Comprehensive Threat Exposure Management Platform
If your security team is drowning in a sea of “critical” alerts from your vulnerability scanner, you know the feeling of being busy without being effective. You spend all your time triaging and patching, but you never feel like you’re actually ahead of the attackers. This is the core problem that Continuous Threat Exposure Management (CTEM) was designed to solve. It’s a strategic shift away from a reactive checklist and toward a proactive program that focuses on the exposures that truly matter. This guide will walk you through what a CTEM program entails, what to look for in a platform, and how to evaluate your options. We’ll help you answer the critical question: what’s the best continuous threat exposure management tool to bring clarity and focus back to your security program?
Let’s cut through the jargon. Continuous Threat Exposure Management (CTEM) is a strategic approach that shifts your security program from being reactive to proactive. Instead of just scanning for vulnerabilities and getting a massive, overwhelming list of things to fix, CTEM creates a continuous loop. It’s a five-stage cycle of scoping, discovery, prioritization, validation, and mobilization that helps you see your organization through an attacker’s eyes. Think of it as a constant, live-fire drill for your defenses.
The goal is to move beyond a simple checklist of vulnerabilities. A CTEM program helps you understand which exposures actually pose a threat to your critical assets and provides a clear path to remediation before an attacker can exploit them. It’s not just another tool to add to your stack; it’s a framework for making smarter, faster, and more impactful security decisions. By implementing a CTEM program, you can focus your team’s valuable time and resources on the threats that truly matter to your business, transforming your security posture from a defensive crouch into a confident, forward-leaning stance. This approach is central to a modern threat exposure management platform that unifies your view of cyber risks.
Your organization’s attack surface is growing every day. With the constant addition of new cloud services, APIs, and remote devices, the old way of doing things—like quarterly scans and manual prioritization—just can’t keep up. Attackers are moving faster than ever, with some vulnerabilities being weaponized in under 24 hours. This new reality demands a security program that is just as agile and relentless.
CTEM is essential because it provides the structure needed to manage this complexity. It forces a continuous evaluation of your total attack surface, ensuring you have a real-time inventory of your assets and their potential exposures. This isn’t just about finding more vulnerabilities; it’s about finding the right ones. By focusing on exploitable attack paths that lead to your most critical business systems, CTEM helps you make security a core business function, not just an IT problem.
The biggest difference between CTEM and traditional vulnerability management is the shift from a tool-based process to a strategic program. Traditional vulnerability management often leaves teams drowning in data. You run a scan, get a report with thousands of CVEs, and then face the impossible task of figuring out what to patch first. It’s a reactive cycle that lacks business context and often leads to burnout and critical gaps in security.
CTEM, on the other hand, is a continuous and proactive program. It goes beyond just identifying vulnerabilities by adding crucial layers of context. It asks questions like: Is this vulnerability actually exploitable in our environment? Does it expose a critical asset? What is the potential business impact? This focus on vulnerability and threat prioritization ensures that security efforts are directly aligned with business risk. Instead of trying to patch everything, you’re strategically fixing the issues that present the most immediate and significant threat.
When you start evaluating Continuous Threat Exposure Management (CTEM) platforms, you’ll quickly realize they aren’t all built the same. The right tool goes beyond simple vulnerability scanning; it gives you a dynamic, attacker-centric view of your security posture. Think of it as moving from a static, outdated map to a live GPS that reroutes you around threats in real time.
A strong CTEM program is built on a continuous loop of five key stages: scoping, discovery, prioritization, validation, and mobilization. Your chosen tool should support every single one of these stages. To make sure you’re investing in a platform that will actually reduce your exposure and make your team’s life easier, look for one that delivers on a few core capabilities. These features are the difference between simply collecting security data and turning that data into decisive, proactive action. Let’s walk through the non-negotiables.
