Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Think of your organization’s digital presence as a sprawling, ever-expanding city. New buildings (servers) go up, old ones are forgotten, and unofficial shortcuts (shadow IT) appear overnight. Trying to defend this city without a current map is impossible. You’re left reacting to alarms instead of strategically placing your guards. This is where attack surface intelligence mapping comes in. It’s the process of creating a detailed, living blueprint of your entire digital estate, marking every potential entry point an attacker could use. It’s not a one-time survey; it’s a continuous process that provides the foundational visibility you need to move from a reactive security posture to a proactive one, anticipating and blocking threats with confidence.
Think of your organization’s digital presence as a sprawling estate. Attack surface intelligence mapping is the process of creating a detailed blueprint of that estate, marking every single door, window, and potential entry point an attacker could use. It’s about systematically identifying, cataloging, and analyzing all your internet-facing assets—from servers and domains to cloud services and employee laptops. But it doesn’t stop at just listing them out. The “intelligence” part is key; it involves adding context to this map, understanding which entry points are unlocked, which are weak, and which are most likely to be targeted by threats.
This isn’t a one-and-done task. Your digital footprint is constantly changing as you add new software, spin up cloud instances, or connect with new partners. That’s why effective mapping is a continuous process. It provides a living, breathing view of your total attack surface, helping you see your organization through an attacker’s eyes. By doing this, you can move from a reactive security posture—where you’re constantly putting out fires—to a proactive one where you can anticipate and block threats before they ever become a problem. It’s the foundational step for building a security strategy that is both resilient and realistic.
Let’s get specific. Attack surface intelligence is the outcome of continuously discovering and analyzing your organization’s entire digital footprint. This includes every asset exposed to the internet, like IP addresses, domains, certificates, and applications. The process involves a few core activities. First is asset inventory, which is simply finding and listing everything you own. Next comes threat modeling, where you think like an attacker to identify potential weaknesses. Finally, you perform a vulnerability assessment to find specific, exploitable flaws in those assets. The goal is to create a comprehensive and contextualized inventory of your exposure, so you know exactly what you need to protect and where your most significant risks lie.
Having a map of your attack surface is one thing; using it to make smart decisions is another. This is where intelligence transforms your security strategy. Instead of treating all vulnerabilities equally, you can use this insight to prioritize exposure based on which assets are most critical or most likely to be attacked. This intelligence helps you focus your team’s limited time and resources on the risks that truly matter. It allows you to answer critical questions like, “Which of our systems are exposed to the latest ransomware campaign?” or “Is that old server in the corner a real threat?” This proactive approach helps you stay ahead of attackers and secure your environment with confidence.
The most significant benefit of proactive mapping is a dramatic reduction in your risk of a breach. When you understand your exposures, you can address the most critical vulnerabilities first, effectively shrinking your attack surface. This process provides detailed reports that guide your remediation efforts, ensuring you’re fixing the right problems at the right time. Organizations that adopt this approach find they can manage their security programs more efficiently. Instead of guessing where the next threat might come from, they have a unified view of cyber risks that allows for confident, data-driven action. It’s about turning unknown risks into known, manageable variables.
Before you can protect your organization, you need a clear and complete picture of what you’re protecting. Defining your attack surface landscape is the foundational step in building a strong security posture. It’s about creating a comprehensive map of every digital point an attacker could potentially exploit. This isn’t just about the servers in your data center; it includes everything from cloud infrastructure and third-party applications to the unsanctioned software running on an employee’s laptop. A thorough understanding of this landscape is what separates a reactive security team from a proactive one that can anticipate and neutralize threats before they cause damage.
You can’t secure what you can’t see. The first step in mapping your attack surface is creating a complete inventory of all your digital assets. This means identifying every server, endpoint, application, and network device connected to your organization. Keeping this inventory current is a major challenge, which is why automated asset discovery tools are so important. These tools continuously scan your environment to identify and catalog all assets, giving you a real-time view of your total attack surface. Without an accurate and continuously updated asset list, you’re essentially trying to guard a house without knowing where all the doors and windows are.
