Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
Before an attacker launches an assault, they do their homework. Their first step is to meticulously map your digital footprint, searching for the path of least resistance—an exposed database, an unpatched server, or a forgotten subdomain. The reality is that your attack surface is already being mapped; the only question is whether you’ll see it before they do. This is why cloud attack surface management mapping is so critical. It’s the discipline of proactively charting your own territory to find and close security gaps from an attacker’s perspective. By beating them to the punch, you can neutralize threats before they materialize. This guide will show you how to build this offensive-minded defense.
Think of Cloud Attack Surface Management (ASM) as the ongoing practice of seeing your organization through an attacker’s eyes. It’s a continuous process that helps your security teams identify, monitor, and secure all the digital assets connected to your cloud environment. This isn’t just about the servers and applications you know about; it’s about discovering the unknown, unmanaged, and often forgotten assets that could serve as an entry point for a threat actor.
In the cloud, your attack surface is constantly shifting. New virtual machines are spun up, containers are deployed, and developers grant new permissions—all in a matter of minutes. Without a solid ASM strategy, these changes can create blind spots where vulnerabilities can hide. The goal is to gain real-time visibility into your entire cloud footprint. This allows you to move from a reactive mode—scrambling after an attack happens—to a proactive one where you can find and fix security gaps before they can be exploited. It’s the foundational step in building a security program that can keep up with the speed of modern IT. A unified platform like Uni5 Xposure can bring all this information into a single view, making it easier to manage and transform your approach from reactive vulnerability management to proactive exposure reduction.
So, what exactly is a cloud attack surface? In simple terms, it’s the sum of all possible points where an unauthorized user could try to enter your cloud environment and extract data. Imagine your cloud infrastructure is a building. Your attack surface would be every single door, window, vent, and unlocked gate—every potential way in. The more entry points you have, the larger your attack surface is, and the more opportunities an attacker has to find a way inside. In the cloud, these entry points aren’t just servers; they include everything from misconfigured storage buckets to exposed APIs and credentials stored in code. Defining your attack surface means identifying every one of these potential access points across your entire cloud presence.
Your cloud attack surface is made up of many different components, each with its own set of potential risks. A complete inventory is essential for understanding your exposure. Key components include APIs that connect your applications, third-party services with access to your systems, and databases or storage buckets holding sensitive information. You also have to account for containers, user accounts with varying levels of permissions, and code repositories where secrets might be accidentally exposed. Each of these elements represents a different vector an attacker could use. A comprehensive approach to total attack surface management requires you to look at all these pieces together to see the full picture of your risk.
Mapping your attack surface is crucial because you can’t protect what you can’t see. It provides a detailed blueprint of your digital footprint, helping you pinpoint weaknesses before an attacker does. This visibility is the first step toward effective vulnerability and threat prioritization, allowing you to focus your security efforts on the most critical issues. When you understand your exposure, you can also improve your incident response times because you already know where your most valuable assets are. Ultimately, mapping is about shifting from a defensive crouch to a confident, proactive stance. It’s a continuous effort that helps you stay ahead of emerging threats and make informed decisions to reduce your overall risk.
To effectively manage your cloud attack surface, you need to know exactly what you’re looking at. Think of it like creating a detailed map of a city before you can plan the best security patrol routes. Your cloud environment is a sprawling digital city with different districts, each with its own unique entry points and potential vulnerabilities. Focusing on a few key areas will help you build a comprehensive and actionable map that covers your most critical assets and exposures. By breaking down your environment into these core components, you can systematically identify and address risks without getting overwhelmed by the sheer scale of the cloud.
This is the foundation of your cloud presence—the virtual land your digital city is built on. Your cloud infrastructure includes all the core components like virtual machines, containers, storage buckets, and serverless functions. It’s crucial to map every internet-facing asset, from IP addresses to cloud services, because these are your most visible and accessible entry points for attackers. A complete view of your total attack surface management starts here. Leaving even one server or storage instance unmapped is like leaving a door unlocked; it’s an open invitation for someone to walk right in. Continuous discovery is key, as new assets can be spun up and down in minutes.
