Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
Many security teams believe their existing tools have them fully covered. With a firewall, endpoint protection, and a vulnerability scanner, it’s easy to assume you can see everything that matters. This is one of the most dangerous myths in cybersecurity today. These tools often operate in silos, creating significant blind spots where threats can hide. Your true attack surface includes forgotten cloud assets, shadow IT, and third-party connections that your traditional tools miss entirely. This article cuts through the noise to debunk the common myths that create a false sense of security, helping you understand your real attack surface exposures and build a defense strategy based on reality, not assumptions.
Before we get into the specifics of managing exposures, let’s make sure we’re on the same page about what an attack surface actually is. Think of your organization as a fortress. Your attack surface is the sum of all its doors, windows, secret passages, and weak points in the walls—every single spot an attacker could use to get inside. It’s the complete picture of your company’s exposure to cyber threats. This isn’t just about your servers and software; it includes everything from your cloud infrastructure and employee laptops to the people who use them. Understanding this entire landscape is the first step toward building a solid defense.
Let’s break it down. Your attack surface is the total of all possible entry points an unauthorized user could exploit to access your systems and data. This includes your hardware, software, cloud assets, and even the human element, like employees who might fall for a phishing scam. Every device connected to your network, every line of code in your applications, and every employee with access to sensitive information contributes to your attack surface. The more assets you have, the larger your surface becomes, creating more potential opportunities for attackers. A complete view of your total attack surface is essential because you simply can’t protect what you can’t see.
Your attack surface isn’t just one big thing; it has different dimensions. The digital attack surface includes all your internet-facing assets, like websites, web applications, cloud storage, and APIs. These are the most visible and frequently targeted points. Then there’s the internal attack surface, which consists of assets inside your network perimeter—think employee workstations, on-premise servers, and internal databases. Finally, and just as important, is the human attack surface. This involves your employees, contractors, and partners who can be targeted through social engineering tactics like phishing to gain credentials and access your network from the inside. Each area requires a different defensive approach.
Exposures are the specific vulnerabilities and weaknesses that exist across your attack surface. Attackers are always looking for the path of least resistance, and they often find it in predictable places. Common hiding spots include unpatched software, misconfigured cloud settings, weak or stolen credentials, and forgotten or unmanaged devices known as “shadow IT.” Third-party vendors with access to your network can also introduce significant risk. Attackers exploit these gaps to steal data, disrupt operations, or deploy ransomware. The key is to find and address these weak spots before they do, which requires a proactive approach to vulnerability and threat prioritization.
Every unmanaged exposure is like an unlocked door waiting for an intruder. As your organization grows—adding more cloud services, remote employees, and connected devices—your attack surface expands, making it harder to track every potential weakness. This growth can quickly overwhelm security teams, who are often flooded with thousands of low-level alerts from various tools. This “alert fatigue” makes it difficult to focus on the threats that truly matter. By shifting from a reactive vulnerability-patching cycle to proactive exposure management, you can cut through the noise. This approach helps you identify and prioritize the most critical risks, allowing your team to focus its efforts where they will have the biggest impact on your security posture.
Understanding what an attack surface is feels like step one. But the real question is, why should you dedicate time and resources to actively managing it? The simple answer is that a neglected attack surface is a welcome mat for threats. Proactive management isn’t just about patching vulnerabilities; it’s about building a resilient security posture that protects your operations, reputation, and bottom line. It’s the difference between constantly reacting to fires and preventing them from starting in the first place. By getting a handle on your exposures, you can make smarter, more strategic decisions that reduce risk across the entire organization.
When an attacker exploits an exposure, the consequences go far beyond the technical fix. Think about the operational chaos: critical systems go down, productivity grinds to a halt, and customer trust evaporates. By minimizing unnecessary data exposure, you can reduce your attack surface and lessen the potential impact of a ransomware attack. It’s not just about preventing a breach but also about containing the damage if one occurs. Organizations that invest in adversarial exposure validation see tangible results, with some reporting a 47% improvement in their mean time to detection for critical threats. This speed can be the deciding factor between a minor incident and a major crisis.
