Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Let’s be direct: if your team is drowning in a sea of CVEs and struggling to decide what to patch first, you’re not alone. The sheer volume of vulnerabilities can feel overwhelming, leaving even the most skilled security teams stuck in a reactive cycle of chasing alerts. This is where modern vulnerability management tools come in. They are designed to do more than just scan and report; they bring clarity to the chaos. The right platform helps you see your entire attack surface, integrates real-time threat intelligence to pinpoint active risks, and ultimately transforms your long list of weaknesses into a prioritized, actionable plan.
Let’s get straight to it. Vulnerability management tools are essential software solutions that continuously identify, assess, and help you fix security weaknesses across your entire IT environment. Think of them as your automated security patrol, systematically checking every digital nook and cranny—from servers and networks to applications and cloud assets—for unlocked doors that an attacker could exploit.
The core function of these tools is to move beyond simple scanning. They are designed to provide actionable insights that help your team prioritize what to fix first. Instead of just handing you a massive list of potential issues, a strong vulnerability management tool helps you understand the context behind each weakness. This systematic process of finding and addressing security gaps is fundamental to reducing your overall attack surface and preventing breaches before they happen.
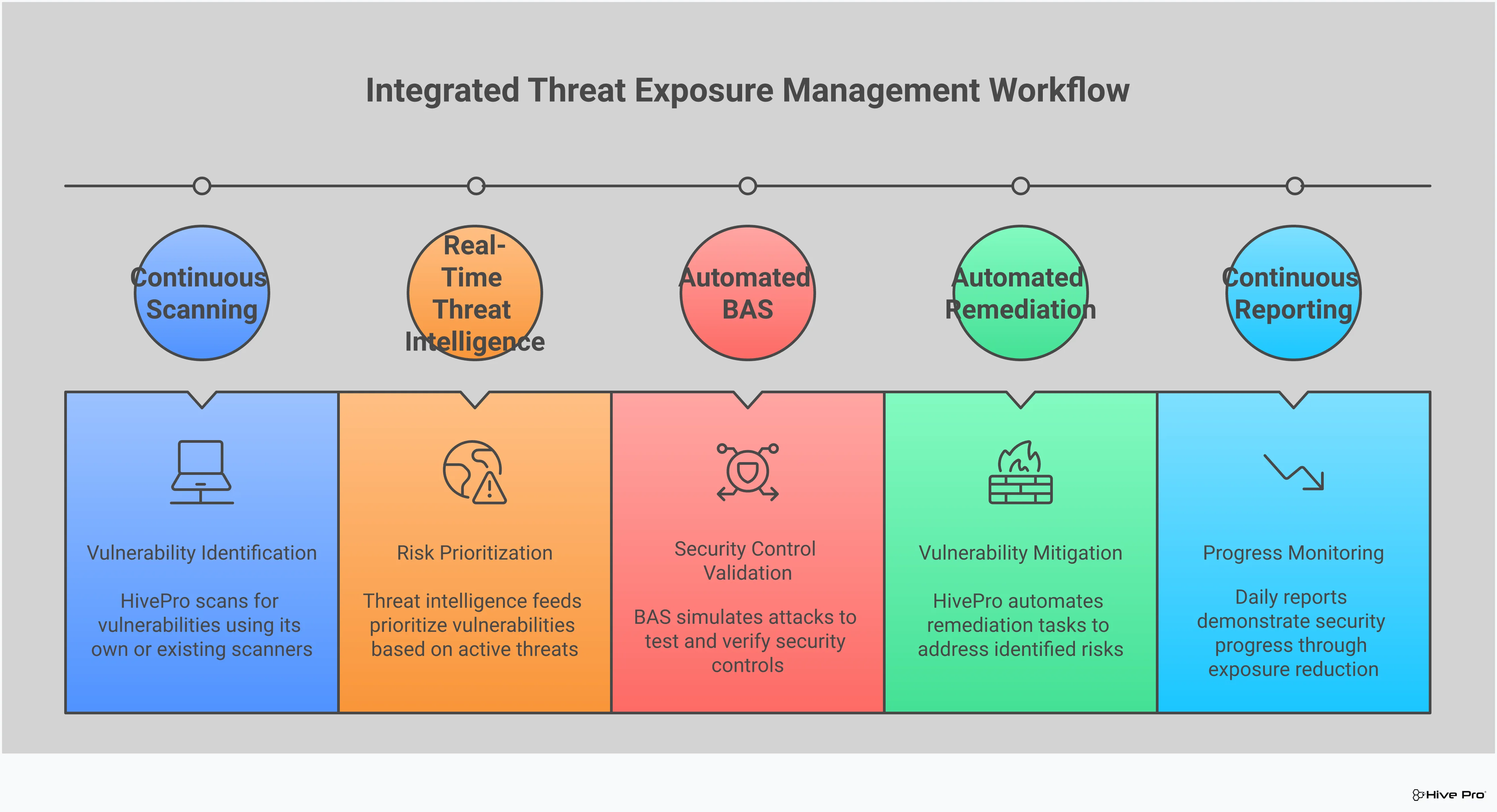
By automating the discovery and assessment process, these tools free up your security team from tedious manual work and significantly shorten the time attackers have to act. This allows your team to focus on strategic remediation efforts rather than getting lost in the noise of endless alerts. Ultimately, the goal is to transform your security posture from reactive to proactive, using a continuous cycle of discovery, prioritization, and remediation. This is the foundation of modern threat exposure management, where the focus shifts to understanding and reducing risk with intelligent vulnerability prioritization.
Let’s be direct: manually tracking vulnerabilities across your entire IT environment is no longer feasible. The sheer volume of new threats emerging daily, combined with the growing complexity of networks, applications, and cloud infrastructure, makes a manual approach a recipe for disaster. Attackers are opportunistic, and the rising cost of data breaches shows that companies of all sizes are in their crosshairs. Without a dedicated tool, your security team is left trying to put out fires instead of preventing them.
