Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
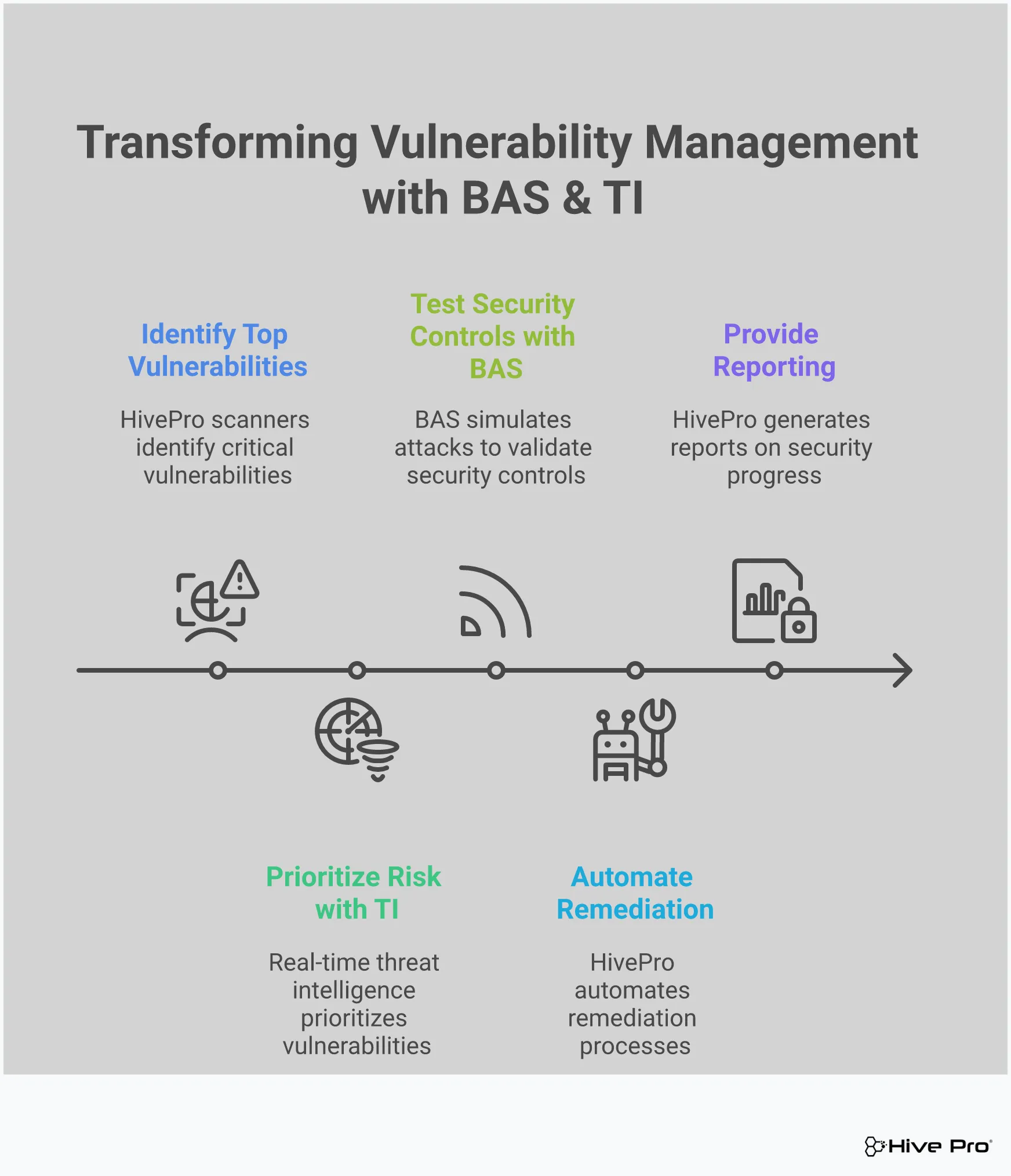
The difference between a good security program and a great one often comes down to context. Without it, a list of 10,000 vulnerabilities is just a list. But when you can see that three of those vulnerabilities are being actively exploited by a threat group targeting your industry, your priorities become crystal clear. This is the power of combining actionable threat intelligence with your vulnerability data. It helps you focus your limited resources on the fixes that will have the biggest impact. By taking it a step further and using simulations to validate your defenses against those specific threats, you close the loop on your exposure. Hive Pro is an end-to-end CTEM solution built to provide this exact context.
