Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Your vulnerability management backlog is probably overflowing. With thousands of new CVEs disclosed every year, it’s impossible to patch everything, and trying to do so leads to burnout and wasted effort. The CISA KEV catalog is the answer to this overwhelming noise. It’s not just another list of potential threats; it’s a curated, evidence-based guide to the vulnerabilities attackers are actively using in the wild right now. By focusing your team’s limited time and resources on this list, you shift from a reactive cycle of chasing alerts to a proactive strategy of neutralizing proven threats. This guide will show you how to build a repeatable process around this critical intelligence, preparing you for today’s attacks and whatever the cisa known exploited vulnerabilities may 2025 list brings.
Think of the CISA Known Exploited Vulnerabilities (KEV) catalog as your team’s ultimate cheat sheet for prioritization. In a world of endless vulnerability alerts, it’s easy to get overwhelmed. The KEV catalog cuts through the noise by listing only the vulnerabilities that attackers are actually using in the wild. It’s not a theoretical list of what could be dangerous; it’s a practical, evidence-based list of what is dangerous right now.
This resource is managed by the Cybersecurity and Infrastructure Security Agency (CISA) and serves as a critical tool for any organization looking to sharpen its vulnerability management strategy. Instead of chasing every single CVE that pops up, you can focus your efforts on the threats that pose a clear and present danger. For federal agencies, following the KEV catalog is a requirement, but for everyone else, it’s simply a smart, efficient way to reduce your attack surface and protect your assets from real-world attacks. By aligning your patching schedule with the KEV list, you’re directly addressing the tactics used by active threat actors, making your security posture much stronger.
A vulnerability doesn’t land in the KEV catalog just because it has a high CVSS score. The single most important criterion is reliable evidence of active exploitation. CISA’s team works with partners in the cybersecurity community to confirm that a specific vulnerability is being used in an attack. This is what makes the catalog so powerful. It was created to help network defenders and security teams better manage vulnerabilities by shifting the focus from theoretical risk to proven threats. This means you can trust that every entry on the list represents an immediate risk that deserves your attention.
Each entry in the KEV catalog gives you the essential information you need to act quickly. You won’t have to dig through dense reports to find what matters. A typical entry includes the CVE ID, the vendor or project affected, the specific product, and a brief description of the vulnerability. Most importantly, it provides the date the vulnerability was added to the catalog, the required action you need to take, and a firm due date for remediation. This clear, concise format helps your team understand the problem and the required solution without any guesswork.
For Federal Civilian Executive Branch (FCEB) agencies, adhering to the KEV catalog is mandatory under Binding Operational Directive (BOD) 22-01. This directive requires them to remediate all listed vulnerabilities by the specified due dates. While this mandate doesn’t apply directly to private organizations, it has set a new standard for the entire industry. Following these deadlines is a powerful best practice that demonstrates a commitment to proactive security. Integrating KEV data into your vulnerability management tools can help you prioritize vulnerabilities and ensure you’re addressing the most critical threats in a timely manner.
With thousands of new vulnerabilities disclosed every year, it’s impossible to patch everything. Your team is likely drowning in alerts, making it difficult to know where to even begin. The CISA KEV catalog cuts through that noise by giving you a curated, high-priority list of threats that deserve your immediate attention. Think of it less as another security feed and more as a strategic tool to guide your defense. Instead of spending cycles debating the potential impact of a vulnerability based on its CVSS score, you can work from a list of what attackers are actively using in the wild. This shift helps you move from a reactive cycle of constant patching to a proactive strategy focused on reducing your most significant exposures. Using the KEV catalog helps your team work smarter, not harder, by focusing finite resources on the issues that pose a clear and present danger to your organization. It provides a common ground for security, IT, and operations teams to agree on priorities and take decisive action.
The single biggest advantage of the KEV catalog is that it lists vulnerabilities with confirmed, active exploits. It’s not a theoretical list based on CVSS scores; it’s a practical guide to the threats that are causing real-world damage right now. This allows your team to prioritize vulnerabilities and threats based on what attackers are actually doing, not just what they could do. By concentrating on these proven risks, you can allocate your team’s time and resources to the fixes that will have the most immediate impact on your security posture. It helps answer the critical question every security team faces: “Of the hundreds of vulnerabilities we have, which ones do we fix first?”