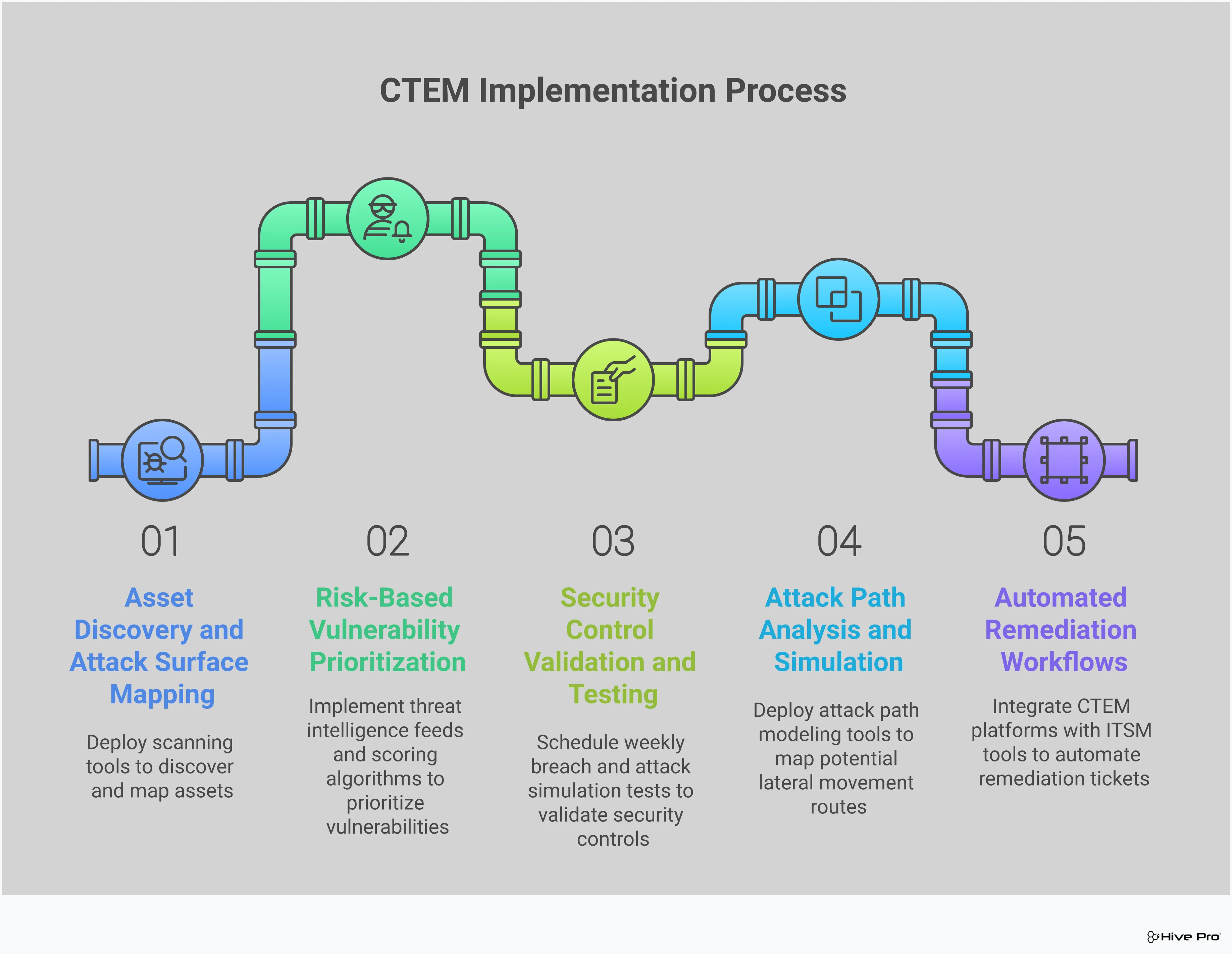
You can’t protect what you don’t know you have. The first job of any CTEM tool is to provide complete and continuous visibility across your entire environment. This means discovering every single asset—servers, cloud instances, applications, IoT devices, and code repositories—whether they are officially managed by IT or not. A great platform continuously scans your total attack surface to find and catalog everything, giving you a comprehensive inventory. This isn’t a one-time snapshot; it’s a living, breathing map of all your digital assets and the potential entry points an attacker could exploit.