When we talk about an end-to-end solution, we mean a single, unified platform that handles every stage of threat exposure management. Instead of juggling multiple tools that don’t communicate well, you get a seamless workflow from start to finish. Hive Pro provides exactly that by covering the entire Continuous Threat Exposure Management (CTEM) lifecycle. This approach helps you move from simply managing a long list of vulnerabilities to proactively reducing your real-world exposure to threats. It’s about connecting the dots between a potential weakness and an actual business risk, all within one system.
Hive Pro is built on the five pillars of Gartner’s CTEM framework: Scoping, Discovery, Prioritization, Validation, and Mobilization. Covering all five steps means you get a complete picture of your security posture without any gaps. You can define what’s important (Scoping), find all your assets and their vulnerabilities (Discovery), and figure out which threats need immediate attention (Prioritization). Then, you can test if your defenses actually work against those threats (Validation) and finally, get clear guidance on how to fix the problems (Mobilization). Having a single Continuous Threat Exposure Management platform that handles all five pillars simplifies your security operations and ensures nothing falls through the cracks.
The engine driving this end-to-end approach is the Uni5 Xposure platform. It’s designed to give you a continuous, clear view of your entire attack surface. The platform doesn’t just find weaknesses; it helps you understand them in the context of real-world threats and then guides your team toward the most effective remediation steps. One of its standout features is its ability to run simulated attacks. This allows you to safely test your vulnerabilities and see how an attacker might exploit them. It’s a practical way to validate whether your security controls are performing as expected, transforming your security strategy from a reactive guessing game into confident, proactive action.
For years, security teams have been stuck in a reactive cycle of scan, patch, and repeat. The shift to exposure management is about breaking that cycle. It’s not just about finding vulnerabilities; it’s about understanding which ones truly put your organization at risk and closing those gaps before they can be exploited. Hive Pro is designed to guide this transition, moving your security posture from a state of reaction to one of proactive defense. This approach helps you focus on imminent risks and attacks, transforming your strategy into confident, forward-thinking action.
Being reactive means you’re always one step behind, patching vulnerabilities after they’ve been disclosed or, worse, after an incident. It’s an endless game of catch-up. Hive Pro helps you become proactive by transforming your approach from simple vulnerability management into a comprehensive exposure management strategy. Instead of just fixing problems as they appear, you can anticipate and neutralize threats before they materialize. This means focusing your resources on the exposures that attackers are most likely to target, allowing you to reduce your actual risk quickly and efficiently.
Your digital footprint is constantly changing. New cloud instances, web apps, and devices create potential entry points you might not even know about, and periodic scanning just can’t keep up. Hive Pro’s Uni5 Xposure platform is built to continuously reveal your full attack surface, giving you a real-time, unified view of all your assets. This constant visibility helps you find and fix security weaknesses across your entire environment, from on-premise servers to cloud infrastructure. By understanding your complete attack surface, you can eliminate blind spots and ensure no potential threat goes unnoticed.
Meeting compliance standards is important, but it’s the bare minimum—it doesn’t guarantee you’re secure. A truly effective security program moves beyond checking boxes to focus on preventing breaches. Organizations with a CTEM program are three times less likely to suffer a breach because they prioritize vulnerabilities based on their potential impact on business operations. Hive Pro helps you make this shift by providing advanced vulnerability and threat prioritization. You can see which weaknesses are not only severe but also actively exploited, allowing you to focus your team’s efforts on the fixes that deliver the greatest security impact.
