Monthly Threat Digest: March 2025
For a detailed threat digest, download the pdf file here
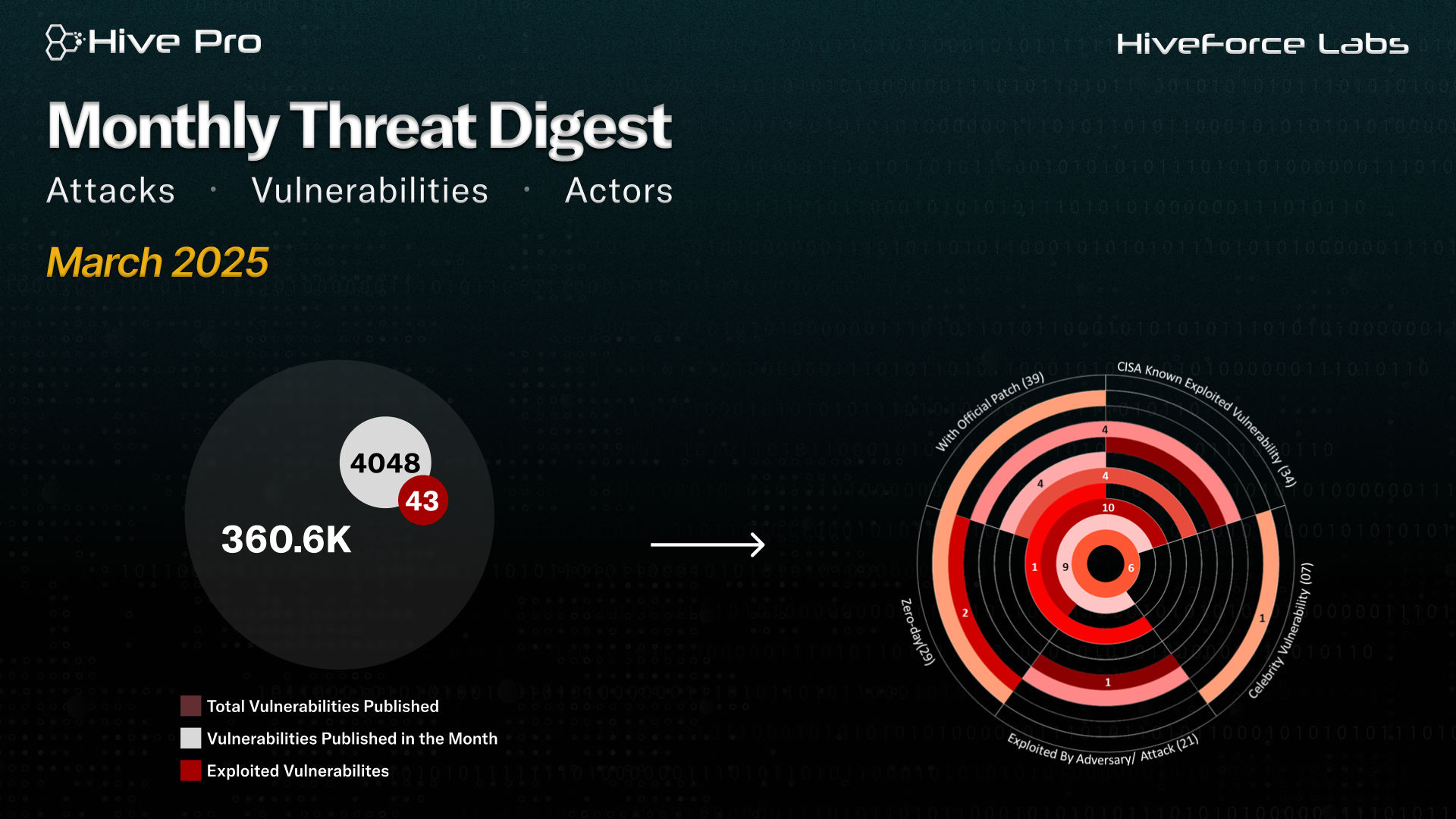
Summary
March sent shockwaves through the cybersecurity landscape by actively exploiting four celebrity vulnerabilities and 29 zero-days. Among the most alarming was a sophisticated supply chain attack that compromised the GitHub Action, exposing secrets in CI/CD workflows. This breach cataloged as CVE-2025-30154, triggered a secondary attack on CVE-2025-30066, endangering over 23,000 repositories.
Meanwhile, two critical flaws CVE-2025-0364 and CVE-2024-54761 were discovered in the BigAnt Server, with no official patch available. The existence of public exploits makes immediate defensive measures, such as disabling SaaS registration and restricting access is crucial. Google also rushed to patch CVE-2025-2783, a zero-day Chrome vulnerability actively exploited in the wild. This flaw has been weaponized in phishing campaigns, redirecting unsuspecting victims to malicious domains under the cyber-espionage operation ForumTroll.
Adding to the chaos, OBSCURE#BAT a stealthy malware campaign, leveraged social engineering and deceptive downloads to infiltrate systems, mainly preying on English-speaking users. Meanwhile, China’s MirrorFace APT group, traditionally focused on Japan-linked targets, launched its first known attack against a European entity. Dubbed Operation AkaiRyū (Red Dragon), the campaign unveiled an upgraded arsenal of espionage tactics. Elsewhere, the elusive FishMonger group (aka Earth Lusca) executed Operation FishMedley, targeting governments, NGOs, and think tanks across Asia, Europe, and the United States.
State-sponsored cyber espionage also took a new turn with Silk Typhoon an advanced threat actor now exploiting mainstream IT solutions remote management tools, cloud apps, and unpatched vulnerabilities to breach networks. As cyber threats intensify, vigilance and adaptability are no longer optional they are essential. Organizations must stay ahead of adversaries, fortifying their defenses against an ever-evolving digital battleground.
Subscribe to keep up on a weekly basis with our weekly threat digests and newsletters.