Your attack surface doesn’t end at your own network perimeter. It extends to every vendor, partner, and third-party service you use. As SecurityScorecard notes, your attack surface includes “third-party services and applications that could create weaknesses in your security.” A vulnerability in a supplier’s system or a misconfigured API in a SaaS tool can easily become a backdoor into your own environment. That’s why a critical part of mapping your landscape involves a thorough third-party risk assessment. You need to understand their vulnerabilities just as well as your own to get a true sense of your exposure.
Cloud environments are dynamic and complex, making them a particularly challenging part of the attack surface to map. Assets like virtual machines, containers, and serverless functions can be spun up and down in minutes, creating a constantly shifting landscape. To effectively manage this, you need to maintain a detailed inventory of all your cloud-hosted assets, including web applications, IP addresses, domains, and certificates. Relying on outdated or incomplete information is a recipe for disaster. A continuous discovery process is essential for keeping up with the pace of cloud development and ensuring no exposed asset goes unnoticed.
One of the biggest blind spots for any security team is shadow IT—the hardware, software, and services used by employees without official approval. As SentinelOne points out, this practice “creates hidden weak spots that are hard to find.” When an employee uses an unsanctioned file-sharing app or connects a personal device to the network, they introduce unmanaged and unmonitored risks. These assets aren’t patched or configured according to company policy, making them easy targets for attackers. Actively monitoring your network to discover and manage shadow IT is crucial for closing these gaps and achieving a complete view of your attack surface.
Attack surface intelligence isn’t a one-and-done project; it’s a living, breathing cycle that helps your security program mature. Think of it as a four-part process: you find what you have, figure out its weaknesses, add context about real-world threats, and then prioritize your response based on risk. This systematic approach transforms security from a guessing game into a strategic operation. By following these steps, you can create a clear, actionable picture of your exposure and focus your team’s efforts where they’ll have the most impact. It’s about working smarter, not just harder, to stay ahead of potential threats.
You can’t protect what you don’t know exists. The first step is to get a complete and continuously updated inventory of all your digital assets. This means everything: servers, laptops, cloud instances, IoT devices, applications, and even forgotten subdomains. Deploying automated discovery tools is essential for creating a comprehensive map of your attack surface. These tools continuously scan your environment to identify and catalog every connected asset, ensuring nothing gets overlooked. A complete inventory is the foundation for your entire security strategy, giving you a clear picture of your organization’s total attack surface and eliminating dangerous blind spots.
Once you have a handle on your assets, the next move is to identify their weaknesses. This is where vulnerability assessment comes in. Your approach can include a mix of techniques, from automated vulnerability scanning that regularly checks for known flaws to more in-depth penetration testing that simulates a real-world attack. The goal is to systematically uncover security gaps across your entire asset inventory. Combining different assessment methods gives you a more complete view of your vulnerabilities, which is a critical step before you can begin the work of vulnerability and threat prioritization.
A long list of vulnerabilities can be overwhelming and, frankly, not very useful on its own. To make sense of it all, you need to integrate threat intelligence. This adds crucial context by telling you which vulnerabilities are being actively exploited in the wild, what tactics attackers are using, and which of your assets are the most attractive targets. High-quality threat intelligence, often curated by dedicated research teams like HiveForce Labs, helps you see your vulnerabilities through an attacker’s eyes. This allows you to separate the theoretical risks from the clear and present dangers, so you can focus on fixing the issues that truly matter.
With your asset inventory, vulnerability data, and threat intelligence in hand, you can finally build a meaningful risk scoring system. Instead of relying on generic CVSS scores, you can create a custom risk model that reflects your organization’s specific priorities. This system should weigh factors like asset criticality, threat likelihood, and potential business impact. By assigning a realistic risk score to each vulnerability, you can create a prioritized roadmap for remediation. This data-driven approach helps your team focus its limited time and resources on the most significant threats, enabling a proactive security posture with the help of a unified platform like Uni5 Xposure.