Threat intelligence is everywhere, but most of it is just noise. Security teams are often flooded with generic alerts, vulnerability feeds, and industry reports that are difficult to connect back to their specific environment. The real challenge isn’t getting more data; it’s getting the right data and turning it into a clear action plan. This is where a different approach to threat intelligence becomes essential—one that cuts through the clutter and tells you exactly what you need to fix right now.
Instead of just aggregating public feeds, Hive Pro focuses on delivering curated, contextual intelligence that’s directly relevant to your attack surface. It’s about connecting the dots between a theoretical vulnerability and a real-world threat actor who might exploit it. This approach transforms threat intelligence from a passive stream of information into an active tool for decision-making. By understanding which threats are being actively exploited and how they map to your specific assets, you can move from a state of constant reaction to one of proactive defense. It’s the difference between having a list of 10,000 problems and having a prioritized list of the 10 that truly matter today.
At the heart of our platform is HiveForce Labs, our in-house team of threat researchers and ethical hackers. This team doesn’t just repackage public information; they actively hunt for threats, analyze attacker techniques, and dissect malware to understand how adversaries operate. Their research powers the intelligence within the Uni5 Xposure platform, ensuring the insights you receive are timely, accurate, and relevant. The goal is to provide you with more than just data—it’s to give you clear guidance. HiveForce Labs translates complex threat information into actionable steps, helping your team understand not only what to fix but also why it matters, so you can confidently address your most critical weaknesses.
If you’re using a traditional scanner, you know the feeling of being overwhelmed by a massive list of vulnerabilities. Hive Pro helps you focus on what’s truly important by using threat intelligence to drive vulnerability and threat prioritization. We correlate your unique vulnerabilities with data on active exploits, threat actor TTPs, and malware campaigns. This allows you to see which issues pose a genuine, immediate risk to your organization. Instead of chasing every “critical” CVE, you can concentrate your resources on the vulnerabilities that attackers are actually using. This risk-based approach is how our platform helps reduce your attack surface, focusing your team’s efforts where they will have the greatest impact.
Threat intelligence is most powerful when you can see it in action. Our platform doesn’t just tell you about a threat; it shows you how it could impact your environment. Through adversarial exposure validation, we use breach and attack simulation (BAS) to test your defenses against the very threats our intelligence identifies. This gives you a real-world understanding of your security posture. You can see if your existing controls would actually stop an attack and identify gaps before a real adversary finds them. This process provides crucial context, helping you validate that your security investments are working as expected and confirming that your remediation efforts have successfully closed the exposure.
Knowing you have vulnerabilities is one thing; knowing if they can actually be exploited is another. This is where Breach and Attack Simulation (BAS) comes in. Think of it as a continuous, automated sparring partner for your security team. Instead of waiting for a real attack to see how your defenses hold up, BAS safely simulates real-world attack scenarios to test your security posture from an adversary’s perspective. It’s a fundamental shift from a passive, theoretical approach to an active, practical one.
By running these controlled simulations, you can see exactly how an attacker might move through your network, which security controls might fail, and which vulnerabilities present the most immediate danger. This process is a core component of a modern Continuous Threat Exposure Management (CTEM) program. It moves you beyond just patching vulnerabilities and helps you validate that your entire security ecosystem—from firewalls to endpoint detection—is working together as intended. It’s about replacing assumptions with evidence so you can make smarter, faster decisions to reduce your exposure.
A long list of vulnerabilities can be overwhelming. The key is to know which ones truly matter. BAS helps you cut through the noise by validating your exposure to real threats. It allows your team to safely simulate attack scenarios based on the latest threat intelligence, showing you precisely how an adversary could exploit a specific weakness in your environment. This proactive approach helps you understand your true risk.
Instead of just having a theoretical risk score, you get practical proof of how an attack could unfold. This allows you to prioritize remediation efforts on the vulnerabilities that are not just high-severity on paper, but are confirmed to be exploitable in your unique setup. This process of adversarial exposure validation is crucial for focusing your team’s limited time and resources on the fixes that will have the biggest impact on your security.
