Comprehensive Threat Exposure Management Platform
The end-of-life announcement for Cisco Vulnerability Management (formerly Kenna Security) might feel like a disruption, but it’s actually a perfect opportunity to re-evaluate your entire security strategy. For years, teams have been stuck in a reactive cycle, chasing an endless list of CVEs with little context. Now, you have a compelling reason to break free. The search for a Cisco Vulnerability Management replacement is your chance to shift from simply managing vulnerabilities to proactively reducing your threat exposure. We’ll explore how modern platforms use real-world threat intelligence and attack simulation to help you focus on what truly matters, turning a mandatory migration into a strategic upgrade.
If your team relies on Cisco Vulnerability Management (formerly Kenna Security), you’ve probably heard the news. Cisco is officially retiring the platform, which means it’s time to start planning your next move. This isn’t just about swapping one tool for another; it’s a chance to re-evaluate your entire approach to vulnerability management and find a solution that truly fits your security needs for the years ahead. Let’s walk through what this end-of-life announcement means for you and why acting now is so important.
When a product reaches its end-of-life (EOL), it means the vendor will stop selling, supporting, and updating it after a specific date. According to Cisco’s official announcement, current users have a limited window before they’re left without vendor support, security patches, or new features. For any organization that depends on this tool for identifying and managing security risks, this is a critical deadline. Continuing to use the platform past the EOL date isn’t a viable option, so the search for a replacement needs to start sooner rather than later to ensure a smooth and secure transition.
Running unsupported software is like leaving your front door unlocked. Once the EOL date passes, Cisco will no longer release patches for new vulnerabilities discovered in the platform. Any security flaw found becomes a permanent, unfixable gap in your defenses. Attackers actively look for these kinds of unsupported systems because they represent easy targets. Without ongoing support, you also risk falling out of compliance with industry regulations and standards. This isn’t just a technical problem; it’s a business risk that can lead to data breaches, financial loss, and damage to your reputation.
The threat landscape doesn’t stand still, and your security tools shouldn’t either. This transition is the perfect opportunity to move beyond traditional vulnerability scanning, which often produces long, unmanageable lists of issues with little context. Modern security challenges require a more intelligent approach. You need a platform that can help you prioritize vulnerabilities based on real-world threat intelligence—showing you which flaws are actively being exploited in the wild. This allows your team to focus its limited time and resources on fixing the problems that pose the most immediate danger to your organization.