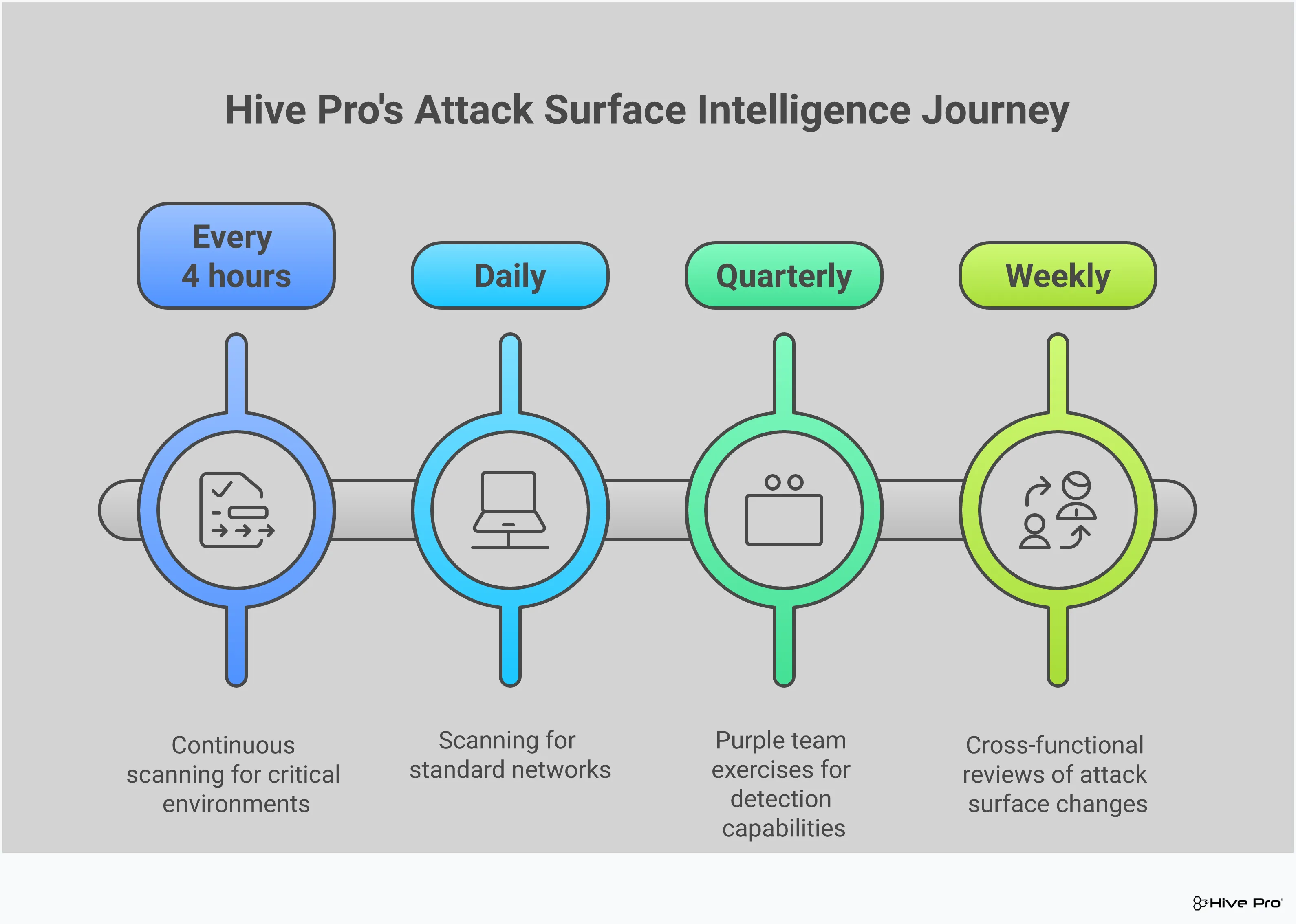
Once you understand your landscape, the next step is to gather intelligence on the threats and vulnerabilities within it. This isn’t a one-and-done task; it’s an ongoing process that combines several techniques to give you a complete and accurate picture of your exposure. Think of it as building a case file on your own organization from an attacker’s perspective. By using a mix of quiet observation and direct probing, you can uncover weaknesses before an adversary does. A comprehensive approach to total attack surface management relies on using multiple intelligence sources to build a resilient security posture. Let’s walk through four proven methods your team can start using right away.