Compliance isn’t just a box to check; it’s a baseline for security that you’re expected to meet—and exceed. Regulations like GDPR, HIPAA, and PCI DSS all have stringent requirements for protecting data and managing system vulnerabilities. A well-managed attack surface is a core component of a defensible compliance strategy. But compliance also involves your team. Effective cybersecurity awareness programs help employees understand their crucial role in protecting the organization from breaches. When your team is trained to spot phishing attempts and handle data responsibly, they become part of your defense, strengthening your compliance posture from the inside out.
Let’s talk numbers. The financial fallout from a breach can be staggering, encompassing everything from regulatory fines and legal fees to the high cost of incident response and remediation. Threat activity is on the rise, with a recent Armis study finding that 68% of organizations saw an increase in threats in early 2023 compared to the previous year. This escalating risk is why the attack surface management market is projected to grow significantly. Investing in a robust exposure management program isn’t an expense; it’s a strategic move to protect your organization from financial devastation and preserve its long-term health.
Proactive management means shifting from a reactive stance to a forward-looking one. Attack Surface Management (ASM) is a continuous process that helps you find, understand, and protect all the digital assets an attacker could target. Instead of waiting for an alert, you’re constantly looking for weaknesses. This approach involves total attack surface management, where continuous monitoring helps you spot unusual activity—like a large number of files being encrypted—that could signal an active ransomware attack. By identifying and prioritizing your biggest risks before they can be exploited, you systematically reduce your organization’s overall exposure and build a more resilient defense.
When it comes to managing your attack surface, a few persistent myths can create a false sense of security, leaving dangerous gaps in your defenses. These misconceptions aren’t just wrong; they can actively undermine your security posture by encouraging complacency and misallocating resources. Believing you’re fully covered when you have significant blind spots is one of the fastest ways to become a target. Let’s clear the air and tackle four of the most common—and riskiest—myths head-on. By understanding where these ideas fall short, you can build a more realistic and resilient security strategy. This isn’t about pointing fingers; it’s about getting real about the challenges we all face and finding a smarter path forward. Moving past these myths is the first step toward a proactive approach that truly reduces your organization’s exposure.
It’s tempting to think of security as a checklist: deploy a firewall, install antivirus, and you’re done. But this mindset is incredibly dangerous. Your attack surface is not static; it changes every time a new employee joins, a new device connects, or a new application is deployed. As one expert panel noted, “security requires unceasing effort, and fixing things and adapting to new threats is essential.” True security is a continuous cycle of discovery, assessment, and response. You need a program that provides total attack surface management by constantly scanning for new assets and exposures. Security isn’t a one-time project; it’s an ongoing commitment to vigilance.
Moving to the cloud offers incredible benefits, but it doesn’t outsource your security responsibilities. While cloud providers secure the underlying infrastructure, you are responsible for securing everything you put in the cloud. This is known as the shared responsibility model. Misconfigurations, overly permissive access, and unpatched applications in your cloud environment are common entry points for attackers. As security firm Corelight points out, “the network is where unknown vulnerabilities often reside, and cloud services require diligent management to ensure security.” Assuming the cloud is secure by default ignores your role in the partnership and leaves a massive part of your modern attack surface completely exposed.
Many organizations have a collection of security tools, each designed to protect a specific area. The problem is that these tools often operate in silos, creating blind spots where exposures can hide. You might have a great endpoint solution and a solid network scanner, but what are they missing between them? Research from SecurityMetrics found that “68% of organizations were unaware of the vulnerabilities present in their systems,” highlighting the gaps left by disconnected tools. Relying on a patchwork of solutions can lead to a fragmented view of your risk. A unified exposure management platform is essential for seeing the complete picture and understanding how different vulnerabilities connect to create real-world threats.
Placing the entire burden of security on a single team is a recipe for failure. Every employee has a role to play in protecting the organization. Developers writing code, IT teams configuring systems, and even marketing staff using third-party apps all make decisions that impact the company’s attack surface. As XM Cyber explains, the idea that security is solely the security team’s concern “underestimates the role that every employee plays in maintaining security.” A strong defense requires a culture of security where everyone feels a sense of ownership. When teams collaborate, they can identify and remediate exposures much faster and more effectively.
