Comprehensive Threat Exposure Management Platform

Cisco has announced the end-of-sale for Cisco Vulnerability Management (formerly Kenna Security), leaving security teams with a critical decision: remain on a legacy path or transform.
Yes, it is true that the Kenna Security platform will be supported until June 30th, 2028 but the platform won’t be keeping in pace with the evolving requirements of the customers while the threat landscape and tactics will continuously be evolving. This imbalance will put the security teams and leaders at a disadvantage.
This is the reason, don’t treat this as just a moment to make a lateral change with the solution you’ll use, it’s an opportunity to transform how you approach and manage risk.
When your reliable sedan reaches end-of-life, you don’t just buy another sedan from 2015. You look at what’s available now, an electric vehicle with better range, smarter safety features, and lower operating costs.
Simply replacing Kenna with another (Risk-based vulnerability management) tool, or RBVM, is like trading your old car for another “old car”. You solve the immediate problem but miss the chance to leap forward and upgrade your Vulnerability Management Program.
Focused only on network infrastructure and applications—never expanded to cloud, containers, mobile apps, or open-source components
Relied on theoretical risk scores rather than validated exposures through real attack simulations
Applied global threat data without filtering for specific industries or geographies
Failed to incorporate asset criticality based on what actually matters to your organization
Cisco Vulnerability Manager (Formerly Kenna) is not included in the 2025 Gartner Magic Quadrant for Exposure Assessment Platforms (EAP)
Businesses shouldn’t wait for the Kenna Platform to end support in June 2028 but should rather take a proactive approach in:
Eliminate vulnerability blind spots with highest CVE coverage in the industry
Industry and geography-specific threat prioritization. Focus on attacks that actually target your sector and region.
Prioritize based on asset criticality and business impact. Protect what matters most to your organization first.
Connect CVEs to specific threat actors and active campaigns. Understand who’s targeting you and how.
Real-world attack simulations evaluate security control effectiveness. Know what is truly exploitable, not just theoretically risky.
Complete visibility across networks, applications, open-source software, cloud environments, and containers.
Choose between on-prem or cloud-based on your requirements
Works with existing scanners or replaces them entirely for cost savings
Featured in the 2025 Magic Quadrant for Exposure Assessment Platform
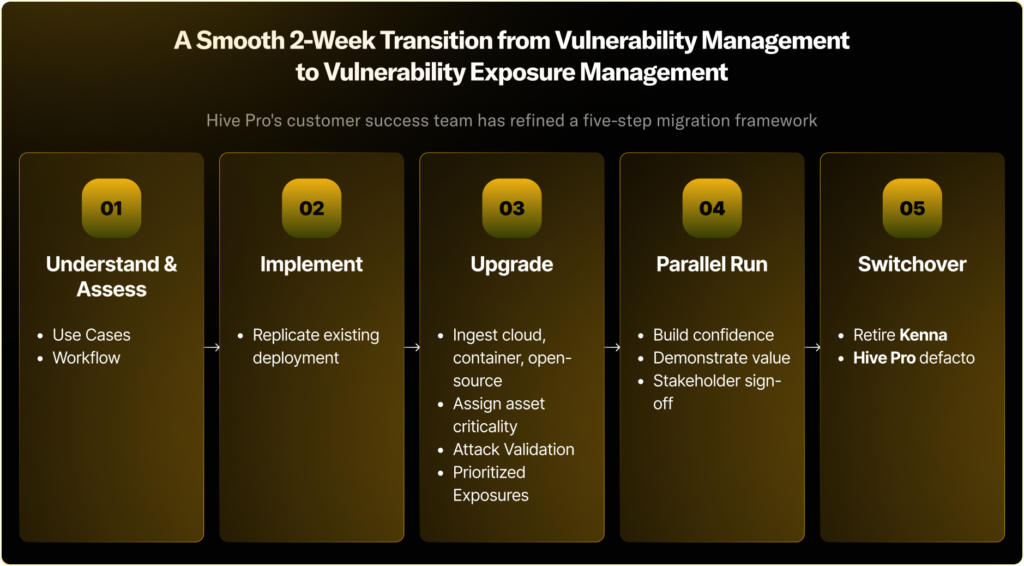
The end of Kenna isn’t a setback—it’s an opportunity! This is your signal to stop managing vulnerabilities in isolation and start holistically managing exposures.
Don’t Just Replace Kenna—Evolve to Vulnerability Exposure Management with Hive Pro
Hive Pro has helped multiple customers across the US to migrate from traditional VM tools such as Tenable, Qualys and Rapid7 to Exposure Management with Hive Pro.
Please get in touch with us to discover how Hive Pro can make the Kenna to Hive Pro journey pain-free both technically as well as commercially, we are the right partner of choice.