You’ve invested heavily in security tools, but are they configured correctly and performing as expected? BAS acts as a quality assurance check for your security controls. By launching simulated attacks that mimic the techniques used by actual threat actors, you can test the effectiveness of your firewalls, endpoint protection, SIEM, and other defenses. It’s like running a fire drill to ensure your prevention and detection systems work when you need them most.
This continuous testing reveals gaps, misconfigurations, or blind spots that might otherwise go unnoticed until a real incident occurs. When a simulated attack bypasses a control, your team gets immediate, actionable feedback. This enables them to fine-tune configurations, update rules, and ensure your security stack is optimized to stop real threats, helping your team work more efficiently and effectively.
Ultimately, the goal is to stop breaches. BAS provides the critical assurance that your defenses are effective against the tactics, techniques, and procedures (TTPs) used by today’s attackers. Organizations that integrate BAS into their security programs are often far less likely to suffer a breach because they are constantly confirming their readiness. It’s one thing to have a security tool in place; it’s another to have proof that it can block a specific ransomware strain’s attack path.
This level of validation provides a critical layer of assurance that goes beyond compliance checklists. By aligning simulations with frameworks like MITRE ATT&CK, you can systematically verify your ability to defend against known adversary behaviors. This confirmation is a key outcome of the Uni5 Xposure Platform, giving your security leaders the confidence that their strategy and investments are genuinely reducing the organization’s risk.
When you’re trying to get a handle on your organization’s security, the last thing you need is another complicated tool that just adds to the noise. The goal is to find a solution that simplifies your workflow, provides clarity, and helps your team take meaningful action. Hive Pro’s platform is built around these principles, giving you a clear, comprehensive way to manage your threat exposure from end to end. It’s designed to be the central hub for your security operations, pulling everything together so you can see the big picture without getting lost in the details.
The Uni5 Xposure platform is designed to help companies find, understand, and fix their cybersecurity weaknesses. It’s not about just running scans and generating endless reports; it’s about creating a continuous, proactive cycle of identifying risks, prioritizing them based on real-world threats, and validating that your defenses are working as expected. This approach helps you break free from the constant fire-fighting that defines so many security teams. Let’s look at the core features that make this possible and how they help you move from a reactive stance to a confident, proactive security posture.
You can’t protect what you can’t see. Your attack surface is constantly changing, with new assets, cloud instances, and applications popping up all the time. Keeping track of it all manually is nearly impossible. Hive Pro gives you a continuous, automated view of your total attack surface, so you always have an up-to-date inventory of every asset across your entire environment. This includes everything from on-premise servers and employee laptops to cloud infrastructure and IoT devices. By discovering and mapping all your assets, you eliminate blind spots and create a solid foundation for your entire security program.
Juggling multiple security tools, each with its own dashboard and data format, is a recipe for confusion and missed threats. Hive Pro brings all your exposure data into a single, unified view. It’s the only platform that covers all five stages of Gartner’s Continuous Threat Exposure Management (CTEM) framework: Scoping, Discovery, Prioritization, Validation, and Mobilization. This means you don’t need to stitch together information from different point solutions. Instead, you get a cohesive picture of your security posture in one place, making it much easier to connect the dots, identify patterns, and understand your true risk level at a glance.
Adopting a new platform shouldn’t mean you have to abandon the tools your team already knows and trusts. Hive Pro is designed to enhance your existing security stack, not replace it. It seamlessly integrates with popular security scanners from vendors like Qualys, Tenable, and Rapid7, consolidating their findings into one centralized platform. This allows you to leverage your current investments while gaining a more holistic and simplified way to manage risks. By bringing all your vulnerability data together, you can correlate findings and get a much richer context for prioritization and remediation.