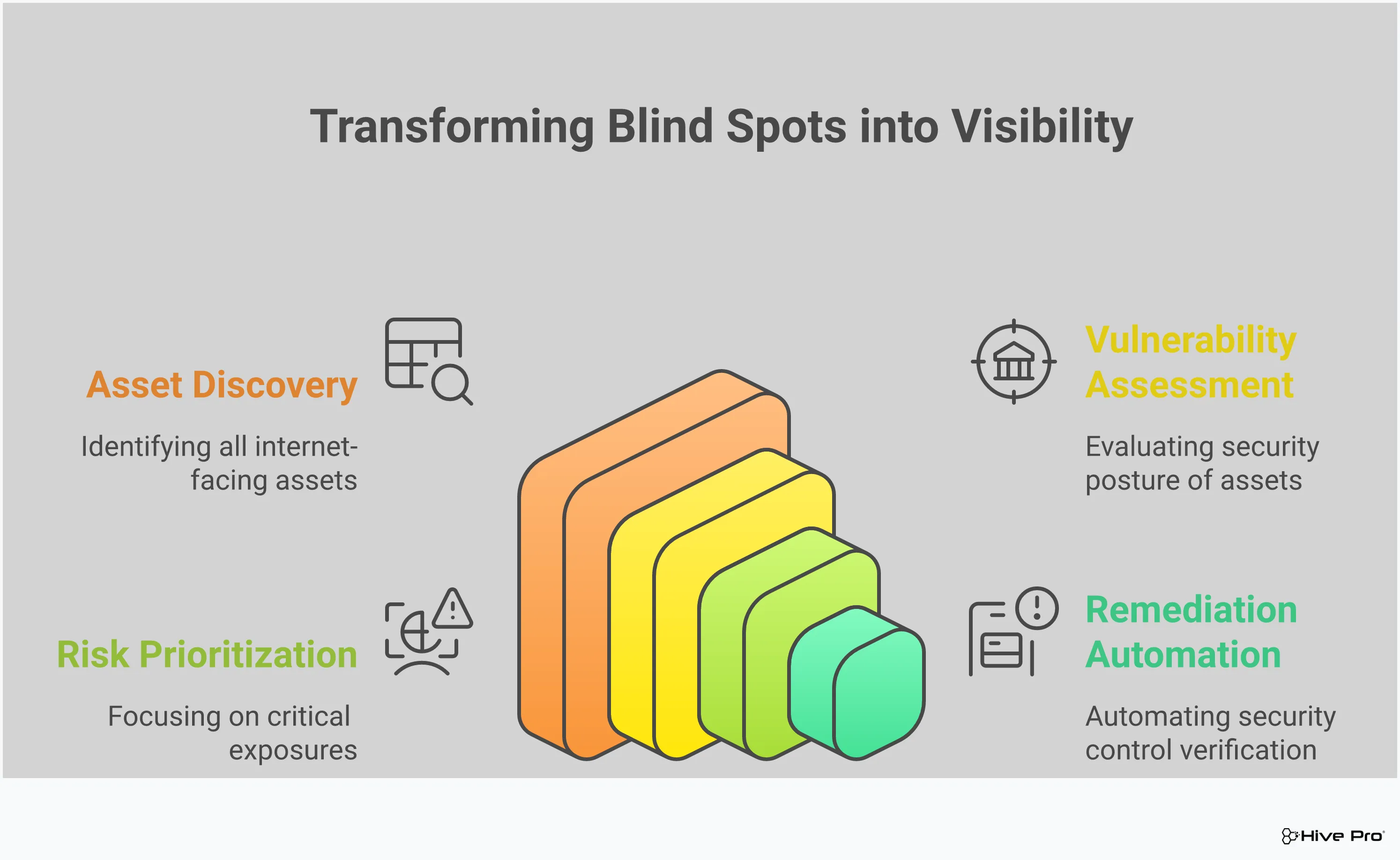
Effective exposure management isn’t a single action but a continuous cycle. It’s about creating a system that gives you a constant, clear picture of your security posture so you can act with confidence. Breaking it down into core parts helps make the process more manageable and ensures you cover all your bases. Think of it as building a strong foundation—each part supports the others to create a resilient defense strategy that adapts as your organization and the threat landscape evolve. This approach helps you move from a reactive stance, where you’re always playing catch-up, to a proactive one where you’re in control.