A robust vulnerability management tool shifts your security posture from reactive to proactive. Instead of scrambling after an incident, you can continuously identify and assess security weaknesses across your systems. This allows you to get ahead of attackers by understanding your exposure before they can exploit it. By adopting a tool that provides a complete view of your attack surface, you can make informed, strategic decisions about where to focus your resources to effectively safeguard your organization against an ever-changing threat landscape.
Beyond just finding flaws, these tools bring critical efficiency to your security operations. They automate the time-consuming tasks of scanning and discovery, freeing up your team for higher-value work. More importantly, the right platform helps you prioritize what needs to be fixed first based on real-world risk, not just a generic severity score. This ensures your team isn’t wasting time on low-risk issues while a critical vulnerability remains exposed. This automation also creates a clear audit trail, generating the reports you need to prove compliance with regulations like HIPAA or PCI-DSS and demonstrate due diligence to stakeholders.
Choosing a vulnerability management tool isn’t just about picking the one with the longest feature list. It’s about finding a platform that fits your team’s workflow and gives you the clarity to act decisively. The right tool moves you from drowning in a sea of alerts to confidently addressing the risks that truly matter. As you evaluate your options, look for solutions that provide a complete, contextualized view of your security posture. Focus on capabilities that help you discover your entire attack surface, prioritize threats intelligently, and validate that your defenses are actually working.
You can’t protect what you don’t know you have. That’s why the first thing to look for is a tool that can provide a complete and continuously updated inventory of all your assets. This includes everything from servers and laptops to cloud instances, containers, and IoT devices. A powerful tool will give you a unified view of your total attack surface, ensuring no rogue or forgotten assets are left exposed. Without this foundational visibility, even the most advanced scanning will have blind spots, leaving you vulnerable to attacks that you never see coming.
A long list of vulnerabilities is just noise. The key is to find the signal. Modern vulnerability management tools move beyond basic CVSS scores and use risk-based prioritization. They integrate real-time threat intelligence to tell you which vulnerabilities are being actively exploited in the wild and which ones pose a direct threat to your critical assets. This context is crucial. It allows your team to stop chasing every single vulnerability and instead focus their limited time and resources on fixing the flaws that attackers are most likely to use against you.
