Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Your antivirus software is the trusted gatekeeper of your digital world, silently working in the background to block threats. But what happens when that gatekeeper suddenly walks off the job? A widespread antivirus software outage recently showed us the answer, grinding critical industries to a halt and exposing just how fragile our reliance on a single tool can be. This wasn’t a minor glitch; it was a global stress test that revealed deep vulnerabilities in our infrastructure. For security professionals, it served as a powerful reminder that “set it and forget it” is a dangerous mindset. This guide will help you move beyond reacting to crises by providing a proactive framework to prepare for, respond to, and prevent the next outage.
An antivirus (AV) software outage happens when your primary line of defense against malware simply stops working. It’s not just a glitch; it’s a critical failure that leaves your systems wide open. Think of it as the security guard for your digital assets suddenly walking off the job without notice. This disruption means your protection against viruses, ransomware, and other cyber threats is gone, creating a dangerous blind spot in your security posture.
Understanding what an outage is and why it happens is the first step toward building a more resilient defense. It’s easy to set up AV software and assume it’s always running perfectly in the background, but that “set it and forget it” mindset can be costly. These outages can stem from a variety of issues, from simple software bugs to targeted attacks designed to disable your defenses. The key is to move from a reactive stance—scrambling when something breaks—to a proactive one where you anticipate these failures and have a plan in place. A comprehensive Threat Exposure Management platform can help you see these gaps before an attacker does.
So, what actually knocks your antivirus offline? The causes are often a mix of technical and human factors. Common culprits include software bugs that slip through development, conflicts with other programs installed on your systems, or even routine updates gone wrong. Sometimes, the cause is more malicious, like a cyberattack specifically designed to disable your security tools before launching a larger assault.
Human error also plays a significant role. A misconfigured setting or a delayed patch can easily lead to a system-wide failure. According to recent analyses, security issues and software failures are consistently the top causes of major outages. This highlights the need for robust software testing and quality assurance to catch potential problems before they impact your live environment and leave your organization vulnerable.
You can often spot an impending outage if you know what to look for. The most obvious sign is your antivirus software turning itself off automatically. If your team reports that the AV client is disabled or won’t start, that’s a major red flag. Another warning sign is a failure to update; if the software can’t download the latest virus definitions, its effectiveness drops dramatically.
Pay close attention to system performance alerts and user reports. Are devices running unusually slow? Are strange pop-ups appearing? These could indicate a conflict between your antivirus and another program, or worse, that malware has already slipped past your disabled defenses. Monitoring for unusual behavior in your security tools is critical for identifying potential failures before they become full-blown security incidents.
When your antivirus software fails, the impact isn’t contained to a single device. It creates a ripple effect across your entire network. A single unprotected endpoint can become the entry point for an attacker to move laterally through your systems, escalating a minor issue into a major breach. This single point of failure exposes your organization to a host of threats, from data-stealing malware to crippling ransomware attacks.
The consequences extend beyond the immediate technical vulnerabilities. An outage can compromise overall network security and threaten your data integrity, putting sensitive customer or company information at risk. This can lead to significant financial losses, reputational damage, and regulatory penalties. The impact of IT downtime from a security tool failure underscores why having a multi-layered defense is non-negotiable for modern organizations.
When a single piece of security software fails, the fallout isn’t contained to a few isolated networks. In our deeply interconnected world, one faulty update can trigger a global chain reaction, grinding essential services to a halt. The recent widespread outage caused by a single antivirus provider serves as a stark reminder of this vulnerability. It demonstrated how reliance on one tool can create a single point of failure with devastating consequences for industries worldwide. This event wasn’t just a technical glitch; it was a real-world stress test that revealed critical weaknesses in global infrastructure, impacting everything from travel and finance to healthcare and emergency response.
For security professionals, this is a clear call to action. It highlights the urgent need to move beyond reactive measures and adopt a more proactive and resilient security posture. Understanding your organization’s complete exposure and having a plan for when a primary defense fails is no longer optional. It’s about ensuring business continuity when the tools you depend on suddenly become the source of the problem.
The ripple effect of the outage on critical infrastructure was immediate and widespread. The aviation industry, for example, was thrown into chaos, with over 5,000 flights canceled globally as airlines lost access to essential systems. This wasn’t just an inconvenience; it was a complete shutdown of a vital economic artery. The disruption spread quickly to government services, transportation networks, and media outlets, illustrating how a single software flaw can paralyze the foundational systems that society relies on. This event exposed the fragility of a total attack surface that spans countless interconnected private and public entities, all dependent on a handful of software providers.