You can’t protect what you don’t know you have. The first step is to get a complete and accurate inventory of every asset across your entire digital footprint. This goes far beyond just servers and laptops. We’re talking about everything from cloud instances and applications to IoT devices and user accounts. This isn’t a one-time checklist; it’s a continuous process. Your environment is always changing, so you need a way to constantly discover your full attack surface as it expands and shifts. This complete visibility is the bedrock of your entire security program, providing the context you need for every decision that follows.
Once you have a map of your assets, the next step is to understand the risks associated with each one. A framework for assessing risk helps you move from a simple inventory list to a strategic overview of your security landscape. This involves looking at each asset and asking critical questions. How sensitive is the data it holds? How accessible is it from the internet? How critical is it to your daily business operations? By evaluating these factors, you can begin to understand the potential business impact of an exposure on any given asset, which is essential for making smart, risk-informed decisions.
Let’s be realistic: you can’t fix every single vulnerability at once. Your team’s time and resources are finite, so you have to focus on what matters most. Effective prioritization means moving beyond just technical severity scores. Instead, you should concentrate on the exposures that pose the greatest threat to your specific business goals. By combining asset criticality, threat intelligence, and vulnerability data, you can focus on imminent risks and attacks that could cause real damage. This approach helps you direct your remediation efforts where they will have the biggest impact, reducing your overall risk much more efficiently.
Your attack surface is dynamic. New devices connect, software is updated, and configurations change every day. A security assessment is outdated almost as soon as it’s completed. That’s why continuous monitoring is non-negotiable. You need automated tools that provide real-time visibility into your environment, alerting you to new assets, misconfigurations, and emerging threats as they happen. This creates a proactive feedback loop, allowing you to find and fix weak spots before they can be exploited. It transforms your security program from a reactive, fire-fighting exercise into a forward-looking, strategic operation that keeps pace with your business.
Knowing where your exposures are is half the battle; the other half is building a robust defense to protect them. A strong security strategy isn’t about a single tool or policy. It’s about creating layers of defense that work together to reduce your attack surface and make it much harder for attackers to succeed. By focusing on a few core areas, you can significantly strengthen your security posture and move from a reactive stance to a proactive one. These strategies are foundational elements of a modern security program, and they all contribute to a more resilient and defensible environment. Think of it less like building a single, impenetrable wall and more like designing a fortress with multiple checkpoints, guards, and response plans. Each layer is designed to slow down, detect, and stop an attacker, giving your team the advantage. A comprehensive platform like Uni5 Xposure can help unify these efforts by providing a single view of your risks, but the principles themselves are universal and can be applied across any organization. Let’s walk through five key strategies you can implement to build a stronger, more intelligent defense that adapts to the threats you face.
Think of your network as a large, open-plan office. If someone unwanted gets in the front door, they can wander anywhere they please. Network segmentation is like building walls and locked doors inside that office. By dividing your network into smaller, isolated zones, you can contain a breach if one occurs. If an attacker compromises one segment, they can’t easily move laterally to access critical assets in another. This containment strategy is crucial for limiting the blast radius of an attack and gives your security team more time to detect and respond to the threat before it spreads across the entire organization.
Not everyone needs the keys to the entire kingdom. Implementing strict access controls is about ensuring users and systems only have the permissions necessary to perform their specific functions. This is the principle of least privilege in action. Use tools like multi-factor authentication (MFA) to add a critical layer of verification and web application firewalls (WAFs) to protect your apps from common attacks. By carefully managing who can access what, you drastically reduce the risk of both accidental data exposure and malicious attacks from compromised accounts. Every access point should be treated as a potential vulnerability that needs to be secured.