Your vulnerability management tool shouldn’t operate in a silo. To be effective, it needs to integrate smoothly with your existing security and IT ecosystem. Look for a platform with robust APIs and pre-built integrations for tools like SIEMs, SOAR platforms, and ticketing systems such as Jira or ServiceNow. This security automation streamlines the entire remediation lifecycle, from ticket creation to verification. By automating routine tasks, you free up your security team to concentrate on more strategic initiatives instead of getting bogged down in manual processes.
The days of running quarterly or even monthly vulnerability scans are over. Your environment is dynamic, with new assets spinning up and configurations changing constantly. Your vulnerability management tool needs to keep pace. Look for a solution that offers continuous, real-time monitoring and scanning. This approach provides an always-on, up-to-date picture of your security posture, unlike periodic scans that can leave you exposed for weeks or months. This is a core principle of a Continuous Threat Exposure Management (CTEM) program, which helps you proactively manage your exposure as it evolves.
Finding a vulnerability is one thing; confirming it’s exploitable in your environment is another. This is where Breach and Attack Simulation (BAS) comes in. Leading platforms include BAS capabilities to safely simulate real-world attack paths and test whether your security controls—like firewalls and EDR—would actually stop an attack. This adversarial exposure validation helps you confirm which vulnerabilities pose a genuine risk, reducing false positives and helping you prioritize with confidence. It also validates that your remediation efforts were successful, closing the loop on your vulnerability management lifecycle.
A vulnerability management tool is only as good as the actions it inspires. That requires clear, customizable reporting that speaks to different audiences. Your technical teams need granular details to fix issues, while your CISO and executive board need high-level dashboards that communicate overall risk posture and progress over time. The right tool makes it easy to generate these reports. It should also help you streamline compliance management by mapping vulnerabilities to specific regulatory frameworks like PCI DSS, HIPAA, or ISO 27001, making audit preparation much less painful.
Choosing the right vulnerability management tool can feel overwhelming with so many options on the market. To make it easier, I’ve pulled together a list of some of the top players in the space. Each platform brings something different to the table, from comprehensive threat exposure management to powerful, focused scanning. Think of this as your starting point for finding the solution that best fits your team’s workflow, your company’s security goals, and your existing tech stack.
We’ll look at what makes each tool unique, who it’s best for, and its core strengths. Whether you’re a large enterprise needing an all-in-one solution or a smaller team looking for an efficient scanner, there’s a tool here for you. Let’s get into the specifics of what Hive Pro, Tenable, Qualys, and others have to offer.
The Hive Pro Uni5 Xposure Platform is built for teams that want to move beyond traditional, reactive vulnerability management. It provides a complete picture of your cyber risks in one place, helping you focus on the threats that actually matter. What sets it apart is the integration of in-house threat intelligence from HiveForce Labs, which gives you context on which vulnerabilities are being actively exploited in the wild. This approach helps you prioritize remediation efforts based on real-world risk, not just CVSS scores. It’s a great fit for organizations looking to adopt a proactive Threat Exposure Management (CTEM) strategy and get a handle on their entire attack surface.
Tenable is a well-known name in the security space, and its Vulnerability Management platform is a core part of its offering. The platform is designed to help you find and fix weaknesses across your modern attack surface, including cloud infrastructure, web apps, and containers. One of its key features is its use of AI to help predict which vulnerabilities are most likely to be exploited, allowing your team to prioritize more effectively. It’s a solid choice for businesses that need a reliable, comprehensive solution for identifying and addressing security gaps before they can be leveraged by attackers.
Qualys VMDR (Vulnerability Management, Detection, and Response) brings together several security functions into a single, unified platform. It’s designed to give you a continuous inventory of all your IT assets, identify their vulnerabilities, and prioritize them based on threat intelligence and AI-powered risk scores. The “response” part of its name means it also helps you deploy patches to fix the issues it finds, all from one console. This all-in-one approach can simplify workflows and reduce the need to juggle multiple tools. It’s a strong contender for organizations that want a streamlined solution for the entire vulnerability lifecycle.
Rapid7’s InsightVM is known for its live vulnerability and endpoint analytics. It goes beyond standard scanning by collecting data directly from your assets, giving you a real-time view of your risk. The platform is great at covering a wide range of environments, from traditional networks to cloud and containerized platforms. It also helps teams work more efficiently by integrating with popular tools like Slack and Jira, making it easier to assign and track remediation tasks. If your team values real-time data and seamless workflow integrations, InsightVM is definitely worth a look.
