Hive Pro Recognized in 2023 Gartner® Hype Cycle™ for Security Operations & Market Guide™ for Vulnerability Assessment
Hive Pro was recently acknowledged in two prestigious Gartner publications known to identify industry leaders and innovators:
The Market Guide for Vulnerability Assessment (2023): “Security and risk management leaders can use this guide to understand VA technologies as part of a broader exposure management program.”
The Hype Cycle for Security Operations (2023): “Security and risk management leaders can use this research to strategize and deliver SecOps capability and functions.”
This recognition underscores Hive Pro’s unique value proposition across the Security Operations market, our exceptional performance with customers, and our dedication to driving the future of security operations.
Why Hive Pro?
Because we are bold enough to tackle the most pressing issues in threat and vulnerability management head on. Here are the problems we saw as detrimental to security teams:
| Constant Asset Blind Spots | Multiple Siloed Security Tools |
| Growing Security Data Sprawl | A Massive Vulnerability Backlog |
| Little Control Assurance Testing | Generic & Incomplete Vulnerability |
| Poor Contextual Threat Intelligence | Broken Cross-Functional Collaboration |
How Hive Pro Helps:
Hive Pro eliminates all of the above problems with Uni5, our unified platform approach to vulnerability and threat exposure management.
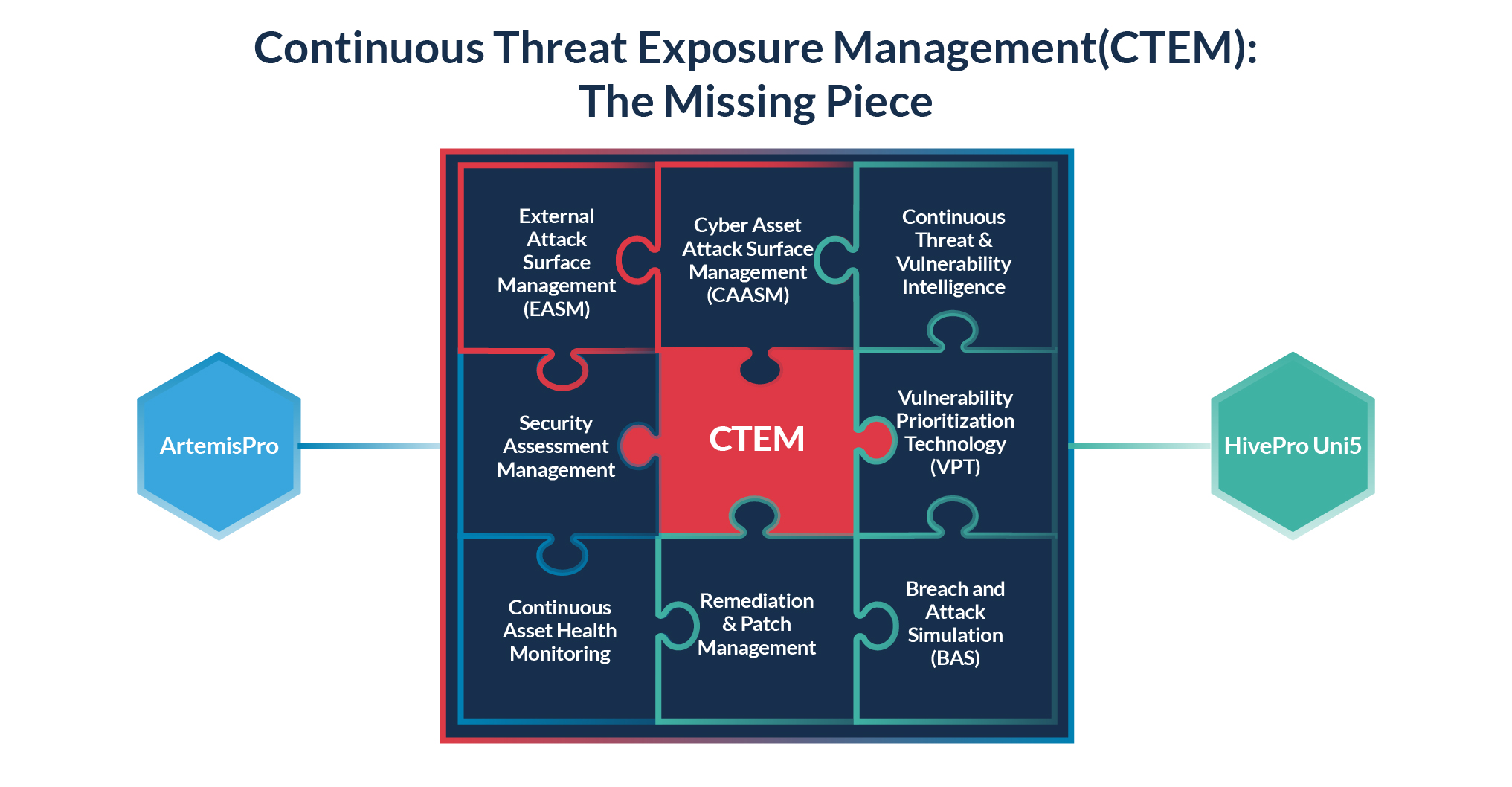
Hive Pro’s platform is engineered to deliver a cohesive approach towards cybersecurity, addressing multifaceted needs through an integration of key features:
- EM (Exposure Management) and CAASM (Cyber Asset Attack Surface Management): Hive Pro facilitates the continual evaluation of the visibility, vulnerability, and accessibility of an organization’s digital assets. We provide a systematic process aligned with Gartner’s continuous threat exposure management program, effectively managing, and mitigating the risks associated with the digital attack surface.