If infrastructure is the land, applications are the buildings. This layer includes all the software running on your infrastructure, such as your websites, APIs, and customer-facing web applications. Weaknesses in these applications, like outdated components or flaws in online forms and shopping carts, are prime targets for attackers. Mapping this layer means identifying every application, understanding its function, and pinpointing how it communicates with other services. It’s not just about finding the apps you know about; it’s about uncovering every single one, because a forgotten, unpatched application can quickly become your biggest liability and an easy entry point for a breach.
These are the roads and highways leading into and out of your digital city. Network access points include firewalls, virtual private networks (VPNs), load balancers, and API gateways. Each one is a control point that governs who and what can enter your environment. Mapping these points helps you understand your network’s perimeter and identify any gaps in your defenses. Are your firewall rules too permissive? Is a VPN configured improperly? Answering these questions is essential for securing your network traffic. Effective vulnerability and threat prioritization helps you focus on fixing the most critical network exposures first, ensuring your resources go where they’re needed most.
IAM policies are the keys to every building in your city. This area covers user accounts, roles, permissions, and authentication methods that control who can access your cloud resources and what they can do once they’re inside. Misconfigured IAM is a massive risk, as it can lead to privilege escalation, allowing an attacker with minor access to gain control over critical systems. Mapping your IAM involves auditing user permissions, enforcing the principle of least privilege, and ensuring strong security measures like multi-factor authentication are in place. You need to know who has access to what and why, without exception.
No business operates in a vacuum, and your cloud environment is no different. Third-party integrations are the supply chains and partnerships that connect your city to others. These include SaaS platforms, APIs from vendors, and other external services that your applications rely on. While these integrations add functionality, they can also introduce new risks. A vulnerability in a third-party tool can become a vulnerability in your own system. It’s vital to map all these connections, vet your vendors’ security practices, and use adversarial exposure validation to test that these integrations don’t create unintended backdoors into your environment.
Think of cloud attack surface mapping as creating a detailed, living blueprint of your digital presence. It’s not a one-and-done project you can check off a list; it’s a continuous cycle that helps you see your organization exactly as an attacker would. The goal is to move from a reactive state—where you’re constantly putting out fires—to a proactive one where you can anticipate and neutralize threats before they cause damage. This process involves several key stages, each building on the last to give you a comprehensive and actionable view of your security posture.
