Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Vulnerability Prioritization Technology (VPT) has been evolving over the years, adapting to the changing architectures and systems that drive the world. Today’s organizations have a significantly high attack surface spanning through heterogeneous environments of many IoT devices, systems on-premise, cloud environments, custom applications, etc. Without potent technology, security teams struggle to prioritize the remediation of vulnerabilities and associated threats in a timely manner. However, the VPT-empowered Threat Exposure Management (TEM) platform HivePro Uni5 solves the problems security teams face and reinforces vulnerability mitigation.
Security Operations Centers (SOCs) are an integral part of an organization’s cybersecurity strategy. They are responsible for detecting, responding to, and mitigating security threats and breaches. However, SOC teams often face challenges that can hinder their effectiveness.
One major problem SOC teams face is the lack of a single source of truth. With the increasing complexity of modern networks and the proliferation of security tools, it can be difficult for SOC teams to get a clear and comprehensive view of the organization’s security posture. This can lead to missed threats and a lack of situational awareness.
Siloed security technologies can also be a problem for SOC teams. Many organizations have a patchwork of different security tools, each with its separate console and set of alerts. This can make it difficult for SOC teams to correlate events and get a complete picture of the organization’s security posture. It can also lead to a proliferation of false positives, wasting valuable time and resources.
Another challenge faced by SOC teams is a lack of collaboration between the security team and the remediation team. When a security breach occurs, it is essential that the security team works closely with the remediation team to identify and mitigate the threat quickly. However, a lack of communication and coordination between these two teams can significantly slow down the response time and increase the risk of further damage.
Finally, many organizations have difficulty justifying the costs associated with downtime due to security breaches. This can make it difficult for SOC teams to get the resources and support they need to manage and respond to threats effectively. Without a strong business case for downtime, it can be challenging for SOC teams to secure the necessary resources to prevent and mitigate security breaches.
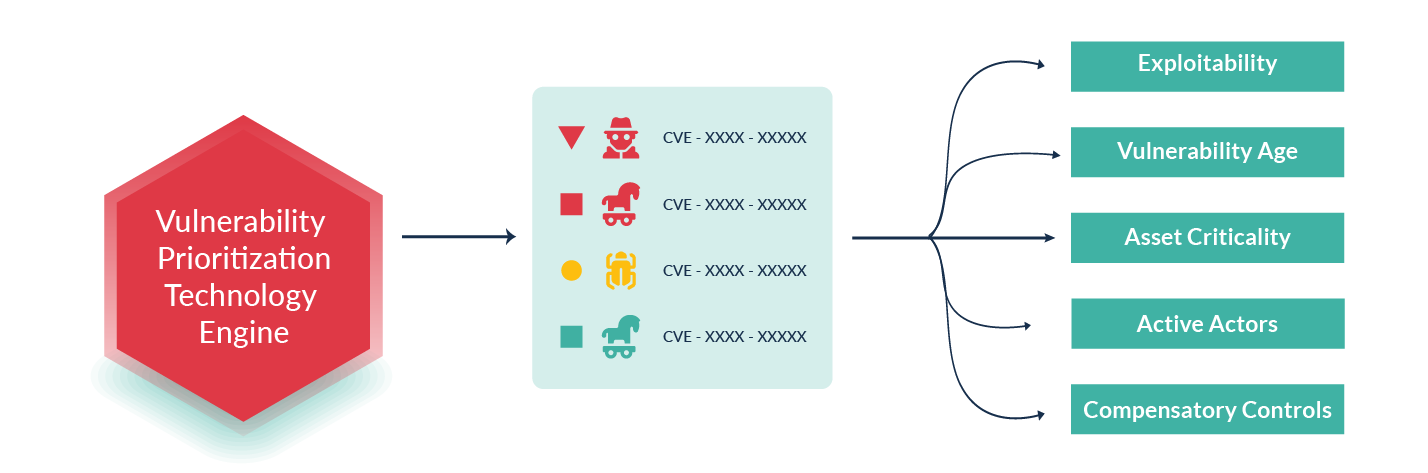
The VPT platform adds context to the vulnerabilities identified in an organization and links them with threats, which helps the team to do targeted mitigation. Parameters such as exploitability, vulnerability age, asset criticality, actors, and compensatory controls are considered to define the priority of the vulnerabilities.
The newly launched VPT Dashboard is designed and built with the core principle of the product, i.e., the consumerization of cybersecurity, which not only eases information consumption by executives, CISOs, and security analysts but also provides a clear view of the security posture of your infrastructure at a glance.
Traditional prioritization methods leave the security team with a number or rank without any additional context, resulting in blind spots, such as 0-day vulnerabilities that haven’t been assigned a CVSS score and can easily fly under the radar and jeopardize the organization.
On the other hand, Uni5 VPT allows you to customize your remediation plan based on team size or business requirements by giving prioritization from all perspectives. For example, some organizations might want to fix actor-targeted vulnerabilities with a lower score first based on history and not CVEs with higher risk scores.
The new interface allows you to track every minor detail, including but not limited to vulnerabilities being aggressively weaponized, actively exploited in the wild, already uploaded to pentesting frameworks, targeted by actors, and more. Along with a detailed report of the vulnerabilities, the VPT dashboard also generates a remediation plan that can serve as a blueprint for the security teams to enforce defensive measures. All this data, when juxtaposed with the vulnerabilities in your systems, provides context that helps you decide which vulnerabilities to address first.