When you know which vulnerabilities are being actively exploited, you can direct your remediation efforts with precision. This helps your team escape the cycle of “patch fatigue,” where the sheer volume of alerts makes it difficult to get meaningful work done. The KEV catalog provides a clear, actionable list that helps you focus on the patches that matter most. Instead of spreading your resources thin trying to address every medium-to-high severity finding, you can concentrate on sealing the entry points that attackers are currently targeting. This focused approach ensures your efforts directly reduce the likelihood of a breach and demonstrate clear progress in strengthening your defenses.
A KEV entry is more than just a CVE number; it’s confirmation that a vulnerability has been weaponized. This real-world context is incredibly valuable for making informed decisions and communicating urgency across the organization. It’s one thing to tell your IT team they need to patch a system because of a high severity score. It’s far more compelling to say they need to patch it because attackers are using it to compromise other companies today. This context, backed by intelligence from teams like HiveForce Labs, helps you get the buy-in you need for rapid remediation, turning abstract risks into tangible threats that everyone understands.
The KEV catalog isn’t just another long list of CVEs. It’s a highly curated, action-oriented resource that tells you exactly which vulnerabilities are being used in real-world attacks. This focus helps you cut through the noise of thousands of newly discovered flaws each month. The catalog covers a wide range of technologies and, more importantly, gives you a clear timeline for action. Understanding what’s included and how quickly you need to respond is the first step in building an effective defense around this critical intelligence.
The KEV catalog’s strength lies in its broad scope. It doesn’t just focus on one type of technology; it includes vulnerabilities across your entire IT ecosystem. You’ll find entries for everything from common operating systems and web browsers to enterprise applications, network devices, and cloud infrastructure. This makes it a critical resource for prioritizing your vulnerability management efforts, no matter what your tech stack looks like. By mapping KEV entries to your environment, you can see exactly how these active threats relate to your organization’s total attack surface. It shifts the focus from a theoretical risk to a tangible threat that requires immediate attention within your specific systems.
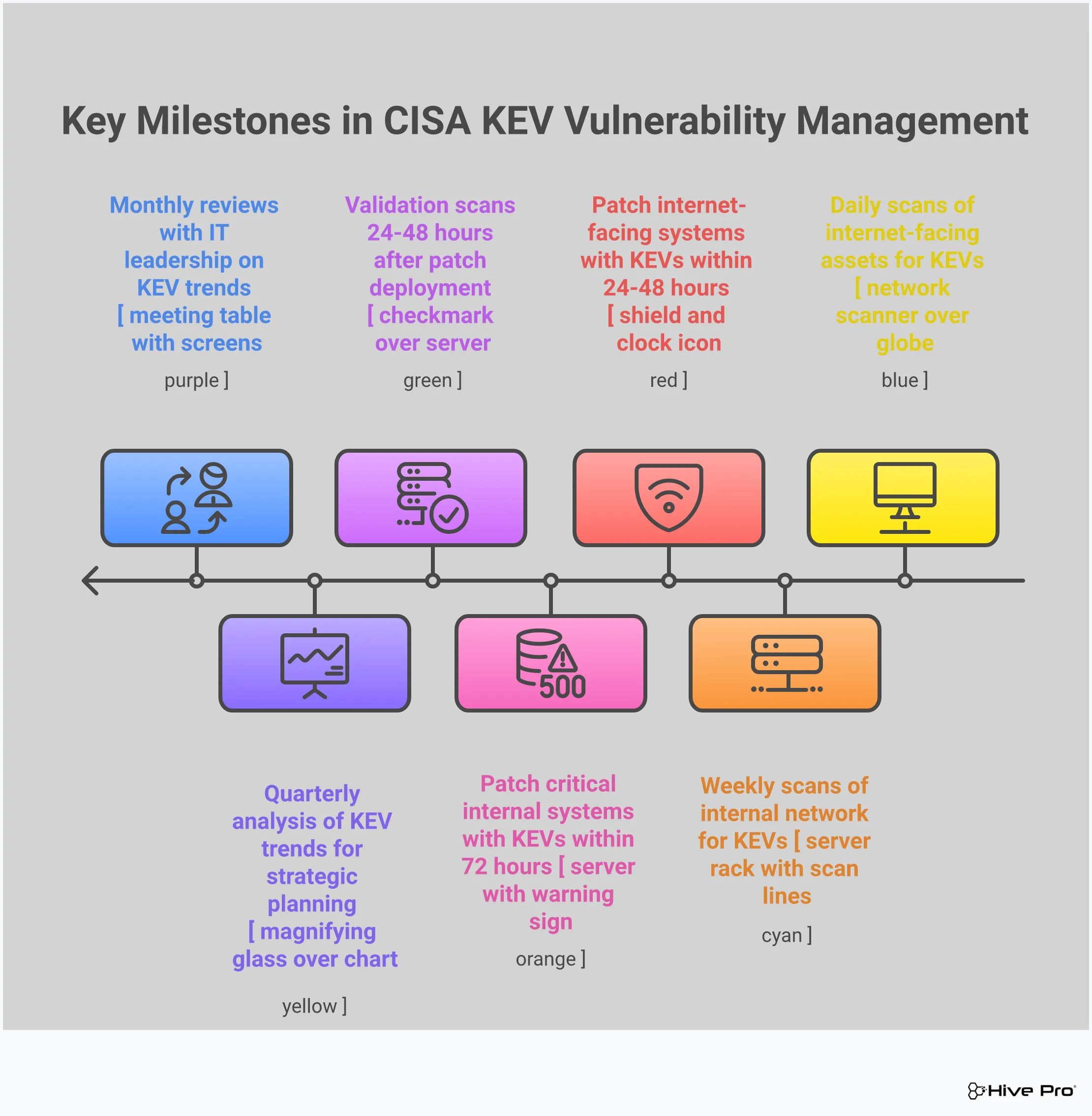
Every vulnerability added to the KEV catalog comes with a strict remediation deadline. For federal agencies, these due dates are mandatory. For everyone else, they serve as a powerful benchmark for how quickly you should act. These timelines are often short—sometimes just a week or two—reflecting the urgency of the threat. This powerful addition allows you to align with federal security standards and focus remediation efforts where they matter most: on threats that attackers are weaponizing right now. Following these deadlines helps your team adopt a more proactive security posture, ensuring you address the most dangerous vulnerabilities before they can be exploited in your environment. This is the core of effective vulnerability and threat prioritization.