By systematically discovering, classifying, and monitoring your assets, you can cut through the noise of countless alerts and focus on the vulnerabilities that truly matter. This approach transforms vulnerability management from a guessing game into a strategic, data-driven function. It’s about understanding the full context of your environment—what you own, where it is, how it’s connected, and how it could be exploited. Let’s walk through the essential steps that make up an effective cloud attack surface mapping strategy.
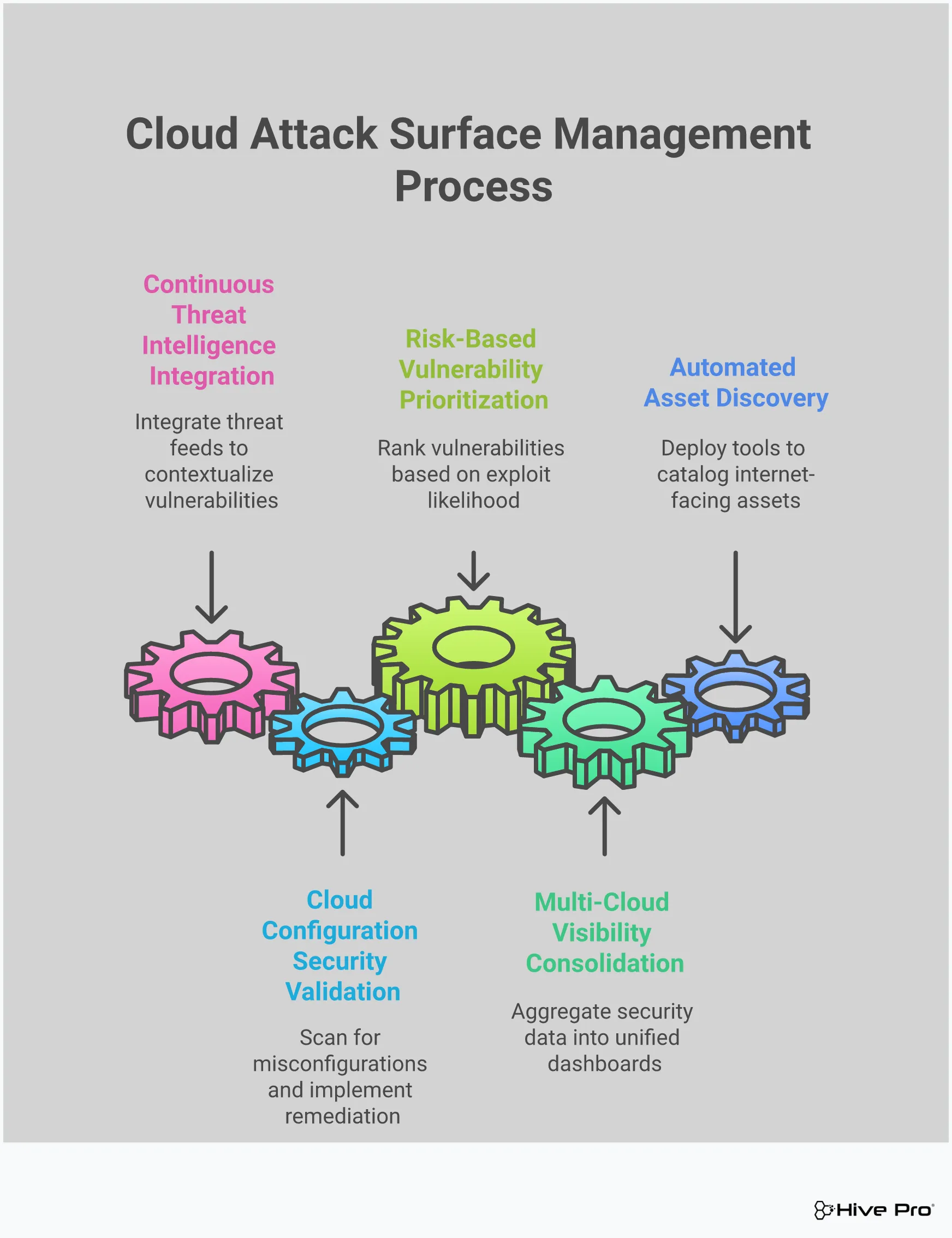
You can’t protect what you don’t know you have. The first step is a thorough discovery process to create a complete inventory of all your assets. This isn’t just about servers and laptops; it includes every piece of hardware, software, cloud instance, and API that connects to the internet. The key here is automation. A continuous scanning process automatically finds and catalogs every asset, giving you a real-time, comprehensive view of your total attack surface. This foundational inventory is the single source of truth for your entire security program, ensuring no asset is left unmanaged or unprotected.
Once you have your complete asset inventory, the next step is to make sense of it all. Not every asset carries the same level of risk. You need to classify your findings by sorting them, identifying potential weaknesses, and ranking them based on how attractive they might be to an attacker. This is where you shift from simply listing assets to understanding their strategic importance and potential impact on the business. Effective vulnerability and threat prioritization means focusing your team’s limited time and resources on the issues that pose the most significant threat, rather than getting lost in a sea of low-risk alerts.
With your assets inventoried and classified, it’s time to assess the actual risk. This step is about looking at your environment through an attacker’s eyes to uncover hidden weaknesses and unmanaged assets. A crucial part of this is identifying “Shadow IT”—the software, services, and devices employees use without official approval. These unmanaged resources create significant blind spots. Your risk assessment method should focus on uncovering these gaps and understanding the context of each vulnerability. This gives you a realistic picture of your exposure and helps you build a more resilient security posture.
Your cloud environment is constantly changing. New assets are spun up, configurations are altered, and fresh vulnerabilities are discovered every day. A static map of your attack surface becomes outdated almost immediately. That’s why continuous monitoring is non-negotiable. By constantly scanning your environment in real-time, you can detect new assets, unauthorized changes, and emerging threats as they happen. This ongoing vigilance is the core of a proactive security strategy, allowing you to adapt quickly and maintain full visibility with a platform like Uni5 Xposure.