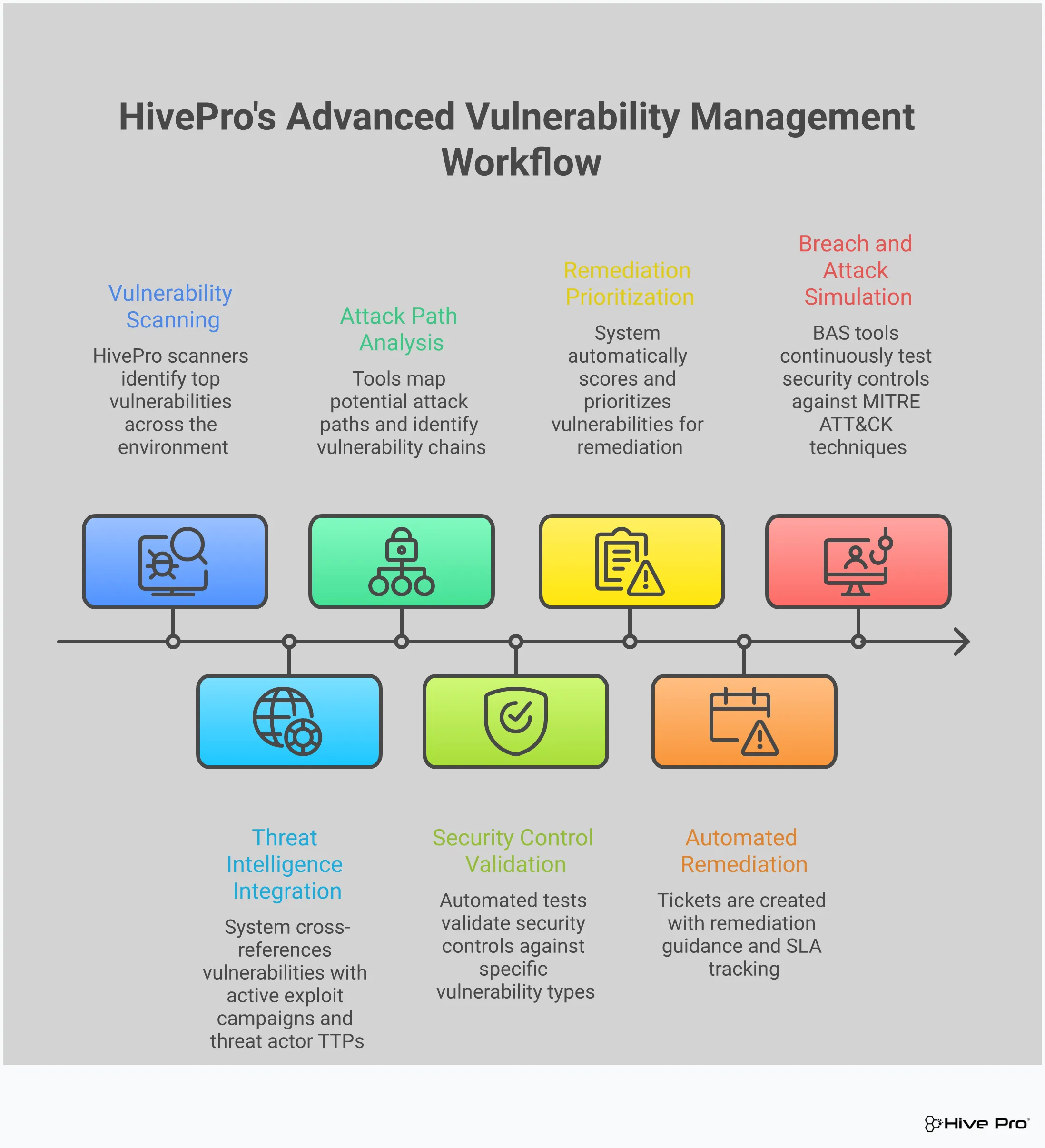
Moving on from a tool like Cisco Vulnerability Management isn’t just about finding a replacement—it’s an opportunity to rethink your entire approach. Legacy vulnerability management often feels like a reactive game of whack-a-mole, where you’re constantly chasing down an endless list of CVEs. The goal now is to shift from that reactive cycle to a proactive strategy focused on reducing your actual exposure. This means looking for a platform that helps you understand the connections between different security weaknesses and how they might create a path for an attacker.
A modern platform should give you a complete picture of your risk, not just a list of vulnerabilities. It needs to connect the dots between a software flaw, an active threat, and a potential pathway to your critical assets. As you evaluate your options, look for a solution that helps you see your security posture through an attacker’s eyes. This means moving beyond simple scanning and scoring to a more holistic, intelligence-driven approach. The right tool will help you focus your team’s limited time and resources on the threats that truly matter to your organization, turning a mountain of data into a clear, prioritized action plan.
You can’t protect what you don’t know you have. Traditional vulnerability scanners are great at finding issues on known assets, but what about the forgotten servers, shadow IT, and cloud instances that pop up without the security team’s knowledge? A solid Cisco VM alternative needs to provide comprehensive attack surface management to continuously discover and inventory every asset connected to your organization. This isn’t just about creating a list. True exposure management helps you understand how different security weaknesses connect to create bigger risks. Seeing your entire attack surface gives you the context to understand how an attacker might move through your systems, turning a low-priority vulnerability on one machine into a critical entry point to your most sensitive data.
A high CVSS score doesn’t always mean a high risk to your business. Without context, your team can waste countless hours patching vulnerabilities that no one is actively exploiting. That’s why your next platform must integrate real-world threat intelligence. This data tells you which vulnerabilities are being used in active attack campaigns, have public exploits available, or are being discussed on the dark web. By layering this intelligence over your vulnerability data, you can prioritize threats based on genuine, immediate risk. This allows your team to stop chasing every single alert and instead focus on fixing the weaknesses that attackers are most likely to target right now. It’s the difference between a noisy, overwhelming backlog and a clear, actionable remediation plan.