Knowing which vulnerabilities are being actively exploited is one thing; knowing what to do about them is another. Simply having access to the KEV catalog isn’t enough. To truly reduce your risk, you need a clear, repeatable process for finding, prioritizing, and fixing these critical threats. A solid response strategy turns the KEV catalog from an informative list into a proactive defense mechanism. It ensures your team isn’t just reacting to fires but is systematically reducing your attack surface before attackers can find a foothold. Building this strategy involves four key steps: setting up your monitoring, assessing your unique risk, planning your remediation, and validating your fixes.
You can’t fix what you don’t know you have. The first step is to establish a robust monitoring system that continuously checks your environment against the CISA KEV catalog. This proactive approach allows for timely detection and response. Instead of waiting for a manual review or an annual pen test, you need automated tools that provide a complete picture of your total attack surface. By integrating the KEV feed directly into your scanning and asset management tools, you can get immediate alerts when a newly listed vulnerability is discovered on one of your systems. This ensures you’re aware of your exposure the moment it becomes a known, active threat, giving your team a critical head start on remediation.
Once a KEV is detected in your environment, the next step is to understand its potential impact. Not every KEV carries the same weight for every organization. By integrating data from the CISA KEV catalog, you can better assess your unique risk landscape, focusing on vulnerabilities that are not only present but are also actively targeted. Ask critical questions: Is the affected asset internet-facing? Does it store sensitive customer data? Is it essential for business operations? This is where vulnerability and threat prioritization becomes essential. Adding this business context helps you distinguish a critical, must-fix-now threat from a lower-priority issue, allowing you to direct your resources where they’ll have the greatest impact.
With your priorities straight, it’s time to act. Developing a remediation workflow that prioritizes vulnerabilities listed in the KEV catalog is essential. This ensures that your team’s time and effort are allocated effectively to address the most critical threats first. A good workflow clearly defines roles and responsibilities, sets realistic timelines that align with CISA’s deadlines, and outlines the specific steps for patching or mitigation. Having a documented process removes ambiguity and helps your team move quickly and confidently. This plan should be a living document, refined over time as you learn what works best for your organization’s unique structure and technology stack.