Nessus Professional, from Tenable, is one of the most widely recognized and trusted vulnerability scanners in the industry. While it’s more of a point-in-time scanner than a full management platform, its power and accuracy are undeniable. It’s excellent for performing deep scans, configuration audits, and compliance checks against industry standards. Many security professionals use Nessus for its detailed assessments and comprehensive reporting. It’s an ideal tool for security consultants, penetration testers, and internal teams who need a robust scanner to complement their broader vulnerability management program.
For teams looking for an open-source option, Greenbone OpenVAS is a powerful and popular choice. As a vulnerability scanner, it performs comprehensive network scans to identify security holes. Because it’s open-source, it offers a high degree of flexibility and can be a cost-effective solution for organizations with the technical expertise to manage it. Maintained by Greenbone Networks, the tool has a large community and a long history of development. It’s a great fit for teams on a budget or those who prefer the customizability that open-source software provides.
IBM’s entry into the space, Security QRadar VMDR, is designed to work within the broader IBM Security ecosystem. Its main strength is its tight integration with threat intelligence, allowing you to prioritize vulnerabilities based on real-time data about active threats and attacker activity. This helps you understand which flaws pose the most immediate danger to your organization. For companies already invested in IBM’s security stack, like the QRadar SIEM, this tool can provide a cohesive and context-rich approach to managing vulnerabilities and responding to threats more effectively.
When you start looking at different vulnerability management tools, you’ll notice they often promise similar outcomes: find vulnerabilities and help you fix them. But how they get there can vary dramatically. The real differentiators are found in the specific features they offer, how they structure their pricing, and how easy they are to actually implement and use day-to-day.
Choosing the right tool means looking past the marketing claims and digging into these core areas. A platform that excels in one area might fall short in another, and what works for one organization might not be the right fit for yours. Let’s break down how to compare these tools side-by-side so you can find a solution that truly strengthens your security posture instead of just adding another dashboard to your collection.
Modern vulnerability management tools have moved far beyond simple network scanning. The best platforms combine scanning with threat intelligence and risk analysis to give you a clear, contextualized view of your exposure. Instead of just handing you a list of potential threats, they provide actionable insights that help you prioritize vulnerabilities and address risks before they can be exploited.
When comparing features, look for a tool that offers a complete picture. Does it provide AI-driven asset visibility to map your entire attack surface? Can it track threats in real-time across all your systems? A truly effective solution won’t just identify weaknesses; it will help you understand which ones pose the most immediate danger based on active, real-world threats.
Pricing for vulnerability management tools is rarely one-size-fits-all. Most vendors base their pricing on the number of assets you need to protect, which can include everything from employee devices and servers to web apps and cloud resources. For example, some plans might charge per device annually, while others offer tiered pricing for a set number of assets over one to three years.
When evaluating cost, think about your organization’s growth. Will the pricing model scale with you, or will you face a steep price hike as you add more assets? Also, be sure to ask what’s included. Are features like advanced threat intelligence, attack simulation, or detailed compliance reporting part of the core package, or are they expensive add-ons? Understanding the total cost of ownership is key to making a smart investment.
A powerful tool is only effective if your team can actually use it. The platform you choose should be straightforward to set up and manage, with a clear, intuitive dashboard that shows you critical risks at a glance. A user-friendly interface is essential for helping your security team work efficiently without a steep learning curve.
Look for a solution that fits seamlessly into your existing workflows. Can it integrate with your ticketing systems, SIEM, and other security tools? The goal is to find a platform that simplifies your processes, not complicates them. Gathering feedback from your team during a trial period can also reveal a lot about a tool’s day-to-day usability and help you find a solution that your team will embrace.
Choosing a vulnerability management tool isn’t about finding a flawless solution—it’s about finding the right fit for your team, your environment, and your security goals. While the top platforms share many powerful features, they also come with their own sets of trade-offs. Understanding these common strengths and weaknesses will help you see past the marketing jargon and focus on what truly matters for your organization’s security posture.