Drowning in a sea of “critical” alerts is a common problem for security teams. A top-tier CTEM tool cuts through the noise by helping you focus on the vulnerabilities that pose a genuine threat to your business. Instead of relying solely on static CVSS scores, it should enrich vulnerability data with real-time threat intelligence and business context. This approach to vulnerability and threat prioritization helps you answer the most important question: “What do we need to fix right now?” By focusing your team’s limited time and resources on the exposures that are actively being exploited or are most likely to be targeted, you can make a much bigger impact on your overall security.
How do you know your security tools are actually working as expected? A key feature of a modern CTEM platform is the ability to validate your security controls. This involves safely testing your defenses—like firewalls, EDR, and web application firewalls—against known threat behaviors to see if they hold up. This process of adversarial exposure validation moves you from assumption to certainty. Instead of just hoping your configurations are correct, you can prove that your controls can block specific attack techniques. This gives you concrete evidence of your security effectiveness and highlights gaps that need immediate attention before an attacker finds them.
To truly understand your exposure, you need to think like an attacker. The best CTEM tools include Breach and Attack Simulation (BAS) capabilities that let you safely simulate real-world attack paths. These simulations show you exactly how an adversary could chain together multiple vulnerabilities to move from the perimeter to your most critical assets. By running these tests, you can identify and close complex attack paths that a traditional vulnerability scanner would miss. Platforms like Uni5 Xposure use these simulations to provide clear, actionable recommendations, helping your team understand not just what to fix, but why it matters in the context of a full-blown attack.
A CTEM tool shouldn’t operate in a silo. It needs to fit smoothly into your existing security ecosystem. Look for a platform with robust APIs and out-of-the-box integrations for the tools your team already relies on, such as SIEMs, SOAR platforms, and ticketing systems. This ensures that the insights from your CTEM tool can be easily shared and acted upon. Equally important is clear, intuitive reporting. The platform should offer customizable dashboards that can communicate risk to different audiences—from the technical details your security operations team needs to the high-level summaries your CISO needs to present to the board.
Choosing the right CTEM tool feels like a huge decision, because it is. You’re not just buying software; you’re adopting a new framework for your entire security program. The good news is that there are some fantastic platforms out there designed to make this transition smoother. Each tool has its own unique strengths, so the “best” one really depends on your team’s specific needs, current security stack, and overall goals. Some platforms excel at attack surface discovery, while others are powerhouses in validation and breach simulation. Your choice will shape how your team identifies, prioritizes, and remediates threats for years to come.
Think of this list as a starting point for your research. As you explore these options, pay close attention to how they handle each stage of the CTEM lifecycle—from discovery and prioritization to validation and mobilization. Consider how easily they can integrate with the tools you already use and what kind of support they offer. The right platform will feel less like another dashboard to check and more like a central hub that gives your team clarity and confidence. It should provide actionable insights, not just more data, and help you communicate risk effectively to stakeholders across the business.
Hive Pro’s goal is to shift your security program from a reactive to a proactive stance. Its Uni5 Xposure Platform is a comprehensive solution built to implement the entire CTEM framework from end to end. It handles everything from scoping and discovery to prioritization, validation, and mobilization, all within a single, unified platform. This is a great option for teams looking to consolidate their toolset and adopt a structured, proactive approach to reducing exposure. By bringing all these functions together, it helps you focus on the threats that pose an imminent risk without having to piece together data from multiple sources.
Nagomi Security excels at giving you a complete picture of your security posture by combining three key functions: seeing your weaknesses, testing your defenses, and running attack simulations. The platform provides a constant view of your exposed systems and users, so you always know where you’re vulnerable. It then tests your existing security controls to see if they’re actually working as expected. What makes it particularly helpful is that it provides clear, step-by-step advice to fix the most urgent problems first, giving your team an actionable path forward for remediation.
If you’re looking for an AI-powered approach, SentinelOne Singularity is a strong contender. It uses artificial intelligence to automatically find and stop threats across your entire digital estate—including all your devices, servers, clouds, and even temporary containerized systems. This focus on automation helps security teams manage a wide and complex attack surface more efficiently. Its ability to uncover hidden threats and prevent data leaks makes it a powerful tool for organizations that need real-time, autonomous protection against sophisticated attacks.