Passive reconnaissance is your first, and quietest, line of inquiry. It’s all about gathering information about your organization without directly interacting with your systems. This means you’re not sending any packets or queries that could trigger alarms. Instead, you’re collecting publicly available data from sources like website records, DNS information, social media profiles, and job postings. The goal is to build a foundational map of your digital footprint from the outside in, just like an attacker would. This method is essentially digital eavesdropping; you’re learning as much as you can about the target without ever knocking on the door, which makes it an invaluable and low-risk way to identify potential entry points.
Where passive reconnaissance is about listening, active scanning is about asking questions. This technique involves directly probing your systems with specialized tools to find vulnerabilities, open ports, and misconfigurations. It’s like methodically checking every door and window of a building to see which ones are unlocked. Active scanning provides a wealth of detailed, technical information that passive methods can’t uncover. However, because you are directly engaging with the target systems, this activity can be detected by firewalls and intrusion detection systems. That’s why it’s crucial to conduct active scanning carefully and with proper authorization, ensuring you can effectively prioritize the vulnerabilities you find with a solution for vulnerability and threat prioritization.
Open-Source Intelligence (OSINT) is the practice of collecting and analyzing data from publicly available sources to generate actionable intelligence. It goes beyond simple passive reconnaissance by pulling from a vast array of information, including news articles, academic papers, public forums, code repositories, and even chatter on the dark web. Think of yourself as a detective piecing together clues from different places to reveal a larger picture. OSINT can help you uncover everything from leaked employee credentials to discussions about exploiting a specific technology your company uses. By systematically gathering and analyzing this data, you can discover hidden risks and gain context on threats that may not be visible through technical scanning alone.
Manually gathering intelligence across a modern, dynamic attack surface is nearly impossible. This is where automated discovery tools become essential. These platforms continuously scan your environment to identify assets, detect vulnerabilities, and map your entire digital footprint in real time. Automation drastically improves the efficiency and accuracy of your intelligence-gathering efforts, freeing up your security team from tedious data collection. Instead of spending their time trying to find assets, your team can focus on analyzing the results and remediating risks. Using a comprehensive platform like Uni5 Xposure allows you to automate discovery and maintain a continuously updated inventory of your assets and their associated exposures.
Jumping into attack surface mapping without a plan is like trying to build a house without a blueprint. You might get a few walls up, but the foundation will be shaky, and you’ll waste a lot of time and effort. A solid strategy provides the structure you need to move from a reactive security posture to a proactive one. It’s about being deliberate in how you discover, analyze, and protect your digital footprint.
Building an effective strategy means thinking through the entire process before you even run your first scan. It involves setting clear goals, defining your scope, assembling the right team, and being realistic about your resources. This isn’t just about creating a one-time map; it’s about establishing a continuous program that adapts as your organization evolves. A well-thought-out strategy ensures your mapping efforts are focused, efficient, and aligned with your overall security objectives. It turns a daunting task into a manageable and repeatable process that delivers real value by helping you see your organization through an attacker’s eyes and close security gaps before they can be exploited.