- VPT (Vulnerability Prioritization Technology): Hive Pro’s VPT streamlines a variety of vulnerability telemetry sources into a centralized location. Drawing upon Gartner’s insights, our approach considers exploitability, asset criticality, and compensating controls to provide prioritized, pragmatic recommendations for critical remediation, in line with a risk-based vulnerability management strategy.
- Threat Intelligence: Reflecting Gartner’s focus on contextualized findings, Hive Pro’s integrated Threat Intelligence goes beyond Common Vulnerability Scoring System (CVSS) scores, incorporating active threat actor and vulnerability information. Our insights lead to actionable intelligence and increased responsiveness to dynamic security threats. We have 218k+ CVE database and 115k+ Patch Intel, tracking more than 260 Threat actors and 3100+ in-built Attack scenarios.
- Automated Security Control Assessment: Aligned with Gartner’s emphasis on efficiency, Hive Pro’s platform reduces operational fatigue of standalone tools. We facilitate a proactive approach to security by automating assessments, ensuring your controls are effective and compliant, thus resonating with Gartner’s perspective on operational optimization.
- BAS (Breach and Attack Simulation): Hive Pro’s BAS capabilities echo Gartner’s recommendation for proactive security measures. We enable organizations to understand whether compensatory controls work efficiently or not, and also re-prioritize vulnerabilities based on existing controls. This comprehensive approach allows for a proactive and informed response to potential breaches, in line with Gartner’s emphasis on understanding exposure from an attacker’s point of view.
In one unified platform, Hive Pro gives you continuous visibility into your assets, vulnerabilities, threats, and relevant threat actors. We then feed the latter inputs, your security data inputs from all historical and ongoing security assessments, and our business intelligence through the Hive Pro Uni5’s AI-powered, vulnerability prioritization engine. What results is the missing piece in vulnerability management for the past 20 years—that is, focused and targeted prioritization based on your business context.
This evidence-backed approach evolves the historical, generic, and inefficient CVSS-based prioritization engines of current days. Our prioritization engine is also just one part of the Hive Pro Uni5 equation, as exhibited in the jigsaw puzzle above which is symbolic of our bringing together capabilities integral to vulnerability and threat management into one, unified platform.
Additionally, Hive Pro Uni5 drives actionable security remediation. With our automated security control testing, workflow management, in-platform collaboration, and streamlined patch remediation, we initiate and close the loop on managing vulnerabilities, eliminating threats, and reducing risks.
The Benefits of Adopting Hive Pro:
Integration Flexibility: Hive Pro seamlessly integrates with various Network Security scanners, ITSM & Patch Management platforms, and customized Application Security reports, centralizing Vulnerability Management.
Transition Feasibility: We offer a smooth transition from existing VM platforms, aligning with your organization’s unique needs.
Continuous Threat Exposure Management (CTEM): In alignment with the Gartner perspective, our platform focus adds tangible business value through visibility, prioritization, and comprehensive risk management.
The Outcomes You Can Expect:
Fster Remediation – Response in hours rather than days: Automate threat advisory remediation and get instant visibility into prioritized vulnerabilities on critical assets.
Enhanced Operational Efficiency – End-to-End vulnerability workflow & project lifecycle management: Initiate, manage, and communicate on continuous asset and vulnerability scans, vulnerability assessments, security assessments, and penetration tests.
Visibility to Blind Spots: Get proactive visibility into all your assets and the attacks, hackers & their techniques that are most likely to exploit existing vulnerabilities on your network.
Optimize Security Controls with Actionable Intelligence: Receive real time analysis with our Breach and Attack Simulation(BAS) module to improve the efficacy of your security controls and to validate your vulnerability management efforts.
See it for yourself today by Booking A Demo
Try it for yourself today by signing up for our 30-Day Free Trial
And keep up with the latest threats, vulnerabilities, and attacks by subscribing to our Weekly Digests.
Author: Zaira Pirzada
Gartner Disclaimer: Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