An attack surface management platform shouldn’t replace your existing security tools—it should make them better. A common misconception is that ASM is a standalone solution. In reality, it works best as a central hub that integrates with your entire security stack, including vulnerability scanners, SIEMs, and ticketing systems. This integration provides a unified view of your cyber risks, enriching the data from other tools with crucial business context. It helps you validate your security controls and ensures your entire team is working from the same, up-to-date information, breaking down silos and improving overall efficiency.
Mapping your cloud attack surface sounds straightforward, but it comes with its own set of hurdles. The very nature of the cloud—its scale, speed, and complexity—creates challenges that can leave security teams feeling like they’re always one step behind. From assets that appear and disappear in minutes to the struggle of keeping up with compliance, these issues are common. But they aren’t insurmountable. Understanding these challenges is the first step to building a strategy that gives you a clear, continuous, and complete picture of your cloud environment.
Cloud environments are anything but static. Digital assets are constantly changing as developers spin up new instances, decommission old ones, and reconfigure services on the fly. This constant flux means that a one-time or even quarterly scan is obsolete almost as soon as it’s finished. To keep up, you need a total attack surface management approach that provides real-time visibility. Without continuous discovery, you’re operating with an incomplete map, leaving new and temporary assets exposed and unmonitored. The key is to shift from periodic snapshots to a live view of your environment.
Few organizations stick to a single cloud provider. Your teams are likely using a mix of AWS, Azure, Google Cloud, and other platforms to get the job done. While this approach offers flexibility, it creates siloed environments, each with its own security controls and dashboards. This fragmentation makes it incredibly difficult to get a single, unified view of your entire attack surface. An effective mapping strategy must be able to cut across these silos, consolidating asset information from all your cloud providers into one place. This gives you the comprehensive visibility needed to manage risk consistently across your entire digital footprint.
You can’t protect what you don’t know you have. This is a fundamental truth in cybersecurity, and it’s a major challenge in the cloud. Security teams often lack a complete inventory of all their digital assets, especially with the rise of “Shadow IT”—assets deployed by employees without official approval. Attack surface mapping is your first line of defense, helping you find hidden weaknesses, discover unmanaged assets, and get a true sense of your exposure. By illuminating these blind spots, you can begin the critical work of vulnerability and threat prioritization based on a complete and accurate asset inventory.
Meeting industry regulations and data protection laws is a non-negotiable part of doing business. Frameworks like GDPR, HIPAA, and PCI DSS require you to know exactly where your data is, who can access it, and how it’s protected. Attack surface mapping provides the foundational asset inventory needed to demonstrate compliance. It gives you a real-time view of your assets and their vulnerabilities, allowing you to prove to auditors that you have the necessary controls in place. This continuous insight helps you identify and fix potential compliance gaps before they become critical issues, keeping you ahead of the latest threat advisories.
Let’s be realistic: most security teams are stretched thin. There often aren’t enough people, hours in the day, or budget to perform thorough and continuous mapping manually. This resource gap is one of the biggest obstacles to effective cloud security. Relying on manual processes is simply not sustainable in dynamic cloud environments. This is where automation becomes a game-changer. By using a platform that automates discovery, inventory, and analysis, you empower your team to do more with less. It frees them from tedious manual tasks and allows them to focus on strategic initiatives, like adversarial exposure validation and proactive risk reduction.
Mapping your cloud attack surface isn’t something you can tackle with a spreadsheet and a few hours of manual work. Your cloud environment is constantly changing, with assets spinning up and down in minutes. To keep up, you need a dedicated toolkit that automates discovery and analysis, giving you a clear, real-time picture of your exposure. Think of it less like a static paper map and more like a dynamic GPS that reroutes you around security risks as they appear.
The right combination of tools helps you move from guessing what your attack surface looks like to knowing exactly what it is. Each tool in your kit plays a specific role, from finding your assets to identifying their weaknesses and understanding the threats targeting them. When these tools work together, they provide a unified view that cuts through the noise of countless alerts. This allows your team to focus on the vulnerabilities that truly matter and take confident, proactive steps to secure your cloud infrastructure. A comprehensive Threat Exposure Management Platform integrates these capabilities, but understanding each component is key to building a strong defense. Let’s walk through the essential tools you’ll want to have in your security arsenal.