Before you start mapping, you need to know what you’re trying to achieve. Mapping your attack surface is essential because it helps you find weak spots, prioritize security efforts, and improve incident response. Your plan should start by defining these goals. Are you trying to get a handle on shadow IT, prepare for an audit, or simply gain better visibility into your cloud environments? Clearly stating your objectives will guide your entire process and help you measure success later on. This initial planning phase is also crucial for getting buy-in from other departments and securing the resources you’ll need for a successful total attack surface management program.
Once you have your goals, you can outline the practical steps. The first move is to define what you need to map. Decide on the scope of your project—are you focusing only on public-facing websites and APIs, or do you need to include all internal networks and cloud systems? After defining your scope, you can begin to map your basic setup. This involves creating an initial inventory of all your known digital assets, including servers, databases, applications, and how they connect to each other. While this can start as a manual process, using a platform to automatically discover and inventory your assets will give you a more accurate and comprehensive foundation to build upon.
Attack surface mapping isn’t a solo mission for the security team. To get a complete and accurate picture, you need to get different departments to work together. Your IT team knows the network infrastructure, your DevOps team understands the cloud configurations, and your business teams know which applications are critical to daily operations. By creating a cross-functional team, you can ensure all assets and their associated risks are considered. This collaborative approach breaks down information silos and fosters a shared sense of ownership over the organization’s security, leading to a much more comprehensive and effective mapping process.
Let’s be realistic: many organizations don’t have enough time, tools, or skilled people to do thorough mapping on their own. It’s crucial to honestly assess your internal capabilities before you begin. Do you have team members with the expertise to manage a mapping program? Do you have the budget for the necessary tools? Answering these questions will help you identify any gaps. Understanding these limitations allows you to plan accordingly, whether that means providing additional training, investing in new technology, or partnering with a solution that can automate discovery and help your team prioritize exposure without adding to their workload.
Let’s be honest: modern attack surfaces are messy. With cloud services, remote work, and countless connected devices, your organization’s digital footprint is likely sprawling and changing by the minute. Trying to map and manage this complexity can feel like trying to nail Jell-O to a wall. But it’s not impossible. The key is to move away from static, point-in-time assessments and adopt a more dynamic, continuous approach.
Managing a complex attack surface requires a strategy that can keep up with the pace of your business. It’s about having the right mindset, the right tools, and the right processes in place. Instead of getting overwhelmed by the sheer scale of it all, you can break the problem down into manageable pieces. By focusing on the core challenges—like dynamic environments and data accuracy—you can build a program that not only works but also scales as your organization grows. Let’s walk through four practical steps to get control over your complex attack surface.
Digital systems are in a constant state of flux, especially with the widespread use of cloud services and containers. These environments are designed to be agile, which is great for development but a real headache for security. Assets are spun up and down in minutes, making it nearly impossible for traditional, manual mapping efforts to keep up. This constant change means your attack surface map is often outdated the moment it’s created.
The solution isn’t to scan more frequently but to adopt tools and processes built for this dynamic reality. You need a system that provides continuous adaptation and discovery. This means moving beyond periodic snapshots and toward a real-time understanding of your environment, recognizing that cloud systems can introduce many layers of hidden weaknesses that require constant vigilance.
You can’t protect what you can’t see. Gaining clear, comprehensive visibility across your entire digital landscape is the foundation of effective attack surface management. Without it, you’re essentially flying blind, leaving gaps that attackers are more than happy to exploit. The right visibility solution goes beyond simple asset discovery; it provides a real-time, contextualized inventory of your external assets.
This is where a dedicated platform for Total Attack Surface Management becomes essential. These tools automate the discovery process, giving security teams the up-to-date information they need to identify and neutralize threats proactively. Instead of manually piecing together data from different sources, you get a single, unified view of your exposure, allowing you to act with confidence.
An inaccurate attack surface map is worse than no map at all. It creates a false sense of security, leading you to believe you’re protected when critical vulnerabilities remain exposed. Keeping your data accurate is a persistent challenge because new assets pop up and new weaknesses are discovered constantly. If your data isn’t current, your prioritization and remediation efforts will be focused on the wrong things.