Finding a vulnerability is one thing; knowing if your security controls can actually stop an exploit is another. This is where Breach and Attack Simulation (BAS) comes in. Instead of just assuming your firewalls, EDR, and other security tools are working correctly, BAS lets you safely and continuously test them against real-world attack scenarios. Think of it as a fire drill for your security stack. A platform with adversarial exposure validation capabilities can show you exactly where your defenses hold up and where they fail. This proactive approach helps you find and fix gaps before an actual attacker can exploit them, giving you confidence that your security investments are delivering real protection. It replaces outdated, point-in-time scans with continuous validation.
Your vulnerability management tool shouldn’t be an island. To be effective, it needs to fit seamlessly into your existing security ecosystem. Look for a platform that offers robust, pre-built integrations with the tools your team already relies on, including SIEMs, SOAR platforms, ticketing systems like Jira or ServiceNow, and CMDBs. Strong integration capabilities create a more unified and efficient workflow. When your exposure management platform can automatically push high-priority vulnerabilities to a ticketing system or trigger a response in your SOAR, you shorten the time from detection to remediation. This breaks down silos between teams and ensures that critical risk information gets to the right people quickly, turning insights into action without manual effort.
Your business isn’t static, and your security platform shouldn’t be either. Whether you’re a growing startup or a global enterprise, you need a solution that can scale with you. This means it should be able to handle an ever-increasing number of assets across on-prem, cloud, and hybrid environments without a drop in performance. The right platform should also be flexible enough to support your security program as it matures. It should provide value whether you’re just getting started with vulnerability management or running a sophisticated, multi-faceted security operation. As your organization evolves through growth, mergers, or acquisitions, your chosen solution needs to adapt effortlessly, ensuring your security posture remains strong and consistent.
With Cisco Vulnerability Management (formerly Kenna Security) heading for retirement, you have a great opportunity to re-evaluate your needs and find a platform that truly fits your security program. The market is full of strong contenders, each with a unique approach to managing threats and vulnerabilities. Instead of just finding a one-to-one replacement, think about what your ideal solution looks like. Do you need a more unified view of your attack surface? Better threat intelligence? Or the ability to test your controls against real-world attacks?
To help you get started, we’ve rounded up five top-rated alternatives. We’ll look at what makes each platform stand out, from comprehensive exposure management systems to scanner-agnostic tools that fit right into your existing stack. This isn’t just about filling a gap left by Cisco; it’s about finding a partner that can help you build a more proactive and resilient security posture for the future.
If you’re looking for a platform that moves beyond traditional vulnerability management, the Hive Pro Uni5 Xposure Platform is built for proactive threat exposure management. It provides a unified view of your entire attack surface, helping you see and manage cyber risks from a single dashboard. What sets it apart is the integration of in-house threat intelligence from HiveForce Labs, which helps you prioritize vulnerabilities based on which ones are actively being exploited in the wild. This focus on imminent threats means your team can stop chasing every single vulnerability and concentrate on fixing what matters most. It’s a complete suite designed to guide you from discovery and prioritization all the way through remediation.
Tenable One is an exposure management platform designed to give you a unified view of your entire attack surface, from IT infrastructure to cloud environments and web apps. It moves beyond traditional vulnerability scanning by contextualizing cyber risk, so you can see how vulnerabilities connect and create attack paths. Tenable emphasizes its “end-to-end unified exposure management,” providing a clear path forward for risk management. With over 300 integrations, it’s built to connect with the security tools you already use, making it easier to get a comprehensive picture of your security posture. This approach helps teams understand risk in a broader context and prioritize their efforts more effectively.
For teams that loved Kenna’s flexibility, ArmorCode presents itself as a modern, “scanner-agnostic” platform. This means it’s designed to work with all your existing security tools, so you aren’t locked into a single vendor’s ecosystem. ArmorCode can pull in and correlate data from over 325 different security and developer tools, giving you a centralized place to manage vulnerabilities and prioritize remediation. This flexibility is a major draw for organizations that have already invested in a diverse set of scanning tools. By unifying findings from various sources, it helps streamline workflows and gives security teams a single source of truth for their vulnerability management program.
