Comprehensive Threat Exposure Management Platform
For a detailed threat digest, download the pdf file here
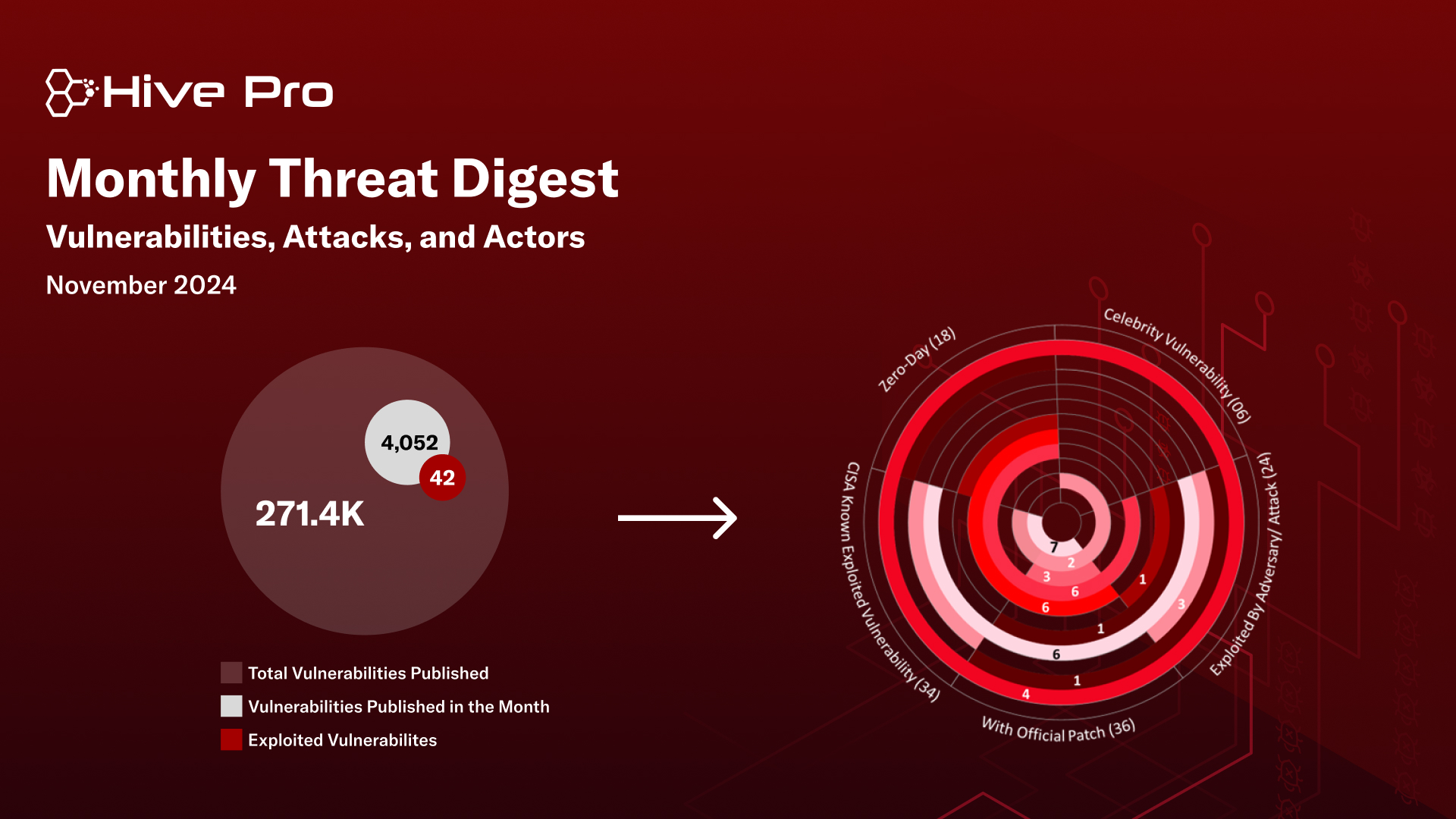
November brought a series of alarming developments in the cybersecurity landscape, with Eighteen zero-day vulnerabilities identified alongside critical flaws in widely used platforms. Among these, VMware’s vCenter Server was found vulnerable to CVE-2024-38812, which enables remote code execution through a heap overflow, and CVE-2024-38813, allowing privilege escalation. Both vulnerabilities are actively exploited in the wild, underscoring the urgent need for mitigation. Similarly, Palo Alto Networks released patches for two zero-day vulnerabilities in its PAN-OS software CVE-2024-0012 and CVE-2024-9474 which are being weaponized in a global reconnaissance campaign targeting critical infrastructure across various sectors.
In parallel, ransomware attacks surged, with groups like Helldown and Ymir leading aggressive campaigns. These incidents highlight the evolving complexity of ransomware tactics, emphasizing the importance of robust backup and disaster recovery plans as well as ongoing employee training to detect and avoid phishing schemes.
Throughout November, at least nine distinct threat actors carried out targeted operations. Among them, Earth Estries, a Chinese cyber-espionage group, targeted telecommunications, government organizations, and ISPs in regions such as the U.S., APAC, the Middle East, and South Africa. Exploiting vulnerabilities in public-facing servers, the group deployed tools like GhostSpider, SNAPPYBEE, and MASOL RAT for sustained espionage. Concurrently, Matrix, believed to be operating out of Russia, executed a highly disruptive Distributed Denial-of-Service (DDoS) campaign. By exploiting vulnerabilities in IoT devices, routers, and enterprise systems, and leveraging weak credentials, Matrix created a global botnet powered by the notorious Mirai malware.
Subscribe to keep up on a weekly basis with our weekly threat digests and newsletters.