To combat this, deploy automated asset discovery tools that continuously scan your network to identify and inventory all assets. This proactive approach ensures that your asset list is always current and comprehensive, preventing shadow IT and forgotten devices from becoming your next big security incident. Continuous identification is the only way to guarantee that nothing is overlooked and your security decisions are based on reality.
For large organizations, trying to map the entire attack surface at once is a recipe for failure. The scope is simply too large. A more effective strategy is to break the process down into smaller, more manageable parts. You could start by focusing on a single department, a specific geographic region, or a critical business application. This phased approach allows you to score early wins and build momentum.
This is where a framework like Continuous Threat Exposure Management (CTEM) comes into play. A core component of CTEM is Cyber Asset Attack Surface Management (CAASM), which focuses on creating a complete and accurate inventory of all your assets. By starting with a solid asset foundation, you can effectively scale your program. A platform like Hive Pro’s Uni5 Xposure provides this unified view, helping you manage your entire exposure management lifecycle from a single place.
Once you have a handle on the fundamentals, you can bring in more advanced technologies to make your attack surface mapping more efficient and effective. Modern security challenges, like sprawling cloud environments and a constant stream of new assets, require equally modern solutions. These tools don’t just speed up the process; they offer a depth of insight that manual methods simply can’t match. By integrating automation, AI, and real-time monitoring, you can move from a static, point-in-time map to a dynamic, living picture of your security posture. This allows your team to stop chasing yesterday’s vulnerabilities and start proactively defending against tomorrow’s threats. Let’s look at a few key technologies that can make a significant difference.
Think of the sheer volume of data your security tools generate daily. It’s impossible for any human team to analyze all of it effectively. This is where artificial intelligence and machine learning come in. These technologies are brilliant at sifting through vast datasets to identify subtle patterns, anomalies, and potential threats that would otherwise go unnoticed. Instead of just reacting to alerts, you can use AI to proactively identify vulnerabilities in your attack surface before they can be exploited. This approach helps you prioritize threats based on real risk, not just CVE scores. By automating much of this analysis, you free up your team to focus on strategic initiatives and complex threat hunting.
Securing cloud environments is a unique beast. Unlike on-premise infrastructure, the cloud is dynamic, and assets can be spun up or down in minutes. This creates a huge potential for misconfigurations, accidental data exposure, and other vulnerabilities that are easy to miss. Traditional security tools often fall short here. You need security measures designed specifically for the cloud that can keep up with its pace and scale. This means implementing best practices for cloud security and using tools that provide a clear, unified view across your multi-cloud and hybrid environments. Strong security postures in the cloud depend on continuous visibility and control over these ephemeral assets.
You can’t protect what you don’t know you have. That’s why automated asset discovery is a foundational piece of any modern security program. These tools continuously scan your networks—including on-prem, cloud, and remote environments—to identify and inventory every connected device, application, and service. This process ensures your attack surface map is always current and comprehensive, leaving no room for overlooked assets or shadow IT to create blind spots. Automating this discovery is crucial for maintaining an accurate picture of your total attack surface and is the first step toward managing it effectively. It turns a periodic, manual chore into a continuous, reliable process.
Your attack surface isn’t static; it changes with every new code deployment, software update, or employee device that connects to your network. An annual or quarterly scan is no longer enough. Real-time monitoring, often called Continuous Attack Surface Management (CASM), gives you a live view of your exposures as they evolve. This capability is essential for staying ahead of attackers who are constantly probing for new weaknesses. With a platform that provides continuous exposure management, you get immediate insight into how your risk profile is changing. This allows you to spot and remediate vulnerabilities in minutes or hours, not weeks or months.
Gathering attack surface intelligence is a huge step, but its real power comes from how you weave it into your daily security practices. Simply having a list of assets and vulnerabilities isn’t enough. You need to make that data actionable so it can inform your decisions, strengthen your defenses, and guide your team’s efforts. Integrating intelligence means moving it from a static report to a dynamic part of your security ecosystem.