Rapid7 InsightVM has built a solid reputation for its advanced risk-scoring capabilities. It’s particularly well-known for helping organizations effectively prioritize their remediation efforts. The platform goes beyond just identifying vulnerabilities; it analyzes how risky they are in the context of your specific environment. This allows your team to focus on fixing the flaws that attackers are most likely to exploit, ensuring your limited resources are spent on the issues that matter most. For teams struggling with a long list of vulnerabilities and no clear starting point, InsightVM can provide much-needed clarity.
Cymulate is an excellent choice for teams that want to rigorously test their security controls, processes, and people. It’s highly effective for the validation stage of the CTEM framework, providing deep insights into how well your defenses hold up against simulated attacks. By running continuous breach and attack simulations, Cymulate helps you identify gaps in your security posture before a real attacker does. This makes it a great fit for organizations that want to move beyond theoretical risk and get practical, real-world data on their security readiness.
Tenable.io is a powerhouse when it comes to visibility. The platform goes far beyond basic vulnerability scanning to constantly discover new and previously unknown assets across your environment. It then connects those assets with real-time threat intelligence to give you a comprehensive and continuously updated view of your security posture. For organizations with sprawling, dynamic IT environments, Tenable.io provides the foundational visibility needed to understand the full scope of their attack surface. This complete view is the critical first step in any effective threat exposure management program.
Qualys VMDR (Vulnerability Management, Detection, and Response) brings several critical security functions into one integrated solution. By combining these capabilities, it provides a unified view of vulnerabilities across your entire environment, from on-premises systems to cloud instances and remote endpoints. This all-in-one approach helps streamline the process of identifying, prioritizing, and remediating threats. For teams looking to simplify their security stack and create a more efficient workflow, Qualys VMDR offers a cohesive platform that covers the full lifecycle of a vulnerability.
If your vulnerability scanner spits out a list of thousands of “critical” issues, you know how impossible it feels to decide what to fix first. This is where Continuous Threat Exposure Management (CTEM) completely changes the game. Instead of just flagging every potential weakness, CTEM platforms act like a seasoned security strategist, using multiple layers of context to pinpoint the handful of vulnerabilities that pose a genuine, immediate threat to your organization. It’s about moving from a massive, overwhelming to-do list to a focused, actionable plan. Here’s how they do it.
A high CVSS score doesn’t always mean a high-priority problem. A vulnerability is only a real threat if attackers are actively exploiting it. CTEM tools connect to a constant stream of real-time threat intelligence to see what’s happening in the wild. They track which vulnerabilities are being used in current malware campaigns, which exploits are being sold on the dark web, and what tactics threat actors are favoring right now. This intelligence, often curated by expert teams like HiveForce Labs, allows you to filter out the theoretical risks and focus on the clear and present dangers. You stop wasting time on vulnerabilities that no one is using and start defending against the attacks that are actually happening.
A vulnerability on a developer’s test machine is not the same as one on your customer-facing payment portal. CTEM platforms understand this critical difference. They don’t just scan your assets; they help you map them to their business function and criticality. By understanding which systems are essential for revenue, operations, or data protection, the platform can prioritize vulnerabilities that threaten your most valuable assets. This approach aligns security efforts with business risk, ensuring your team’s limited time and resources are spent protecting what truly matters. It’s the key to answering not just “Is it vulnerable?” but “Does it matter to the business if it’s compromised?”
Just because a vulnerability exists doesn’t mean it’s a viable entry point for an attacker in your specific environment. You might have other security controls in place that block the attack path. CTEM tools go beyond simple detection to perform exploitability assessments. They validate whether a vulnerability can actually be reached and exploited, considering your unique network architecture, firewalls, and security configurations. This validation step is crucial for prioritizing what to fix first because it separates the theoretical weaknesses from the practically exploitable ones. It stops your team from chasing ghosts and lets them focus on sealing the real, open doors into your network.
The best defense is a good offense. Modern CTEM platforms use AI to think like an attacker and predict their next move. By running sophisticated simulations, these tools can identify and visualize the most likely attack paths an adversary would take to get from an initial entry point to your organization’s crown jewels. These AI-powered simulations reveal the true threat level of each exposure, showing you exactly how a breach could unfold. This allows you to proactively close off those pathways before they can be exploited. It’s a forward-looking approach that helps you stay one step ahead, securing your organization against not just today’s threats, but tomorrow’s as well.
