Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
To build a truly effective defense, you have to learn to see your organization through an attacker’s eyes. Attackers don’t care about your internal vulnerability scan reports or how many patches you applied last week. They look for one thing: an open door. They search for an accessible pathway that lets them get inside your network and cause damage. This is why clarifying the difference between vulnerability and exposure is so fundamental to modern security. A vulnerability might be a broken lock, but an exposure is the fact that the door is standing wide open on a busy street. This guide will explain this relationship and help you shift your focus from just cataloging weaknesses to actively reducing your attack surface.
Think of a vulnerability as a crack in your digital armor. It’s a specific weakness or flaw in your software, hardware, or processes that an attacker could potentially exploit to cause harm. These aren’t just abstract coding mistakes; they are tangible gaps in your defenses that represent potential entry points into your network. Understanding these weaknesses is the first step in building a security strategy that goes beyond just reacting to threats and starts proactively sealing the cracks before they can be exploited.
A vulnerability is a security weakness inherent in a system, design, or control that can be exploited by a threat actor. It’s a condition that makes a successful attack possible. For example, if a web application doesn’t properly validate user input, an attacker could inject malicious code—that’s a vulnerability. It’s important to remember that a vulnerability exists whether or not it has been discovered or exploited. It’s a latent flaw within your environment. Identifying these flaws is the core function of vulnerability management, which aims to find and catalog these potential entry points before they can be used against you.
Vulnerabilities can show up in many forms across your entire IT environment. Some of the most common examples include unpatched software or operating systems, where a known flaw has a fix available but hasn’t been applied yet. Others are weak authentication requirements, like allowing simple passwords without multi-factor authentication, which makes accounts easy to compromise. You might also find vulnerabilities in the form of software coding errors, such as SQL injection or cross-site scripting (XSS) flaws. Even an unsecured open network port can be a vulnerability, offering a direct line for an attacker to access your systems.
Once a vulnerability is discovered, it’s typically cataloged in a public database to help security teams track it. The most well-known system is the Common Vulnerabilities and Exposures (CVE) list, which assigns a unique ID to each publicly disclosed flaw. To help teams understand the severity, each vulnerability is often given a score using the Common Vulnerability Scoring System (CVSS). This score, ranging from 0 to 10, helps you prioritize remediation efforts by indicating how critical the flaw is based on factors like its exploitability and potential impact. This scoring system helps turn a long list of vulnerabilities into an actionable plan.
A single vulnerability might seem minor, but it represents a direct threat to your overall security posture. It’s a potential entry point that an attacker can use to gain a foothold in your network. From there, they can move laterally, escalate privileges, and eventually access sensitive data or disrupt operations. When a vulnerability is combined with an exposure—meaning the vulnerable system is accessible to attackers—the risk of a data breach or other security incident increases dramatically. Ignoring vulnerabilities is like leaving your digital doors and windows open; it’s not a matter of if someone will try to get in, but when.
Now that we’ve covered vulnerabilities, let’s look at exposures. While related, they aren’t the same. An exposure is any condition that makes a system accessible, creating an opportunity for an attacker to do harm. It’s the pathway they can take to find and exploit a vulnerability. Understanding your exposures means seeing your organization through an attacker’s eyes, which is the first step toward building a proactive defense that anticipates threats instead of just reacting to them.
Think of an exposure as an “open door” in your security infrastructure. It’s a condition that makes an asset accessible and therefore vulnerable to attack. This isn’t always a complex software bug; it can be a simple misconfiguration, an unprotected port, or a forgotten development server that’s still online. While a vulnerability might be the broken lock on the door, the exposure is the fact that the door was left wide open in the first place, inviting someone to find and exploit that weakness.
Exposures can appear in many forms across your digital environment. A classic example is an internet-facing server with a known critical vulnerability—the exposure is the server’s public connection, which makes the flaw accessible. Other common exposures include sensitive data stored in an unencrypted cloud bucket, an internal system an attacker can reach through a network misconfiguration, or credentials accidentally hardcoded into a public code repository. Each of these creates an opening for an attacker to get a foothold, turning a theoretical weakness into a practical threat.
Measuring exposure isn’t about a single score; it’s about gaining a complete view of your organization’s attack surface. You need to know what is accessible, how it can be reached, and by whom. This requires continuously scanning your entire environment—from on-premise servers to cloud assets—to identify potential entry points. A complete approach to total attack surface management provides the visibility to see your organization as an attacker would. By mapping all accessible assets and pathways, you can start to quantify your exposure and find the areas needing immediate attention.