This process turns raw data into a strategic advantage. When you connect intelligence to your security controls, incident response plans, and monitoring systems, you create a feedback loop that continuously refines your posture. It helps you answer critical questions like, “Are our defenses working against the threats we’re seeing?” and “Where should we focus our resources for the biggest impact?” By making intelligence a core component of your operations, you shift from a reactive stance—fixing things after they break—to a proactive one where you anticipate and neutralize threats before they can cause harm. This is how you build a resilient and confident security program.
Your internal vulnerability scans tell you where you have weaknesses. External threat intelligence tells you which of those weaknesses attackers are actively exploiting. The magic happens when you bring these two data sets together. Correlating intelligence means you can see your digital footprint just as an attacker does, connecting real-world threats from across the internet and the dark web to your specific assets. This context is everything. It allows you to move beyond a simple high/medium/low vulnerability score and focus on the threats that pose an immediate danger to your organization. This is the foundation of risk-based vulnerability and threat prioritization, ensuring your team spends its time on what truly matters.
You have firewalls, EDRs, and a dozen other security tools in place, but are they configured correctly and actually stopping threats? Attack surface intelligence gives you a map of potential entry points. You can use this map to validate your security controls by simulating real-world attack scenarios against your known exposures. By proactively testing your defenses, you can identify gaps before an attacker does. This process of adversarial exposure validation helps you understand if your tools are performing as expected and provides clear evidence to justify security investments. It’s about replacing assumptions with certainty and ensuring your defenses are prepared for potential threats.
An effective incident response (IR) plan relies on speed and accuracy, both of which depend on having a clear understanding of your environment. Attack surface intelligence provides your IR team with a detailed, up-to-date map of your digital assets, dependencies, and potential attack paths. When an incident occurs, your team won’t waste precious time trying to figure out what a compromised asset is or what it connects to. Instead, they can immediately access this information to understand the potential blast radius, isolate affected systems, and eradicate the threat more efficiently. Integrating this intelligence into your IR playbooks makes your response faster, more effective, and less disruptive to the business.
Your attack surface is not static; it changes every time a new employee joins, a new device connects, or a new application is deployed. That’s why a one-time assessment is never enough. You need to establish a system for continuous monitoring that constantly scans for new assets, services, and vulnerabilities. A total attack surface management program gives you an attacker’s-eye view of your organization in near real-time. This proactive approach ensures you’re always aware of your exposure and can quickly address new risks as they appear. It’s the key to maintaining a strong security posture in a dynamic environment and staying ahead of attackers.
Mapping your attack surface is a great first step, but how do you know if your efforts are actually making a difference? You need a clear way to measure your progress and demonstrate the value of your program. Tracking the right metrics shows you where you’re improving, where you need to focus, and how your work directly contributes to a stronger security posture. It’s about moving from simply identifying risks to actively reducing them and proving it with data.
To show real progress, you need to track KPIs that reflect both speed and effectiveness. Attack surface mapping helps you find and fix problems early, which is the best way to prevent attacks from happening in the first place. Start by measuring how quickly your team can identify and respond to new threats. Key indicators like Mean Time to Detect (MTTD) for new assets and Mean Time to Remediate (MTTR) for critical vulnerabilities are essential. You should also track the overall reduction in high-risk vulnerabilities over time. A consistently shrinking number of critical issues is a clear sign of success. Another great KPI is asset inventory coverage—what percentage of your known digital footprint is under continuous monitoring? Aiming for 100% coverage ensures you’re not leaving any doors open for attackers. A unified platform like Uni5 Xposure can give you a single dashboard to monitor these metrics.
