Actors, Threats and Vulnerabilities 20 February to 26 February 2023
For a detailed threat digest, download the pdf file here
Summary
For a detailed threat digest, download the pdf file here
HiveForce Labs has identified five active threat actors over the past week. The Earth Kitsune APT and Lazarus Group are North Korean-based cybercrime groups that focus on information theft and espionage activities. The other three actors named WIP26, Hydrochasma, and Clasiop are also well-known for their information theft and espionage capabilities. For more information, please refer to the “Actors” section for key takeaways
Last week, we identified ten new strains of active malware. Three of them were information stealers: Stealc, DarkCloud, and Icarus. We discovered two new malware strains called SoulSearcher and Mylobot. Additionally, two were classified as backdoors: WhiskerSpy and WinorDLL64. We found two new RATs: Lilith RAT and Atharvan RAT. We also identified one new strain of ransomware called HardBit. For more information, please refer to the “Attacks” section for important highlights.
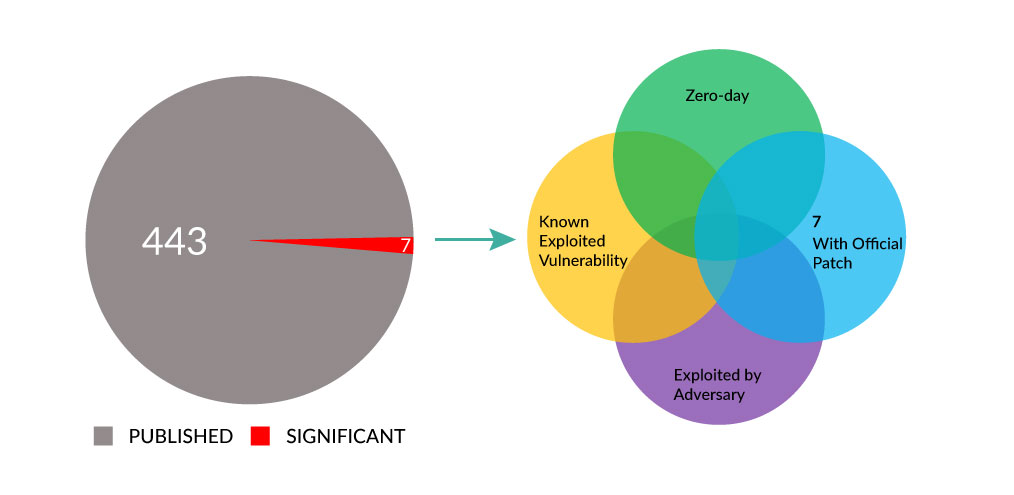
Last week, we identified seven vulnerabilities that organizations should be aware of. One of these vulnerabilities affects VMware Carbon Black App Control and permits access to the underlying server. The remaining six vulnerabilities affect FortiWeb, FortiOS, FortiNAC, and FortiProxy, and allow local attackers to elevate privileges and execute unauthorized code or commands. For more information, please refer to the key takeaway section on vulnerabilities.