The financial sector felt the impact almost instantly. Major banks across the US, Canada, Australia, and other countries experienced disruptions to online banking and ATM services, locking customers out of their accounts. The economic damage was staggering, with the top 500 US companies alone facing an estimated $5.4 billion in losses. The provider’s stock price plummeted by over 11%, reflecting the massive loss of market confidence. For financial institutions, where trust and uptime are everything, this outage was a painful lesson in the importance of having a security framework that can withstand the failure of a single component and effectively prioritize exposure across critical assets.
Nowhere were the consequences more alarming than in healthcare. Hospitals across North America were forced to postpone non-urgent surgeries and appointments as they lost access to patient records and critical monitoring equipment. In some cases, even security systems went offline. In the UK, doctors’ offices were unable to view medical histories or issue prescriptions, putting patient safety at direct risk. This crisis showed that a software outage is not just an IT problem; it’s a human one. It underscores the need for a unified view of cyber risks in environments where digital systems are directly linked to patient care and well-being.
When every second counts, the failure of emergency services can be catastrophic. During the outage, 911 dispatch centers in several US states were disrupted, with New Hampshire’s system going down completely. In Copenhagen, the fire department could no longer receive automatic fire alerts, delaying response times when they were needed most. These failures highlight a critical vulnerability in our public safety infrastructure. It’s a powerful argument for continuous adversarial exposure validation to ensure that the systems designed to protect us are resilient enough to withstand the unexpected failure of a trusted security tool.
When your antivirus software goes down, it’s not just a minor technical glitch—it’s like leaving the front door of your business wide open. The consequences are immediate and can ripple through your entire organization. Attackers are always scanning for weaknesses, and an AV outage is a golden opportunity for them to strike. Understanding the specific risks is the first step toward building a more resilient security posture that doesn’t rely on a single point of failure. Let’s look at what’s immediately on the line when your primary defense is offline.
The moment your AV fails, every connected device becomes a potential entry point for threats. Endpoints, servers, and critical network infrastructure lose their first line of defense against malware, ransomware, and zero-day exploits. This instantly broadens your total attack surface, turning theoretical vulnerabilities into active, exploitable gaps. Since security issues are already a leading cause of outages, an AV failure compounds the problem by removing the very tool meant to prevent them. Without it, your team is flying blind, unable to detect or block malicious activity in real time, leaving your most valuable systems completely unprotected.
Your systems house your most critical asset: data. An AV outage creates a direct path for attackers to access and exfiltrate sensitive information, including customer records, financial data, and intellectual property. Even a brief lapse in protection is enough for sophisticated malware to infiltrate your network, encrypt files, or quietly send data to an external server. While other security layers exist, the AV is a fundamental safeguard. Its failure means you can no longer be confident that your data is shielded from unauthorized access or corruption, putting your business and your customers at significant risk.
An AV outage isn’t just a security problem; it’s a compliance nightmare. Regulations like GDPR, HIPAA, and PCI DSS mandate continuous monitoring and protection of sensitive data. A downed antivirus solution can be interpreted as a failure to maintain adequate security controls, leading to a breach of compliance. This can result in steep fines, mandatory public disclosures, and lasting damage to your reputation. Organizations must be prepared to get systems back online as quickly as possible to minimize operational downtime and demonstrate due diligence to auditors. Proving you have a plan to manage exposure is key.
Beyond data and compliance, an AV failure directly threatens your ability to do business. A successful malware or ransomware attack can bring your operations to a grinding halt, shutting down production lines, disabling customer service platforms, and disrupting your entire supply chain. The resulting downtime leads to lost revenue, decreased productivity, and frustrated customers. Building more resilient IT systems means having a strategy that accounts for tool failure. A comprehensive view of your cyber risks, like the one provided by the Uni5 Xposure Platform, helps you understand the business impact of an outage and prioritize your response to keep things running.
An antivirus outage can feel like a nightmare scenario, but it doesn’t have to be a catastrophe. With the right preparation, you can build a security posture that’s resilient enough to handle unexpected failures. Instead of just reacting when things go wrong, you can create a proactive strategy that minimizes downtime and keeps your organization protected. The key is to focus on building layers of defense and having clear plans in place before you ever need them. Here’s how you can get started.