Finding vulnerabilities is just the first step; knowing which ones to fix first is the real challenge. With thousands of potential issues, teams can quickly become overwhelmed. Hive Pro cuts through the noise by helping you focus on the most critical threats that are actively being exploited in the wild. The platform provides automated, actionable guidance for remediation, telling your team not only what to fix but how to fix it. This vulnerability and threat prioritization ensures your team spends its time on the issues that matter most, significantly reducing your exposure to real-world attacks.
The cybersecurity market is crowded with tools, each promising to solve a piece of the puzzle. This often leaves security teams juggling multiple dashboards, trying to connect dots between siloed data sets, and struggling to see the big picture of their organization’s risk. It’s a common frustration that leads to alert fatigue, missed threats, and a constant feeling of being one step behind attackers. Instead of adding another point solution to your stack, Hive Pro offers a fundamentally different approach.
We built our Uni5 Xposure platform to replace complexity with clarity. By integrating the entire threat exposure management lifecycle into a single, unified system, we help you move beyond simply collecting vulnerability data. The goal is to provide a clear, continuous, and contextualized view of your security posture. This means you can stop wasting time trying to make different tools talk to each other and start focusing on what actually matters: finding and fixing the exposures that pose a real threat to your business. It’s about consolidating your efforts, not just your tools, to achieve better security outcomes with greater efficiency.
Continuous Threat Exposure Management (CTEM) is a framework designed to create a sustainable and repeatable security program. It’s not a one-off project but an ongoing cycle. Gartner outlines this cycle in five key steps: Scoping, Discovery, Prioritization, Validation, and Mobilization. While many vendors address one or two of these areas, Hive Pro is the only platform that covers all five.
This end-to-end coverage means you can manage your entire program from a single place. You can define your attack surface, discover assets and vulnerabilities, prioritize what to fix based on real-world threats, validate that your controls are working, and mobilize your teams to remediate effectively. Having a complete CTEM solution eliminates the dangerous visibility gaps that open up when you have to stitch together multiple, disconnected tools.
If your team is struggling with “tool sprawl,” you know the pain. Managing dozens of different security products creates data silos, complicates workflows, and makes it nearly impossible to get a consistent view of risk. Each tool has its own alerts, its own dashboard, and its own way of measuring things. This fragmentation doesn’t just drain your budget; it drains your team’s time and energy.
Hive Pro was designed to solve this exact problem. A unified platform consolidates all your exposure data into one place, giving you a single source of truth. This allows for more intelligent vulnerability and threat prioritization because the system sees the full context. By breaking down silos, you improve your security posture, streamline operations, and get a much better return on your security investments.
When it comes to evaluating technology, third-party validation from a respected firm like Gartner carries a lot of weight. In its foundational report on Exposure Management, Gartner surveyed the market to see who was delivering on the promise of a holistic security approach. The findings were clear.
Gartner recognized Hive Pro as the only company offering a complete, end-to-end solution for Continuous Threat Exposure Management. This distinction highlights our commitment to providing a truly comprehensive platform, not just another niche tool. For security leaders, this recognition offers confidence that you are investing in a solution that is vetted by industry experts and built to address the full scope of modern threat exposure challenges. It confirms that our unified approach isn’t just a vision—it’s a reality.
While every organization can gain from a more proactive security posture, some industries and teams face unique pressures that make a Continuous Threat Exposure Management (CTEM) approach essential. If you’re navigating strict regulatory landscapes, dealing with sector-specific threats, or trying to improve your security team’s efficiency, a unified platform can make a significant difference. Hive Pro’s end-to-end solution is designed to address the distinct challenges faced by modern businesses, moving them from a state of constant reaction to one of confident control.
Whether you’re in a highly regulated field or simply looking to streamline your security operations, understanding your specific needs is the first step. Let’s look at how a CTEM program provides targeted benefits for different industries and the security professionals working within them.