Let’s talk about the budget. Investing in a new security platform is a big decision, and the price tag is often the first thing stakeholders look at. But the real cost of a CTEM tool goes far beyond the initial subscription fee. To make a smart investment, you need to understand the full picture, from pricing models and hidden expenses to the long-term return you can expect. Thinking about the total cost of ownership (TCO) from the start will help you build a stronger business case and avoid any surprises down the road. It’s about finding a solution that not only fits your technical needs but also makes financial sense for your organization.
CTEM pricing isn’t always straightforward because the solutions themselves are so comprehensive. The price often reflects the tool’s scope, since CTEM is a proactive, five-phase program that continuously identifies, prioritizes, validates, and remediates security exposures. You’ll typically see pricing based on the number of assets (servers, endpoints, cloud resources), the number of users, or a tiered subscription model with different feature sets. When you’re comparing vendors, make sure you’re clear on what’s included in each package. A cheaper tool that only handles one part of the CTEM lifecycle might end up costing you more in manual effort and security gaps down the line. Ask vendors for a detailed breakdown so you can make an apples-to-apples comparison.
Adopting a CTEM platform is more than just plugging in a new tool; it’s a strategic change. This “fundamental shift from periodic, reactive security to continuous, proactive exposure management” comes with costs that aren’t listed on the quote. You’ll need to account for implementation and integration with your existing security stack, like your SIEM and ticketing systems. Then there’s training—your team will need time to learn the new platform and workflows. Don’t forget about ongoing maintenance and potential fees for premium support. Thinking through these additional expenses is a key part of making the business case for CTEM and ensuring a smooth rollout.
Justifying the expense of a new tool is always a challenge, and proving the ROI is a crucial part of any evaluation. While preventing a costly breach is the ultimate goal, you can also measure ROI through operational efficiencies. Start tracking metrics like the reduction in time your team spends manually triaging alerts or the decrease in your mean-time-to-remediate (MTTR) for critical vulnerabilities. You might also see savings from consolidating other tools that your CTEM platform now makes redundant. Over time, a stronger security posture can even lead to lower cyber insurance premiums, though it can take time to see direct insurance savings.
Adopting a new CTEM platform is more than just a software installation; it’s a strategic shift in how your team approaches security. While the benefits are significant, it’s smart to go in with a clear picture of the potential hurdles. Getting ahead of these common challenges will make the transition smoother and help you get value from your new tool much faster. The main areas to prepare for involve integrating the technology, preparing your people, and adapting your processes. By anticipating these bumps in the road, you can create a clear path for a successful rollout that transforms your security posture from reactive to proactive.
Most security teams are already working with a complex ecosystem of tools. The last thing you need is another siloed solution that just adds to the noise. A major challenge is ensuring your CTEM platform can connect with your existing security stack—your SIEM, SOAR, ticketing systems, and cloud environments. Without seamless integration, you risk creating more work and alert fatigue for your team. The right CTEM tool should act as a central hub, pulling data from your other tools to give you a single, unified view of risk. Look for a platform with robust APIs and pre-built connectors so your new Uni5 Xposure Platform can communicate effortlessly with the tools you already rely on.
A powerful tool is only effective if your team knows how to use it. Implementing CTEM requires a structured approach that goes beyond a simple software tutorial. It involves training your team on new workflows and, more importantly, on a new, proactive mindset. Before you even begin, it’s crucial to define what you want to achieve. Are you aiming for faster remediation times or better reporting for leadership? Once your goals are set, you can map out your current systems to see where the CTEM tool fits in. This helps you create a clear training plan focused on the “why” behind a continuous approach to vulnerability and threat prioritization.
Change can be met with resistance, especially when it alters long-standing routines. CTEM represents a fundamental shift away from the traditional, reactive cycle of scanning and patching. Instead of just working through a list of vulnerabilities, your teams will need to think continuously about exposure and business risk. This change can be disruptive for teams accustomed to a more periodic, ticket-based workflow. The key is to communicate the value of this new approach. The goal isn’t just to find more flaws; it’s to focus everyone’s effort on the threats that pose a genuine danger to the business. This helps everyone see the bigger picture of managing your total attack surface collaboratively.