Once you’ve identified your exposures, you need to assess the risk they pose. This is where context is everything. An exposed database is a problem, but an exposed database holding sensitive customer data is a crisis waiting to happen. This is why effective vulnerability and threat prioritization looks beyond just the technical severity of a flaw. It considers the business impact of the exposed asset and the likelihood of an exploit. Combining vulnerability data with exposure context helps you manage risk more effectively by focusing your team on the issues that present the most immediate danger.
Vulnerabilities and exposures are two sides of the same coin, and their relationship is what determines your actual risk level. A vulnerability on its own is a potential problem, but when it becomes exposed, it turns into an active threat vector that attackers can target. Think of it as the difference between having a flammable object in a locked, fireproof safe versus leaving it out in the open next to a lit candle. The interaction between the weakness (vulnerability) and its accessibility (exposure) is the critical point where risk truly materializes.
Understanding this dynamic is fundamental to moving beyond a simple checklist of patched vulnerabilities. It allows you to see your security landscape as an attacker would, focusing on the pathways they can actually exploit. This perspective shift helps you prioritize what truly matters, directing your resources toward the exposed weaknesses that pose the most immediate danger to your organization.
So, how do these two concepts connect in the real world? A vulnerability is a weakness, like a bug in your software code or a misconfigured server setting. An exposure is the condition that makes this vulnerability accessible to an attacker. For instance, an internet-facing server running software with a critical vulnerability is a classic example of an exposure. The weakness exists (the vulnerability), and it’s reachable from the outside (the exposure), creating a direct path for a potential attack.
Without an exposure, a vulnerability might pose a very low risk. If that same server with the flawed software was isolated on an internal, air-gapped network with no outside access, the vulnerability would still be there, but the immediate risk of external exploitation would be virtually zero. The connection is simple: an exposure is what gives a vulnerability teeth.
Your attack surface is the sum of all your exposures—every point where an unauthorized user could try to enter or extract data from your environment. This includes everything from your web applications and APIs to your physical devices and cloud assets. To effectively reduce risk, you need to manage your total attack surface by identifying and minimizing these exposures.
While vulnerability management focuses on finding and fixing specific flaws within your systems, exposure management takes a broader view. It looks at the entire landscape of what’s visible and accessible to attackers. By understanding how vulnerabilities contribute to your overall attack surface, you can better prioritize remediation efforts. You’ll focus first on the vulnerabilities that are exposed and present a clear and present danger, rather than getting lost in a sea of low-risk internal flaws.
It’s easy to use “vulnerability” and “exposure” interchangeably, but they aren’t the same thing. Let’s clear it up with a simple analogy: an unlocked door is a vulnerability. The fact that the door leads directly to a public street and is visible to anyone walking by is the exposure. Someone walking through that unlocked door without permission is the exploit.
A vulnerability is the weakness itself, while an exposure is the state that allows that weakness to be potentially exploited. You can have thousands of vulnerabilities in your environment, but if they aren’t exposed, they can’t be easily leveraged by an external attacker. This distinction is crucial because it helps you focus your security efforts on the issues that are not just theoretical problems but actual, accessible risks.
Understanding the interplay between vulnerabilities and exposures is key to building a strong, proactive security plan. A strategy that only focuses on patching every single vulnerability is inefficient and can lead to burnout. Instead, a modern approach uses vulnerability management as a component of a larger exposure management program. This allows you to prioritize threats based on real-world risk.
By first identifying your exposures, you can pinpoint which vulnerabilities need immediate attention. This risk-based approach helps you allocate your time and resources more effectively, addressing the most critical issues first. It transforms your security program from a reactive, patch-everything-you-can model to a strategic one that actively reduces your attack surface and hardens your defenses against likely attack vectors.
Understanding the difference between a vulnerability and an exposure is one thing, but putting that knowledge into practice requires a clear management strategy. For years, vulnerability management has been the standard. However, as digital environments become more complex, a broader approach—exposure management—is gaining ground. These two aren’t interchangeable; they represent different philosophies for securing your organization, each with its own methods, tools, and goals. Let’s break down how they compare and why a modern security program needs to incorporate both.