Deploying a patch isn’t the end of the story. After implementing fixes, you must validate their effectiveness to ensure the vulnerability is fully remediated. This final step closes the loop on your response strategy. Validation can involve re-scanning the asset to confirm the patch was applied correctly or using adversarial exposure validation techniques to simulate an attack and test your defenses. Continuous monitoring is also crucial here to watch for any signs that the vulnerability has been exploited or has reappeared due to a configuration change. This confirmation step provides the assurance that your efforts have successfully reduced your organization’s risk.
A solid strategy for handling KEVs is a great start, but you need the right technology to bring it to life. Trying to manage these critical vulnerabilities with spreadsheets and manual processes just won’t cut it. The KEV catalog is constantly updated, and attackers move fast. Without the right tools, your team will be stuck in a reactive cycle, always playing catch-up and struggling to meet remediation deadlines. This is where a modern, integrated security stack makes all the difference.
The goal is to build a system that turns the KEV catalog from a simple list into a dynamic, actionable intelligence feed that’s woven directly into your security operations. Your tech should automate the tedious work of detection and correlation, freeing up your team to focus on the strategic work of risk assessment and remediation. A well-designed stack provides a unified view of cyber risks, helping you see exactly where you’re exposed, what to fix first, and how your efforts are reducing overall risk. It’s about moving from simply knowing about a threat to confidently and efficiently neutralizing it before it can be used against you.
If your team is still tracking vulnerabilities across different spreadsheets and reports, it’s time for an upgrade. A centralized vulnerability management platform acts as your single source of truth. It pulls in data from all your scanning tools and asset inventories, giving you one place to see your entire security posture. When a new KEV appears, the platform can immediately show you every affected asset in your environment. This eliminates the frantic, manual search and allows you to instantly grasp the scope of the problem. It’s the foundation for a focused and efficient vulnerability and threat prioritization process, helping you manage remediation workflows and report progress clearly.
When a vulnerability is on the KEV list, you’re in a race against attackers. Manual, periodic scanning is too slow to keep up. You need automated, continuous scanning to find threats as soon as they emerge. These tools constantly monitor your environment, checking for new weaknesses across your entire digital footprint. By integrating the KEV catalog directly into your scanning solution, you can get instant alerts when a known exploited vulnerability is discovered on one of your assets. This gives your team a critical head start, shrinking the window of opportunity for an attacker and helping you begin the remediation process immediately. This proactive approach is a core part of total attack surface management.
Finding a KEV is only the first step; you have to fix it. This is where a robust patch management system becomes essential. These systems help you streamline the entire patching process, from testing a fix in a safe environment to deploying it across thousands of endpoints without disrupting business operations. For KEVs with tight remediation deadlines, an efficient patching workflow is non-negotiable. A good system allows you to schedule deployments, track their progress, and verify that patches have been successfully applied. This ensures you not only meet compliance requirements but also genuinely close the security gap.
Having great individual tools isn’t enough if they don’t work together. Disconnected systems create information silos, slow down your response time, and leave you with dangerous blind spots. The most effective KEV response programs are built on integrated technology that provides a single, cohesive view of risk. When your scanner, threat intelligence feed, and patch management system are all connected, you can follow a vulnerability from detection to remediation in one seamless workflow. This allows you to visualize KEV-related risks on a single dashboard, automatically assign remediation tasks, and track progress against CISA’s deadlines without switching between multiple screens.
Having access to the KEV catalog is a great first step, but turning that data into decisive action requires a solid operational plan. An efficient KEV program isn’t about speed alone; it’s about creating a repeatable, predictable process that reduces risk without burning out your team. When a new vulnerability hits the catalog, your team should know exactly what to do, who’s responsible, and how to track the fix from start to finish. By streamlining your workflow, you can move from a reactive scramble to a proactive, controlled response.
When a KEV alert comes in, the last thing you want is confusion over who owns the response. A well-defined process ensures that everyone knows their role. Your vulnerability management team might be responsible for monitoring the KEV catalog and identifying affected assets, while your IT or DevOps teams handle the actual patching and deployment. Meanwhile, a security manager or CISO should be accountable for the overall remediation timeline and reporting progress to leadership.