You can’t protect what you don’t know you have. That’s where automated discovery tools come in. These are your first line of defense, continuously scanning your environment to find every connected asset—the known, the unknown, and the forgotten. As Corelight notes, effective Attack Surface Management (ASM) “requires deep network visibility” to give security teams a real-time inventory. These tools are the foundation of your map, providing the comprehensive total attack surface management needed to see every server, container, and API endpoint. Without this complete picture, you’re essentially trying to secure your environment with blinders on.
It’s a common myth that moving to the cloud means your provider handles all the security. The reality is, you’re responsible for configuring your cloud services correctly, and that’s where CSPM tools are essential. They act like a compliance officer for your cloud environment, continuously checking for misconfigurations, policy violations, and security gaps. As one expert points out, a major misconception is that cloud systems “are automatically secure.” CSPM tools help you dispel that myth by ensuring your configurations meet both internal security standards and external regulatory requirements, preventing easy entry points for attackers.
Once you’ve discovered your assets, the next step is to find their weaknesses. Vulnerability scanners are the tools for the job. They actively probe your systems, applications, and networks for known vulnerabilities, like outdated software or insecure code. This process is a core part of attack surface management, helping you “reduce the likelihood of cyber incidents” stemming from overlooked vulnerabilities. By integrating scanners into your workflow, you can systematically identify and prioritize flaws across your entire cloud environment. This allows you to focus your remediation efforts on the most critical issues with effective vulnerability and threat prioritization.
A long list of vulnerabilities isn’t very helpful without context. Which ones are actively being exploited in the wild? Which are being used by threat actors targeting your industry? Threat intelligence platforms answer these questions. They provide crucial insights into emerging threats, attacker tactics, and active campaigns, allowing you to see your vulnerabilities through the eyes of an adversary. This intelligence helps you proactively adjust your security posture instead of just reacting to alerts. By leveraging real-world data from sources like HiveForce Labs, you can prioritize the risks that pose an immediate danger to your organization.
With so many tools discovering assets and vulnerabilities, you need a single source of truth to keep everything organized. A Configuration Management Database (CMDB) serves as this central repository. It maintains a complete and accurate inventory of all your cloud assets and their configurations. As Censys highlights, a CMDB “plays a vital role in maintaining this inventory,” which is the bedrock of effective attack surface management. Think of it as the master blueprint of your cloud environment. It ensures that every team—from security to IT operations—is working from the same, up-to-date information, which is critical for coordinating your security efforts.
Once you have a map of your cloud environment, the next question is: where do you look first? Not all assets carry the same level of risk, and your team’s resources are finite. Focusing your monitoring efforts on the most critical and exposed areas allows you to manage risk more effectively. By prioritizing these key areas, you can move from a reactive stance to a proactive security posture, addressing the most likely points of attack before they can be exploited. These five areas are the perfect place to start.
Think of your public-facing assets as the digital front door to your organization. These are the servers, applications, and services that are intentionally exposed to the internet. Because they are accessible to everyone, they are also the most visible targets for attackers. As research from Censys points out, “Exposed, public-facing assets are the number one way ransomware groups get in.” Your monitoring strategy must include continuous scanning of these assets for vulnerabilities, open ports, and misconfigurations. A complete total attack surface management program gives your team the real-time visibility needed to spot and fix these exposures before an attacker finds them.
You can’t protect what you don’t know you have. Shadow IT—the hardware or software used within an organization without approval from the IT department—creates significant blind spots. As Palo Alto Networks notes, “Regular security tools often miss hidden or unknown cloud services, leaving them open to attacks.” These unknown resources, from a developer spinning up a temporary cloud server to a marketing team adopting a new SaaS tool, expand your attack surface in unpredictable ways. Effective monitoring requires discovery tools that can continuously scan your environment to uncover these unmanaged assets and bring them under the umbrella of your security program.