The goal is to find a tool that doesn’t just identify threats but gives your team actionable steps to mitigate risks before they can be exploited. It’s about moving from a state of constant reaction to one of proactive defense. Let’s break down what you can generally expect from the leading tools on the market—the good and the not-so-good.
When you look at user feedback and expert analysis, a clear theme emerges: the best vulnerability management solutions do more than just scan for weaknesses. They provide the context needed to prioritize remediation effectively. According to expert insights, top-tier tools are praised for their ability to turn a long list of potential threats into a manageable, prioritized workflow. Users often highlight the value of platforms that integrate seamlessly with their existing tech stack, making it easier to automate tasks and respond faster. The consensus is that a tool’s real value lies in its ability to provide actionable intelligence, not just raw data.
Most mature vulnerability management tools excel at the fundamentals. You can expect robust scanning capabilities that cover a wide range of assets across your network, from on-prem servers to cloud instances. These platforms are generally good at providing a comprehensive overview of your organization’s security posture at a given moment. Many also offer features to help prioritize fixes based on CVSS scores and asset criticality. Automation is another common strength, with many tools able to integrate with ticketing and patching systems to streamline the remediation process and reduce the manual workload on your security team.
Despite their strengths, many traditional tools have common drawbacks. A frequent complaint is the lack of a truly unified view, forcing teams to stitch together data from multiple dashboards to see the full picture. This often leads to alert fatigue and a struggle to identify which vulnerabilities pose an immediate, real-world threat. Many platforms are slow to incorporate the latest threat intelligence, leaving you a step behind attackers. Another challenge is the validation of security controls; without a way to test if your defenses actually work against specific attack scenarios, you’re left making assumptions. This is why modern platforms are integrating adversarial exposure validation to close that gap.
Vulnerability management isn’t just about running scans and generating long lists of CVEs. That approach often leads to overwhelming backlogs and a constant feeling of playing catch-up. The real turning point comes when you integrate threat intelligence into your process. This shifts the focus from simply identifying weaknesses to understanding the active threats targeting those weaknesses. By layering in data on attacker tactics, techniques, and procedures (TTPs), you gain the context needed to see which vulnerabilities pose a genuine, immediate risk to your organization. It’s the difference between having a map of every pothole in the city versus knowing which ones are on your daily commute and are most likely to cause a flat tire. This intelligence-driven approach is fundamental to building a proactive security posture.
Threat intelligence gives you a direct line of sight into how adversaries operate. Instead of just seeing a vulnerability’s CVSS score, you can see if it’s part of a known exploit chain, favored by a specific ransomware group, or being used in active campaigns targeting your industry. This context is crucial. Modern vulnerability management tools combine scanning with threat intelligence to dramatically shorten the window of exposure. By understanding the how and why behind an attack, your team can better anticipate an adversary’s next move and implement more effective, targeted defenses instead of just patching based on a generic severity score.
Your team has limited time and resources; you can’t fix every single vulnerability at once. Threat intelligence is your filter, helping you zero in on what matters most right now. It allows you to prioritize vulnerabilities that are being actively exploited in the wild, rather than theoretical risks. This is the core of risk-based prioritization. By focusing on the threats that have a high probability of impacting your specific environment, you can direct your remediation efforts where they will have the greatest effect. This asset-centric approach ensures you’re tackling the most urgent fires first and measurably reducing your organization’s exposure to imminent threats.
Integrating threat intelligence fundamentally changes your security program from a reactive to a proactive model. Instead of waiting for a critical alert or a failed audit to spur action, you can proactively hunt for and mitigate the highest-risk exposures before they are exploited. This proactive stance is powered by continuous intelligence that informs your entire security strategy. When you automate vulnerability management processes with real-time threat data, you empower your team to stay ahead of attackers. This allows you to move beyond a simple patch-and-pray cycle and build a resilient, forward-looking defense that is always adapting to the evolving threat landscape.
Finding vulnerabilities is one thing, but knowing if your defenses can actually stop an attack exploiting them is another challenge entirely. This is where Breach and Attack Simulation (BAS) comes in. Think of it as a continuous, automated sparring partner for your security infrastructure. Instead of relying on theoretical assumptions about your security posture, BAS tools safely simulate real-world attack techniques to see how your defenses hold up.