A simple misconfiguration can be the one crack an attacker needs to slip through your defenses. Weak settings, default passwords, and unnecessary open ports are common weak spots that are easily exploited. Mastering your configuration management means establishing secure baselines for all your systems and continuously auditing them for deviations. Regular checks can help you identify and fix these vulnerabilities before they become a problem. This isn’t a one-time task; it’s an ongoing process of digital hygiene that ensures your infrastructure remains hardened against evolving threats and human error.
You have firewalls, endpoint protection, and detection systems in place, but do they actually work as expected? You can’t afford to just assume they do. You need to actively test and validate your security controls to ensure they are effective against real-world attack techniques. This is where practices like penetration testing and breach and attack simulation come in. By simulating attacks, you can identify gaps in your defenses, understand the potential impact of an exploit, and prioritize remediation efforts. This process of adversarial exposure validation turns theoretical security into proven, battle-tested defense.
The old security model of a hard outer shell with a soft, trusted interior is no longer effective. In a zero-trust model, you don’t automatically trust any user or device, regardless of whether they are inside or outside your network perimeter. The guiding principle is “never trust, always verify.” Every single access request must be strictly authenticated, authorized, and encrypted before being granted. Adopting a zero-trust architecture is a fundamental shift that treats every part of your network as potentially hostile, which significantly reduces the risk of unauthorized access and lateral movement.
Having a solid strategy is one thing, but executing it requires the right set of tools. The good news is that there are powerful technologies designed to help you get a handle on your attack surface and manage exposures effectively. Think of these tools not as a replacement for your team’s expertise, but as a way to amplify their efforts, automate the tedious work, and provide the clarity needed to make smart, fast decisions. Let’s walk through some of the key technologies that can make a real difference in your security program.
If you feel like you’re drowning in security data from dozens of different tools, you’re not alone. Unified exposure management platforms are designed to solve this exact problem. They help security teams deal with the huge amount of information they get by showing them what truly matters for the business. Instead of juggling multiple dashboards, these platforms consolidate data from across your entire environment—from your network to the cloud—into a single, coherent view. This allows you to see how different vulnerabilities and assets connect, helping you prioritize risks based on their potential business impact. A platform like Hive Pro’s Uni5 Xposure gives you that unified view to transform reactive work into confident, proactive action.
Vulnerability assessment tools are the workhorses of many security programs. They scan your systems, applications, and networks for known weaknesses, like outdated software or misconfigurations. It’s important to remember that vulnerability management is about fixing known software flaws, while attack surface management is about seeing and controlling all your assets and their access. These tools are fantastic at identifying specific issues, but their real power is unlocked when their findings are put into a broader context. A great vulnerability and threat prioritization process considers not just the severity of a flaw, but also the importance of the asset it’s on and whether it’s actively being exploited in the wild.
Think of a SIEM as your security operations center’s central nervous system. SIEM systems collect and analyze security data from across the organization, providing real-time visibility into potential threats and enabling faster response times. They gather logs and event data from firewalls, servers, and other devices, looking for patterns or anomalies that could signal an attack. While a SIEM is primarily focused on real-time threat detection and incident response, the data it collects is incredibly valuable for understanding your attack surface. It can show you which assets are being targeted most often, helping you refine your defensive priorities.
Finding vulnerabilities is only half the battle; you also have to fix them. With thousands of potential exposures, manual remediation just isn’t scalable. This is where automated tools come in. They help manage the attack surface by quickly finding, analyzing, and fixing vulnerabilities, which saves time and effort. Automation can handle tasks like patching systems, updating configurations, or even isolating a compromised device from the network. By automating these routine but critical tasks, you free up your security team to focus on more complex threats and strategic initiatives, like validating your security controls against real-world attack scenarios.
The world of exposure management is growing—and fast. The global attack surface management market is projected to grow at a compound annual growth rate of 31.3% from 2024 to 2030, which tells you just how critical this area has become. Looking ahead, we can expect to see even more intelligence and automation built into these tools. AI and machine learning will play a bigger role in predicting where the next attack might come from and identifying complex attack paths that a human analyst might miss. The future is about moving from a reactive to a predictive posture, powered by cutting-edge threat intelligence from research teams like HiveForce Labs.