With a growing number of CTEM platforms on the market, picking the right one can feel like a major undertaking. The best tool for your organization isn’t necessarily the one with the longest feature list, but the one that fits seamlessly into your existing workflows, addresses your specific risks, and empowers your team to act decisively. Making the right choice requires a structured approach that goes beyond slick marketing demos.
Think of this process in three distinct phases. First, you need to define exactly what you’re looking for by creating a clear evaluation checklist based on your unique environment and security goals. Second, you have to put the top contenders to the test in your own environment through a pilot program or proof of concept (PoC). This is where you separate theory from reality. Finally, you need to look beyond the technology itself and assess the vendor. A strong partnership with a supportive and knowledgeable vendor can be just as critical as the software itself. Let’s walk through how to handle each of these steps to find a CTEM tool that truly works for you.
Before you start scheduling demos, sit down with your team and create a checklist of your non-negotiables. This ensures you’re evaluating every potential tool against the same critical standards. Your list should prioritize functionality that solves your biggest challenges.
First, confirm the tool provides comprehensive coverage. It needs to continuously scan and map your total attack surface—from on-prem servers and cloud instances to employee laptops and third-party services. Next, focus on intelligence. The platform must be able to prioritize risks based on more than just a CVSS score, incorporating real-time threat intelligence to show you what attackers are actively exploiting. Finally, check for easy integration. The right tool should connect smoothly with your existing security stack, like your SIEM and SOAR, to create a unified view of your security posture.
A product demo is designed to show a tool in its best light. A proof of concept (PoC) shows you how it performs in the real world—your world. Once you’ve narrowed your list down to two or three top contenders, running a pilot test is the single best way to make a confident decision. This is your chance to see if the platform delivers on its promises.
During the PoC, focus on testing the core capabilities you identified in your checklist. Can the tool effectively test your existing security measures to see if they’re actually blocking threats? More importantly, does it allow you to validate your security controls by simulating real-world attack scenarios? This practical testing helps you confirm that your patches and configurations are effective and gives your team hands-on experience with the tool’s workflow.
When you choose a CTEM platform, you’re not just buying a piece of software; you’re starting a long-term relationship with the vendor. The quality of their support can make or break your success. A great product with poor support will only lead to frustration, while a responsive and knowledgeable partner can help you get the most out of your investment.
Look for a vendor that offers robust onboarding, training, and ongoing technical support. Do they have a dedicated team to help you with integration and implementation? Do they offer access to security experts who can provide strategic guidance? Before making a final decision, dig into reviews and see what current customer experiences are like. A vendor who acts as a true partner is an invaluable asset.
Choosing the right CTEM tool is a huge step, but the work doesn’t stop there. A successful rollout depends just as much on your strategy and processes as it does on the software itself. To get the most out of your new platform, you need a solid plan that brings your people and technology together. Think of it less like flipping a switch and more like building a new, more efficient engine for your security program. By focusing on clear communication, measurable goals, and streamlined workflows from the start, you can ensure your CTEM initiative delivers real, lasting value and transforms how your organization manages cyber risk.
A CTEM program isn’t just a security project; it’s a business initiative. To succeed, you need support from stakeholders across the organization, including IT, DevOps, and executive leadership. Frame the conversation around shared goals. As experts at Zafran note, “Building a compelling business case for CTEM isn’t just about security; it’s about business survival and competitive advantage.” Instead of just talking about vulnerability counts, explain how a unified view of cyber risks protects revenue, ensures compliance, and enables faster innovation. When everyone understands the “why” behind the change, they’re far more likely to get on board and help make the implementation a success.
How will you know if your CTEM program is working? You can’t prove its value without clear, measurable goals. Before you go live, define the key performance indicators (KPIs) you’ll use to track progress. According to Strobes, effective metrics include “the reduction in vulnerabilities, the time taken to remediate issues, and the overall improvement in security posture.” Tracking these KPIs from day one will help you demonstrate the ROI of your investment to leadership. It also gives your team clear targets to aim for, turning abstract security goals into concrete achievements and helping you focus on vulnerability and threat prioritization that truly matters.