Clearly documenting these responsibilities prevents tasks from falling through the cracks. Map out the entire workflow: who receives the initial alert, who validates the vulnerability’s presence in your environment, who applies the patch, and who confirms the fix was successful. This clarity ensures a swift and coordinated effort every time.
Clear and consistent communication is the backbone of an effective KEV response. When a vulnerability is confirmed, how will you notify the relevant teams? An email blast that gets lost in a crowded inbox won’t cut it. Establish dedicated communication channels, like a specific Slack channel, a Microsoft Teams group, or automated alerts within your ticketing system.
The goal is to create a single source of truth where all stakeholders can see the vulnerability details, remediation deadlines, and status updates in real time. This is especially important for coordinating between security, IT operations, and development teams who may work in different systems. Centralizing communication ensures everyone is working from the same information and that critical remediation due dates are never missed.
The KEV catalog is your ultimate cheat sheet for prioritization. It tells you exactly which vulnerabilities attackers are using right now, allowing you to focus your team’s limited time and resources where they will have the most impact. Instead of getting overwhelmed by thousands of “critical” or “high” severity CVEs, you can treat every KEV entry as a top-priority incident.
This means KEV-related tickets should jump to the front of the remediation queue. Empower your team to pause lower-priority tasks to address these immediate threats. By aligning your efforts with this real-world threat intelligence, you ensure you’re fixing the problems that matter most. This approach is central to an effective vulnerability and threat prioritization strategy, moving your program from simply being busy to being effective.
You can’t improve what you don’t measure. To understand if your KEV program is working, you need to track key performance indicators (KPIs). The most important metric is Mean Time to Remediate (MTTR) specifically for KEVs. How quickly is your team closing out these high-priority vulnerabilities from the moment they are added to the catalog?
Other valuable metrics include the percentage of KEVs patched before CISA’s deadline and the total number of open KEVs in your environment over time. Tracking these figures helps you identify bottlenecks in your workflow, justify the need for more resources, and demonstrate the value of your security program to leadership. These vulnerability management metrics provide clear evidence that your team is actively reducing the organization’s most significant exposures.
Integrating KEV data into your daily security operations doesn’t have to be a massive overhaul. It’s about adopting a few key habits that turn reactive firefighting into a proactive defense. By focusing on continuous monitoring, collaboration, smart automation, and clear record-keeping, you can build a robust KEV response program that keeps your organization ahead of active threats.
The KEV catalog isn’t a static list. New vulnerabilities are added as attackers find new exploits, so your approach must be just as dynamic. Adopting a continuous monitoring mindset means making KEV checks a regular part of your security rhythm. This allows you to stay ahead of threats instead of just reacting to them. By constantly scanning your environment against the latest KEV entries, you can ensure you’re always addressing the most critical risks first. This proactive stance is fundamental to modern threat exposure management.
Vulnerability management is a team sport, requiring action from security, IT, and development. The KEV catalog, with its clear deadlines, provides a shared language and a common set of priorities that can unite these teams. When everyone understands the urgency of a specific vulnerability, you can foster collaboration and break down the silos that slow down remediation. A unified platform where all stakeholders see the same risk data is essential for getting everyone aligned and moving in the same direction.
Manually tracking KEV updates and creating remediation tickets is a recipe for burnout. Automation is your best friend here. You can set up workflows to automatically ingest KEV updates, trigger scans, and assign remediation tasks based on CISA’s due dates. This doesn’t just save time; it ensures a consistent and rapid response to the most urgent threats. By automating routine work, you free up your team to focus on the complex analysis and strategic planning needed to strengthen your security posture.
Good documentation is non-negotiable. Keeping clear records of which KEV vulnerabilities you’ve identified, when they were patched, and how the fix was validated is crucial for compliance and accountability. This audit trail proves you’re meeting your obligations and helps you track performance over time. More importantly, these records provide valuable insights for future incident response planning. When you can easily look back at how you handled a threat, you can refine your processes and become more efficient at managing vulnerabilities in the long run.
Think of the KEV catalog as more than just a high-priority to-do list. It’s a strategic tool that can fundamentally improve how you approach security. When you move beyond simply checking boxes and start integrating KEV intelligence into your broader program, you shift from a reactive cycle of patching to building a truly resilient defense. The catalog gives you the data-driven focus needed to make meaningful improvements that reduce your exposure to real-world attacks. By weaving KEV insights into your daily operations and long-term planning, you can build a security posture that is proactive, efficient, and genuinely effective against the threats that matter most.