Qualys VMDR (Vulnerability Management, Detection, and Response) encourages organizations to adopt a more proactive approach to cyber risk. The platform introduces the concept of a Risk Operations Center (ROC), a framework designed to unify security, IT, and risk management teams. By creating a shared language of verified risk reduction, Qualys aims to break down silos and foster better collaboration. This focus on a unified strategy helps ensure everyone is working toward the same goal: reducing the organization’s overall exposure. It’s a solution for teams looking to build a more integrated and strategic risk management program that goes beyond just scanning and patching vulnerabilities.
Rapid7 InsightVM is a well-established player in the vulnerability management space, known for its powerful scanning and risk prioritization capabilities. It helps you automatically collect data from across your entire environment—from endpoints to cloud services—to identify vulnerabilities and assess risk. InsightVM uses real-time threat intelligence to score vulnerabilities, helping you focus on the ones that pose the greatest threat to your organization. It also provides clear remediation guidance and integrates with ticketing and automation tools to streamline your patching process. For teams looking for a robust, proven solution to discover, prioritize, and remediate vulnerabilities, InsightVM remains a solid choice.
When you start looking at replacements for Cisco Vulnerability Management, you’ll notice they all promise to find and prioritize your security risks. But how they get there can be very different. The best platform for you depends on your specific needs, your existing security stack, and the maturity of your program. Instead of just comparing feature lists, let’s look at how the top contenders handle the core jobs of a modern threat exposure management program. This will help you see beyond the marketing and understand which solution truly fits your workflow. We’ll focus on four key areas: how they see your attack surface, how they prioritize what to fix, how they use threat intelligence, and how they help you actually get things fixed.
Your attack surface is everything a potential attacker could target. It’s no longer just the servers in your data center; it includes cloud instances, web apps, employee laptops, and IoT devices. A solid Cisco VM alternative needs to give you a complete and continuous view of all of it. Platforms like Tenable One have shifted the conversation toward “exposure management,” which recognizes that risk is about more than just a CVE score on a server. It’s about understanding the entire landscape. The goal is to find a tool that provides a unified view, so you’re not trying to piece together data from a dozen different scanners. A platform that offers Total Attack Surface Management can help you discover both known and unknown assets, giving you a single source of truth for what you need to protect.
If your team is drowning in a sea of “critical” vulnerabilities, you know that CVSS scores alone aren’t enough. Modern platforms move beyond this static scoring by adding real-world context. They ask more important questions: Is this vulnerability being actively exploited in the wild? Is it on a critical, internet-facing asset? Could it be chained with other weaknesses to create a path to your crown jewels? This context-driven approach is key to reducing alert fatigue and focusing your team on the fixes that matter. Understanding how different security issues connect is what separates a basic vulnerability scanner from a true exposure management platform. This is where a solution that provides deep Vulnerability & Threat Prioritization becomes essential, helping you cut through the noise.
Effective prioritization depends on high-quality, timely threat intelligence. Your platform needs to pull in data from multiple sources—open-source feeds, commercial providers, and government agencies—to understand which vulnerabilities are being targeted right now. While some platforms boast hundreds of integrations, the real value comes from how that data is operationalized. The platform should automatically correlate threat data with the vulnerabilities found on your assets. This is what turns a long list of CVEs into a short, actionable list of immediate risks. Many platforms also provide their own curated intelligence from in-house research teams, like the insights from HiveForce Labs, which can give you an edge by highlighting emerging threats before they become widespread.
Finding and prioritizing vulnerabilities is only the first step; you still have to fix them. The best platforms bridge the gap between security and IT or DevOps teams by providing clear, automated remediation guidance. Some modern tools, like ArmorCode, are “scanner-agnostic,” meaning they can ingest data from your existing tools and use AI to group similar issues and suggest fixes. This streamlines the handoff process and reduces manual work. Look for a solution that integrates with your ticketing and IT management systems, like Jira or ServiceNow, to automatically create tickets with all the necessary context. This ensures the right person gets the right information to fix the problem quickly, closing the loop and measurably reducing your risk.
If your vulnerability management program feels like a never-ending game of whack-a-mole, you’re not alone. Traditional scanners can generate an overwhelming number of alerts, leaving your team struggling to figure out where to even begin. Most of these alerts are just noise—vulnerabilities that are technically present but pose little to no real-world risk to your organization. This is where threat intelligence changes the game. It’s the difference between knowing you have a thousand unlocked doors and knowing which specific door a burglar is actively trying to pick.