Relying on a single security tool is like having only one key to your house—if you lose it, you’re locked out. A single point of failure is a massive risk, which is why having backup security solutions is non-negotiable. This doesn’t just mean having a second antivirus product on standby. It’s about creating a diverse, layered security stack. Think endpoint detection and response (EDR), robust firewalls, and network monitoring tools that can pick up the slack if one component fails. By addressing potential failure points across your infrastructure, you can build more resilient IT systems that reduce the severity of any single outage. A unified platform can give you a clear view of your entire security stack, helping you spot gaps where a backup solution is needed.
We’ve all seen it happen: a buggy software update takes down a critical system. To prevent this, you need to treat every update with caution and control. Instead of rolling out a new patch to your entire organization at once, establish a phased deployment protocol. Start with a small, non-critical group of systems to see if any issues arise. It’s also essential to have a documented rollback plan ready to go. If an update causes problems, you need to be able to revert to the previous stable version quickly and efficiently. Implementing thorough testing procedures before a full deployment can help you catch bugs before they cause a widespread outage, turning a potential crisis into a minor hiccup.
You can’t protect what you can’t see. Continuous monitoring is your early warning system, helping you spot the subtle signs of trouble before they escalate into a full-blown outage. This means keeping a close eye on the health of your security agents. Are services stopping unexpectedly? Is CPU usage spiking? Has the volume of detected threats suddenly dropped to zero? These could all be indicators that your antivirus software is failing. Using an observability platform to proactively identify and resolve issues is critical. Centralizing this data gives you a single, unified view of your cyber risks, allowing your team to act on intelligence, not intuition.
Your security tools might look fine on a dashboard, but are they actually working as expected? Don’t wait for a real attack to find out. Regularly testing and validating your defenses is like running a fire drill—it ensures everything works when you need it most. Use tools for Adversarial Exposure Validation to simulate real-world attack scenarios and see how your security stack responds. Can your EDR solution detect a threat if your primary AV is disabled? Do your monitoring systems trigger the right alerts? This process helps you find and fix weaknesses in your defenses before an attacker can exploit them, ensuring your backup systems and response plans are truly effective.
An antivirus outage is a stark reminder that a single point of failure can bring your entire security posture down. Instead of just reacting to incidents, the goal is to build a framework that anticipates and withstands them. A resilient security strategy isn’t about having one perfect tool; it’s about creating a system of overlapping defenses and intelligent processes that keep you protected, even when one component fails. This proactive approach is what separates a manageable incident from a full-blown crisis. Let’s look at how you can construct a more durable defense.
Relying solely on antivirus software is like putting a single lock on your front door and leaving all the windows open. A true defense-in-depth strategy involves layering multiple security controls. Think of it as a series of checkpoints: firewalls, intrusion detection and prevention systems (IDPS), endpoint detection and response (EDR), and secure web gateways all work together. If one layer fails or is bypassed, another is there to catch the threat. To make this work, you need to implement thorough and automated testing procedures to ensure each layer is functioning correctly. This multi-layered approach significantly reduces your attack surface and contains threats before they can cause widespread damage.
What happens if your primary security tool goes offline? Redundancy is your answer. It’s about having a solid Plan B for your critical systems and processes. This goes beyond just having backup data; it means having failover security solutions ready to deploy. By addressing key failure points—from hardware failures and software bugs to human error—you can build more resilient IT systems that minimize the impact of an outage. This could involve having a secondary EDR solution on standby or a cloud-based security service that can be activated instantly. The key is to plan for failure so that when it happens, your team can switch to a backup system smoothly without leaving your organization exposed.
Migrating security functions to the cloud can introduce a new level of resilience. Cloud-native security platforms often come with built-in redundancy and scalability that can be difficult and expensive to replicate with on-premise infrastructure. While cloud service failures can happen, top-tier providers invest heavily in reliability and have geographically distributed data centers to minimize downtime. Using cloud-based security tools for things like email filtering, identity management, or even SIEM can distribute your risk. This way, an issue with your on-premise AV doesn’t take down your entire security stack. It’s about strategically using the cloud to create a more flexible and durable security architecture.
Traditional security tools often rely on known signatures, which makes them blind to novel threats and vulnerable during an outage. This is where AI and machine learning change the game. Modern security platforms use AI to analyze behavior, identify anomalies, and detect threats without relying on a static database. This proactive approach is the core of Continuous Threat Exposure Management (CTEM). Instead of just reacting to known vulnerabilities, a CTEM program integrates real-time threat detection and prioritization. This allows your team to focus on the most critical risks and adapt your defenses continuously, ensuring you have intelligent oversight even if your primary AV tool is compromised.