A CTEM tool is fantastic at finding and prioritizing threats, but it can’t fix them for you. That’s where your team and processes come in. To avoid creating more noise than action, you need to establish clear, repeatable remediation workflows. As Balbix highlights, this requires a “structured, five-stage process to proactively identify, prioritize, and address security risks.” This means defining who is responsible for what, setting realistic timelines for fixes, and integrating the CTEM platform with your existing ticketing systems like Jira or ServiceNow. A smooth workflow ensures that when a critical threat is identified on your total attack surface, everyone knows exactly what to do next.
Choosing a Continuous Threat Exposure Management (CTEM) platform is a significant decision that goes beyond comparing feature lists. The right tool should feel like a natural extension of your security team, fitting into your existing workflows and helping you achieve your specific goals. What works for one organization might not be the best fit for another, so it’s crucial to focus on the capabilities that will make the biggest impact on your program.
A great starting point is to look for a platform that can grow with you and integrates smoothly with your current security stack. Your CTEM tool shouldn’t create another data silo. Instead, it should easily share information with your SIEM, EDR, and other solutions to provide a single, clear view of your security posture. This level of integration streamlines operations and helps your team respond to threats more effectively.
Beyond connectivity, the core of any strong CTEM program is its ability to help you focus your resources. The prioritization phase is what truly separates a modern platform from a traditional scanner. It should help you decide what to fix first by analyzing real-world exploitability and business context, not just CVSS scores. This ensures your team spends its time on the risks that actually matter.
Finally, a top-tier platform empowers you to shift from a reactive to a proactive stance. It’s not enough to just identify vulnerabilities; you need to know if your defenses can withstand an actual attack. Look for a solution that allows you to validate your controls. When you can simulate real attacks, you can prove that your patches and security measures hold up, giving your team—and your leadership—confidence in your security program.
My team is already overwhelmed with alerts. Will a CTEM program just add more noise? That’s a completely fair question, and it gets to the heart of why CTEM is so effective. The goal isn’t to find more vulnerabilities; it’s to find the right ones. A CTEM program actually cuts through the noise by adding layers of context—like real-time threat intelligence and business criticality—to your security data. Instead of giving you a longer to-do list, it gives you a shorter, smarter one focused on the handful of exposures that pose a genuine threat to your most important assets.
Is CTEM a replacement for my existing vulnerability scanner, or does it work with it? It can be either, depending on the platform you choose. Think of CTEM as the strategic program and the vulnerability scanner as one of the tools that can feed into it. Many comprehensive CTEM platforms have their own powerful discovery and scanning capabilities that can replace a traditional scanner. However, a good platform will also integrate with the tools you already have, pulling in their data to create a single, unified view of your exposure. The main goal is to move beyond simple scanning to a continuous cycle of prioritization and validation.
How does a CTEM program help me justify security spending to leadership? CTEM helps you speak the language of the business. Instead of presenting a list of thousands of technical CVEs, you can show a clear, prioritized list of risks to critical business systems. You can demonstrate exactly how a specific vulnerability could lead to a breach of customer data or a disruption of revenue-generating services. By providing clear metrics on risk reduction and simulating attacks to prove your defenses are working, you can translate your team’s efforts into tangible business value that leadership can easily understand and support.
What’s the first practical step my team can take to move towards a CTEM approach? The best place to start is with the “scoping” phase, and you can do this even before you buy a new tool. Sit down with your team and business leaders to identify your organization’s crown jewels. What are the most critical applications, systems, and data stores that you absolutely must protect? Knowing what matters most gives you a lens through which to view all your security efforts. This initial step provides the focus you need to start prioritizing effectively and builds the foundation for a full CTEM program.
How is CTEM different from other security concepts like Attack Surface Management (ASM)? Think of Attack Surface Management as a critical component within the broader CTEM framework. ASM is primarily focused on the discovery phase—continuously identifying all of your internet-facing assets to see what an attacker sees. CTEM takes that information and runs with it. It’s a complete, five-stage cycle that not only discovers your assets but also prioritizes the exposures on them, validates your defenses against potential attacks, and mobilizes your teams to fix the most critical issues. In short, ASM finds the doors, and CTEM tells you which ones are unlocked, which ones lead to your valuables, and how to secure them.