Think of vulnerability management as the process of finding and fixing known cracks in your foundation. It’s a crucial, targeted effort focused on patching specific weaknesses, like a software flaw with a CVE number. The goal is remediation. Exposure management, on the other hand, takes a step back to look at the entire blueprint of your house. It focuses on reducing your overall attack surface by identifying and addressing every possible way an attacker could get in, whether it’s through a known vulnerability, a misconfiguration, or an exposed asset you didn’t even know you had. It’s a proactive strategy aimed at minimizing opportunities for exploitation before they happen.
Because their goals are different, these two approaches rely on different toolsets. A traditional vulnerability management program typically uses vulnerability scanners to periodically check systems against a database of known flaws. It’s a bit like running a diagnostic test on a car. Exposure management requires a more comprehensive and continuous toolkit. It involves solutions for asset discovery, attack surface monitoring, and security control validation to get a complete, real-time picture of your security posture. A platform like Uni5 Xposure unifies these capabilities, giving you a single place to see and manage all potential exposures across your entire environment.
The biggest shift from vulnerability management to exposure management is the move from periodic scans to continuous assessment. Your digital environment is constantly changing—new devices connect, cloud instances are spun up, and configurations are altered. A weekly or monthly vulnerability scan can easily miss a critical exposure that appears and is exploited between scans. Continuous monitoring is the cornerstone of exposure management because it provides an always-on, attacker’s-eye view of your assets. This allows you to identify and mitigate risks as they emerge, rather than playing catch-up after a scheduled scan finally flags a problem that’s been open for days.
The most effective security programs don’t choose one approach over the other—they integrate them. Exposure management and vulnerability management work best as a team. Exposure management provides the high-level, strategic context. It helps you see your entire attack surface and understand which areas pose the most significant risk to your business. This allows for smarter vulnerability and threat prioritization. Once you’ve identified a critical exposure, vulnerability management provides the tactical workflow to remediate the specific flaws within it. By combining the big-picture view of exposure management with the focused remediation of vulnerability management, you create a much stronger, more resilient security posture.
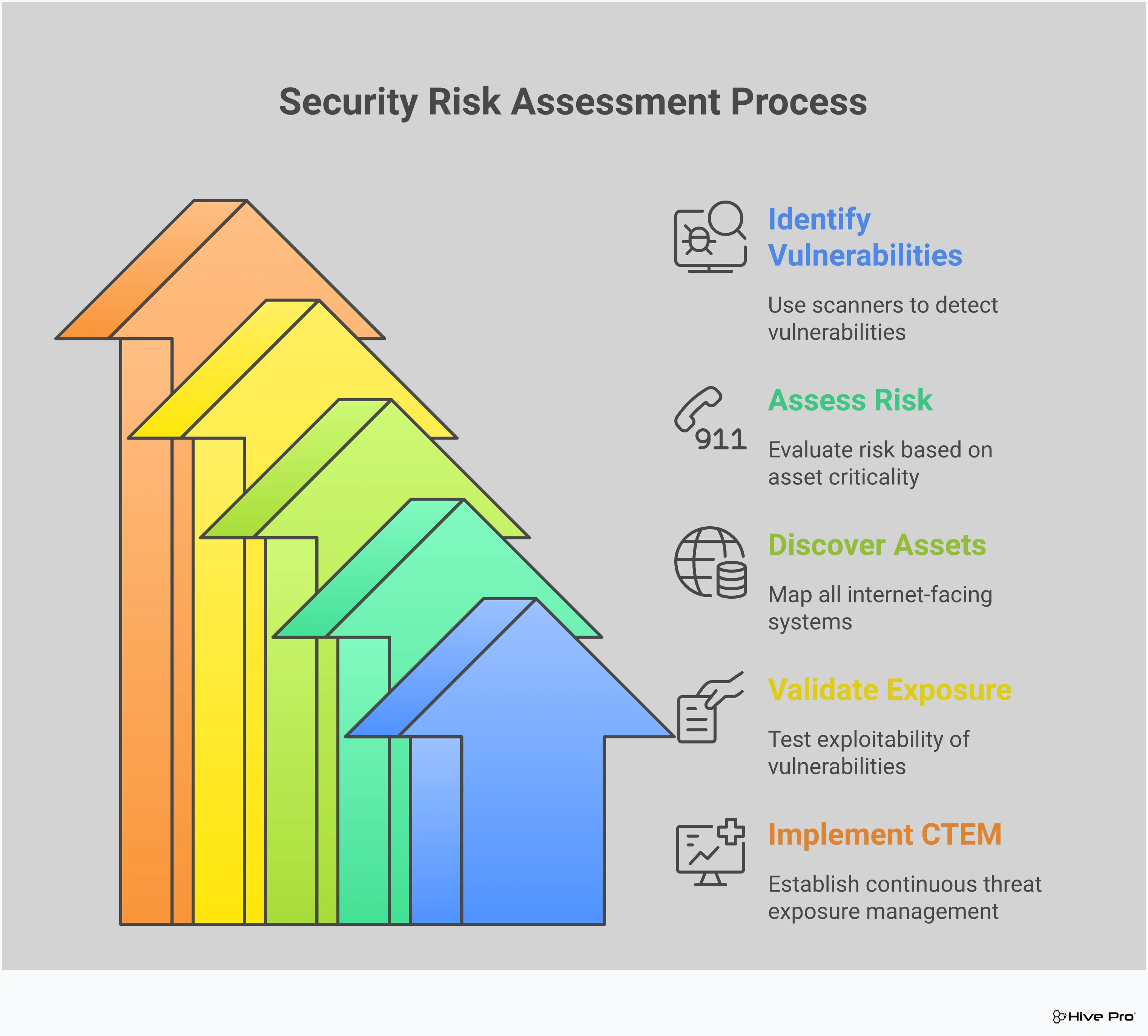
Shifting from a reactive to a proactive security posture means you stop chasing an endless list of vulnerabilities and start strategically reducing your attack surface. This requires a solid framework—a repeatable process for identifying, prioritizing, and addressing the exposures that pose a genuine threat to your organization. Think of it less as a frantic game of whack-a-mole and more as a deliberate strategy to fortify your defenses where it counts. A proactive framework helps you answer the most important questions: What are our most critical assets? Which attack paths are most likely to be exploited? And what actions will have the biggest impact on reducing our overall risk?