When your primary defense goes down, it’s not a matter of if you’ll need a plan, but how fast you can execute it. An active antivirus outage is a high-stakes scenario where every second counts. Having a clear, pre-defined game plan is what separates a manageable incident from a full-blown crisis. Your team needs to know exactly what to do, who to call, and which tools to use to contain the threat and restore your defenses. This isn’t about improvisation; it’s about following a well-rehearsed script designed to minimize damage and downtime. The following steps will help you build a response plan that is both robust and practical, ensuring you can move from reactive panic to proactive control. A comprehensive approach to threat exposure management includes planning for these worst-case scenarios.
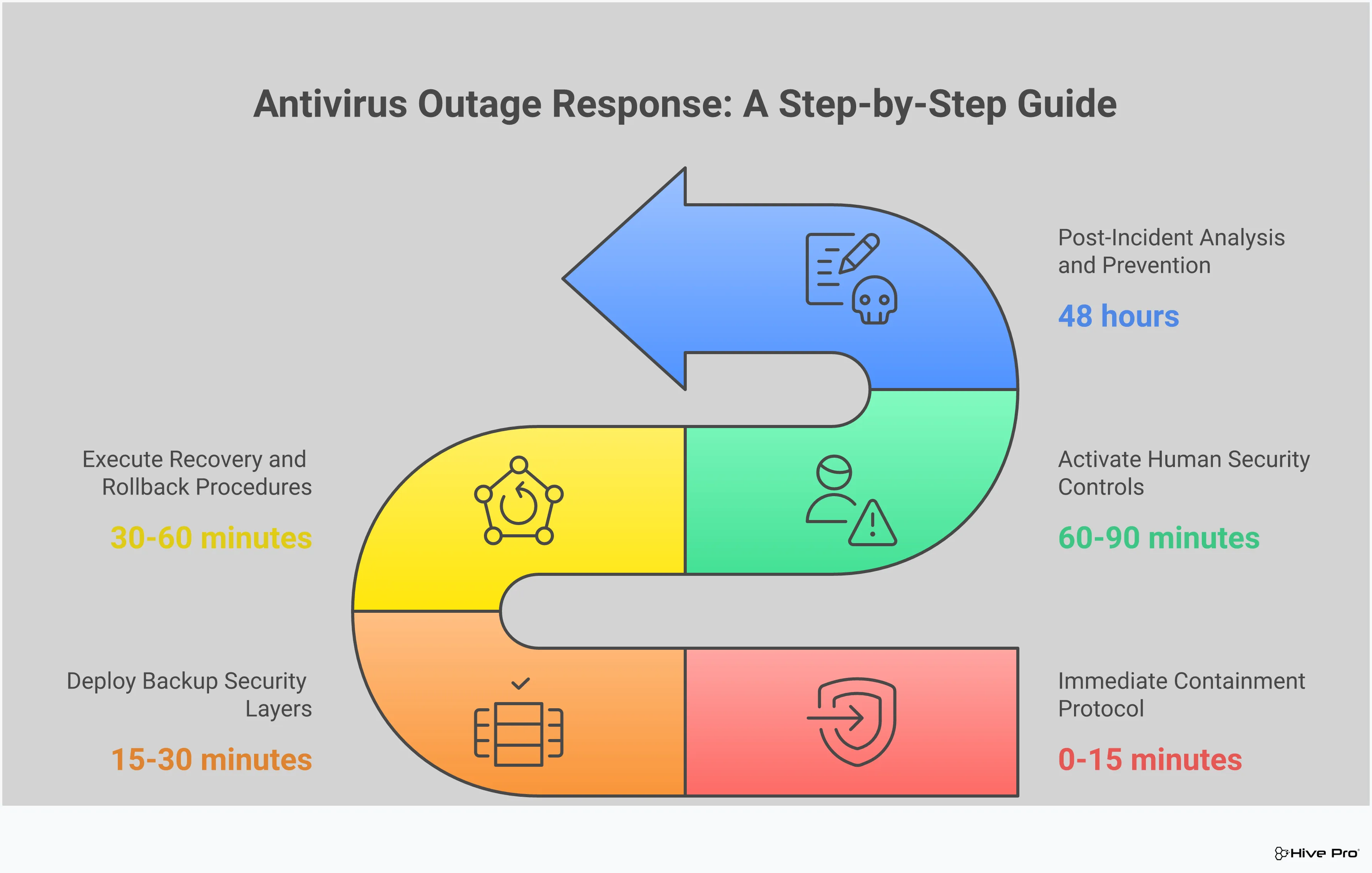
The moment you confirm an outage, your immediate response protocol should kick in. This isn’t the time to figure things out—it’s time to act. Your first step is to activate your incident response team and establish clear lines of communication. The protocol should detail how to quickly assess the scope of the outage: Which systems are affected? Is it a specific segment or the entire network? The next move is containment. Isolate the affected endpoints or network segments to prevent potential threats from spreading while your primary defense is offline. This protocol should be documented, accessible, and regularly reviewed so that everyone on the team knows their role and can perform it without hesitation.