For industries like healthcare and finance, compliance isn’t just a suggestion—it’s a requirement. The pressure to protect sensitive patient and financial data is immense, and the consequences of a breach go far beyond fines. A CTEM program helps you meet these stringent demands by focusing on what matters most. Hive Pro helps you find the security weaknesses that attackers are actively using, allowing you to fix the most urgent problems first. This proactive stance is critical for demonstrating due diligence and maintaining trust with customers and regulators. By continuously validating your defenses against real-world threats, you can build a security program that not only satisfies auditors but also genuinely protects your most critical assets.
Government agencies and retail companies operate in vastly different worlds, but both face unique and persistent threats. A one-size-fits-all security strategy simply won’t work. Research shows that organizations with CTEM programs are three times less likely to suffer a breach, highlighting the power of a tailored approach. For government bodies, this means protecting critical infrastructure and sensitive national data. For retailers, it means securing vast networks of e-commerce platforms and point-of-sale systems. Hive Pro’s platform helps you understand the convergence of identity, infrastructure, and intelligence in your specific environment, so you can build a defense that’s right for your sector.
Your security team is your first line of defense, but they are often overworked and overwhelmed. Juggling multiple, disconnected tools can lead to alert fatigue and critical security gaps. In fact, teams using too many point solutions are often less efficient and more likely to miss important threats. Hive Pro’s Uni5 Xposure platform is designed to solve this problem. By providing a single, unified view of your entire attack surface, it cuts through the noise. The platform is intuitive and easy to use for security professionals at all levels, which means your team can spend less time managing tools and more time neutralizing threats. This streamlined approach helps reduce burnout and empowers your team to work more effectively.
Adopting a new platform is a big decision, and you need to know it will deliver real results. It’s not just about adding another tool; it’s about fundamentally changing how your security program operates for the better. Moving to a Continuous Threat Exposure Management (CTEM) approach is about achieving tangible, measurable improvements that strengthen your security posture and make your team’s life easier. With a unified platform, you can stop chasing endless alerts and start focusing on what truly matters: preventing breaches. This shift means moving away from a constant state of reaction and toward a strategy of proactive defense. It’s about gaining the visibility and context needed to make confident, risk-based decisions that align with your business goals. When you can see your entire attack surface and understand which threats are actively being exploited, you can direct your resources with precision. Let’s look at the concrete outcomes you can anticipate when you partner with Hive Pro. From drastically cutting down your attack surface to making your team more effective, the goal is to build a more resilient and proactive security program that can stand up to modern threats.
The sheer volume of vulnerabilities can feel overwhelming, but the reality is that not all of them pose an immediate threat. The key is focusing on the ones that do. Imagine being able to reduce your vulnerabilities by 95%. Within a single day, Hive Pro can help you pinpoint the top 1% of risks that attackers are most likely to exploit. This is possible through smart vulnerability and threat prioritization that considers real-world threat intelligence, not just generic CVSS scores. By concentrating your team’s efforts on the critical few instead of the trivial many, you can achieve a significant and immediate reduction in your actual exposure, making your organization a much harder target for adversaries.
If your team is drowning in alerts from a dozen different tools, you’re not alone. Security teams juggling multiple point solutions are 45% more likely to suffer from alert fatigue and 25% more likely to have security gaps. This constant noise makes it difficult to spot real threats. By consolidating your security stack, you can improve your team’s efficiency by up to 35%. Hive Pro’s Uni5 Xposure Platform brings all your exposure data into a single, unified view. This streamlines workflows, eliminates redundant tasks, and gives your team the clarity needed to act decisively. Instead of wasting time correlating data across different dashboards, your team can focus on high-impact remediation activities.
True security isn’t just about preventing attacks; it’s about ensuring the business can continue to operate even when faced with a threat. This is operational resilience. A Continuous Threat Exposure Management program is designed to help you build this resilience by prioritizing vulnerabilities based on their potential impact on your specific business operations. By understanding which assets are critical to your revenue and daily functions, you can focus your defenses where they matter most. This approach shifts the conversation from technical risk to business risk, allowing you to build a stronger, more defensible organization that can withstand and recover from attacks without grinding to a halt.