The flexibility of the cloud is one of its greatest strengths, but it also opens the door to human error. A simple misconfiguration, like an unsecured storage bucket or an overly permissive firewall rule, can expose sensitive data to the entire internet. These mistakes are incredibly common and are a leading cause of cloud data breaches. Your monitoring efforts should include a Cloud Security Posture Management (CSPM) approach that constantly checks your cloud services against security best practices and compliance standards. This helps you automatically detect and remediate misconfigurations, closing critical security gaps that might otherwise go unnoticed.
Modern applications rely heavily on Application Programming Interfaces (APIs) to connect services and transfer data. While essential for functionality, each API is also a potential entry point for an attacker. As security firm Wiz highlights, “Unsafe APIs are a big risk.” Many organizations struggle to even inventory all of their APIs, let alone secure them properly. Your monitoring strategy must involve discovering all internal and external APIs, analyzing them for vulnerabilities like weak authentication or improper data exposure, and ensuring they are protected. Without a clear view of your API landscape, you’re leaving a critical part of your attack surface unmonitored and vulnerable.
Not all threats come from the outside. Compromised credentials, especially for accounts with elevated permissions, can give an attacker the keys to your kingdom. That’s why monitoring identity and access management (IAM) is so crucial. This involves auditing who has access to what and ensuring principles like least-privileged access are enforced. As IBM suggests, making changes like “giving people only the access they need… or using multi-factor authentication (MFA)” is fundamental. Continuous monitoring of access logs and user permissions helps you spot suspicious activity and ensures that your vulnerability and threat prioritization efforts account for the risk associated with privileged accounts.
Moving to the cloud comes with a lot of new territory, and it’s easy for misconceptions to take root. When it comes to your attack surface, believing these myths can leave dangerous gaps in your security posture. Let’s clear up a few common misunderstandings so you can build a cloud security strategy based on facts, not fiction. Getting this right helps you focus your resources where they matter most and protect your organization from real-world threats.
This is probably the most common and dangerous myth out there. While cloud providers like AWS, Google Cloud, and Azure have incredible security teams, they operate on a shared responsibility model. They are responsible for the security of the cloud—the physical data centers, the hardware, and the core infrastructure. But you are responsible for security in the cloud. This includes your data, applications, user access, and configurations. Thinking your provider handles everything is like assuming the company that built your office building is also responsible for locking your office door at night. You need a clear understanding of your role in the shared responsibility model to secure your assets properly.
It would be great if a single tool could solve all our security problems, but that’s just not realistic. Your security stack is a team of specialized players, and each has a distinct role. Attack Surface Management (ASM) is your scout—it gives you the lay of the land and shows you what you need to protect. But it’s not designed to replace your other security software. Instead, it should complement your existing tools, like Cloud Security Posture Management (CSPM) and vulnerability scanners. A platform that provides a unified view of cyber risks brings these different data points together, helping you see the full picture without juggling a dozen different dashboards.
Mapping your attack surface is a critical first step, but it’s just that—a first step. Knowing what assets you have and where they are is essential for visibility, but visibility alone doesn’t equal security. True security comes from the actions you take based on that map. It’s about analyzing the discovered assets, identifying potential exposures, and then taking action. This means having a solid process for vulnerability and threat prioritization to focus on the most critical risks first. Mapping is the foundation, but the real work is in continuously monitoring, assessing, and remediating the exposures you find.
The idea that you need a massive team to manage your attack surface is a holdover from a time when security was a more manual process. Modern security platforms have changed the game. With the right automation, you can achieve real-time visibility into all your known, unknown, and unmanaged assets without an army of analysts. These tools do the heavy lifting of discovery and inventory, freeing up your team to focus on strategic tasks like risk analysis and remediation. Effective total attack surface management is about working smarter, not just adding more people. It makes proactive security achievable for teams of any size.
Mapping your cloud attack surface is the essential first step, but it’s what you do with that map that truly matters. A static inventory of assets won’t protect you from dynamic threats. The goal is to shift from a reactive, “whack-a-mole” approach to a proactive strategy that anticipates and neutralizes threats before they can be exploited. This means turning your map into a living, breathing part of your security program.