With your antivirus down, your other security layers become your front line. This is where a defense-in-depth strategy proves its worth. Your game plan must include deploying alternative security measures to fill the gap. This could mean heightening the sensitivity of your Endpoint Detection and Response (EDR) tools, applying stricter firewall rules, or limiting outbound traffic to known-good destinations. If you have a secondary AV solution or other endpoint controls, now is the time to ensure they are fully active. Having a complete picture of your total attack surface is critical here, as it helps you identify which alternative controls will be most effective for your exposed assets.
Your recovery plan is your roadmap back to a secure state. It should provide a step-by-step process for restoring the antivirus service as quickly and safely as possible. This might involve rolling back a faulty update, applying a patch from the vendor, or, in a worst-case scenario, switching to a backup provider. IT teams must be prepared to get systems back up and running to minimize operational downtime. To be effective, this plan can’t just live in a document; it needs to be tested. Regular drills and simulations, like those used in adversarial exposure validation, ensure your team can execute the plan flawlessly under pressure and identify any weaknesses before a real incident occurs.
During an outage, silence creates uncertainty and fear. Clear, consistent communication is essential for managing the situation both internally and externally. Your plan should outline who needs to be notified, what information they need, and how often they should receive updates. Internally, keep leadership, IT staff, and other relevant departments informed about the status, the steps being taken, and the expected timeline for resolution. If the outage could impact customers or partners, your external communication strategy should be ready to go, providing transparent and honest updates. This proactive approach builds trust and shows you are in control of the situation.
Technology is a powerful defense, but it’s not foolproof. When a tool like your antivirus software goes down, your team becomes your most critical security asset. Investing in their education turns your entire organization into a vigilant, proactive defense layer. A well-informed team can spot threats that automated systems might miss, especially during an outage. This isn’t just about running a few training sessions; it’s about building a security-first culture where everyone understands their role in protecting the organization’s data and systems. For security leaders, this shift from viewing employees as a liability to seeing them as a core part of the defense strategy is essential. By making security a shared responsibility, you create a resilient organization that is prepared for any disruption. This human firewall is your best bet for containing threats and minimizing damage when your primary technical controls are unavailable, ensuring business continuity and protecting your reputation. It’s a proactive stance that moves beyond simple compliance and fosters a genuine partnership between your security team and the rest of the company.
A formal security awareness program is the foundation of user education. These programs should be more than just an annual slideshow. Effective training involves regular, engaging sessions that cover the latest threats, from sophisticated phishing emails to social engineering tactics. User education in cybersecurity is crucial for preventing threats that target human behavior. By simulating real-world attacks and providing clear guidance, you can build a program that equips your team to recognize and react to suspicious activity, turning a potential vulnerability into a strong defense.
Your team needs clear, simple rules to follow every day. Training employees on malware prevention is a critical step in protecting your business. Focus on essential habits like using strong, unique passwords, enabling multi-factor authentication, and practicing safe browsing. Teach them how to identify suspicious links and attachments before clicking. Providing this knowledge gives your employees the confidence to make smart security decisions, effectively reducing the risk of human error and strengthening your overall security posture, even when primary defenses are offline.
When an employee spots something unusual, how easy is it for them to report it? A complicated or intimidating process will discourage them from speaking up. Your goal is to make incident reporting as simple as sending a message. Establish a clear, no-blame channel where team members can quickly flag potential threats. This allows your security team to investigate and respond immediately, containing issues before they escalate. A streamlined incident reporting process not only speeds up response times but also reinforces a culture where everyone feels responsible for security.
The threat landscape is constantly changing, which means your training needs to be a continuous effort. A single training session can quickly become outdated. Sustainable security depends on regular updates and refreshers that keep your team informed about new attack vectors and evolving threats. You can use real-world examples from recent events or share insights from resources like threat advisories to keep the content relevant. Committing to ongoing education ensures your team’s skills stay sharp and your human firewall remains a formidable defense against any threat.