This proactive approach moves you beyond just patching vulnerabilities and into the realm of validating your entire security ecosystem. It helps answer critical questions like, “Would our EDR solution actually detect this specific ransomware strain?” or “Is our firewall configured correctly to block this lateral movement technique?” By running these controlled attack scenarios, you get concrete evidence of what’s working and, more importantly, what isn’t. This continuous feedback loop is essential for building a resilient security program. Integrating BAS into your vulnerability management strategy allows you to test your controls, validate your fixes, and fine-tune your detection capabilities, ensuring you’re prepared for actual threats. It’s a core component of modern adversarial exposure validation.
You’ve invested heavily in firewalls, endpoint detection, and other security tools, but how do you know they’re performing as expected? BAS platforms allow you to continuously test your security controls against the latest attack scenarios. Instead of waiting for an annual penetration test, you can run simulations daily or weekly to ensure your defenses are effective and properly configured. This process helps you identify gaps and misconfigurations before an attacker can exploit them. By safely mimicking the tactics used by real adversaries, you can get a clear picture of your security readiness and make data-driven decisions to strengthen your defenses against emerging threats.
Patching a vulnerability is a critical step, but it’s not the end of the story. How can you be certain the fix was successful and didn’t inadvertently open another door? BAS provides a platform to validate the effectiveness of your remediation efforts. After your team applies a patch, you can run a simulated attack that targets the specific vulnerability you just addressed. This confirms that the vulnerability is truly closed and that your security controls can now successfully block the exploit. This step closes the loop on the remediation lifecycle, giving you the confidence that your hard work has paid off and your organization is genuinely more secure.
Security teams are often drowning in a sea of alerts, making it difficult to spot the signals through the noise. By simulating attacks, you can better understand which alerts are actionable and which are false positives, which helps significantly reduce alert fatigue among your security analysts. When a BAS tool runs a simulation, you can see exactly which alerts your systems generate—or fail to generate. This insight allows you to fine-tune your detection rules, so your team can focus its energy on credible threats instead of chasing down benign events. It’s a practical way to optimize your security operations and improve your team’s overall effectiveness.
Picking the right vulnerability management tool feels like a huge decision because it is. This tool will become a core part of your security stack, so you want to get it right. Instead of getting overwhelmed by feature lists, let’s break down the process into a few practical steps to help you find the perfect fit for your team and your organization.
Before you even look at a demo, you need a clear picture of what you’re trying to protect. Every organization’s environment is unique. Are you running everything in the cloud, on-prem, or a hybrid of both? Do you have a lot of IoT devices, containers, or mobile assets? The right tool needs to see everything. Make a list of all your asset types and ask potential vendors if they can provide full coverage. Think about the future, too. You need a solution that can grow with you as your company and its total attack surface expand. Don’t settle for a tool that only covers a fraction of your environment—blind spots are where attackers thrive.
A vulnerability management tool that doesn’t play well with your other systems will just create more work for your team. The goal is to streamline your workflow, not complicate it. Check if the tool can integrate smoothly with your existing security infrastructure, like your SIEM, SOAR, and ticketing systems such as JIRA or ServiceNow. This is key for automating remediation workflows and making sure vulnerabilities are assigned and tracked efficiently. A good tool should do more than just find problems; it should provide actionable insights that help you fix them. This turns your vulnerability management program from a simple scanning exercise into a strategic risk reduction engine.
Let’s talk about money. While budget is always a factor, don’t just look at the initial price tag. Consider the total cost of ownership, which includes implementation, training for your team, and ongoing support. Some vendors offer multi-year subscriptions at a discount, which can be a great way to lock in a price if you’ve found the right fit. Think about the resources you have available. Does your team have the bandwidth to manage a complex new tool, or do you need something more intuitive and user-friendly? Investing in the right platform is a critical step in securing your organization and staying ahead of threats, so make sure it’s a tool your team can actually use effectively from day one.
Selecting a new vulnerability management tool is a big step, but the real work begins with implementation. This phase is more than just installing software; it’s about integrating a new process and mindset into your organization. A smooth rollout sets the stage for a successful program, so planning for the technical and human elements is key to getting it right from day one.