This approach moves beyond simply scanning for known CVEs. It integrates a deep understanding of your unique environment with real-world threat intelligence to give you a clear, contextualized view of your risk. By building a framework around exposure management, you empower your team to focus their limited time and resources on the threats that matter most. Instead of drowning in alerts, you can take confident, decisive action. A platform like Uni5 Xposure provides the foundation for this framework, unifying your view of cyber risks and guiding you from discovery to remediation.
Not all vulnerabilities are created equal. A critical CVE on a non-essential, isolated server is far less concerning than a medium-risk vulnerability on a public-facing, mission-critical application. A proactive framework starts by prioritizing risks based on their potential business impact. This means looking beyond the CVSS score and considering the context. Exposure management focuses on what is accessible and how it can be exploited, while traditional vulnerability management often stops at identifying the weakness itself. True vulnerability and threat prioritization involves mapping vulnerabilities to the assets they affect and understanding the potential blast radius if an attacker were to succeed. This allows you to focus on fixing the issues that could actually disrupt your business.
Once you’ve identified your highest-priority exposures, you need a plan to detect and respond to threats against them. This goes beyond just patching. It involves continuous monitoring of your entire attack surface to spot changes or signs of malicious activity. While traditional vulnerability management can be a tactical hunt for known flaws, a proactive framework integrates this process into a broader security strategy. By maintaining a complete inventory of your assets and understanding how they are exposed, you can implement more effective detection rules and create response playbooks tailored to your most critical risks. This ensures you’re not just finding weaknesses but are also prepared to defend them.
Prioritization and detection are only as effective as the intelligence that fuels them. Generic threat feeds can create a lot of noise, but actionable intelligence tells you which vulnerabilities are being actively exploited in the wild and by whom. Vulnerability management alone often doesn’t answer the crucial question: can this weakness actually be used by an attacker against us? By integrating insights from a dedicated research team like HiveForce Labs, you can connect global threat trends to your specific environment. This context helps you cut through the noise of thousands of “critical” vulnerabilities and focus on the handful that pose an imminent threat to your organization right now.
A proactive framework turns insights into action with a clear remediation plan. This isn’t just about creating a ticket and hoping for the best. It’s a strategic process that outlines specific steps, assigns ownership, and sets realistic timelines. Importantly, remediation in an exposure management context isn’t always about patching. Sometimes, the most effective solution is to change a firewall rule, disable a risky service, or implement a compensating control to block an attack path. The goal is to reduce the exposure as quickly and efficiently as possible. Building a strong security plan requires understanding these different remediation options and choosing the right one for each situation.