Choosing a new security platform is a big deal. It’s not just about buying software; it’s about finding a partner that will fundamentally change how your team manages threats. You need a solution that fits your specific environment, addresses your biggest challenges, and makes your team’s life easier, not harder. The right Continuous Threat Exposure Management (CTEM) platform should feel like a natural extension of your team, giving you the clarity and confidence to move from a reactive stance to a proactive one.
Making this decision requires looking beyond feature lists and marketing claims. It’s about understanding the core philosophy of the platform and seeing if it aligns with your security goals. You should be asking questions like: Will this help us see our entire attack surface? Can it help us prioritize what actually matters? Does it validate that our defenses are working? Answering these questions will help you determine if a comprehensive, end-to-end solution like Hive Pro is the right fit to help you build a more resilient security program.
A solid CTEM platform should guide you through a continuous, five-step cycle: scoping, discovery, prioritization, validation, and mobilization. First, it needs to continuously discover all your digital assets—from servers to cloud instances—so you know exactly what you need to protect. Next, it must help you prioritize threats by analyzing real-time intelligence and understanding what’s most critical to your business. You can’t fix everything, so you need to fix the right things first. The platform should also provide Adversarial Exposure Validation to test if your security controls can actually withstand an attack. It’s one thing to have a firewall; it’s another to know it works against current attack techniques.
When you’re ready to decide, think beyond the initial price. Consider the total cost, including setup, integrations, and team training. It’s also smart to plan for potential challenges, like getting the new tool to work with your existing systems and helping your team adapt to new workflows. Before you commit, make a checklist of the features that are most important to your team. A great way to see if a tool is a good fit is to run a pilot program or a proof of concept. This lets you test the platform in your own environment. Finally, don’t underestimate the value of good vendor support. The right partner will offer training and help you get everything set up for success with their Uni5 Xposure Platform.
My team is already focused on vulnerability management. How is exposure management different? Think of it this way: vulnerability management gives you a long list of every crack in your foundation, while exposure management points out the specific cracks that an intruder is actively trying to get through. It’s a shift in focus from simply cataloging every potential weakness to understanding which ones pose a genuine, immediate threat to your business. Instead of just relying on a technical severity score, you start prioritizing based on real-world attacker activity.
You mentioned Breach and Attack Simulation (BAS). Is it safe to run simulated attacks on our live environment? Yes, it’s completely safe. The simulations are designed to be non-disruptive and mimic the techniques of an attacker without using any actual malicious code. It’s like running a fire drill for your security systems. The goal is to test your defenses and see how they respond in a controlled way, so you can find and fix gaps before a real adversary does, all without impacting your daily operations.
We already have several security tools. How does a unified platform like Hive Pro help instead of just adding another one to the pile? This is a common concern, and it’s a valid one. Hive Pro isn’t meant to be just another tool in a cluttered toolbox; it’s designed to be the toolbox itself. It integrates with the scanners and systems you already use, pulling all that data into one place. This eliminates the need for your team to jump between different dashboards and manually connect the dots. It simplifies their workflow and provides a single, clear picture of your risk, making everyone more efficient.
How is the threat intelligence from HiveForce Labs different from the public feeds and services we already use? Most threat feeds give you a massive stream of raw data, leaving your team to figure out what’s relevant. HiveForce Labs provides curated, actionable intelligence. Our in-house researchers analyze how attackers are currently operating and then map that information directly to the specific vulnerabilities in your environment. It’s the difference between being told it’s raining somewhere in the world versus being told to grab an umbrella before you walk out your front door.
What’s the first tangible result we can expect to see after implementing Hive Pro? The most immediate result you’ll see is clarity. That overwhelming list of thousands of vulnerabilities will be distilled into a short, manageable list of the critical few that attackers are actively exploiting. This allows your team to stop chasing every alert and focus their energy on fixing the problems that truly matter. You’ll quickly move from a state of feeling overwhelmed to one of confident, prioritized action.