Let’s be real: even the best tools can face a bumpy rollout. A common challenge is simply knowing what to protect. A scanner can’t secure an asset it doesn’t know exists, so you need a solid process for total attack surface management that continuously discovers everything. Another major hurdle is getting engineering teams to act on findings. Instead of just sending them a list of vulnerabilities, integrate the tool directly into their world. Connect it to their existing ticketing systems and CI/CD pipelines so security becomes a natural part of their workflow, not a disruptive interruption.
A new tool doesn’t run itself. Your program’s success depends on having the right people with the right skills. This means your team needs to interpret scan results, analyze threat intelligence, and prioritize what truly matters. They also need strong communication skills to explain to other departments why a fix is urgent. Invest in proper training, but also work to foster a culture that prioritizes security across the organization. Vulnerability management is an ongoing cycle, not a one-off project. When everyone understands their role, you shift from a reactive approach to a proactive, security-first mindset.
Getting the most value from your new tool is about making your entire security operation more efficient. Start by automating as much as possible: schedule scans, generate reports, and create remediation tickets automatically. This frees up your team for more strategic work. Deep integration also maximizes your return. A tool that connects seamlessly with your existing security stack—like your SIEM and SOAR—creates a unified view of your security posture. Finally, use the tool’s reporting and analytics to demonstrate value to leadership. Show them tangible metrics like a reduced mean-time-to-remediate (MTTR) to prove the tool’s worth and help secure future security investments.
My team is already overwhelmed with alerts. Won’t a new vulnerability management tool just add to the noise? That’s a completely valid concern, and it’s the exact problem a modern tool is designed to solve. A basic scanner will absolutely drown you in a sea of low-context alerts. A true vulnerability management platform, however, does the opposite. It acts as a filter by using threat intelligence to show you which vulnerabilities are being actively exploited and pose a real, immediate threat. Instead of a list of 10,000 potential issues, you get a prioritized list of the 10 you need to fix right now. The goal isn’t to create more work, but to bring clarity so your team can focus its energy on risks that actually matter.
What’s the real difference between a vulnerability scanner and a full threat exposure management platform? Think of it like this: a vulnerability scanner is like getting a list of all the unlocked doors and windows in your building. It’s useful information, but it’s just a snapshot in time. A threat exposure management platform gives you that list, but also tells you which unlocked doors are on the ground floor, which ones have active burglars casing them, and whether your security cameras are actually working. It provides the full context by mapping your entire attack surface, integrating real-world threat intelligence, and validating your security controls, turning raw data into a strategic plan for reducing risk.
How does Breach and Attack Simulation (BAS) fit into our daily workflow? Is it just for pen testers? Not at all. While pen testers do specialized work, BAS is designed for your internal security team to use continuously. It automates the process of safely testing your defenses against the latest attack techniques. You can use it to validate that a patch you just deployed actually worked or to confirm that your security tools are configured correctly to stop a specific threat. It becomes a routine check-up for your security posture, giving you constant feedback on whether your defenses are performing as expected, rather than waiting for an annual test to find out you have a problem.
We get threat intelligence feeds, but how does a tool make that information more actionable? Raw threat intelligence feeds can feel like drinking from a firehose. A good vulnerability management platform acts as the translator. It takes that global threat data and maps it directly to the specific vulnerabilities found in your environment. So instead of just knowing that a certain ransomware group is active, the tool will tell you, “This specific server has a vulnerability that this exact ransomware group is exploiting right now.” It connects the dots for you, turning abstract threat data into a concrete, prioritized to-do list for your team.
How can I justify the investment in a comprehensive vulnerability management tool to my leadership? When talking to leadership, focus on business risk, not just technical details. Explain that a modern tool moves security from a cost center to a strategic function that protects the business. You can frame the investment around reducing the financial risk of a data breach, ensuring compliance with industry regulations to avoid fines, and improving operational efficiency. Use the tool’s reporting to show clear metrics, like a reduction in critical vulnerabilities or a faster time to remediate threats. This demonstrates a tangible return on investment by showing how you are proactively lowering the company’s overall risk profile.