Integrating threat intelligence into your vulnerability management platform provides the context you need to see which threats actually matter. Instead of relying solely on a static CVSS score, you can see which vulnerabilities are being actively exploited in the wild, which are being used by threat actors targeting your industry, and which are part of a known attack chain. This allows you to shift from a reactive, compliance-driven approach to a proactive, risk-based strategy. You can finally stop chasing every single alert and start focusing your team’s limited time and resources on the vulnerabilities that represent a clear and present danger. This is the core of modern vulnerability and threat prioritization. It transforms your vulnerability data from a long list of problems into a clear, actionable roadmap for reducing your actual exposure.
A vulnerability’s theoretical severity score doesn’t tell the whole story. What truly matters is whether attackers are actually using it. By leveraging real-world data on active exploits, you can understand the current threat landscape and make informed decisions about which vulnerabilities to address first. This intelligence isn’t guesswork; it’s gathered from a wide range of sources, including dark web chatter, honeypots, and dedicated security research teams like HiveForce Labs. Knowing that a specific CVE has a readily available exploit kit or is being used in active ransomware campaigns instantly elevates its priority, allowing you to fix the most dangerous issues before they can be used against you.
Effective prioritization goes beyond just knowing a vulnerability is being exploited. It’s about understanding the bigger picture. Threat intelligence helps you connect the dots between a specific vulnerability and the tactics, techniques, and procedures (TTPs) of known threat actors. This allows you to prioritize vulnerabilities based on the most current threats and their potential impact on your specific environment. For example, if a threat group known for targeting the financial sector is exploiting a particular flaw, banks and investment firms should treat that vulnerability with extreme urgency. This approach replaces outdated, point-in-time scans with a continuous, context-aware view of your risk, informed by up-to-date threat advisories.
Let’s be realistic: no security team has the resources to fix every single vulnerability. The goal isn’t to patch everything; it’s to patch what matters. By focusing remediation on the issues that pose the highest risk, you can allocate your resources more effectively and make a measurable impact on your security posture. Threat intelligence is the key that enables this focus. It cuts through the noise of low-risk alerts and shines a spotlight on the critical exposures that demand immediate attention. This targeted approach not only reduces your risk of a breach but also prevents your security and IT teams from burning out on an endless list of low-priority tasks.
Finding vulnerabilities is just the first step. The real question is, can any of them actually be exploited in your environment? Traditional vulnerability scanners give you a list of potential weaknesses, but they don’t show you the full picture. They can’t tell you if an attacker could chain together multiple low-level vulnerabilities to create a critical attack path, or if your existing security controls would stop them in their tracks. This is where you need to think like an attacker.
Breach and Attack Simulation (BAS) moves you from a passive, list-based approach to an active, evidence-based one. Instead of just wondering if a vulnerability is a real threat, BAS tools safely simulate real-world attack techniques to test your defenses. This gives you concrete proof of where your security controls are working and, more importantly, where they aren’t. By running these simulations, you can validate your security posture against the same tactics that threat actors are using right now. This process of adversarial exposure validation is essential for understanding your true risk.
Legacy vulnerability management tools are great at generating long lists of CVEs, but they often lack context. They show you isolated problems without explaining how they might be connected or exploited by an attacker. A critical vulnerability on a server might seem like a top priority, but if it’s isolated and protected by a properly configured firewall, the actual risk could be low. Conversely, a medium-severity flaw on a public-facing web server could be the entry point an attacker needs. BAS helps you see these attack paths and understand how different weaknesses create larger risks, allowing you to focus on what truly matters.
You’ve invested heavily in firewalls, endpoint detection, and other security tools. But are they configured correctly? Are they actually effective against modern threats? BAS helps you answer these questions with confidence. By running simulated attacks based on frameworks like MITRE ATT&CK, you can test whether your security stack performs as expected. This validation process shows you exactly how your defenses hold up against specific attack techniques. It helps you find misconfigurations, policy gaps, and other weaknesses before a real attacker does, turning your security program from a guessing game into a data-driven operation.