Technology is a powerful ally in managing your attack surface, but it’s only one piece of the puzzle. Your biggest asset—and sometimes your most unpredictable variable—is your people. A misconfigured server can be patched, but a single click on a malicious link by an unsuspecting employee can bypass even the most sophisticated defenses. That’s why building a human firewall is just as critical as deploying a technical one. Even with a platform that gives you a unified view of cyber risks, human error remains a leading cause of security breaches.
A truly resilient security strategy integrates people, processes, and technology. When your team is informed, engaged, and feels a sense of shared ownership over security, they transform from potential liabilities into your first line of defense. This shift doesn’t happen by accident; it requires a deliberate effort to educate, collaborate, and foster a security-conscious culture. Investing in your people is one of the highest-return investments you can make in your cybersecurity program, turning every employee into an active participant in protecting the organization from the inside out.
Let’s be honest: most security training is boring. A once-a-year slideshow isn’t going to cut it. Effective security awareness programs are continuous, engaging, and relevant to your employees’ daily roles. The goal is to move beyond compliance checklists and build real-world skills. A strong program empowers employees to recognize and avoid cyber threats, from sophisticated phishing emails to social engineering tactics. Consider implementing regular phishing simulations to test and reinforce learning in a safe environment. Tailor the training to different departments—what the finance team needs to know about wire fraud is different from what developers need to know about secure coding. By making training practical and ongoing, you build muscle memory that helps your team react correctly when a real threat appears.
Security isn’t just the security team’s problem. When developers, IT operations, and business leaders work in silos, critical exposures can be missed. Fostering collaboration ensures that everyone can understand their essential role in protecting the organization. This means creating open channels of communication where a developer feels comfortable asking a security expert about a new application’s configuration, or the marketing team knows who to call about a suspicious email. Breaking down these walls helps integrate security into the entire business lifecycle, from product development to marketing campaigns. When security is a team sport, you can identify and address threats much faster, creating a more unified and effective defense.
A strong security culture is one where safe practices are second nature. It’s about shifting the mindset from “security is a barrier” to “security is how we protect our customers and ourselves.” This starts from the top down, with leadership championing security as a core business value. When employees are encouraged to report mistakes without fear of blame, they become more vigilant. This culture is built through consistent messaging, positive reinforcement, and making it easy for everyone to do the right thing. Appoint security champions within different teams to act as local resources and advocates. When your team knows how to recognize phishing attempts and feels responsible for reporting them, you’ve built a powerful, organization-wide defense network.
Your attack surface doesn’t end at your own network. It extends to every vendor, partner, and contractor you work with. While you need to vet your third parties’ security controls, your internal team is still the gatekeeper. Well-trained employees are better equipped to identify and respond appropriately to suspicious activities that may originate from a compromised partner account. This includes verifying unusual requests from vendors, spotting fake invoices, or questioning unexpected changes to payment details. Your human firewall is a critical layer of defense in managing the risks that come with an interconnected business ecosystem. Regular training on vendor-related threats ensures your team remains a strong line of defense against attacks that try to exploit these trusted relationships.
An exposure management program is only as good as the results it delivers. But how do you know if your efforts are actually paying off? Moving from a reactive “whack-a-mole” approach to a proactive security posture requires a clear way to measure success. It’s about shifting the conversation from “How many vulnerabilities did we patch?” to “How much did we reduce our actual risk?” This means looking beyond simple volume metrics and focusing on outcomes that matter to the business.
The goal is to create a feedback loop where you can see what’s working, what isn’t, and where to focus your energy next. Having a unified view of your cyber risks is the foundation for this. When you can see your entire attack surface, prioritize threats based on real-world intelligence, and track your remediation efforts in one place, you can start to build a data-driven security program. This approach helps you demonstrate value to leadership and make your organization genuinely harder to breach. A platform like Uni5 Xposure provides this single pane of glass, making it easier to track progress and prove your program’s effectiveness.
