Highlights of Our CISO Dinner
Upgrading struggling vulnerability management programs to Threat Exposure Management, with Host, CISO Al Lindseth formerly from Plains All American Pipeline and PWC - 6 minute podcast
For a detailed threat digest, download the pdf file here
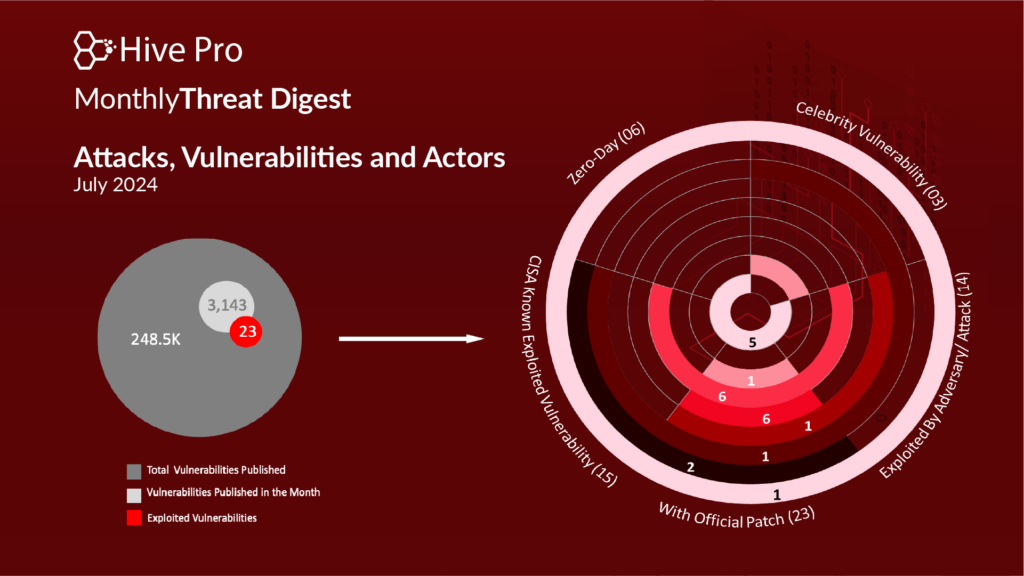
In July, the cybersecurity arena garnered significant attention following the identification of six zero-day vulnerabilities. Additionally, a supply chain attack impacted 100,000 web services globally due to a polyfill flaw. Two critical regression vulnerabilities, regreSSHion with OpenSSH and CVE-2024-41110 with Docker Engine, were reported; these vulnerabilities had been fixed earlier, but the fixes were not carried forward to subsequent versions. Later in the month, critical flaws were discovered in ServiceNow, which were exploited to allow unauthorized users to execute code remotely. These flaws are being exploited as part of a broader global reconnaissance campaign targeting various sectors, including finance, healthcare, and technology.
During this same timeframe, there was a marked increase in ransomware attacks, with variants such as Eldorado ransomware, EstateRansomware, ShadowRoot Ransomware, Play ransomware aggressively targeting victims. As ransomware tactics become increasingly sophisticated, it is
imperative for organizations to bolster their defenses by implementing comprehensive backup and disaster recovery strategies. Furthermore, training employees to detect and prevent phishing attacks remains essential.
Concurrently, eleven threat actors were engaged in various campaigns. Void Banshee, APT group, has been targeting North America, Europe, and Southeast Asia’s Education sector by exploiting the CVE-2024-38112, and deploying the Atlantida stealer for information theft and financial gains. Additionally, a newly emerged cyber threat actor, CRYSTALRAY uses advanced tools and tactics to steal credentials and deploy cryptocurrency miners.
Subscribe to keep up on a weekly basis with our weekly threat digests and newsletters.