A proactive strategy involves more than just running scans; it requires a framework for making smart decisions, fostering collaboration across teams, and continuously refining your defenses. It’s about building a resilient security posture that can adapt as your cloud environment evolves. By focusing on prioritization, teamwork, continuous improvement, and validation, you can transform your attack surface map from a simple diagram into a powerful tool for risk reduction.
Once you have a clear picture of your assets, the next question is: what do you fix first? Not all vulnerabilities are created equal, and trying to address everything at once is a recipe for burnout. This is where a risk prioritization framework comes in. Instead of just looking at a long list of assets, you need to understand which ones pose the most significant threat to your business. Attack surface mapping provides the real-time visibility you need to see all your assets, which is the foundation for preventing attacks before they happen. By combining asset discovery with threat intelligence, you can focus your team’s efforts on the exposures that attackers are most likely to target, ensuring your most critical resources are protected first.
Cloud security isn’t just a job for the security team; it’s a shared responsibility. Developers, IT operations, and security analysts all play a role in managing the cloud attack surface. A common mistake is thinking that attack surface management tools are meant to replace other security software. Instead, they should complement your existing tools to create the most comprehensive view of your environment. This shared visibility helps break down silos and gets everyone on the same page. When your DevOps and security teams are working from the same data, it’s much easier to integrate security into the development lifecycle and fix issues efficiently, rather than pointing fingers after a breach.
Your cloud environment is constantly changing, with new assets spinning up and down every day. That’s why your approach to managing it must be a continuous process, not a one-time project. Think of it as a cycle: find, check, rank, fix, and monitor. This continuous loop ensures that your security posture keeps pace with your evolving infrastructure. By regularly reassessing your attack surface and refining your priorities, you can build a program that gets stronger over time. This approach helps you move beyond simply reacting to alerts and allows you to proactively reduce your exposure based on the latest threat intelligence and business context.
How do you know your security controls are actually working? Don’t just assume they are—validate them. Mapping your attack surface shows you what you need to protect, but you also need to test those protections against real-world attack techniques. This is where you can validate your security controls to see how they stand up to simulated attacks. Continuously tracking and securing your assets is key to reducing the likelihood of incidents that stem from overlooked vulnerabilities. By proactively testing your defenses, you can identify gaps, fine-tune your configurations, and prove to leadership that your security investments are paying off.
How is Cloud Attack Surface Management different from just running vulnerability scans? Think of it this way: a vulnerability scanner looks for weaknesses in the assets you already know about and point it to. Cloud Attack Surface Management starts a step earlier by discovering all your assets first, including forgotten servers or unmanaged cloud services. It provides the complete inventory and business context you need to understand your true exposure, helping you prioritize which vulnerabilities actually pose a real threat.
Is mapping my attack surface a one-time project or an ongoing process? It’s definitely an ongoing process. Your cloud environment changes by the minute as new services are launched and old ones are decommissioned. A map that’s even a day old is already out of date. Effective management relies on continuous, real-time monitoring to keep up with this dynamic pace, ensuring you always have a current and accurate view of your security posture.
My security team is already stretched thin. How can we realistically implement this? This is a common concern, and it’s exactly why automation is so critical. Modern attack surface management platforms are designed to handle the heavy lifting of discovery and inventory for you. Instead of dedicating your team to tedious manual tracking, the right tool automates the process. This frees up your experts to focus on the strategic work of analyzing risks and fixing the most critical issues.
Does an attack surface management platform replace my other security tools, like my CSPM? Not at all—it actually makes them more effective. An ASM platform acts as a central hub that provides crucial context to the data from your other tools. It gives you that complete asset inventory, which your Cloud Security Posture Management (CSPM) or vulnerability scanner can then use to do their jobs more thoroughly. Integrating these systems gives you a single, unified view of your risk.
With so many potential risks, where should I focus my monitoring efforts first? A great starting point is to focus on your public-facing assets. These are the digital front doors to your organization—your websites, APIs, and servers that are visible to the entire internet. Because they are the most exposed, they are often the first targets for attackers. Continuously monitoring these assets for misconfigurations and vulnerabilities gives you the biggest security return for your effort.