You can’t improve what you don’t measure. To prove your program is working, you need to define clear Key Performance Indicators (KPIs) that go beyond vanity metrics. Instead of just tracking the total number of vulnerabilities, focus on metrics that reflect true risk reduction. Consider tracking Mean Time to Remediate (MTTR) for critical vulnerabilities, the percentage of your attack surface that is known and monitored, or the reduction in time it takes to detect a new, unknown asset. Effective security training is another key area; you can measure its success by tracking a decrease in phishing click-through rates. These KPIs give you tangible proof that your strategy is making a difference and help you focus on the vulnerabilities and threats that pose the greatest risk.
When you have solid data and clear KPIs, you can make much smarter decisions about where to invest your team’s time and budget. Measurement helps you pinpoint the weakest spots in your defenses, so you can direct resources to the areas that will have the biggest impact. For example, if your metrics show that misconfigured cloud assets are your primary source of exposure, you know to allocate more time to cloud security training and automated configuration checks. By minimizing unnecessary data exposure in high-risk areas, you can strategically reduce your attack surface and the potential impact of an attack. This data-driven approach ensures you’re getting the best possible return on your security investments.
The threat landscape is constantly changing, which means your security program can’t afford to stand still. Security is a “continuous, evolving journey,” not a destination. The KPIs you track are your guide for this evolution. They will show you where your program is maturing and where new gaps are emerging. For instance, a sudden spike in a particular type of threat might signal the need to update your security controls or invest in new technology. Regularly reviewing your metrics allows you to adapt your strategy, refine your processes, and ensure your defenses keep pace with attackers. Staying informed with up-to-date threat advisories is a critical part of this ongoing process.
Annual penetration tests and quarterly vulnerability scans are no longer enough to keep up with modern threats. Your attack surface changes daily as new assets come online and software is updated. That’s why continuous monitoring is essential for identifying and mitigating risks as they appear. By continuously assessing your environment, you can spot new exposures in near real-time, long before an attacker does. This proactive approach allows you to move from a scheduled, compliance-focused security model to one that is always on and ready to respond. It’s the only way to stay ahead of emerging threats and maintain a consistently strong security posture.
What’s the real difference between managing vulnerabilities and managing my attack surface? Think of it this way: vulnerability management is like checking all the locks on your doors and windows to make sure they’re strong. Attack surface management is like first taking a complete blueprint of your entire house to find every single door, window, skylight, and forgotten basement entrance you might not have even known existed. It’s the bigger picture. While finding and fixing specific flaws is crucial, managing your attack surface is about understanding your entire potential for exposure so you can protect it all.
This all sounds great, but where’s the best place to start if my team is already overwhelmed? The best first step is always discovery. You can’t protect what you can’t see, so focus on getting a complete and accurate inventory of all your assets, especially anything that’s connected to the internet. This isn’t about fixing everything at once; it’s about creating a reliable map of your digital footprint. Once you know what you have, you can begin to understand where your most significant risks are and make a focused plan instead of trying to boil the ocean.
My company already has a bunch of security tools. Isn’t that enough to cover our attack surface? It’s a common assumption, but having multiple tools often creates more noise than clarity. Each tool gives you a piece of the puzzle—your network scanner sees one thing, your cloud security tool sees another. The problem is that these tools rarely talk to each other, leaving dangerous blind spots in between. The goal isn’t just to have tools, but to have a unified view that connects the dots and shows you how a vulnerability on one asset could create a risk for another.
How can I get other departments, like IT and DevOps, to care about security and help with this? The key is to frame security as a shared responsibility that makes everyone’s job easier in the long run, not just another task on their to-do list. Instead of just sending them a list of vulnerabilities, share context. Show them how a specific exposure in their area could impact the business services they support. When you can connect security risks to their priorities—like application uptime or project deadlines—it stops being a “security problem” and becomes a business-wide effort in resilience.
You mention a “zero-trust” mindset. Is that realistic for a company that isn’t starting from scratch? Absolutely. Adopting a zero-trust model doesn’t mean you have to rip and replace your entire infrastructure overnight. It’s a gradual shift in mindset and strategy. You can start small by applying the principle of “never trust, always verify” to your most critical assets first. For example, you could begin by implementing stricter access controls and multi-factor authentication for your most sensitive data or applications. It’s an iterative process of reducing trust and increasing verification over time.