentication. They then leveraged legitimate tools like Salesforce Data Loader and cloud admin consoles to escalate privileges and exfiltrate sensitive data.
In the insurance sector, the group targeted medical and financial records, while in airlines, they focused on customer identity data and causing operational disruptions. Despite the different targets, their approach, and the resulting impact, remained consistent.
SCATTERED SPIDER ISN’T JUST CHANGING TARGETS, THEY’RE PERFECTING A PLAYBOOK. AND UNTIL THAT PLAYBOOK STOPS WORKING, THEY’LL KEEP TURNING PAGES, INDUSTRY BY INDUSTRY.
Attackers often sound authoritative and confident, pressuring third-party providers into bypassing security protocols.
Establishing identity before servicing needs and under no circumstances should security controls be disabled or bypassed to accommodate individual user needs. Unusual requests should be flagged and reviewed.
The theft of NTDS.dit shows there wasn’t enough monitoring in place, and critical systems didn’t have the extra protection they needed.
Attackers remained undetected for months, indicating inadequate threat hunting, log reviews, or proper monitoring in place.
Initial access may have been gained via a third-party vendor, reinforcing the need for strict supply chain security.
This allowed attackers to move laterally and access sensitive systems.
To survive the next wave, Organizations must adopt a multi-layered defense to prevent similar incidents:
Investigations into Scattered Spider are ongoing, led by entities including the UK’s National Crime Agency (NCA) and the FBI. Organizations experiencing ransomware or social engineering-based attacks are strongly encouraged to report incidents to law enforcement and share threat intelligence.
PARTNERING WITH LAW ENFORCEMENT ISN’T OPTIONAL, IT’S ESSENTIAL.
The attack on Marks & Spencer by Scattered Spider reminds us, cybersecurity is no longer just a technical challenge, it’s a human one. Their latest pivot to the US insurance sector is not an isolated incident; it’s the continuation of a relentless, sector-by-sector targeting, systematically dismantling defenses across industries in a clear, sequential pattern. This also shatters the common belief that cyber threats originate only from distant, foreign adversaries. In reality, these attackers can be local, fluent in the language, and culturally adept, making them harder to detect and far more effective at social engineering.
Your industry could be next. Organizations must proactively defend against social engineering, improve their internal processes, and develop resilience to advanced persistent threats.
Scattered Spider represents a new breed of threat actor: young, agile, and dangerously effective. They don’t rely on zero-day exploits or custom malware, they rely on us. That makes defense everyone’s responsibility.
THE THREAT IS EVOLVING. OUR DEFENSES MUST EVOLVE FASTER.