While you can’t predict the future, you can certainly prepare for it. Moving from a reactive to a proactive security posture is the key to minimizing the impact of a potential antivirus outage. It’s about building a resilient framework that can withstand unexpected failures and keep your organization protected. Instead of just responding to threats, a proactive approach helps you anticipate them. This involves a combination of rigorous testing, clear processes, and a commitment to getting better every day. By focusing on these core areas, you can manage risk more effectively and reduce the chances of the next outage catching you off guard.
Think of system audits as a regular health check for your security infrastructure. To prevent outages caused by software bugs or misconfigurations, you need to implement thorough and consistent testing procedures. This means going beyond basic scans and incorporating automated testing and continuous integration practices into your workflow. Regular audits help you find and fix vulnerabilities before they can be exploited or cause system failures. By continuously testing your defenses, you can validate that your security controls are working as expected and identify gaps in your coverage. This is a core part of a strong adversarial exposure validation strategy, ensuring your systems are truly prepared for real-world threats.
During a crisis, confusion is your worst enemy. That’s why clear, accessible documentation is non-negotiable. It’s critical to have a strategy in place to address outages, and that strategy must include documented remediation processes. Your team needs a clear playbook that outlines roles, responsibilities, and step-by-step instructions for responding to an AV failure. This documentation should be a living resource, regularly updated after drills, tests, or real incidents. It should cover everything from your network architecture to your incident response plan, ensuring that anyone on your team can step in and act decisively when time is of the essence.
A strong security policy is the foundation of a resilient defense. This goes beyond a simple list of rules; it’s a comprehensive framework that guides your team’s decisions and actions. Your policy should define clear protocols for everything from patch management and software updates to vendor risk assessment and incident response. Adopting robust software testing practices, including automated testing and regression testing, should be a formal part of this policy to catch bugs before they cause downtime. A platform that provides clear vulnerability and threat prioritization can help you focus your policies on the risks that matter most, ensuring your efforts are directed where they can have the greatest impact.
Security isn’t a one-and-done project; it’s an ongoing process of learning and adapting. The goal is to create a feedback loop where you constantly refine your defenses based on new information and experiences. After any security event—or even a close call—conduct a thorough post-mortem to understand the root cause and identify areas for improvement. By understanding what went wrong, you can enhance the reliability and resilience of your technology infrastructure. This mindset is at the heart of a Continuous Threat Exposure Management (CTEM) program, which helps you transform security from a reactive guessing game into a confident, proactive strategy.
My AV vendor promises high uptime. Why is planning for an outage so critical? Even a promise of 99.9% uptime still leaves room for hours of potential downtime over a year, and as we’ve seen, it only takes minutes for a failure to have a global impact. The issue isn’t just about one tool failing; it’s about the chain reaction it can cause across your operations and even in the services you depend on. Planning for an outage is about accepting that no single tool is perfect and building a security strategy that can withstand a failure, not just hope it never happens.
What’s the most important first step to take during an active AV outage? Your immediate priority is containment. Before you even begin to diagnose the problem or start the recovery process, you need to limit the potential damage. This means isolating the affected systems from the rest of your network as quickly as possible. By creating a barrier, you prevent any malware that might slip through from spreading laterally and turning a localized problem into a network-wide crisis.
Isn’t having an EDR solution enough of a backup if our AV fails? While an Endpoint Detection and Response (EDR) solution is a crucial part of a modern security stack, it’s not a simple replacement for your antivirus. EDR and AV are designed to do different things and catch threats in different ways. True resilience comes from a multi-layered defense where different tools cover each other’s blind spots. Relying on just one backup tool is better than nothing, but a truly strong framework has several overlapping layers of protection.
How can we prevent a faulty software update from causing an outage in the first place? The best way to avoid a bad update taking down your entire environment is to use a phased rollout approach. Instead of deploying a patch to every machine at once, start with a small, controlled group of non-critical systems. This lets you monitor for any issues in a safe environment. Just as important is having a documented rollback plan ready to go, so if the update does cause problems, you can revert to the last stable version quickly and without panic.
Beyond technology, what’s the most effective way to strengthen our defense against the fallout from an outage? Invest in your people. When a technical control fails, your team becomes your primary line of defense. A security-aware culture where employees are trained to spot and report suspicious activity is incredibly powerful. This “human firewall” can catch threats that automated systems might miss during a critical gap in coverage. Making security a shared responsibility across the organization is one of the most effective ways to build a truly resilient defense.