The KEV catalog removes ambiguity from your vulnerability management process. It provides a clear, authoritative source for what needs to be fixed right now. Use this clarity to your advantage by building it directly into your security policies. For example, your policy can mandate that any vulnerability appearing on the KEV list must be remediated by CISA’s deadline, no exceptions. This creates a simple, non-negotiable standard for your team and stakeholders. It also serves as a critical resource for justifying the urgency and resources needed for patching. The conversation shifts from “Why should we fix this?” to “How quickly can we get this done?” This simple policy change can streamline your entire vulnerability management workflow and align everyone on what truly matters.
For federal agencies, following CISA’s directives is mandatory. For everyone else, aligning with the KEV catalog is a powerful way to demonstrate due diligence and strengthen your compliance posture. When auditors, partners, or customers ask how you handle risk, pointing to a KEV-driven patching strategy is a clear and defensible answer. The catalog’s remediation due dates are essential for building effective compliance strategies. Integrating KEV data into your GRC platform can help automate evidence collection for frameworks like SOC 2 or ISO 27001, making audits smoother. It ensures you’re not just meeting a baseline but are actively working to reduce your exposure to the most pressing threats.
Don’t let the immediate urgency of KEV alerts prevent you from seeing the bigger picture. The catalog is a valuable source of strategic intelligence that can help you plan for long-term security improvements. Set aside time to analyze trends in the KEV data. Are you constantly patching the same applications or systems? Does a particular vendor appear on the list more often than others? These patterns can reveal systemic weaknesses in your environment or supply chain. This insight allows you to make smarter, more strategic decisions about your total attack surface. It can guide investments in more secure technologies, justify the retirement of legacy systems, or inform vendor risk management discussions.
The ultimate goal is to get ahead of attackers, and the KEV catalog gives you a direct look at their playbook. By focusing your efforts on the vulnerabilities you know are being used in active campaigns, you are directly countering real-world threats. This is the core of a proactive and future-ready defense. Instead of getting overwhelmed by the sheer volume of CVEs published each year, your team can concentrate its time and energy where it will have the greatest impact. This risk-based approach is a foundational element of a modern Threat Exposure Management platform, helping you build a security program that is adaptive, resilient, and prepared for emerging threats.
My team already prioritizes vulnerabilities with high CVSS scores. Isn’t that enough? A high CVSS score tells you a vulnerability could be severe if exploited, but it doesn’t tell you if anyone is actually exploiting it. The KEV catalog bridges that gap by only listing vulnerabilities with confirmed, active exploits in the wild. Think of it as adding real-world context to your prioritization, so you can focus on the proven threats that pose an immediate danger, not just the theoretical ones.
Is the KEV catalog only a requirement for federal agencies? While it’s a mandatory directive for U.S. Federal Civilian Executive Branch agencies, the KEV catalog is a powerful best practice for any organization. Following its guidance and deadlines is a smart way to align your security efforts with the current threat landscape. It provides a clear, defensible standard for prioritizing the vulnerabilities that attackers are actively using against organizations just like yours.
What’s the first step my team should take to start using the KEV catalog? The best place to start is by setting up a continuous monitoring process. You need a way to automatically check your systems against the KEV list as it’s updated. This ensures you’re immediately aware when a known exploited vulnerability exists in your environment, giving you a crucial head start on fixing it before it can be used against you.
What should we do if we can’t patch a KEV vulnerability by the CISA deadline? Sometimes, patching isn’t immediately possible due to operational constraints. If you can’t meet a deadline, the priority is to implement compensating controls to mitigate the risk. This could involve isolating the affected system, restricting access, or using a virtual patch. The key is to document the reason for the delay and the mitigation steps you’ve taken while you work on a permanent fix.
How does using the KEV catalog fit into a larger threat exposure management program? The KEV catalog is a perfect example of threat-informed defense, which is a core principle of a modern threat exposure management program. It provides the critical intelligence you need to prioritize your actions based on real-world attacker behavior. Integrating KEV data helps you move beyond just managing a list of vulnerabilities and toward proactively reducing your organization’s most significant exposures.