Your environment is constantly changing—new assets are added, software is updated, and configurations are tweaked. A one-time security assessment quickly becomes outdated. Effective security requires continuous monitoring, not just point-in-time scans. Integrating BAS into your workflow creates a continuous feedback loop. You can automatically and regularly test your defenses, measure your security posture over time, and get clear guidance on where to make improvements. This proactive approach helps you stay ahead of emerging threats and build a stronger, more resilient security culture that involves everyone from the security team to the front lines.
Switching your vulnerability management platform is a big move. It’s more than just swapping out one piece of software for another; it’s a project that touches your data, your team’s daily routines, and your budget. Let’s be honest, migrations can be tough. But anticipating the common roadblocks is the best way to ensure a smooth transition from Cisco VM to a modern threat exposure management platform.
Thinking through these challenges ahead of time isn’t just about avoiding problems—it’s about setting your team up for success with a tool that truly strengthens your security posture from day one. Let’s walk through the four biggest hurdles you’re likely to face and talk about how to clear them without losing momentum.
This is often the first technical headache. Moving years of vulnerability data, asset information, and scan histories from one platform to another requires careful planning. The last thing you want is to lose historical context or introduce errors that corrupt your data. The key is to conduct continuous data verification throughout the process, not just at the end. Before you even start, take the time to thoroughly assess your source data to spot any potential issues. Beyond the data itself, think about integration. Your new platform needs to connect seamlessly with your existing security stack—your SIEM, ticketing systems, and other tools—to avoid creating new information silos and manual work for your team.
A new tool is only as good as the team using it. If your people are resistant to change or don’t understand the value, adoption will stall. This is less about technology and more about people. Effective vulnerability management is about building a culture of security that involves everyone, not just the security team. Start communicating early and often about why the change is happening and what benefits it will bring to different teams. Schedule hands-on training sessions and create quick-reference guides. When people understand how the new platform makes their jobs easier and the organization safer, they’re much more likely to embrace it.
Let’s be realistic: budget and time are always tight. In fact, research shows that budget constraints are one of the biggest barriers to improving vulnerability management programs. To get the resources you need, you have to build a strong business case that clearly outlines the ROI. This isn’t just about the cost of the new license; it’s about the cost of not upgrading—like the risk of a breach from an unpatched vulnerability that your old tool missed. When it comes to timelines, resist the pressure for a “big bang” rollout. A phased approach, where you migrate business units or asset groups one at a time, is much more manageable and reduces risk.
You can’t just hit pause on your security operations to implement a new tool. The challenge is to manage the migration without dropping the ball on your daily responsibilities. Many teams are already slowed down by overly complex security stacks with too many point solutions. Use this migration as an opportunity to simplify and streamline. Designate a dedicated project lead or a small team to own the transition. This ensures someone is focused on the migration plan, while the rest of the team can continue their critical work. Planning the cutover during a less critical period and having a solid rollback plan in place will also help you avoid workflow disruptions.
With the end-of-life timeline for Cisco Vulnerability Management set, it’s time to map out your transition. A well-structured plan will help you avoid security gaps and ensure a smooth switch to a new platform. Instead of a simple one-for-one replacement, treat this as an opportunity to strengthen your security posture. Breaking the process down into clear, manageable phases will make the entire migration feel less overwhelming and set your team up for success.
Start by taking a close look at your current vulnerability management program. What’s working well with Cisco VM, and where are the gaps? Talk to your team to understand their daily workflows, pain points, and what they need to be more effective. This is your chance to move beyond traditional vulnerability scanning and adopt a more proactive approach. Consider what a modern threat exposure management platform could offer, such as a unified view of your entire attack surface, better prioritization, and clearer remediation guidance. Document these requirements to create a clear picture of what your ideal solution looks like.
Once you know what you need, you can start evaluating potential replacements. Create a detailed checklist to compare vendors objectively. Key criteria should include the platform’s ability to see your full attack surface, its integration capabilities with your existing security stack, and how it uses threat intelligence to prioritize risks. Ask vendors how their platform handles data from your existing scanners—a “scanner-agnostic” approach can make the transition much smoother. You’ll also want to confirm that the solution can scale with your organization as your attack surface grows and new threats emerge.