Not all vulnerabilities are created equal. To use your resources wisely, you need to prioritize which issues pose the most immediate danger. By understanding your weak spots, you can focus on fixing the most critical ones first, saving valuable time and effort. Instead of just looking at the CVSS score, create metrics that add business context. For example, you can measure risk by combining a vulnerability’s severity with its real-world exploitability and the business criticality of the affected asset. This approach helps you prioritize threats that matter most. Tracking the reduction of your overall organizational risk score over a quarter or a year provides a high-level view of your program’s impact. This helps you effectively identify, measure, and manage your exposure to cyber threats.
Meeting regulatory requirements is a non-negotiable part of cybersecurity. Mapping your attack surface is crucial because it helps you meet industry rules and follow security standards like PCI DSS, HIPAA, or ISO 27001. Your mapping efforts provide the concrete evidence auditors need to see. To measure this, you can track your compliance gap—the percentage of assets that don’t meet a specific regulatory control. You can also create an “audit readiness” score to gauge how prepared you are for an upcoming assessment. The goal is to use your attack surface data to streamline compliance reporting, reducing the time and manual effort required to prove you’re meeting your obligations. This turns a stressful, periodic event into a continuous, manageable process.
An effective attack surface management program is never “done.” It’s a continuous cycle of improvement. To do attack surface mapping well, you should regularly identify and prioritize important assets, create a threat model, and perform consistent vulnerability checks. Start by establishing a baseline of your current attack surface and set realistic goals for reduction and remediation over the next quarter. Then, use automated tools to handle the heavy lifting of asset discovery and vulnerability scanning. This frees up your team to focus on strategic analysis and remediation. You can further refine your program by integrating public information and threat intelligence for a more complete picture of your exposure. Creating tight feedback loops between your security, IT, and development teams ensures that everyone is aligned and that vulnerabilities are fixed efficiently.
Isn’t this just another name for vulnerability scanning? That’s a great question because it gets to the heart of what makes this different. Think of it this way: a vulnerability scan is like checking the locks on all the doors of a house you already know about. Attack surface intelligence mapping is the process of first creating the complete blueprint of the entire estate, including forgotten sheds, underground tunnels, and windows left open, and then using real-world threat information to figure out which unlocked door a burglar is most likely to try first. It’s a much more strategic process that combines a complete asset inventory with contextual threat intelligence to show you your actual risk.
How can a small security team even begin to tackle this? It can definitely feel overwhelming, but you don’t have to map everything all at once. The key is to start with what matters most. Begin by focusing on your most critical, internet-facing applications and systems—the “crown jewels” of your organization. The goal is progress, not perfection on day one. This is also where automated tools become so valuable. They can handle the heavy lifting of continuous discovery and inventory, which frees up your team’s limited time to focus on analyzing the results and fixing the most significant risks.
What’s the most common blind spot you see when companies map their attack surface? Hands down, the biggest blind spots are the assets that aren’t officially managed by the IT or security teams. This includes “shadow IT,” like a marketing department spinning up a cloud server without approval, or a forgotten development server that’s still connected to the internet. Another huge area is third-party risk; your security is only as strong as the vendors you connect with. These unmanaged and unmonitored assets are often the path of least resistance for an attacker.
My company’s environment changes constantly. How can a map ever be accurate? You’ve hit on exactly why the old “point-in-time” assessment model is broken. You’re right, a map that’s only updated quarterly or annually is useless in a dynamic cloud or DevOps environment. The solution is to treat mapping as a continuous, living process, not a static project. By using automated discovery tools that constantly monitor your environment, you get a real-time view of your assets and exposures as they change. It’s about shifting from taking a snapshot to watching a live video feed.
Okay, I have a map of my attack surface. Now what? The map itself is just the starting point. Its real value comes from how you use it to make smarter, faster security decisions. The immediate next step is to use that intelligence to prioritize your remediation efforts, focusing on the weaknesses that pose the greatest actual threat to your business. You can also use the map to validate that your security controls are working as expected and to arm your incident response team with the detailed information they need to act quickly and effectively when an alert comes in.