How do you know your efforts are paying off? A proactive framework includes clear metrics to measure your security effectiveness over time. Instead of just tracking the number of vulnerabilities patched, you should measure the reduction in your overall attack surface, the time it takes to remediate critical exposures, and the results of security control validation. When vulnerabilities and exposures are combined, they can lead to serious problems like data breaches. Tracking your progress in reducing these exposures provides tangible proof of risk reduction. These metrics not only help you refine your strategy but also demonstrate the value of your security program to leadership.
Moving from a reactive to a proactive security stance is about changing your fundamental approach. Instead of just chasing down and patching individual vulnerabilities as they’re discovered, you start looking at the bigger picture of what’s truly exposed to potential attackers. This shift to exposure management is the next step in building a resilient cybersecurity program. It helps you manage risk more effectively by focusing your resources on the issues that present the most immediate and significant threats to your organization, allowing you to get ahead of attackers rather than just cleaning up after them.
In a complex digital environment, you can’t rely on manual checks to keep you safe. The sheer volume of assets, applications, and potential entry points makes it impossible for any team to monitor everything by hand. This is where automation becomes essential. Using tools for continuous monitoring and scanning your entire environment is the only way to effectively manage your total attack surface. Automated threat detection works around the clock to identify anomalies, misconfigurations, and new vulnerabilities as they appear. This gives your team the ability to spot and address potential threats in real-time, moving from a state of periodic review to one of constant vigilance.
Your attack surface is not static; it changes every time a new device is added, a cloud service is configured, or an application is updated. That’s why a one-and-done security scan is no longer enough. Adopting a continuous assessment model means you have an ongoing, up-to-date view of your security posture. This approach involves constantly discovering assets, identifying vulnerabilities, and analyzing exposures across your entire IT ecosystem. A continuous threat exposure management (CTEM) platform provides this live feed, ensuring that your security decisions are always based on the most current and accurate data about your organization’s risk.
Understanding the difference between vulnerabilities and exposures is crucial for building a strong security plan. A truly strategic response moves beyond a simple patch-or-not-patch decision. It requires a clear, documented process for remediation that considers business context. This means focusing on vulnerability and threat prioritization to determine which issues pose the greatest risk to your critical operations. Your plan should outline who is responsible for remediation, establish realistic timelines, and define how progress will be tracked and communicated. This turns security data into a clear roadmap for action.
A proactive security posture is one where you are always a step ahead. It involves systematically identifying, prioritizing, and fixing known vulnerabilities while also actively managing which assets and data are exposed and accessible. This isn’t just about defense; it’s about validation. A proactive approach includes performing adversarial exposure validation to test if your security controls can withstand real-world attack scenarios. Ultimately, it means shifting your team’s focus from constant firefighting to confident, strategic risk reduction. You’ll know what your most critical risks are and have a clear plan to address them before they can be exploited.
What’s the simplest way to tell the difference between a vulnerability and an exposure? Think of it this way: a vulnerability is a weakness, like an unlocked window on the second floor of your house. An exposure is the fact that someone left a ladder leaning against the wall right under that window. The unlocked window is a problem, but the ladder makes it an immediate, accessible threat. You need to know about both to be truly secure.
We already have a vulnerability management program. Why do we need to think about exposure management too? Vulnerability management is essential, but it’s like making sure all the locks in your building work. Exposure management is like checking which doors and windows are actually visible and accessible from the street. It provides the bigger picture, helping you understand your entire attack surface so you can prioritize fixing the locks on the doors that are most likely to be tried by an intruder. The two work together to create a much stronger security strategy.
Is a high CVSS score always the most important thing to fix first? Not necessarily. While a high CVSS score indicates a severe technical flaw, context is what truly determines risk. A vulnerability with a 9.8 score on a server that’s isolated from the internet is far less urgent than a 7.5 vulnerability on a public-facing database that holds sensitive customer data. Prioritizing based on exposure and business impact helps you focus your team’s efforts on the threats that pose a real danger to your organization.
How can we start managing our attack surface without getting overwhelmed? The first step is always visibility. You can’t protect what you don’t know you have. Start by getting a complete inventory of all your assets, especially those that are connected to the internet. Understanding what is visible to an attacker is the foundation of exposure management. Once you have that map, you can begin to identify the most critical and accessible assets and focus your security efforts there first.
Can a vulnerability be a low risk if it isn’t exposed? Absolutely. A critical software flaw on a machine that is completely disconnected from all networks poses a very low immediate risk of being exploited by an external attacker. The vulnerability still exists and should be tracked, but it’s not an active threat vector. This is why understanding your exposures is so powerful—it helps you separate the theoretical problems from the actual, urgent risks.