A big-bang approach to migration is risky. Instead, plan a phased rollout to minimize disruption and ensure everything works as expected. Start with a pilot program involving a small, dedicated group of users who can test the new platform’s core features in a controlled environment. This is the perfect time to validate your security controls and test integrations with your other tools. Once the pilot group gives the green light, you can begin rolling out the platform to the rest of the organization, department by department. This methodical approach allows you to gather feedback, make adjustments, and provide targeted training along the way.
Switching your vulnerability management platform involves more than just swapping out a piece of software; it’s a strategic investment in your security program. As you plan your budget, think about this transition as an opportunity to solve bigger challenges and strengthen your overall security posture. The right platform won’t just replace old features—it will introduce new capabilities that make your team more efficient and your organization more secure. This shift requires a clear understanding of how different platforms are priced and how you can measure the value they bring back to your business.
When you start evaluating alternatives, you’ll find that licensing models can vary quite a bit. Some are based on the number of assets you scan, while others might be priced by user seats or feature tiers. Instead of just looking for a one-to-one replacement, consider this a chance to find a platform that better fits your workflow. Look for solutions that offer a unified view of cyber risks and can integrate seamlessly with the security tools you already use. A platform with extensive integrations can streamline your operations, reduce manual work for your team, and ultimately provide more value than a siloed tool that doesn’t communicate with the rest of your stack.
To build a strong business case, you need to look beyond the sticker price and focus on the return on investment (ROI). Many security teams struggle with common vulnerability management challenges like poor collaboration, tool integration headaches, and the sheer volume of alerts. A modern platform delivers ROI by directly addressing these issues, saving your team time and focusing their efforts on the threats that matter most. Remember to plan your procurement timeline carefully. You’ll need to have new service contracts in place before the final Cisco end-of-life date to avoid any gaps in coverage. Staying with an unsupported tool means you’ll miss out on critical updates and support for new standards, leaving you a step behind attackers.
The post talks about moving from “vulnerability management” to “threat exposure management.” What’s the real difference? Think of it this way: traditional vulnerability management gives you a long list of individual problems, like a leaky faucet or a drafty window in a house. Threat exposure management shows you how a burglar could get in by climbing through that window, using a tool they found under the porch to jimmy the back door, and then accessing the safe. It connects the dots between different weaknesses to show you the actual paths an attacker could take, helping you fix the routes that lead to your most important assets first.
How does Breach and Attack Simulation (BAS) actually help if I’m already scanning for vulnerabilities? Vulnerability scanning tells you what’s broken, while BAS tells you if it matters. A scan might find a weak lock on a door, but a BAS will actually try to open it. It safely mimics real attacker behaviors to test if your security controls—like your firewall or endpoint protection—would actually stop an attack. This gives you proof that your defenses are working as expected and shows you exactly where the gaps are before a real attacker finds them.
My team is overwhelmed with alerts. How does threat intelligence practically reduce that noise? Threat intelligence acts as a filter for all that noise. Instead of just seeing a “critical” vulnerability based on a generic score, it adds real-world context. It tells you if that specific vulnerability is being used in active ransomware campaigns, if exploit code is publicly available, or if threat actors are targeting your industry with it. This allows your team to immediately focus on the handful of issues that pose a clear and present danger, rather than wasting time on thousands of theoretical risks.
What’s the single most important first step I should take when planning my migration away from Cisco VM? Before you even look at demos, sit down with your team and map out what you truly need. Go beyond just replacing the features you had with Cisco VM. Ask your security and IT teams about their biggest daily frustrations and what would make their jobs easier. Documenting these needs—from better reporting to smoother integrations with your ticketing system—will give you a clear scorecard to evaluate new vendors and ensure you choose a platform that solves your actual problems.
You mentioned “scanner-agnostic” platforms. Why is that an important feature to look for? A scanner-agnostic platform can pull in and make sense of data from all the different security tools you already use. Many organizations have a mix of scanners for their network, cloud environments, and applications. Instead of forcing you to rip and replace everything, a scanner-agnostic tool unifies all those findings in one place. This gives you a single, comprehensive view of your risk without locking you into one vendor’s ecosystem, which provides a lot more flexibility as your security stack evolves.